Maximizing C-I-A
As with all other domains in the IT infrastructure, your main goal in the LAN-to-WAN Domain is to deploy and maintain controls that support all of the C-I-A properties of security for your data. The LAN-to-WAN Domain contains several components that play critical roles in providing secure access to your organization’s data. Maintaining that security requires diligence and the right controls.
Minimizing Single Points of Failure
One of the main functions of the LAN-to-WAN Domain is to provide access, or connectivity, between the LAN and the WAN domains. One property in the C-I-A triad is availability. Resources and data are available only if users can successfully establish connections between the two domains. If any device in the LAN-to-WAN Domain is required to make a connection, that device must be functional to fully support data availability. To minimize any downtime due to device failure in the LAN-to-WAN Domain, ensure every node has an alternate whenever possible. Any node that does not have an alternate becomes a single point of failure. If the node fails or becomes unavailable, it affects the entire domain. Evaluate each node to see if a redundant node would remove the single point of failure. Allow unique devices only if there are no other available alternatives and implement compensating controls to protect the availability property.
Dual-Homed ISP Connections
Many organizations employ a single connection to their ISP. If the connection device goes down, so does the Internet access for the entire organization. In the preceding section, you learned to avoid single points of failure. That goal applies to your ISP connection as well. The solution is to establish at least two ISP connections, as shown in Figure 11-7.
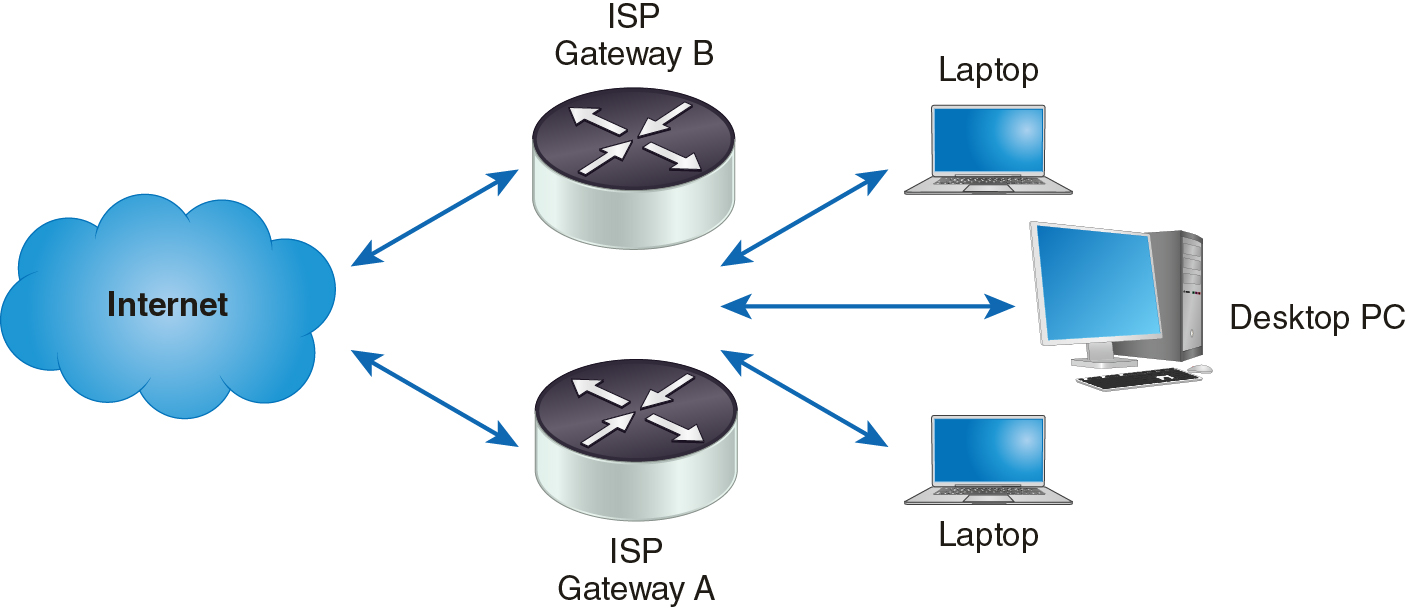
FIGURE 11-7 Multiple ISP Connections to Avoid a Single Point of Failure
A dual-homed ISP connection is a design in which a network maintains two connections to its ISP. If one gateway or connection fails, the other can still connect to the Internet.
In the simplest case, you use the primary connection for normal Internet access. You use the secondary connection only if the primary connection fails. You can implement this solution easily, but it does waste the available bandwidth on the secondary connection because it sits unused most of the time. Another option is to use both connections at all times. Your ISP connection devices can decide which connection to use based on many criteria. More-sophisticated connection-management software can use the best ISP connection based on available bandwidth. This method provides load balancing as well as fault tolerance. Less-sophisticated connection-selection methods may involve simple round-robin or connection-count algorithms. Regardless of the method you use, having a secondary ISP connection can protect you from WAN connection failures.
If you decide to set up dual-homed ISP connections, you can choose from two different options:
Use two connections to the same ISP—Two connections to the same ISP might save money but are still vulnerable to interruption if your ISP fails.
Use two connections to different ISPs—Maintaining two connections to different ISPs will cost more and require more maintenance due to working with different vendors, but will protect your environment if one ISP goes down.
Examine using dual-homed ISP connections to maximize your data availability.
Redundant Routers and Firewalls
A common bottleneck in any network is the router or firewall. In many networks, these devices require that all traffic pass through them. Although that practice does make maintenance and configuration easier, it introduces one or more single points of failure. If all traffic from the Internet passes through one router and that router crashes, how can your Internet users connect to you? The answer is, they can’t.
The easiest way to see the most obvious single points of failures for network connections is to map your network. It is easy to see on a network map where node failure would result in a fragmented network. After you identify routers and firewalls that are single points of failure, you should introduce redundant nodes to your network. Every single point of failure should have at least one alternate device. Having redundant devices allows your network to continue in the case of a device failure. If there are two paths from point A to point E and one path fails, all traffic can use the other path. Implementing redundant devices addresses availability by protecting your network from device failure. In addition, you gain the additional benefit of spreading out traffic among the redundant devices and possibly increasing overall performance. In both cases, redundant network devices can protect the availability of your network.
Web Server Data and Hard Drive Backup and Recovery
You should have a recovery plan in place for every device and computer in your organization. Business continuity plans (BCPs) and disaster recovery plans (DRPs) enable you to recover from disruptions ranging from small to large.
One crucial part of a BCP or a DRP involves recovering data and configuration settings from a secondary copy saved in case you lose your primary copy. This secondary copy of data to be used in case of primary data loss is commonly called a backup image of data, or just a backup. The value of a backup in the recovery process depends on how current it is. Because you’ll lose any work that occurred after your last backup when you recover data, it makes sense to back up frequently.
One of the more common servers in the DMZ is the web server. Web servers provide a generic front end to many enterprise applications and resources. Web servers provide the first visible point of contact for many remote clients and are necessary to bridge the outside Internet user community with the far more structured collection of application components in your organization’s secure network. If your organization’s web server is down, your organization’s web presence is down too. To maximize the availability of your organization’s web presence even in the face of disasters, it is important to ensure you have a current recovery plan for all the web servers in the LAN-to-WAN Domain. A current recovery plan is one that you support with frequent backups—and one that you test on a regular basis. A solid schedule for backups and a plan to recover your web servers in the case of an interruption that involves data loss will maximize your organization’s uptime.
Use of VPN for Remote Access to Organizational Systems and Data
You have seen several topics that relate to data availability but nothing yet that relates to the other two properties of the C-I-A triad, integrity and confidentiality. Information that travels to and from the Internet or another WAN can potentially be accessed by pretty much anyone. The best protection for information on a WAN is to use encryption. You can allow remote users to access resources on your LAN through the LAN-to-WAN Domain by setting up a virtual private network (VPN).
A VPN is a persistent connection between two nodes. The nodes can be on the same network or on separate networks. Many VPNs also encrypt all the traffic that flows along the connection. Because the traffic is encrypted, no unauthorized users can see the information. In this manner, encryption supports data confidentiality. Attackers can modify the data along its route, but without knowing what the data actually contains, the changes would not have a real purpose other than to destroy data. When the altered data reaches the end of the VPN and is decrypted, the VPN endpoint detects the change and takes action. The endpoint can either request that the data be re-sent or throw an error. Either way, you detect the unauthorized change and protect the data’s integrity.
