Chapter 7
Mobile Applications and Silverlight
Globalization, advancement in the wireless technology infrastructure, and increased market competition have forced enterprises to break the physical boundaries of the organization and implement the concept of the virtual organization. Enterprise mobility is a strategic component of virtualized global organizations. Even though Microsoft hasn't released Silverlight for Mobile yet, I cannot end this book on the development of enterprise RIAs without discussing the following:
The role of mobile applications in Enterprise 2.0
Basic concepts and architecture components for mobile applications in general
The latest updates on Silverlight for Mobile and potential capabilities of Silverlight to develop RIAs for the mobile platform
This chapter starts with an overview of enterprise mobility and its key components to understand the role of mobile applications in Enterprise 2.0. Later the chapter will focus on the development of mobile applications by covering the basics of developing enterprise-level mobile applications, main architecture components, key design considerations, and different data synchronization models for mobile applications. Microsoft Silverlight could become a key strategic technology component to implement enterprise mobility. I will end the chapter by covering potential capabilities of Silverlight for developing mobile applications.
Note When I started writing this book, it seemed pretty certain that Microsoft was going to release the first preliminary version of Silverlight for Mobile—Silverlight 1 for Mobile—which in the end remained a private release. Microsoft is now focused on releasing Silverlight 2 for Mobile sometime in 2009, so at the time of writing, there is no product to work with.
Enterprise Mobility for Enterprise 2.0
We can define enterprise mobility as the following:
Enterprise mobility represents the ability of organizations to transform from a traditional organization to a virtual organization. Enterprise mobility enables globally distributed and diversified interorganization and intraorganization teams to access, collaborate on, and process information and execute different business processes utilizing wireless satellite networking–based information systems and services.
Innovation and calculated risks toward implementing enterprise mobility will help organizations to remain strategically ahead in the market. Enterprise mobility will improve the overall productivity, customer satisfaction, and ROI of the virtual organization. System and application virtualization, virtual meeting space, and mobile applications supporting online/offline mode are key components of enterprise mobility and thus virtual organizations.
System and Application Virtualization
System virtualization and application virtualization are two key buzz words for Enterprise 2.0, and they introduce modularity, mobility, scalability, and maintainability in the development and deployment of applications and services.
System virtualization provides system-level virtualization (including the operating system), while application virtualization decouples application installation and execution from the core operating system. Microsoft (http://www.microsoft.com/systemcenter/appv/default.mspx), VMware (http://www.vmware.com/), and Citrix (http://www.citrix.com) are a few of the leading providers of different product suites for enabling system and application virtualization.
Meetings are essential to build consensus and make strategic decisions to achieve organizations' objectives. Face-to-face meetings are more effective and efficient, which is a challenge for virtual organizations since team members are located at different locations and working in different time zones across the world. The virtual meeting space is an innovative approach to overcoming this problem.
The virtual meeting space concept started with teleconferences. Teleconferencing allows voice collaboration over the telephone. Next, computer desktop sharing enabled team members at dispersed locations to share applications, documents, and presentations over a network. Microsoft SharedView (http://connect.microsoft.com/site/sitehome.aspx?SiteID=94) and Cisco WebEx (http://www.webex.com/) are a couple examples of desktop collaboration tools.
The next natural progression is video conferencing, whereby you can collaborate using audio and video across the network, enabling virtual meetings. Recent advancement in wireless technology has enabled full-featured video collaboration studios to provide real-time face-to-face meetings among virtually located teams. HP Halo (http://www.hp.com/halo) is a great example of creating an advanced virtual meeting space for effective audio and video collaboration.
Mobile applications are a prerequisite for any organization supporting a globally distributed community. Mobile application development and infrastructure setup is one of the strategic directions for any organization. Initially, organizations started with very basic mobile applications that provided functionality such as maintaining tasks and organizing an address book for mobile devices. Later, the scope expanded to e-mail management on mobile devices. Research In Motion (http://www.blackberry.com/) dominates the market by providing efficient e-mail management on its Black-Berry devices.
The Apple iPhone (http://www.apple.com/iphone/) has ushered in the second generation of mobile devices. Along with advanced mobile devices, a second-generation mobile technology platform such as Silverlight will help to bring revolutionary changes in the mobile market. Organizations will be able to develop RIAs and smart client applications for mobile devices, virtually connecting team members effectively and increasing overall productivity. The advanced mobile applications will ultimately help organizations to achieve increased ROI by providing effective enterprise mobility.
Mobile applications are unique in nature in terms of usage scenarios and required technology capabilities:
From a usability and requirements point of view, users need access to an organization's systems to perform different types of operations while they are on the move. While connected (online), users expect to be able to carry out a wide range of operations mainly related to accessing and processing different types of information available in different formats and perform data validation and transactions to execute business processes. While disconnected (offline), users would prefer to have access to critical information (locally cached) and perform a limited set of critical operations that later can be synchronized with the main system while they are connected to the network.
From a technology prospective, mobile devices are usually portable and lightweight with very limited technical capabilities in terms of processing power, available processing and storage memory, browser capabilities, bandwidth availability, and continuous connectivity (signal strength). Compared to desktops and laptops, mobile devices have a much smaller screen size (with different sizes for different types of mobile devices) and lower resolution. In addition, mobile devices have extra capabilities such as voice integration and messaging features that can be utilized to develop simplified, yet effective mobile applications.
In Chapters 3 and 4 we discussed the seven key principles—usability, flexibility, simplicity, reusability, scalability, maintainability, and security—for developing, deploying, and distributing SOA-based, loosely coupled, collaborative RIAs. The question is, can we develop SOA-based mobile applications and apply the same principles to develop, deploy, and distribute them?
The answer: mobile applications can be SOA-based RIAs following the seven key principles. You can use the same design concepts, technology, and development tools for desktop, web, and mobile application development. However, the requirements and environment for mobile applications are different from those for desktop and web applications. The ideal approach would be to use a device-agnostic common application framework and develop loosely coupled components and services to support different requirements for different flavors (mobile, web, and desktop versions) of the same application rather than creating separate applications.
Now let's take a look at the basics of mobile applications in terms of the seven key principles that can help to achieve the previously mentioned application implementation goals.
You should consider the three dimensions—effectiveness, efficiency, and satisfaction—of usability (discussed in Chapter 4) during the requirements analysis, technology selection, architecting/designing, and implementation of mobile applications to provide maximum customer satisfaction.
User Interface Design Challenges
During mobile application user interface design, you need to consider key questions such as "Can I get to it?", "Can I figure it out?", "Is it fast enough?", "Does it have what I want?", and "Are my identity and information secured?". These are related to the three dimensions of usability. Getting answers to these types of questions will play a key role in terms of screen design due to some unique challenges we face during mobile application design and implementation.
During the user interface design process for mobile applications, designers should consider and accommodate the following unique characteristics of mobile devices:
Mobile screens are much smaller in size with less screen resolution compared to regular desktop/laptop screens.
There are no consistent standards on mobile screen size and screen resolution; you will find a variety of screen sizes and screen resolutions across different mobile devices.
Many mobile devices come with touch screen capability. As a result, mobile applications should support mobile devices with and without touch screen capabilities.
Both portrait and landscape mobile screens need to be supported.
Keyboards of mobile devices are not consistent and much smaller in size than conventional keyboards.
Along with these unique characteristics, the usage of mobile devices is also unique. Mobile devices are usually used to remain connected while you are away from your office or home and do not have easy access to your regular computer system. You need to access only key information (data and documents) to maintain your awareness and perform only critical but simplified operations to void your absence. You do not need to access all your information nor perform all your regular operations while you are away from the workplace.
To support the preceding considerations and features, you need to define a lightweight, simplified user interface that can provide a high-performing experience with the limited operating resources, memory resources, and bandwidth of mobile devices.
As discussed in Chapter 4, flexible applications have three main characteristics—they are platform independent, loosely coupled and customizable, and have support for agility. These cover most of the criteria that make an SOA-based application.
It is important to perform a thorough analysis of users' expectations, requirements, business processes, and security requirements to identify common patterns and functionalities. With the use of an advanced technology platform such as Silverlight, you can capitalize on the identified common patterns. The common patterns help you implement modular and abstracted components, lightweight and decoupled application services, and a set of templates and standards as a part of the core framework. This will give you a flexible and reusable development platform across mobile and desktop RIAs.
Different mobile devices also have different flavors of browsers with different capabilities. You should consider and analyze mobile browser capabilities for the mobile devices your application needs to support. Based on the browser capabilities, you should design the presentation layer and services integration.
Scalability and Maintainability
High scalability and reliability of enterprise wireless networking are critical success factors for supporting enterprise mobility. Wireless network behavior is different from traditional wired network behavior, and you have different types of challenges to support. In addition to the three key dimensions of the scalability—volume, software, and hardware—discussed in Chapter 4, for enterprise mobility you also need to consider the carrier as the fourth dimension.
Enterprises need to implement a scalable environment that can provide maximum wireless signal strength at every location, which is called carrier scalability, to provide high-performing mobile application services. The enterprise needs to consider these four dimensions to support low-profile mobile devices, remote locations, and a high volume of mobile users.
A highly scalable and high-quality software and infrastructure environment will improve the overall reliability of mobile applications with high performance and high accessibility at any location. Increased reliability helps to improve overall supportability and thus maintainability of mobile applications. Enterprises should also consider continuous monitoring and proper instrumentation of mobile applications to predict future usage, future problems, and future end users' needs. Thus the monitoring dimension helps organizations to maintain and improve the quality of their products.
Mobile Device Management (MDM) tools installed on mobile devices help enterprise administrators to maintain and monitor those devices, as well as to manage the software and distribution of upgrades across different types of mobile devices. MDM tools also aid in reporting errors from mobile devices to a centralized location, thereby helping to improve overall fault management.
Enterprises need to implement challenging but feasible enterprise mobility security policies. These policies need to align with enterprise IT security policies to implement mobile device security, information security during data transmission, and enterprise network security. You can implement five dimensions—information security, identity management, software security, infrastructure security, and regulatory compliance—of IT security (discussed in Chapter 4) to facilitate enterprise mobility in a secured environment.
Use of MDM tools, password protection, virus protection, lost device protection (disabling or formatting mobile devices), device encryption, and data encryption are a few examples of different ways to provide mobile device security.
The enterprise should consider alignment of the mobile application environment with enterprise security standards such as firewall implementation and access to enterprise servers through a Virtual Private Network (VPN) to provide an end-to-end secure environment. Signal and data transmission security is essential for the wireless network. The enterprise should also consider applying security standards such as Advanced Encryption Standard (AES), identity management, and data encryption.
This section details key architecture considerations for developing mobile applications. The team should consider the following factors when finalizing the architecture and implementing the design and development of any mobile application:
Features and capabilities of mobile devices to support—operating systems and browser support and availability of processing and storage memory
Wireless network coverage area
Overall available average signal strength and bandwidth
Enterprise product roadmap, technology roadmap, infrastructure setup, and security policies
Business requirements, user expectations, and mobile application scope—application feature availability in online/offline mode
Developed application deployment features—application footprint, technology platform used for development, data storage requirements
Cost of deployment and maintenance
You can develop four types of mobile applications: rich client, smart client, web client, and RIA. Which type of mobile application is chosen depends on the requirements of the application, the capabilities of mobile devices that need support, the size of application installation and resource requirements, available bandwidth, and coverage of wireless network.
Rich Client Mobile applications
Rich client mobile applications, as well as related data and configurations, are installed on the mobile device. Mobile games and other basic applications are examples of rich client applications. The following are characteristics of rich client mobile applications:
All processing work is performed within the mobile device.
No network connectivity is required to run the application. All application features are available to mobile users in online/offline mode.
There are no dependencies on mobile device browser capabilities, signal strength, and bandwidth.
The application is distributed to all mobile users. The complete application is installed and configured on the mobile device.
Application-related data is stored within the mobile device.
Administrators can maintain and monitor the application with the use of MDM tools.
Application security is dependent on default mobile device security and data encryption.
Smart Client Mobile applications
As with rich clients, smart client mobile applications are also installed on the mobile device. Related data and configurations are stored locally within the mobile device as a local cache. The key difference between the rich client and the smart client is that the latter's main data repository is a central data repository. The smart client application data synchronization service will synchronize the local cache with the central data repository periodically while connected. One of the best examples of a smart client application is the e-mail management application. The following are characteristics of smart client mobile applications:
Most of the processing work is performed within the mobile device.
Constant network connectivity is not required to run the application. All or some application features are available in offline mode.
Users can enable offline application mode even if they are connected to the network.
While working on the application in offline mode, there are no dependencies on mobile device browser capabilities, signal strength, and bandwidth.
In connected mode, data will synchronize with central data storage (two-way synchronization) using the synch service client.
While working in connected mode, the synchronization performance depends on the signal strength, bandwidth, and size of data to be synchronized.
The application is distributed to all mobile users. The complete application is installed and configured on the mobile device.
Application-related data is stored within the mobile device as a local cache.
Administrators can maintain and monitor the application with the use of MDM tools.
Application security is dependent on default mobile device security and data encryption. Data synchronization security depends on implemented data transmission security and enterprise network security.
Web Client Mobile Applications
The web client mobile application is a browser-based application installed on central servers. The application accesses the data from the centrally hosted database. Related configurations might be stored locally within the mobile device. Unlike the rich and smart client applications, the web client application is functional only in connected mode. The following are characteristics of web client mobile applications:
All processing happens on the server side.
Constant network connectivity is required to run the application. No application features are available in offline mode.
Application performance depends on browser capabilities, application design, enterprise-deployed environment, signal strength, bandwidth, network latency, size of data, and number of required round-trips.
The application is browser based and deployed centrally on the servers, so there is no need to distribute it to all mobile users.
There is no local data cache. The required configuration can be stored on the mobile device.
Administrators can centrally maintain and monitor the application.
Application security is dependent on default data transmission security and enterprise network security.
Rich Internet Mobile applications
Similar to the web client application, the rich Internet mobile application is a browser-based application installed on central servers. This type of application accesses data from a centrally hosted database. Related configurations might be stored locally within the mobile device. The key difference between the rich Internet application and the web client mobile application is that the former is developed using platforms such as Silverlight to support Enterprise 2.0 requirements. All characteristics of the web client mobile application are applicable to the rich Internet mobile application. The following are additional or enhanced characteristics of rich Internet mobile applications:
Most of the processing work is performed on the server side.
An advanced plug-in is required to be installed on the mobile device to run the application. All existing mobile devices cannot otherwise support rich Internet mobile applications.
All existing browsers are not compatible with these types of applications.
Based on the application design and mobile device capabilities, a rich Internet mobile application may support limited functionality in offline mode using the local cache.
While working in the application in offline mode, there are no dependencies on the signal strength and bandwidth.
In connected mode, the data may synchronize with central data storage (two-way synchronization) using a synch service client.
While working in connected mode, the synchronization performance depends on the signal strength, bandwidth, and size of data to be synchronized.
Based on the application design, configuration is stored on the mobile device.
Administrators can centrally maintain and monitor the application.
Based on the preceding discussion, Table 7-1 details the comparison between mobile application types and the seven key principles of SOA. The comparison indicates in relative terms how successfully you can achieve the SOA principle. "High" means you can achieve the specific SOA principle maximum relative to other mobile application types, whereas "Low" means you have the least chance of achieving the principle.
Table 7.1 Mobile Application Types and the Seven Key Principles of SOA
| SOA Principle | Mobile Application Types | ||||
| Rich Client | Smart Client | Web Client | Rich Internet | ||
| Usability | High | High | Medium | High | |
| Simplicity | Medium | Low | High | High | |
| Flexibility | Medium | Medium | High | High | |
| Reusability | Low | Medium | Medium | High | |
| Scalability | Low | Medium | High | High | |
| Maintainability | Low | Low | High | Medium | |
| Security | High | High | High | High | |
Mobile applications need to perform communication between mobile devices (clients) and the enterprise server to execute different actions and events, send notifications and messages, and perform information exchange and data synchronization. There are two main communication models—push model and pull model—based on the enterprise system architecture, application implementation approach, and business requirements.
In the push architecture model, central servers will automatically deliver messages to all or selective client devices to communicate specific information or perform specific actions. If the targeted mobile devices are not connected or available within the network range, the messages for those devices remain undelivered and in a queue. The next time the device establishes the connection, the queued message will be delivered automatically.
Figure 7-1 defines the push architecture model for performing communication between the server and mobile devices.
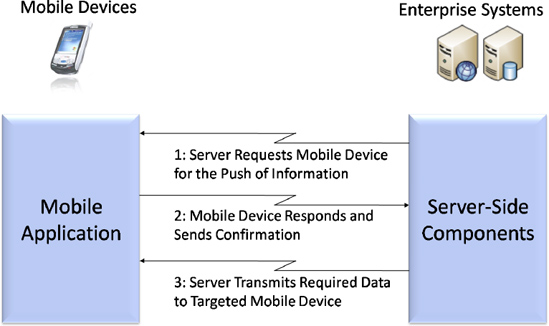
Figure 7.1 Push architecture model
As shown in Figure 7-1, first the server requests the mobile device for the push of the required information. If the device is within the coverage area and is connected to the network, the server receives the confirmation. Next, the server transmits the required data to the targeted mobile device.
It is apparent from the preceding discussion that the implementation of the push model is slightly complex, and we need to think of security considerations to help us define the right push model. The users targeted for automated communication can be determined by an enterprise user provisioning system (e.g., Active Directory for all organization employees) or by a subscription model. A push can increase the overall network traffic, depending on the number of mobile users requested by the push and the number of users connected to the network. The enterprise should consider this factor during system architecture design.
The key benefit of the push model is that mobile users do not need to check for updates or undelivered information. You can also implement strict policies via the push model; for example, if a user has not installed a critical patch after a set duration, you disable the device upon next connection to the network. Usually, enterprises implement the push model for critical features and applications such as application version management, security patches, device monitoring features, e-mail management, personal calendar, and contact management.
The pull architecture model and implementation is much simpler compared to the push model. In the pull architecture model, the user (and thus mobile device) initiates the data transmission request from the server. Figure 7-2 defines the pull architecture model for performing communication between the mobile device and the server.
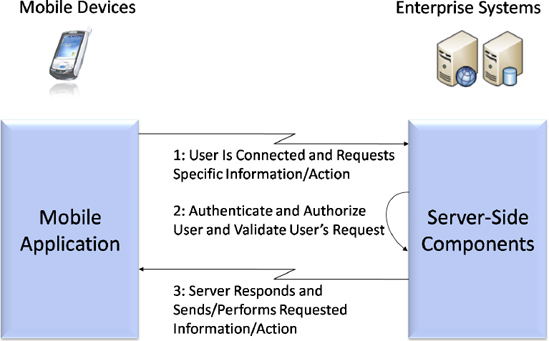
Figure 7.2 Pull architecture model
As shown in Figure 7-2, while the user is connected to the network, he or she (and thus the mobile device) initiates a request to receive information. When the server receives and validates the request, it transmits the requested data to the targeted mobile device.
It is apparent from the preceding discussion that the pull model is a user-controlled approach and is easy to implement. The enterprise will need to implement a security model to authenticate and authorize the user and validate the user's request. Since it is a user-controlled approach, the overall network traffic is usually limited (all users do not make requests at the same time) and thus will be easier to maintain and monitor.
The key disadvantage of the pull model is it is user controlled, and there is no guarantee that all users have received the required information or updated the mobile device by a given time. However, most of the day-to-day mobile application operations and events are user driven, and thus the pull model is the best approach for implementing a communication pattern for noncritical operations.
The smart client and rich Internet mobile applications support application functionality while the user is not connected to the network or chooses to work in offline mode. While the user is disconnected from the network, he or she can perform different actions (as well as make changes to information). Similarly, while the user is in disconnected mode, there can be several changes in the server-side database or a few server-side requests submitted for specific users. Synchronization agents manage the actions taken using either asynchronous or synchronous mode. In addition, there are three major architectural synchronization models: store-and-forward, database synchronization, and file replication.
Store-and-Forward Synchronization Model
The store-and-forward synchronization model represents asynchronous messaging queue features between client and server for error-free actions and information exchange. It's a well-proven information-exchange messaging model usually used to implement stable and reliable enterprise mobility. This model keeps actions and related information as messages in the queue on the server or client side while disconnected. When a connection is established between the client and server, the queued messages are transmitted asynchronously as part of a transaction to keep the message and related information intact. If the connection is lost in the middle of the transaction or, due to some server-or client-side problem, the message could not be transmitted successfully, the message and related data is not lost; upon the next connection, the same message will be transmitted.
Figure 7-3 demonstrates the high-level architecture of the store-and-forward synchronization model. As shown in the diagram, you can implement the push model or automatic synchronization model.
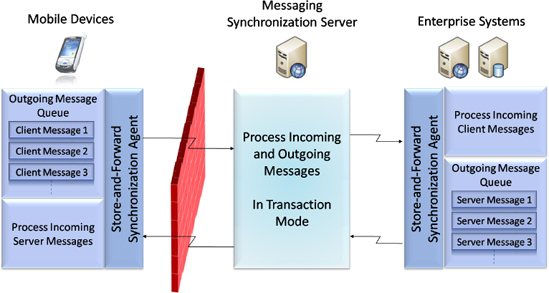
Figure 7.3 Store-and-forward synchronization model
Smart client and rich Internet mobile applications can use the store-and-forward synchronization model to support offline mode.
Database Synchronization Model
The database synchronization model performs traditional database synchronization and replication using different technologies or any available synchronization framework/platform. If changes are made in the database on the client or server while the client is in offline mode, upon connection a conflict occurs, and the synchronization agent will synchronize the updated records. You can implement the default last-in-first-win or first-in-first-win synchronization models or implement a custom conflict resolution model for user-driven synchronization.
If there is more than one user performing the transaction to update the same record at the same time, in the last-in-first-win conflict resolution model, the last committed transaction will remain as the final accepted value. In the first-in-first-win conflict resolution model, the database record is usually locked for the user who first tries to attempt the change, and the updated value will be saved. If other users attempt to change the value at the same time, they cannot update that particular record.
Figure 7-4 demonstrates the high-level architecture of the database synchronization model.
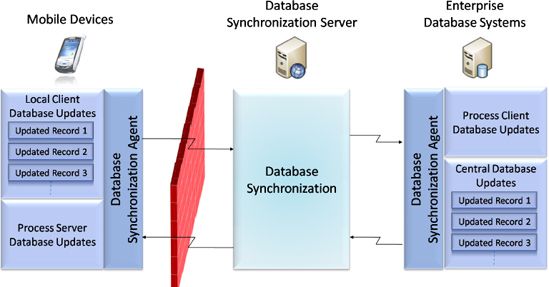
Figure 7.4 Database synchronization model
Smart client and rich Internet mobile applications can use the database synchronization model to support offline mode. You can implement a hybrid approach involving the store-and-forward synchronization model and the database synchronization model to provide effective solutions.
Files/Document Synchronization Model
The files/document synchronization model ensures that the client and the server have the same versions of files that were changed in connected or offline mode on the server or client side. Based on the application requirements and synchronization solution you are using, you may or may not need a file synchronization server.
Figure 7-5 demonstrates the high-level architecture of the file/document synchronization model.
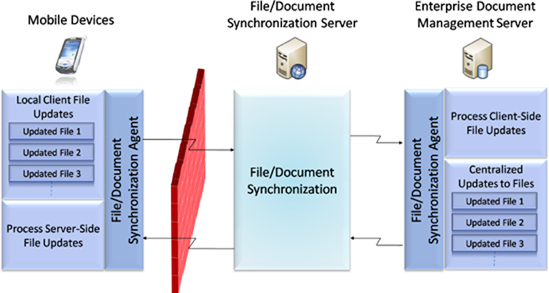
Figure 7.5 File/Document synchronization model
Smart client and rich Internet mobile applications can use the file/document synchronization model to support offline mode. You can implement a hybrid approach involving the store-and-forward synchronization model, the database synchronization model, and the file/document synchronization model to provide effective solutions.
Mobile Application Design Considerations
As discussed earlier, because mobile applications are unique in nature, you need to consider different factors and apply a different strategy during the design and development of mobile applications than you would for desktop or web applications. This section will provide a brief overview of different factors the design team should consider during mobile application design and development.
Making a Decision: Defining the Platform
We discussed three core architecture platform components for mobile applications—mobile application types (rich client, smart client, web client, rich Internet), communication patterns (push and pull models), and synchronization models (store-and-forward, data synchronization, file/document synchronization). First of all, the architect and design team needs to define the mobile application platform and decide on the core architecture platform components.
The technical team should do the following:
Perform extensive requirements analysis.
Evaluate the existing wireless network infrastructure and possibilities to expand it as part of the current development phase or in the near future.
Define the number of users to support and areas to cover (to understand the availability of network and bandwidth).
Understand the capabilities of the mobile devices to be used.
Define mobile operating systems and browsers to support.
Align the proposed approach with the organization's strategic product and technology road maps.
Develop required prototypes.
Based on the preceding analysis, the technical team can make a decision on the mobile application platform and present the proposed mobile solution architecture to the leadership team to receive approval.
Simplified User Interface Design
It is important to follow the "keep it simple" concept of SOA (discussed in Chapter 4) and design a simplified user interface that can meet the unique challenges of mobile applications that we discussed earlier in this chapter. When designing the user interface, you should consider the operating systems and browsers that you will support. Different operating systems and different browsers have different capabilities.
The following are do's and don'ts to consider while you are designing the user interface for mobile applications to provide a clear, concise, and readable user interface:
First the do's:
Make the user interface simple and consistent.
Ensure the interface fits and adjusts to different screen sizes and screen orientations.
Ensure user actions are compatible with keyboard, stylus, and touch screen input.
Design for easy navigation from one screen to another.
Aim to limit the number of text-entry screens. You want such screens to be fewer compared to those in an application for a regular computer system (as it is difficult to type on mobile devices).
Use a font size and font type suitable for mobile device screen sizes.
Include proper background and foreground color contrast.
Consider different language support (impact of globalization and localization).
Focus on "users, users, and users." User requirements should be analyzed and validated before implementation.
Now the don'ts:
Make the user interface very rich, heavy, jazzy, and complex.
Include large horizontal and vertical scrollbars.
Provide long and complex wizard-like approaches with multiple round-trips to servers.
Require frequent refreshes of the complete screen.
Display too much information on a small screen.
Mobile Devices resources Management
Mobile devices have limited resources in terms of processing power (CPU), processing memory, storage memory, network connectivity, bandwidth, and battery strength compare to regular PCs. These limitations make support for more than one type of mobile device complex for a single application, because different mobile devices come with different resource capabilities.
The application design team needs to first define the matrix of supported mobile devices vs. device configuration (resources) to determine the minimum available device resources that need to be supported by the mobile application. The following is a list of high-impact items that consume one or more resources heavily and thus can have a negative impact on the availability of overall resources:
Rich, heavy, jazzy, or complex user interface
Media-driven (e.g., audio and video) applications
Frequent client-server round-trips
High number of required data transactions
Complex business and validation logic execution
Complex algorithms to support different business processes
Large documents
Heavy synchronization features
Large application footprint
Client-side processing
Voice features
The following mobile application features will consume more resources based on the usage of these features by users:
Voice features
Video or camera
Media player and photo album feature
Internet usage
Backlight feature
The application design team must analyze the features required for the mobile application and should make efforts to define a simplified application that balances the required features, richness of experience, and complex business issues.
Communication Protocols: SOAP and JSON
Wireless data transmission between mobile devices and a centralized server is critical for smart client, web client, and rich Internet mobile applications. SOAP and JSON are widely used messaging protocols for wireless data transmission. Both are lightweight and, depending on the situation, one is usually better than the other for providing data transmission.
As you saw in Chapter 4, SOAP, which is based on XML, allows us to use structured messages. As a reminder, a SOAP-based message consists of an envelope and optional header, a body, encoding rules, and an RPC representation. By contrast, JSON is a lightweight data-interchange language using a text format. It is based on a subset of JavaScript.
Compared to SOAP, JSON is more simplified and lightweight and is most suitable for simple and straightforward data transmission. SOAP represents a more descriptive and structured message format that is more suitable for complex data transmission and developing generic SOA-based reusable services.
Preparing for Possible Disasters
Mobile devices deal with many unpredictable, potentially disastrous scenarios compared to desktops. Some examples of such scenarios are the following:
The mobile device loses power and the device is shut down.
The mobile device is running on low battery power and some high-power consuming features are disabled.
The user switches off the mobile device.
The mobile device is in an out-of-network area.
Low signal strength results in operation timeout.
The user takes the device offline.
The user interrupts the existing operation to utilize other features of the mobile device.
The application design team needs to consider different types of problematic scenarios and implement a disaster recovery and self-healing plan for when the application cannot finish its actions.
Silverlight for Mobile Applications
Silverlight is designed for us to develop and deploy cross-platform, cross-browser, and cross-device RIAs. This capability focuses on support for traditional computer machines and mobile handheld devices with different hardware configurations, operating systems, and web browsers. As you learned in earlier chapters, Silverlight 2 is an enterprise-enabled technology platform for developing SOA-based RIAs. This section focuses on how Silverlight can support enterprise mobility by developing SOA-based RIAs for mobile devices.
Silverlight Is Based on the .NET Framework
The main advantage of the Silverlight technology platform is that it is based on .NET Framework 3.5. As a result, the XML-based, loosely coupled presentation layer can be built upon WPF XAML, and all the processing can be implemented by integrating code-behind managed .NET assemblies and web services. The integration of Silverlight for Mobile with the .NET platform makes it easy to develop mobile applications that can support the seven principles of SOA-based applications.
This inherent capability makes Silverlight the right development platform for enterprises to develop RIAs for PCs and mobile devices.
Same Silverlight Applications for Desktop RIAs and Mobile RIAs
The following aspects of Silverlight provide opportunities for supporting the different and unique considerations that desktop RIAs and mobile RIAs have:
Use of XAML for user interface design
Vector graphics capabilities for developing a flexible user interface supporting different screen sizes and screen resolutions
Loosely coupled and service-oriented implementation capabilities
Reusable managed code integration
In addition Microsoft provides the same set of development tools—Visual Studio, Expression Blend, Deep Zoom Composer—for desktop and mobile RIAs. Visual Studio will also facilitate a Silverlight mobile application emulator for debugging Silverlight-based RIAs.
Based on the preceding discussion, it is safe to say that after a careful evaluation and analysis of requirements and an SOA-based architecture definition, an enterprise can develop and deploy a single RIA that can support both desktops and mobile devices. If the requirements are too different, Silver-light enables developers to reuse different components and services for desktop and mobile RIAs.
Where Do We Stand with Silverlight for Mobile?
Now the key question is, after exploring the promising capabilities of the Silverlight technology platform, where does Microsoft stand on Silverlight for Mobile today?
When I started writing this book, it seemed certain that Microsoft was going to release the first version of Silverlight for Mobile—Silverlight 1 for Mobile. Promising mobile RIA demonstrations based on Silverlight 1 for Mobile were presented during the Mix 2008 and TechEd 2008 conferences. Along with the support for Windows mobile phones, Nokia announced support for Silverlight 1 in its Series 60 mobile devices.
Silverlight 1 for Mobile was mainly based on JavaScript (as was the original Silverlight 1 release for the desktop), with more focus on media presentation, and was not fully integrated with the Visual Studio development tools. Even with the preliminary basic version of Silverlight 1 for Mobile, the different demonstrations presented promising capabilities for implementing RIAs for mobile devices.
However, Microsoft decided to keep Silverlight 1 for Mobile as a private test release. It is not available publicly for production development and deployment of Silverlight 1 for Mobile RIAs.
SOME SILVERLIGHT 1 FOR MOBILE–RELATED LINKS
To view a presentation on Silverlight 1 for Mobile presented during Mix 2008, visit http://sessions.visitmix.com/, click MIX08, and search for "Silverlight Mobile."
To get more information on the Nokia Series 60 device with the support for Silverlight, visit http://www.nokia.com/A4136001?newsid=1197788.
As mentioned on the Microsoft Silverlight web site at http://silverlight.net/learn/mobile.aspx, Microsoft is aiming to publicly release the next version of Silverlight for Mobile—Silverlight 2 for Mobile—sometime in 2009. Silverlight 2 for Mobile will be compatible with Silverlight 2 for the desktop and will utilize all the features mentioned previously for developing managed SOA-based RIAs for the mobile devices.
Based on the available information, Nokia Series 60 mobile devices (and probably Samsung mobile devices on which the PDC 2008 demonstration was based), along with Windows-based mobile phones, will support Silverlight 2 for Mobile initially. The requirement will be to have the Silverlight 2 plug-in installed on the mobile devices (as on desktop machines). Mobile device operating systems that allow us to install the Silverlight plug-in will be able to safely run Silverlight-based RIAs.
From the enterprise point of view, it is always good to use a consistent set of development tools that support a broad range of application types to develop applications and services that can be reused across applications. Using the Silverlight development platform, enterprises can achieve this objective. It will be possible to develop and debug Silverlight-based desktop RIAs and mobile RIAs using the same set of Visual Studio development tools. However, as mentioned, mobile applications are unique in nature and are generally used for purposes different from those of desktop machines. Thus it is critical to consider all the design considerations for mobile applications discussed in this chapter before making the decision to use the same RIAs for both types of devices.
SOME SILVERLIGHT 2 FOR MOBILE–RELATED LINKS
Continue visiting the Silverlight site (http://silverlight.net/learn/mobile.aspx) to get the latest information and updates on Silverlight for Mobile.
Get information on different demonstrations presented during PDC 2008 on the MSDN Team Blog for the Mobile Developer Group by visiting http://blogs.msdn.com/mobiledev/archive/2008/11/03/let-s-review-the-pdc-silverlight-2-for-mobile-demos.aspx.
Visit http://sl.weatherbug.com/ to see a demonstration of WeatherBug, a Silverlight 2 for Mobile application. This application was presented originally during MIX 2008 using Silverlight 1 for Mobile.
As enterprises embrace the Enterprise 2.0 concept and become global, the necessity of implementing a virtual enterprise to support employees and customers around the world is increasing. Advanced wireless technology, network capabilities, and virtual and mobile application development platforms enable implementation of enterprise mobility. We started this chapter by exploring the concept of enterprise mobility for Enterprise 2.0 and discussed the key components—application and system virtualization, virtual meeting space, and mobile applications—of enterprise mobility.
The latter part of the chapter mainly focused on giving you an overview of mobile applications and architectural considerations for developing mobile applications. As explained, mobile applications are different in many ways (screen size, screen resolution, device resources, usage scenarios, operating system and browser capabilities, network connectivity, and available bandwidth) from regular PCs. Advanced mobile devices and mobile application development tools enable enterprises to develop and deploy SOA-based mobile applications following the seven principles of SOA-based applications.
Enterprise architects and the development team should perform a thorough analysis and develop the required prototypes and user acceptance testing before deploying mobile applications on a large scale. Based on user requirements and expectations, the team should decide whether to develop a rich client, smart client, web client, or rich Internet mobile application. A simplified user interface that supports the required mobile device platform is the recommended approach. The footprint and complexity of mobile applications should be balanced with what features a mobile device supports, and the application should utilize the minimum of resources possible to provide a high-performing user experience.
At the end of the chapter, we looked at the future of Silverlight for Mobile. As demonstrated by a number of applications in different conferences using Silverlight 1 and Silverlight 2, I am confident that Silverlight 2 for Mobile will be a promising, scalable, rich Internet mobile application development platform for enterprises looking to support enterprise mobility. Silverlight 2 for Mobile is scheduled to be released in 2009; I can hardly wait until then to start developing mobile RIAs using Silverlight 2 for Mobile.
In the next and final chapter of the book, I will give some practical advice and tips on how to adopt Silverlight technology in your enterprise.
