Identifying Critical Requirements for the Audit
The risk assessment will influence the critical requirements for an IT audit. Overall, there are various types of IT audits. In addition to infrastructure audits for compliance, other examples include audits specific to IT processes, such as governance and software development. Another example includes integrated audits, where financial controls are the focus.
Auditing IT infrastructure for compliance incorporates the evaluation of various types of controls. IT organizations today are concerned with controls relating to both security and privacy. Traditionally, privacy and information security activities are separate activities. The two, however, have become more interrelated, and coordination between the two has become a priority for many organizations. Two major factors contributing to this are regulatory issues and the rapid growth and widespread use of the Internet. As a result, both privacy and information security are converging, specifically around compliance issues.
Implementing Security Controls
Before an evaluation of controls can begin, the auditor must first identify the critical controls. To do so, the auditor must consider the audit scope and objective along with the risk assessment. Documentation and any preliminary interviews also help to identify the requirements.
Controls can be classified into different groups to aid in understanding how they fit into the overall security of a system. Table 5-1 illustrates the different dimensions of control classifications. Understanding the classifications provides auditors with a foundation to identify and assess critical controls.
TABLE 5-1 NIST 800-53 R5 Cybersecurity and Data Protection Program (CDPP)
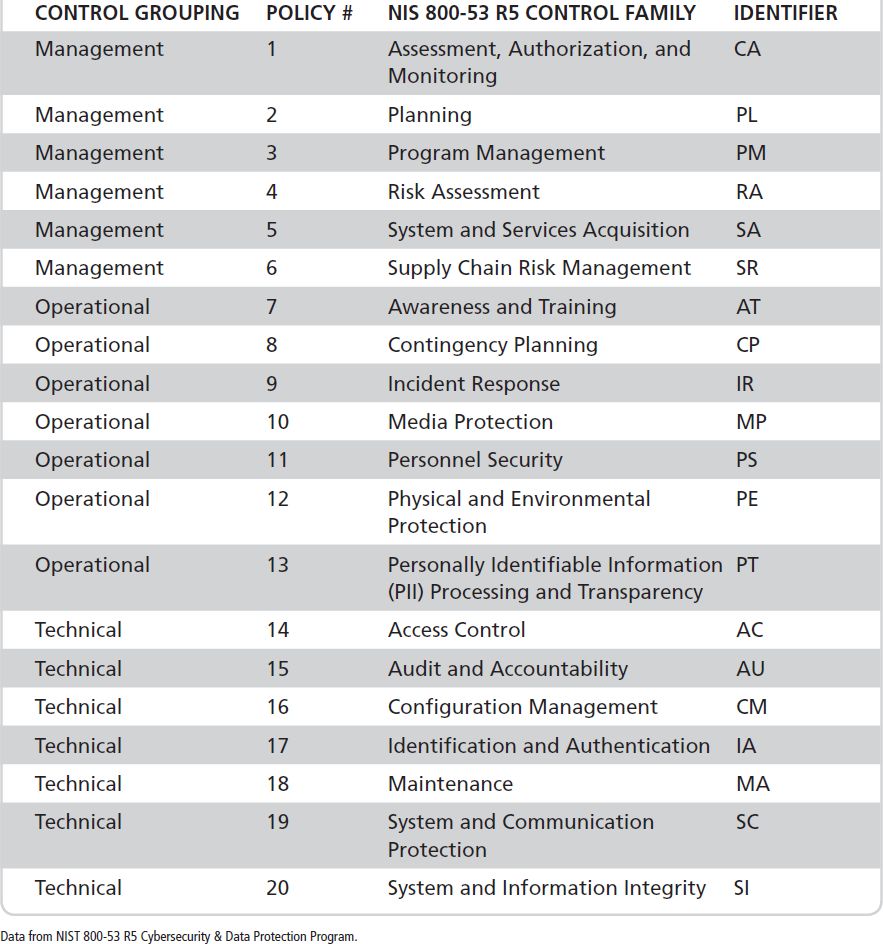
A high-level classification of controls for IT systems includes general and application controls. General controls are also known as infrastructure controls. These types of controls apply broadly to all system components across an organization. Application controls apply to individual application systems. Types of application controls include various transaction controls, such as input, processing, and output controls.
Three IT security controls groupings that are covered by the National Institute of Standards and Technology (NIST) include management, operational, and technical controls. The following list provides a description and examples of each of these:
-
Management controls—These controls are typically governed by management as part of the overall security program. Examples include the following:
-
Security policy
-
Security program management
-
Risk assessment
-
Security and planning in the system development life cycle
-
System and services acquisition
-
-
Operational controls—These controls are implemented by people rather than systems. These controls are often interrelated with both management and technical controls. Examples include the following:
-
Personnel and user issues
-
Contingency and disaster planning
-
Incident response and handling
-
Awareness, training, and education
-
Physical and environmental security
-
-
Technical controls—These controls are performed by the IT systems. Examples include the following:
-
Identification and authorization
-
Logical access control
-
System Communications
-
Cryptography
Control functions can be further classified as one of the following three types:
-
Preventative controls describe any control that’s designed to stop unwanted or unauthorized activity from occurring. A few examples include physical controls such as fences, locks, and alarm systems.
-
Detective controls describe any controls to detect and alert to unwanted or unauthorized activity in progress or after it has occurred. A detective control does not prevent the event but alerts you to the event. Physical examples include alarms or notifications from a physical sensor (door alarms, fire alarms) that alert guards or police. An audit log reviewed regularly could be considered a detective control.
Corrective controls include any measures taken to repair damage or restore resources and capabilities following an unauthorized or unwanted activity. Examples could be restoring corrupted files from a backup server.
-
Protecting Data Privacy
Audits of IT infrastructure relating to security are common. However, due to recent legislation regarding the need to protect personally identifiable information, audits specific to privacy are more commonplace than before. ISACA defines privacy within the context of information systems as “adherence to trust and obligation in relation to any information relating to an identified or identifiable individual (data subject). Management is responsible to comply with privacy in accordance with its privacy policy or applicable privacy laws and regulations.”
Privacy audits go beyond traditional IT audits in that the entire information life-cycle process needs to be considered. This includes not just the controls relating to how it was gathered and secured, but also how it is collected, used, and retained. Specifically, privacy audits address the following three concerns:
-
What type of personal information is processed and stored?
-
Where is it stored?
-
How is it managed?
A privacy audit should consider what privacy laws are applicable to the organization. Auditors should consider who has responsibility for privacy within the organization. This includes the roles of legal counsel and whether a chief privacy officer (CPO) role is established. (The CPO is a senior-level position responsible for the overall management of an organization’s privacy program.) Finally, the policies and procedures specific to privacy should be examined. Table 5-2 provides examples of privacy principles that can be implemented through privacy controls and processes.
TABLE 5-2 The Generally Accepted Privacy Principles.
| Principle | Description |
|---|---|
| Management | The entity defines, documents, communicates, and assigns accountability for its privacy policies and procedures. |
| Notice | The entity provides notice about its privacy policies and procedures and identifies the purposes for which personal information is collected, used, retained, and disclosed. |
| Choice of consent | The entity describes the choices available to the individual and obtains implicit or explicit consent with respect to the collection, use, and disclosure of personal information. |
| Collection | The entity collects personal information only for the purposes identified in the notice. |
| Use and retention | The entity limits the use of personal information to the purposes identified in the notice and for which the individual has provided implicit or explicit consent. The entity retains personal information for only as long as is necessary to fulfill the stated purposes. |
| Access | The entity provides individuals with access to their personal information for review and update. |
| Disclosure to third parties | The entity discloses personal information to third parties only for the purposes identified in the notice and with the implicit or explicit consent of the individual. |
| Security for privacy | The entity protects personal information against unauthorized access. |
| Quality | The entity maintains accurate, complete, and relevant personal information for the purposes identified in the notice. |
| Monitoring and enforcement | The entity monitors compliance with its privacy policies and procedures and has procedures to address privacy-related complaints and disputes. |
