Chapter 5. Programming the COBOL Business Logic
In this chapter:
You are now ready to write the COBOL code of the sample application. This chapter describes:
Writing CICS programs in COBOL
Dealing with file handling in CICS programs
Saving data using a scratchpad facility
Moving control from one program to another in the application
The queuing facilities of temporary storage and transient data
Handing errors in you programs
Writing CICS Programs in COBOL
The source programs are listed on the CD-ROM that is packaged with this book. They include a step-by-step description of what the code does. This chapter is about programming the business logic component, other services including Basic Mapping Support (BMS), the CICS supplied services for formatting a green screen, are described in “Programming the 3270 Presentation Logic Component” in Chapter 11.
Invoking CICS Services
When you need a CICS system service—for example, when reading a record from a file—you just include a CICS command in your code. CICS commands look like:
EXEC CICSfunction[option(argument)][option...]... [terminator]
The options for this command are:
- Terminator
The terminator is language dependent. For COBOL, the reserved word is either END-EXEC or a period (full stop). The full stop option should be avoided since it ends a COBOL sentence. In PL/I, C, and REXX it is the semicolon.
Tip
This way of obtaining a CICS service is identical for PL/I, C, System/390 Assembler, and REXX. However a different approach is used for C++ and Java—for more information see Chapter 7.
- Function
The function is the thing you want to do. For example, reading a file is READ, writing to a terminal is SEND. It must be the first value after EXEC CICS.
- Option
An option or parameter is some specification that’s associated with the function. The word option is slightly misleading since some of the options are mandatory. Options are expressed as keywords, some need an argument in parentheses after the keyword. The syntax is free format after the function; that is, the parameters (options) may appear in any sequence and layout in the code as shown in the following example:
EXEC CICS READ FILE(
filename) RIDFLD(data-area)* Resources[INTO(data-area) SET(ptr-ref)] LENGTH(data-area)* StorageKEYLENGTH(data-value) [GENERIC]* KeysSYSID(systemname) [RBA RRN DEBKEY DEBREC]* OptionsCONSISTENT REPEATABLE* OptionsUNCOMITTED UPDATE [TOKEN(data-area)]* Options[EQUAL GTEQ]* OptionsNOSUSPEND* ConditionsEND-EXEC* Terminator
For example, the options for the READ command include FILE, RIDFLD, UPDATE. FILE tells CICS which file you want to read, and is always followed by a value indicating or pointing to the filename. RIDFLD (record identification field), that is the key that tells CICS which record within the file to address, and likewise needs a value. The values are called arguments and must appear after the keyword within parentheses (brackets). UPDATE, on the other hand, simply means that you intend to modify the record and update it (thereby invoking the CICS transactional protection we discussed earlier) and has no argument associated with it.
So, to read into a piece of working storage named ACCTREC, with intent to update, a record from a file known to CICS as ACCTFIL, using a key that we’ve stored in working storage at ACCTC, the command could be coded like this:
MOVE 'ACCTFIL' TO LF-ACCTFIL EXEC CICS READ FILE(LF-ACCTFIL)* ResourceRIDFLD(ACCTC)* KeyINTO (ACCTREC)* StorageUPDATE* OptionEND-EXEC
When you specify a value, you can either use a character literal (enclosed in quotes), as we did for FILE above, or you can point to the name of a storage area that contains the value you want, as we did for RIDFLD above. In other words, we might have written:
EXEC CICS READ FILE(LF-ACCTFIL) UPDATE
INTO (ACCTREC) RIDFLD(ACCTC)
END-EXECinstead of our earlier command. If you use a literal, follow the usual language rules; for example, for COBOL put it in quotes unless it’s a number.
Data can be moved by CICS from and into your program storage by using the FROM and INTO options (also known as move mode) or you can access the data using a pointer together with the SET parameter (also known as locate mode).
You may be curious about what the compiler does with what is a rather English-like statement. The answer? The compiler doesn’t see that statement. Processing a CICS program for execution starts with a translation step. The CICS translator converts your EXEC CICS commands into native language statements; for example, for COBOL in the form of a CALL statement. You then compile the expanded source and link edit this in the normal way. By the way, in COBOL the generated statements never contain periods (full stops), unless you include one explicitly after the END-EXEC. This means you can use CICS commands within any COBOL construct such as IF or EVALUATE statements (by leaving the period out of the command), or you can end a sentence with the command (by including the period).
Differences from Standard COBOL Programs
The biggest difference between standard COBOL programs and CICS COBOL programs is that you don’t define your files in a CICS program. Instead, they are defined using FILE definitions that are stored in a CICS table, the File Control Table (FCT), which is covered in Handling Files later in this chapter. Other differences are:
You cannot use the entries in the ENVIRONMENT DIVISION and the DATA DIVISION that are normally associated with files. In particular, the entire FILE SECTION is omitted from the DATA DIVISION. Put the record formats that usually appear there in either the WORKING-STORAGE or LINKAGE sections. (WORKING-STORAGE is recommended because most COBOL programmers prefer it that way.)
You should not use the COBOL file processing verbs (such as READ, WRITE, OPEN, and CLOSE). Requests for operating system services are all made through CICS, so CICS takes care of opening and closing files for everyone using the system.
You should not use the COBOL console I/O verbs: ACCEPT and DISPLAY, because they interact with the operating system without CICS getting control.
Some statements and compiler functions produce code that is incompatible with the CICS environment. You must not use the STOP ‘literal’ form of that COBOL verb, because it stops not only yourself but everyone else who uses your CICS address space. In general, you cannot use language features and compiler options that need operating system services during execution. COBOL examples include ACCEPT, OPEN, and READ. There are similar restrictions in the other supported languages.
Because CICS is managing the shared environment:
Certain COBOL compiler options (for example, DYNAM, NOLIB, NORENT and NORES), should not be used. Use your installation’s standard setup.
You must take care with some functions (for example, SORT) which, if used, will stop the shared system being shared. There is a full list of the functions to be avoided in the CICS Application Programming Guide.
CICS COBOL programs should be usually short-running if data is shared. A batch COBOL program might process all records of a file; on the other hand, a typical CICS COBOL program processes just a few requests.
Handling Files
CICS allows you to access file data in a variety of ways. In an online system, most file accesses are random, because the transactions to be processed aren’t batched and sorted into any kind of order. Therefore CICS supports the keyed access method provided by VSAM. It also allows you to access data using a variety of database managers.
This book covers only VSAM Key-Sequenced Data Sets (KSDS) that are accessed by supplying a key. Other VSAM data set format types—Entry-Sequenced Data Sets (ESDS) and Relative-Record Data Sets (RRDS) are described in more detail in the CICS Application Programming Guide. CICS also supports sequential access to keyed files in several forms; one of these, browsing, is covered in the next section.
The most important information kept for each file is the symbolic filename (normally the MVS DDNAME) or the data set name. When a CICS program makes a file request, it always uses a symbolic filename. CICS looks up this name in the FCT, and from the information there it makes the appropriate request of the operating system. This technique keeps CICS programs independent of the specific resources on which they are operating.
In the examples that follow, we’ll use the symbolic filename ACCTFIL for the account file and ACCTNAM for the name file which is actually a path to the same data set via an alternate index on the last name (surname).
READ Commands
There are three READ commands:
- READ
Reads a record from a file.
- READNEXT
Reads the next record during a browse of a file.
- READPREV
Reads the previous record during a browse of a file.
The sample application uses the first two: READ and READNEXT as seen in Browsing a File, later in this chapter.
The command to read a single record from a file is:
EXEC CICS READ FILE(filename) INTO(data-area) LENGTH(data-area) RIDFLD(data-area)optionsEND-EXEC
The options for this command are:
- FILE(filename)
Specifies the name of the file that you want to access. It is required in all READ commands. The entry in the CICS File Control Table (FCT) is used to find out the characteristics of the data set and whether it is on a local or remote system. Filenames can be up to eight characters long and, like any parameter value, should be enclosed in quotes if they are literals.
- INTO(data-area)
Specifies the name of the data area into which the record retrieved from the data set is to be written. When INTO is specified, LENGTH must be specified or must be capable of being deduced from the INTO option. INTO is used in the sample application associated with this book.
- LENGTH(data-area)
Specifies the maximum number of characters where the record is to be put. The LENGTH parameter is required for access to variable record length files. After the READ command is completed, CICS replaces the maximum value you specified with the true length of the record. For this reason, you must specify LENGTH as the name of a data area rather than a literal. For the same reason, you must re-initialize this data area if you use it for LENGTH more than once in the program. An overlong record raises an error condition. For the uses of the READ command we’re covering in this book, the LENGTH option is not required because it is a fixed length file and can always be deduced from the INTO parameter.
- RIDFLD(data-area)
Specifies the record identification field. The contents can be a key, a relative byte address (RBA for an ESDS), or relative record number (RRN for RRDS). This parameter is also required.
Immediately upon completion of the command, the RIDFLD data area is available for reuse by the application program, even if UPDATE was specified.
- Other options (partial list)
Any of the following options which apply to this command can be used. Note that multiples of these may be used. Except where noted, you can use them in any combination.
- UPDATE
Means that you intend to update the record in the current transaction. Specifying UPDATE gives your transaction exclusive control of the requested record (possibly over a whole group of records known as a control interval if you are not using VSAM’s Record Level Sharing (RLS) facility). Consequently, you should use it only when you actually need it; that is, when you are ready to modify and rewrite a record.
- NOHANDLE
Means that you are going to handle all exceptional conditions that CICS may raise when processing your request. Modern usage is to use RESP and RESP2 instead.
- RESP(data-area)
Means that you are going to handle all exceptional conditions that CICS may raise when processing your request. This is an alternative to the older NOHANDLE option and requires a separate data area into which CICS places the value indicating success or otherwise in addition to the standard EIBRESP field in the EIB CICS that is always used. The EIB is explained in more detail in The EXEC Interface Block (EIB) in Chapter 11.
- RESP2(data-area)
Returns a value that may further qualify the RESP response; the data-area value mirrors the EIBRESP2 value in the EIB.
Using the READ Command in the Sample Application
In program NACT02, we need to find out whether the requested record is there. The command we use is shown in Example 5-1.
EXEC CICS READ FILE(WS-LITS-FILES-ACCOUNT)
INTO(NACTREC-DATA)
RIDFLD(ACCTDO IN NACTREC-DATA)
RESP(CA-CRUD-RESP) RESP2(CA-CRUD-REAS)
END-EXEC
IF CA-CRUD-RESP NOT DFHRESP(NORMAL)
* We may have a problem and the RESP2 field may contain more information
END-IFThe major return code will be placed in CS-CRUD-RESP and a qualifier may be supplied in CA-CRUD-REAS.
In this command, the record is placed in the data area named NACTREC-DATA so it should be a data structure corresponding to the account file record. You could define this structure directly in the program, but you’ll also need it in several other programs. So instead you should put the record definition into a library in NACCTREC and copy it into the NACCRUD copybook, which is then copied into the NACT02 program.
In NACCCRUD:
10 NACTREC-DATA.
COPY NACCTREC.In NACT02:
01 DFHCOMMAREA
COPY NACCCRUD.Here ACCTDO IN NACTREC-DATA is where the account number was passed by the frontend that called the program. NACTREC-DATA is the location where the data is to be passed back to the frontend program.
In any application, it is a good idea to keep your record layouts in a library and copy them into the programs that need them. Even in the simplest of applications, the same record is usually used by several programs. This procedure prevents multiple programs from using different definitions of the same thing.
This argument applies equally well to any structure used in common by multiple programs. Map structures are a prime example, as are parameter lists and communication areas, which we’ll discuss later. Apart from its value in the initial programming stage of an application, this technique greatly reduces the effort and hazards associated with any change to a record or map format. You can make the changes in just one place (your library) and then simply recompile all the affected programs. Example 5-1 also introduces the method of testing the major CICS return code. The CICS translator replaces the DFHRESP(condition) with the numeric return code so programmers are able to write intelligible code.
Example 5-2 shows the COBOL record definition we need of the account file in the sample application. Its fields are described beginning at the 20 level in order to allow it to be used within other structures.
20 ACCTDO PIC X(5). //Account number20 SNAMEDO PIC X(18). //Last/surname20 FNAMEDO PIC X(12). //First name20 MIDO PIC X. //Middle initial20 TTLDO PIC X(4). //Title e.g., Mr./Mrs.20 TELDO PIC X(10). //Telephone number20 ADDR1DO PIC X(24). //Address line 120 ADDR2DO PIC X(24). //Address line 220 ADDR3DO PIC X(24). //Address line 320 AUTH1DO PIC X(32). //Additional Authorized Card User 120 AUTH2DO PIC X(32). //Additional Authorized Card User 220 AUTH3DO PIC X(32). //Additional Authorized Card User 320 AUTH4DO PIC X(32). //Additional Authorized Card User 420 CARDSDO PIC X. //Number of cards issued to Customer20 IMODO PIC X(2). //Month card issued20 IDAYDO PIC X(2). //Day card issued20 IYRDO PIC X(2). //Year card issued20 RSNDO PIC X. //Reason code for card issued20 CCODEDO PIC X. //Card status coded e.g. G for Gold20 APPRDO PIC X(3). //Code of card issue approvers20 SCODE1DO PIC X. //Additional privilege code 120 SCODE2DO PIC X. //Additional privilege code 220 SCODE3DO PIC X. //Additional privilege code 320 STATDO PIC X(2). //Account status20 LIMITDO PIC X(8). //Customer Account Credit Limit20 PAY-HIST OCCURS 3. //Pay History first of last three25 BAL PIC X(8). //Account Balance25 BMO PIC 9(2). //Month25 BDAY PIC 9(2). //Day25 BYR PIC 9(2). //Year25 BAMT PIC X(8). //Amount of balance25 PMO PIC 9(2). //Payment month25 PDAY PIC 9(2). //Payment day25 PYR PIC 9(2). //Payment year25 PAMT PIC X(8). //Payment mmount
The record format is already fixed and used by batch programs. Our online CICS sample program must use the same record definition.
Browsing a File
When you search by name using NACT05, you need to be able to point to a particular record in the file, based on end-user input which maybe anywhere in the file. Then you can start reading the file sequentially from that point on. The need for this combination of random and sequential file access—called browsing—arises frequently in online applications. Consequently, CICS provides a special set of EXEC CICS browse commands to make this job easier, namely: STARTBR, READNEXT, READPREV, and ENDBR.
Before looking at these commands, a few words about the performance implications of browsing. Transactions that produce lots of output screens can monopolize system resources. A file browse is often guilty of this. Having a long browse can put a severe load on the system, delaying other transactions and increasing overall response time.
The CICS default design model assumes the end user initiates a transaction that accesses a few data records, processes the information, and returns the results to that user. This process may involve numerous I/O waits that allow CICS to schedule and run other tasks. However, CICS is not an interrupt-driven multitasking system—tasks that involve small amounts of I/O relative to processing are able to monopolize the system regardless of priority.
Starting the browse operation
The STARTBR (start browse) command gets the process started. It tells CICS where in the file you want to start browsing. The format is:
EXEC CICS STARTBR FILE(filename) RIDFLD(data-area) options END-EXEC
The FILE and RIDFLD parameters are described in the READ command. The options allowed are EQUAL and GTEQ; you cannot use them both. They are defined as follows:
- EQUAL
Specifies that the search is satisfied only by a record having the same key (complete or generic) as that specified in the RIDFLD option.
- GTEQ
Specifies that, if the search for a record having the same key (complete or generic) as that specified in the RIDFLD option is unsuccessful, the first record having a greater (higher in the collating sequence) key satisfies the search.
Reading the next record
Starting a browse does not make the first eligible record available to your program; it merely tells CICS where you want to start when you begin issuing read commands. To get the first record, and for each one in sequence after that, you use the READNEXT command:
EXEC CICS READNEXT FILE(filename) INTO(data-area) LENGTH(data-area) RIDFLD(data-area) END-EXEC
The FILE, INTO and LENGTH parameters are defined in the same way as they are in the READ command. You need the FILE parameter because CICS allows you to browse several files at once, and the FILE parameter tells which one to read.
Warning
You cannot execute a READNEXT command for a file unless you’ve first executed a successful STARTBR command for that file. The RIDFLD parameter is used in a somewhat different way. On the READ and STARTBR commands, RIDFLD carries information from the program to CICS; on READNEXT, the flow is primarily in the other direction: RIDFLD points to a data area into which CICS will “feed back” the key of the record it just read. Make sure that RIDFLD points to an area large enough to contain the full key; otherwise any adjacent fields in storage will be overwritten. Don’t change it, either, because you’ll interrupt the sequential flow of the browse operation. Note that this area must be the same one used in the STARTBR command.
Tip
There is a way to do what is called “skip sequential” processing in VSAM by altering the contents of this key area between READNEXT commands. Although we won’t be covering this here, we mention it only to explain why you should not inadvertently change the contents of the data-area in RIDFLD while browsing the file.
Finishing the browse operation
When you’ve finished reading a file sequentially, terminate the browse with the ENDBR command:
EXEC CICS ENDBR FILE(filename)
END-EXECHere FILE functions as it did in the READNEXT command; it tells CICS which browse is being terminated, and obviously must name a file for which a successful STARTBR has been issued earlier.
Using the browse commands in the sample application
The first thing you have to do is construct a key that starts the browse in the right place. The key of the name file consists of the last name (surname). The idea is to build a key that consists of the characters the user keyed in as the last name (surname). Then you can use the GTEQ option on our STARTBR command to get the first qualifying record. For example:
05 WS-LIMIT-NAMES.
10 WS-BROWSE-SNAME PIC X(18) VALUE SPACES.
10 WS-MAX-SNAME PIC X(18) VALUE SPACES.
10 WS-MIN-FNAME PIC X(12) VALUE SPACES.
10 WS-MAX-FNAME PIC X(12) VALUE SPACES.You can then set up the parameters for the search limits. This data comes from the area passed to the NACT05 program which performs this name search. You also need to know where to stop the browse.
Certainly this stops when you overflow the capacity of the data passing area, but you may run out of eligible names before that. So you need to construct a last name value that is the highest alphabetically that could meet your match criteria. If the last name in the record exceeds this value, you know that you’ve read all the (possibly) eligible records. This limiting value is named WS-MAX-SNAME.
Finally, as you read, you need to test whether the forename matches sufficiently to return the record to the caller or not. If you define WS-MIN-FNAME as the smallest allowable value and WS-MAX-FNAME as the largest, then you need the following code to set up all of the relevant areas:
B-010.
MOVE SNAMEDO IN CA-BRWS-ENTRY (1) TO WS-PASSED-SNAME
WS-BROWSE-SNAME
WS-MAX-SNAME
*
INSPECT WS-MAX-SNAME REPLACING ALL SPACES BY HIGH-VALUES
*
MOVE FNAMEDO IN CA-BRWS-ENTRY (1) TO WS-PASSED-FNAME
WS-MAX-FNAME
WS-MIN-FNAME
*
INSPECT WS-MAX-FNAME REPLACING ALL SPACES BY HIGH-VALUES
INSPECT WS-MIN-FNAME REPLACING ALL SPACES BY LOW-VALUESSNAMEDO IN CA-BRWS-ENTRY(1) is where the input last name is passed to the program. Similarly FNAMEDO IN CA-BRWS-ENTRY(1) is where the input forename is passed to the program.
So we can now look at how the code is put together with these commands. But we need to introduce a couple of controlling values:
05 WS-AVAILABILITY-IND PIC X.
88 SOME-AVAILABLE VALUE 'Y'.
88 NONE-AVAILABLE VALUE 'N'.WS-AVAILABILITY-IND is used to control the reading loop. Also we need to note a part of the area passed to the program:
10 CA-BRWS-FOUND PIC 9(4).
88 CA-BRWS-NONE-FOUND VALUE ZERO.
10 CA-BRWS-MORE PIC 9(4).
10 CA-BRWS-MORE-X REDEFINES CA-BRWS-MORE
PIC X(4).
88 CA-BRWS-NO-MORE VALUE '0000'.CA-BRWS-FOUND indicates how many matches were found for the criteria supplied. CA-BRWS-MORE indicates if there were more matches than the number allowed for. These are copied into NACT05 from copybook NACCBRWS. Example 5-3 shows the copybook. It is also found on the CD-ROM in Cobol ApplicationPCsourcecopy.
* The interface to the Browse program is described in a copy book
* in order to ensure consistency. The values in this area designed
* to be in character format to enable ease of translation when the
* program is invoked from a remote system which uses a different
* encoding scheme (e.g., ASCII) than the EBCDIC of the mainframe.
*
* This is the working storage version of the interface to the
* Browse program.
*
05 WS-BRWS-COMMAREA.
*
* This is an "Eyecatcher" and integrity check field.
*
10 WS-BRWS-VERSION PIC XXX VALUE SPACES.
88 WS-BRWS-CORRECT-VERSION VALUE 'V1A'.
*
* Only two functions are provided by the Browse program:
* initiation of a Browse and Continuation of a previously
* initiated browse.
*
10 WS-BRWS-FUNCTION PIC X VALUE SPACE.
88 WS-BRWS-REQ-BROWSE VALUE 'B'.
88 WS-BRWS-REQ-CONTINUE VALUE 'C'.
88 WS-BRWS-VALID-REQUEST VALUE 'B' 'C'.
*
* The response field is designed to conform to the CICS EIBRESP
* characteristics which always contains a numeric value. There
* are also architected values to indicate errors detected by the
* Browse program itself. If there was an interface error, this
* contains a special value of 'FRMT'.
*
10 WS-BRWS-RESP PIC 9(4) VALUE ZERO.
10 WS-BRWS-RESP-X REDEFINES WS-BRWS-RESP
PIC X(4).
88 WS-BRWS-NO-ERROR VALUE '0000'.
88 WS-BRWS-BAD-FORMAT VALUE 'FRMT'.
*
* The reason field is designed to conform to the CICS EIBRESP2
* characteristics which always contains a numeric value. There
* are also architected values to indicate errors detected by the
* Browse program itself. If there was an interface error, this
* contains 'VERE' for Version Error, 'LENE' for Length Error (if
* possible), 'REQE' for Request Error, 'LIME' for Limit Error or
* 'MORE' for More Error (only occurs for a continuation request).
*
10 WS-BRWS-REAS PIC 9(4) VALUE ZERO.
10 WS-BRWS-REAS-X REDEFINES WS-BRWS-REAS
PIC X(4).
88 WS-BRWS-VERSION-ERROR VALUE 'VERE'.
88 WS-BRWS-LENGTH-ERROR VALUE 'LENE'.
88 WS-BRWS-REQUEST-ERROR VALUE 'REQE'.
88 WS-BRWS-LIMIT-ERROR VALUE 'LIME'.
88 WS-BRWS-MORE-ERROR VALUE 'MORE'.
*
* If the response contains a numeric value, this contains the
* character representation of the EIBFN value giving rise to
* the exception condition.
*
10 WS-BRWS-CICS-FUNCTION PIC 9(5) VALUE ZERO.
10 WS-BRWS-CICS-FUNCTION-X
REDEFINES WS-BRWS-CICS-FUNCTION
PIC X(5).
*
* In order to prevent excessive searches, the caller must specify
* the maximum number of matches (s)he is prepared to handle.
* Also because a COMMAREA is limited to a maximum of approximately
* 32,000 bytes, the maximum limit has been set at 80.
*
10 WS-BRWS-LIMIT-TO-GET PIC 9(4) VALUE ZERO.
10 WS-BRWS-LIMIT-TO-GET-X REDEFINES WS-BRWS-LIMIT-TO-GET
PIC X(4).
*
* The Browse program indicates the number of matches found.
* The range is zero to the limit.
*
10 WS-BRWS-FOUND PIC 9(4) VALUE ZERO.
88 WS-BRWS-NONE-FOUND VALUE ZERO.
*
* After satisfying the limit, the Browse program will place
* either '0000' in here if there are no more records satisfying
* the search criteria or a number if there are more. On a
* continuation request this number must be returned to the Browse
* program since it is used to reposition the request.
*
10 WS-BRWS-MORE PIC 9(4) VALUE ZERO.
10 WS-BRWS-MORE-X REDEFINES WS-BRWS-MORE
PIC X(4).
88 WS-BRWS-NO-MORE VALUE '0000'.
*
* The records found on file for a match. Input is in the
* surname and first name fields of the first Entry.
*
10 WS-BRWS-MATCHES.
15 WS-BRWS-ENTRY OCCURS 80.
*
* The description of the account record is placed in a copy book.
*
COPY NACWTREC.The code shown in Example 5-4 initializes the browse of the file using the STARTBR command and sets the availability indicator based on the possibility of a match.
C-START-BROWSE SECTION.
*
*
* This routine initializes the browse of the file via the
* STARTBR command and sets the availability indicator based
* on the possibility of a match.
*
SET CA-BRWS-NONE-FOUND TO TRUE
*
EXEC CICS STARTBR FILE(WS-LITS-FILES-NAME)
RIDFLD(WS-BROWSE-SNAME)
RESP(RESPONSE) RESP2(REASON-CODE)
END-EXEC
*
EVALUATE RESPONSE
WHEN DFHRESP(NORMAL)
SET SOME-AVAILABLE TO TRUE
WHEN DFHRESP(NOTFND)
SET NONE-AVAILABLE TO TRUE
SET CA-BRWS-NO-MORE TO TRUE
*
* If any other condition other than success or NOTFND
* occurs, then a serious problem has occurred, so the
* error handler is invoked.
*
WHEN OTHER
PERFORM Z-ERROR-HANDLER
END-EVALUATE
*
END-C-START-BROWSE.
EXIT.The code shown in Example 5-5 attempts to read a record from the file and sets the availability indicator based on its success.
Y-READ-ONE SECTION.
*
* This code attempts to read a record from the file and
* sets the availability indicator based on its success.
*
* This section is performed from the following sections -
* D-FILL-IN-MATCHES
* E-CONTINUE-BROWSE
*
Y-010.
EXEC CICS READNEXT FILE(WS-LITS-FILES-NAME)
INTO(AN-ACCTREC)
RIDFLD(WS-BROWSE-SNAME)
RESP(RESPONSE) RESP2(REASON-CODE)
END-EXEC
EVALUATE RESPONSE
*
* If either condition occurs, it means a record was read.
*
WHEN DFHRESP(NORMAL)
WHEN DFHRESP(DUPKEY)
*
* But it may not match the full criteria.
*
IF SNAMEDO IN AN-ACCTREC > WS-MAX-SNAME
SET NONE-AVAILABLE TO TRUE
ELSE
SET SOME-AVAILABLE TO TRUE
ADD 1 TO WS-RECORDS-READ
END-IF
*
* If we have exhausted the file, then there
* are obviously no more matches.
*
WHEN DFHRESP(ENDFILE)
SET NONE-AVAILABLE TO TRUE
*
* If any other condition occurs, then a serious problem
* has occurred, so the error handler is invoked.
*
WHEN OTHER
PERFORM Z-ERROR-HANDLER
END-EVALUATE
*
END-Y-READ-ONE.
EXIT.
EJECT.The code shown in Example 5-6 terminates the browsing operations against the file.
Write Commands
There are three file output commands:
Rewriting a file record
The REWRITE command updates the record you’ve just read. You can use it only after you’ve performed a “read for update” by executing a READ command for the same record with UPDATE specified. REWRITE looks like this:
EXEC CICS REWRITE FILE(filename) FROM(data-area) RESP(data-area) RESP2(data-area) END-EXEC
The options for this caommand are:
- FILE(filename)
The same meaning as in the READ command: it is the CICS name of the file you are updating. This parameter is required.
- FROM(data-area)
The name of the data area that contains the updated version of the record to be written to the file. This parameter is required.
- LENGTH(data-value)
The length of the (updated) version of the record. You must specify length, as in a READ command for variable length records, but for fixed length records as in this book, the LENGTH option is not required.
Adding (writing) a file record
The WRITE command adds a new record to the file. The parameters for WRITE are almost the same as for REWRITE, except that you have to identify the record with the RIDFLD option. (You do not do this with the REWRITE command because the record was identified by the previous READ UPDATE operation on the same data set.) The format of the WRITE command is:
EXEC CICS WRITE FILE(filename) FROM(data-area) LENGTH(data-value) RIDFLD(data-value) RESP(data-area) RESP2(data-area) END-EXEC
The key option for this command is:
- RIDFLD(data-area)
The data area containing the key of the record to be written. If the key is located at the front of the record, its argument will be the same as the FROM argument.
Deleting a file record
The DELETE command deletes a record from the file, and looks like this:
EXEC CICS DELETE FILE(filename) RIDFLD(data-area) RESP(data-area) RESP2(data-area) END-EXEC
The parameters are defined in the same way as for the WRITE and REWRITE commands. You can delete a record directly, without reading it for update first. When you do this you must specify the key of the record to be deleted by using RIDFLD. Alternatively, you can decide to delete a record after you’ve read it for update. In this case, you must omit RIDFLD.
Using the write commands in the example application
Program NACT02 uses all three of the file output commands. For add requests, it issues the command:
EXEC CICS WRITE FILE(WS-LITS-FILES-ACCOUNT)
FROM(NACTREC-DATA)
RIDFLD(ACCTDO IN NACTREC-DATA)
RESP(CA-CRUD-RESP) RESP2(CA-CRUD-REAS)
END-EXECACCTDO IN NACTREC-DATA is where the frontend program passed the data of the record to be added.
For a modification, the program first reads the record in question, with UPDATE specified:
EXEC CICS READ FILE(WS-LITS-FILES-ACCOUNT) UPDATE
INTO(OLD-ACCTREC)
RIDFLD(ACCTDO IN NACTREC-DATA)
RESP(CA-CRUD-RESP) RESP2(CA-CRUD-REAS)
END-EXECThen it merges this old data with the new version of the record, again at ACCTDO IN NACTREC-DATA. Finally, it replaces the old record with the new one, in the command:
EXEC CICS REWRITE FILE(WS-LITS-FILES-ACCOUNT)
FROM(NACTREC-DATA)
RESP(CA-CRUD-RESP) RESP2(CA-CRUD-REAS)
END-EXECFor a deletion, the program issues the command without reading it for update. Therefore the key (RIDFLD) is required in the DELETE command, which is:
EXEC CICS DELETE FILE(WS-LITS-FILES-ACCOUNT)
RIDFLD(ACCTDO IN NACTREC-DATA)
RESP(CS-CRUD-RESP) RESP2(CS-CRUD-REAS)
END-EXECIf you have created a lock with a READ UPDATE command and then decide that you don’t need it, you use an EXEC CICS UNLOCK FILE(fileName) RIDFLD(key) command to release it.
Errors on file commands
A wide variety of conditions can arise when using file commands. Here are some of the conditions passed to your program in the RESP field that can arise when you use the file commands that have just been described. A mapping between the response value and the following name can be found in the NACT04 program:
- DISABLED
Occurs if a file is disabled. A file may be disabled because:
It was initially defined as disabled and has not been enabled since.
It has been disabled by an EXEC CICS SET command or by the CEMT[2] transaction.
- DUPKEY
Means that if a VSAM record is retrieved by way of an alternate index with the NONUNIQUEKEY attribute; another alternate index record with the same key follows. It does not occur as a result of a READNEXT command that reads the last of the records having the non-unique key.
- DUPREC
Means that there is already a record in the file with the same key as the one that you are trying to add with a WRITE command. This condition may result from a user error or may be expected by the program. In either of these cases, there should be specific code to handle the situation. This condition is handled in the NACT02 program when dealing with the locking file, since this could mean another user has already locked the account.
It can also fall into the should-not-occur category. In this case no special code is required beyond logging information that may help find the problem, cleaning up if necessary, and identifying the problem to the user.
- ENDFILE
Means that you’ve attempted to read sequentially beyond the end of the file in a browse (using the READNEXT command). This is a condition that you should program for in any browse operation. In the example application, for instance, a search on “Zuckerman” or a similar name might cause ENDFILE, and you code for it explicitly as shown in Example 5-4 in the C-START-BROWSE SECTION in the browse program, NACT05.
- FILENOTFOUND
Means that the symbolic filename in a file command cannot be found in the File Control Table. This is often a coding error; look for a difference in spelling between the command and the FCT entry. If it happens after the program is put into actual use (“in production”), look for an accidental change to the definition for that file. The file may be on another system or it hasn’t been created; there are any number of possibilities that could cause this response.
- ILLOGIC
Is a catch-all class for errors detected by VSAM that don’t fall into one of the other categories that CICS recognizes. The RESP2 value will tell you the specific error.
- INVREQ
Means that CICS regards your command as an invalid request for one of the following reasons:
You requested a type of operation (write, update, browse, and so on) that wasn’t included in the “service requests” of the definition for the file in question.
You tried to REWRITE a record without first reading it for update.
You issued a DELETE command without specifying a key (RIDFLD), and without first reading the target record for update.
You issued a DELETE command specifying a key (RIDFLD) for a VSAM file when a read for update command is outstanding.
After one read for update, you issued another read for update for another record in the same file without disposing of the first record (by a REWRITE, UNLOCK, or DELETE command).
You issued a READNEXT, READPREV or an ENDBR command without first doing a STARTBR on the same file.
- IOERR
Means that the operating system is unable to read or write the file, presumably because of physical damage. This can happen at any time, and there is usually nothing to do in the program except to abend the transaction and inform the user of the problem.
- ISCINVREQ
Means that the remote system indicates a failure which does not correspond to a known condition.
- LENGERR
Is usually caused by a coding error and could result from one of the following reasons:
The length you specified on a WRITE or REWRITE operation was greater than the maximum record size for the file. (See the description of the LENGTH option in the CICS Application Programming Reference.)
You indicated a wrong length on a READ, READNEXT, WRITE or REWRITE command to a file containing fixed-length records.
- NOSPACE
Means that there’s no space in the file to fit the record you’ve just tried to put there with a WRITE or REWRITE command. This doesn’t mean that there’s no space at all in the data set; it simply means that the record with the particular key you specified will not fit until the file is extended or reorganized. Like IOERR, this may occur at any time, and should be handled accordingly.
- NOTAUTH
Means that a resource or command security check has failed.
- NOTFND
Means that there is no record in the file with the key specified in the RIDFLD, parameter on a READ, READNEXT, READPREV, STARTBR, or DELETE command. NOTFND may result from a user error, may be expected by the program, or may indicate an error in the program logic:
IF NOT WS-CRUD-BAD-LOCK EVALUATE WS-CRUD-RESP WHEN DFHRESP(NORMAL) CONTINUE WHEN DFHRESP(NOTFND) IF NOT CA-SENT-MENU PERFORM TA-BAD-CRUD-RESPONSE (Handle abend) END-IF WHEN OTHER PERFORM TA-BAD-CRUD-RESPONSE END-EVALUATE END-IFWhen adding:
EVALUATE TRUE ** * when this account already exists, the user must be informed * WHEN WS-CRUD-NO-ERROR SET MSG-DUPLICATE TO TRUE MOVE-1 TO ACCTML MOVE DFHBMBRY TO ACCTMA SET WS-BB-ERROR-PRESENT TO TRUE . . . END-EVALUATEWarning
In program NACT01, when you check to see if the requested account record is on file, you expect NOTFND if the request is to add a record. The actual work was done in NACT02. However, it shows a user error (in the account number) if it happens on any other type of request. For both these cases, you need to provide recovery code.
- NOTOPEN
The requested file is CLOSED and UNENABLED. The CLOSED, UNENABLED state is reached after a close request has been received against an OPEN ENABLED file and the file is no longer in use.
The requested file is still open and in use by other requests, but a close request against the file has been received. Existing users are allowed to complete.
This condition can occur only during the execution of the following commands: READ, WRITE, DELETE, or STARTBR. Other commands cannot raise this condition because they are part of an active request.
This condition does not occur if the request is made to either a CLOSED, ENABLED file or a CLOSED, DISABLED file. In the first case, the file is opened as part of executing the request. In the second case, the DISABLED condition is raised.
As you have probably gathered from this description, NOTOPEN usually results from an operations problem, and you may want to notify the operations staff of the problem, or send a message to the user to do so.
- SYSIDERR
Means that the SYSID option specifies either a name of a CICS system that is not defined in the intersystem table or a system to which the link is closed.
Other File Services
Before leaving the topic of file commands, we’ll list some of the other facilities that are available. You can find guidance information on using file control in the CICS Application Programming Guide, and a full list of commands, options, and exceptional conditions in the CICS Application Programming Reference. Both of these books are part of the CICS library and are found on the CD-ROM.
Saving Data: Using a Scratchpad Facility
Sequential file facilities are provided because of the need to save data from the execution of one transaction, passing it on to another that occurs later. There are two instances of this requirement in the sample application:
The first resulted from the decision to use pseudo-conversational transactions; this arises from the need to save data from one interaction with the terminal user to the next, even though no task exists for that terminal for most of the intervening time. For this you need something to save state, for example, a scratchpad facility.
The second requirement came from the need to log the changes to the account file. Here you require some sort of queuing facility: a way to add items to a list (one in each update transaction) and read them later (in the log-print transaction).
There are several different scratchpad areas in CICS that you can use to transfer and save data, within or between transactions. See Queuing Facilities: Temporary Storage and Transient Data, later in this chapter. The CICS Application Programming Reference gives you a complete list of the commands you can use to get access to these areas:
- Communication Area or COMMAREA
This is an area used for passing data between both programs within a transaction and transactions at a given terminal. It’s described later in connection with the program control commands in Controlling Programs, later in this chapter. The COMMAREA is the recommended scratchpad area.
The COMMAREA offers an alternative solution to the double updating problem. For example, it would be perfectly feasible for the NACT01 program to pass the contents of the account file record over to the NACT02 program in the COMMAREA. The NACT02 program could then re-retrieve the account record for update and compare it with the version passed in COMMAREA. Any difference would show that some other task had changed the account record.
Although this solution may be easier to code, it isn’t as good from the user’s point of view. You see, with this scheme, you don’t find out about any conflict over the record until you’re ready to update it. Unfortunately, that means you then have to tell one user that his or her update cannot be made, but you can’t tell them until they’ve keyed in all the changed data.
- Common Work Area (known as the CWA)
Any transaction can access the CWA, and since there’s only one CWA for each CICS address space, the whole system, the format and use of this area must be agreed upon by all transactions in all applications that use it. Avoid this method; the affinities created cause major problems if groups of transactions have to be split up sometime in the future.
- Transaction Work Area (TWA)
The TWA exists only for the duration of a transaction. Consequently, you can use it to pass data among programs executed in the same transaction (like COMMAREA), but not between transactions (unlike COMMAREA). The TWA isn’t commonly used now (and probably shouldn’t be) as a scratchpad area in modern CICS programs.
Affinities
An affinity is created when a resource that contains state data of a pseudo-conversation is tied to one instance of a CICS. If the KanDoIT company takes over other companies, they will want to run multiple machines with many CICS regions/address spaces and if the state of one credit card is on one machine and the data on another, the application will not scale up because the transaction may (will) have an affinity to the first machine. The first place that this normally occurs is in the use of a resource that is tied to one CICS region, for example, a CWA. Secondly, it is using temporary storage with a key that uses a resource name that is unique to that CICS, for example, a termid. This is a highly complex subject; see the CICS Application Programming Guide for more information.
Controlling Programs
A transaction (task) may use several programs in the course of completing its work.
Associating Programs and Transactions
The installed program definition contains one entry for every program used by any application in the CICS system. Each entry holds, among other things, three particularly important pieces of information:
The language in which the program is written, which CICS needs to know in order to set up its linkages and control blocks properly
How many tasks are using the program at the moment
Where the program is (in main storage and/or on disk)
The installed transaction definition has an entry for every transaction identifier in the system (using “transaction” in the CICS sense of the word). The important information kept about each transaction is the transaction identifier and the name of the first program to be executed on behalf of the transaction.
You can see how these two sets of definitions work in concert:
The user types in a transaction identifier at the terminal (or the previous transaction may have determined it).
CICS looks up this identifier in the list of installed transaction definitions.
This tells CICS which program to invoke first.
CICS looks up this program in the list of installed program definitions, finds out where it is, and loads it if it isn’t already in main storage.
CICS builds the control blocks necessary for this transaction, using information from the definition of the transaction, program, and principle facility. For programs in command-level COBOL, like ours, this includes making a private copy of working storage to make it re-entrant for this particular execution of the program.
CICS passes control to the program, which begins running using the environment that has been set up. This program may pass control to any other program in the list of installed program definitions or may autoinstall a program on its first reference, if necessary, in the course of completing the transaction.
Commands for Passing Program Control
There are two CICS commands for passing control from one program to another. One is the LINK command, which is similar to a CALL statement in COBOL. The other is the XCTL (transfer control) command, which has no COBOL counterpart. When one program links to another, the first program in working storage and remains in main storage. When the second (linked-to) program finishes and gives up (RETURNs) control, the first program resumes at the instruction after the LINK. The linked-to program is considered to be operating at one logical level lower than the program that does the linking.
In contrast, when one program transfers control (XCTL) to another, the first program is considered terminated, and the second program operates at the same level as the first. When the second program finishes, control is returned not to the first program, but to whatever program last invoked it.
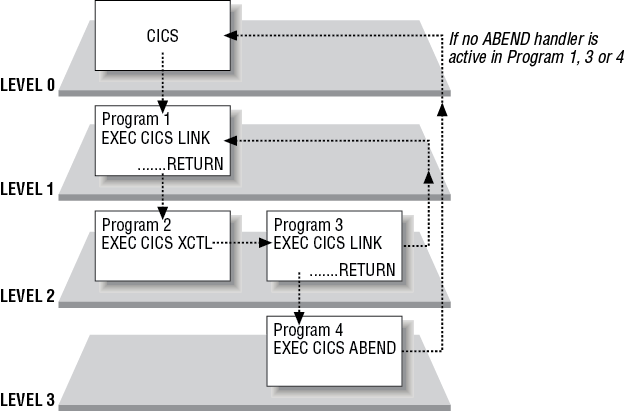
Some people like to think of CICS itself as the highest program level in this process, with the first program in the transaction as the next level down, and so on. If you look at it from this point of view, CICS links to the program named in the list of installed transaction definitions when it initiates the transaction (see Figure 5-1). When the transaction is complete, this program (or another one operating at the same level) returns control to the next higher level, which happens to be CICS itself.
The LINK Command
The LINK command is used to link to another program expecting return. The syntax of the LINK command looks like this:
EXEC CICS LINK PROGRAM(name) COMMAREA(data-area) LENGTH(data-value) RESP(data-area) RESP2(data-area) END-EXEC
- PROGRAM(name)
Specifies the identifier (1–8 characters) of the program to which control is to be passed unconditionally. The linked-to program can execute either in the same region/address space as its caller (default) or may execute remotely if a remote SYSID is specified. This type of link is known as a distributed program link (DPL).
- COMMAREA(data-area)
Specifies a communication area that is to be made available to the invoked program. In this option the data area is passed, and you must give it the name DFHCOMMAREA in the receiving program. (See the section about passing data to other programs in the CICS Application Programming Guide.)
- LENGTH(data-value)
Specifies the length in bytes of the COMMAREA (communication area) and must not exceed 32,500 bytes. This need not be specified as the length can be inferred from the COMMAREA argument.
The XCTL Command
The XCTL command is used to transfer control from one program to another:
EXEC CICS XCTL PROGRAM(name) COMMAREA(data-area) LENGTH(data-value) RESP(data-area) RESP2(data-area) END-EXEC
The parameters are the same as for the LINK command.
The RETURN Command
The RETURN command returns control to the previous program within a transaction. The syntax is simply:
EXEC CICS RETURN END-EXEC
When the program at the highest level for the transaction returns control to CICS, however, there are two additional options that you can specify:
You can say what transaction is to be executed when the next input comes from the same terminal. (This is how you get into pseudo-conversational mode.)
You can specify data that’s to be passed on to that next transaction.
In this case the RETURN command is slightly longer:
EXEC CICS RETURN TRANSID(nextid) COMMAREA(data-area) LENGTH(data-value) END-EXEC
- TRANSID(nextid)
Specifies the transaction identifier (1–4 characters) to be used with the next input message entered from the terminal with which the task that issued the RETURN command has been associated. The specified name must have been defined as a transaction to CICS.
- COMMAREA(data-area)
Specifies a communication area that is to be made available to the next program that receives control. In a COBOL receiving program, you must give this data area the name DFHCOMMAREA. (See the CICS Application Programming Guide for more information about the CICS COMMAREA.) Because the data area is freed before the next program starts, a copy of the data area is created and a pointer to the copy is passed.
- LENGTH(data-value)
Specifies the length in bytes of the COMMAREA. The maximum as before is 32,500 bytes but, as always, the shorter the better. This need not be specified as the length can be inferred from the COMMAREA argument.
The COBOL CALL Statement
As well as passing control to other programs by means of LINK and XCTL commands, a CICS COBOL program can invoke another program with a COBOL CALL statement. Although there’s somewhat less system overhead (in other words, a shorter path length) with this method, there are some considerations that may count against it. For example:
A called program remains in its last-used state after it returns control, so a second call finds the program in this state. LINK and XCTL commands, on the other hand, always find the new program in its initial state.
With static calls, you must link-edit the calling and called programs together and present them to CICS as a single unit, with one name. This has two consequences:
It may result in a module that is quite large.
It prevents two programs that call the same program from sharing a copy of the called program.
With dynamic calls, CALL data-area have the advantage over LINK in terms of shorter length as long as the program is called more than twice.
Programs that are called are different than LINKed programs:
They use the conventional GOBACK statement to return to their caller rather than EXEC CICS RETURN.
No CICS trace entries are created on the GOBACK; problem analysis is more difficult.
Subroutines
Now, the answer to that problem we met earlier—whether and how to break up a large routine. For single-task efficiency, generally inline code is best, PERFORM next, straight CALL third, XCTL next, and LINK last. However, any of the first three choices may make for a long load module, and that can impact future understanding as to how the whole thing works when it comes to fixing bugs in later years.
Always use XCTL if it will do, of course, rather than LINK. In the NACT01 program there is one use of XCTL. That’s just a program logic issue; you either need control back or you don’t. In the example, as you’ll see, we’ve broken our own rule and used a LINK (rather than an XCTL) to the error handling program. However, we do have an excuse ready. See Handling Errors, earlier in this chapter.
The probability of the code being re-used is another issue. If you have a long complex routine for calculating withholding tax for veterans in a payroll system, but you use it only if salary or dependents change and you have hardly any veterans, then by all means put it in a separate routine and LINK to it.
Examples of Passing Control and Data Between Programs and Transactions
The previous sections provide the background about passing data from one transaction to another; you may be wondering how the receiving program accesses this data. When the sample application meets an error from which it cannot recover, it transfers control to the general-purpose error program, NACT04. We pass three items of information to the NACT04 program:
The name of the program that passed control (and where the error was detected)
The function that failed
The return code from the command that failed
The copybooks used to pass this information to the error handling program by the other modules in the COBOL application are shown in Example 5-7.
*
* This is the working storage version of the interface to the
* Error Handler program.
*
05 WS-ERRH-ERROR-COMMAREA.
*
* This is an "Eyecatcher" and integrity check field.
*
10 WS-ERRH-VERSION PIC XXX VALUE SPACES.
88 WS-ERRH-CORRECT-VERSION VALUE 'V1A'.
10 FILLER PIC X VALUE SPACES.
*
* The error field is designed to conform to the CICS EIBRESP
* characteristics which always contains a numeric value. There
* are also architected values to indicate errors detected by the
* various programs in the applications suite.
*
10 WS-ERRH-ERROR PIC 9(4) VALUE ZERO.
10 WS-ERRH-ERROR-X REDEFINES WS-ERRH-ERROR
PIC X(4).
*
* The reason field is designed to conform to the CICS EIBRESP2
* characteristics which always contains a numeric value. There
* are also architected values to indicate errors detected by the
* various programs in the applications suite.
*
10 WS-ERRH-REASON PIC 9(4) VALUE ZERO.
10 WS-ERRH-REASON-X REDEFINES WS-ERRH-REASON
PIC X(4).
*
* If the response contains a numeric value, this contains the
* character representation of the EIBFN value giving rise to
* the exception condition.
*
10 WS-ERRH-CICS-FUNCTION PIC 9(5) VALUE ZERO.
10 WS-ERRH-CICS-FUNCTION-X
REDEFINES WS-ERRH-CICS-FUNCTION
PIC X(5).
*
* Since the Error Handler can be LINKed or XCTLed to as well as
* being entered via CICS ABEND handling, this field allows the
* program trapping the error to identify itself.
*
10 WS-ERRH-PROGRAM PIC X(8) VALUE SPACES.
*
* This is set by the Error Handler to indicate the number of
* messages it generated from the error information. This is
* intended to allow a program which has LINKed to the Error
* Handler to use the information in a manner it deems suitable.
*
10 WS-ERRH-NUMBER PIC 9(4) VALUE ZERO.
*
* The array of messages generated.
*
10 WS-ERRH-MESSAGES.
15 WS-ERRH-MESSAGE PIC X(120) OCCURS 3.The data is passed to the NACT04 program using the XCTL command:
EXEC CICS XCTL PROGRAM(ABEND-PROGRAM)
COMMAREA(WS-ERRH-ERROR-COMMAREA)
RESP(RESPONSE) RESP2(REASON-CODE)
END-EXECCommunicating Between Transactions in the Sample Application
The LINK command is used to connect the NACT01 program to the CRUD (NACT02) program and also to the BRWS (NACT05) program:
EXEC CICS LINK PROGRAM(CRUD-PROGRAM)
COMMAREA(WS-CRUD-COMMAREA)
RESP(RESPONSE) RESP2(REASON-CODE)
END-EXECAccessing the COMMAREA in the called program
In the NACT02 code you will see how this is done. To the NACT02 program, CICS makes it look like you are receiving one parameter:
LINKAGE SECTION
01 DFHCOMMAREA
COPY NACCCRUDExamples of EXEC CICS RETURN use
There are several different types of return to CICS. The simplest occurs in program NACT02, after the user has indicated a wish to exit from the application. No next TRANSID (transaction identifier) is set, and no data is passed forward to the next transaction. The return command is just:
EXEC CICS RETURN END-EXEC
In program NACT01, in contrast, we need to indicate that the next transaction to be executed from the same terminal is the same as the current one whose transaction ID is stored in EIBTRNID of the EIB, so the RETURN command is written:
EXEC CICS RETURN TRANSID(EIBTRNID)
COMMAREA(DFHCOMMAREA)
END-EXECErrors on the Program Control Commands
CICS recognizes these exceptional conditions on program control commands:
- INVREQ
This means that one of two things happened:
You specified COMMAREA or LENGTH on a RETURN command in a program that was not at the highest level (that is, a RETURN that would not terminate the transaction by returning control to CICS).
You specified the TRANSID option on a RETURN from a task that had no terminal associated with it. In either form, INVREQ usually means a programming error.
- LENGERR
This means that the length of the data, specified using the RETURN command with the length option, is outside the valid range of 1 to 32,500.
- NOTAUTH
This means that a resource or command security check has failed. There is a complete list of reasons for such failures in the section on NOTAUTH in the CICS Application Programming Reference.
- PGMIDERR
This means that the program to which control was passed, on a LINK or an XCTL command, cannot be found in the list of installed program definitions, isn’t in the library, or has been disabled. It corresponds to FILENOTFOUND on a file command, and has similar causes. If it occurs during the testing phase, look for a spelling mismatch; if it occurs once the system has been put into actual use (in production), have your systems people check the list of installed program definitions.
Abending a Transaction
In addition to the normal return sequences, there is another command that is used in abnormal circumstances. This is the ABEND command. It returns control to CICS directly, as shown in Figure 5-1, if no ABEND handlers are active in any of the previous programs.
Use the ABEND command when a situation arises that the program cannot handle. This may be a condition beyond the control of the program (such as an input/output error on a file) or it may simply be a combination of circumstances that should not occur if the program logic is correct. In either case, ABEND is the right command to terminate the transaction. The format is:
EXEC CICS ABEND ABCODE(name)
END-EXECThe option for this command is:
- ABCODE(name)
Simply a four-character code identifying the particular ABEND command. It does two jobs: it tells CICS that you want a dump of your transaction, and it identifies the dump. Enclose it in quotes if it is a literal.
In addition, if no ABEND handlers are active and the program is at the highest level (Level 1 as described in Figure 5-1) control will be returned to CICS. The ABEND command has another very important property: it causes CICS to undo (back out) all of the changes made by this unit of work to recoverable resources.
Warning
Do not start the name of an ABEND code with the letter A, because it is reserved for CICS itself.
In our example application, we use this command at the end of program NACT04, where we send control when we’ve encountered a situation that prevents us from continuing the requested transaction. The code is:
EXEC CICS ABEND ABCODE(WS-LITS-SPECIAL) END-EXEC
Suppose, for example, that program NACT02 successfully adds a new record to the account file, but meets a NOSPACE condition when trying to add the corresponding new record to the index file. The resulting ABEND command issued in program NACT04:
Produces a dump of all the main storage areas related to the transaction. A dump isn’t always needed.
Removes the new record or any changes from the account file, so that the two files are still synchronized with each other, even after the failure.
Returns control to the ABEND handler further up the stack, if none to CICS.
Other Program Control Commands
There are two other program control commands that we’ll mention here, but not cover in detail.
The LOAD command brings a program (any phase (VSE) or load module (MVS) in the list of installed program definitions or in the DFHRPL concatenation) into main storage but doesn’t give it control. This is useful for tables of the type that are assembled and stored in a program library, but doesn’t contain executable code.
The RELEASE command tells CICS that you’ve finished using such a program.
Queuing Facilities: Temporary Storage and Transient Data
CICS provides two queuing facilities: temporary storage and transient data. The following paragraphs tell you how to use temporary storage, both for queuing and as a scratchpad. There is a brief description of transient data in the following section, outlining the differences between the two facilities, and suggests when you might use one or the other.
Temporary Storage
Temporary storage is a set of sequential files, implemented using a VSAM data set on a disk, an area of main storage, or a coupling facility.
The CICS temporary storage facilities allow a task to create a queue of items, stored under a name (16 characters long in CICS TS for OS/390 Version 1.3 and 8 characters in all previous releases) selected by the user program. Each queue, which you can think of as a minature sequential file, exists until some task deletes it. The task that deletes it isn’t usually the same task that created it, although it could be. The queue can contain up to 32,767 items and any number of different tasks can add to it, read it from any point within it, or change the contents of any items in it.
When there is just one item in a queue, we think of this facility as a scratchpad; when there is more than one, we think of it as a queuing facility. The items can be of almost any length up to 32,767 bytes, and they can be of different lengths within the same queue. If you are using the queue as a temporary sequential file, you can think of each item in it as a record.
The simplest use of temporary storage is:
EXEC CICS READQ TS QUEUE(name)
INTO(data-area)
RESP(response) RESP2(reason)There are options to allow you to start where you like, read the next, and find out how many items there are in the queue.
Transient Data
There is another facility in CICS, called transient data, which comes in two flavors—intrapartition and extrapartition:
- Intrapartition transient data
Intrapartition transient data is similar to temporary storage. Both temporary storage and transient data allow you to write and read queues of data items, which are often essentially small sequential files and each queue requires a resource definition called the Destination Control Table (DCT) entry. Like temporary storage queues, intrapartition transient data queues are implemented as a single VSAM data set managed by CICS. However, temporary storage items can be reread whereas with transient data a read is a destructive read. Also, temporary storage items can be read in any order, whereas with transient data they are read in the order that they are written. Table 5-1 illustrates the differences between temporary storage and transient data.
- Extrapartition transient data
Extrapartition transient data is the means by which CICS supports standard sequential access method (SAM) files. The commands used for extrapartition queues are the same as for intrapartition queues, and each queue also requires a DCT entry. In this case, however, a read or write operation is actually a read or write to a sequential file, and each queue is a file. You can either read or write an extrapartition queue, but not both.
The EXEC CICS WRITEQ TD Command
The WRITEQ TD command writes transient data to a predefined symbolic destination. The syntax is as follows:
EXEC CICS WRITEQ TD QUEUE(name) FROM(data-area) RESP(data-area) RESP2(data-area) END-EXEC
The options for this command are:
- QUEUE(name)
Specifies the symbolic name (1–4 alphanumeric characters) of the queue to be written to. The named queue must have been defined to CICS.
- FROM(data-area)
Specifies the data that is to be written to the transient data queue.
The EXEC CICS WRITEQ TD command as used in the NACT04 program
By default we produce messages that are sent to transient data. We also want to display these at the terminal if we have one. In the NACT04 program, transient data is used to send error information to the CICS-supplied extrapartition transient data queue, CSSL. The code is as follows:
MOVE 2 TO WS-ERRH-NUMBER
EXEC CICS WRITEQ TD QUEUE(LO-ERROR-QUEUE)
FROM(MA-STD-INFO)
RESP(MA-RESP) RESP2(MA-REASON)
END-EXECHandling Errors
The NACT04 program is a general-purpose error routine. It isn’t invoked directly by any transaction, but instead receives control from programs NACT01, NACT02, and NACT03 when they meet a condition from which they cannot recover.
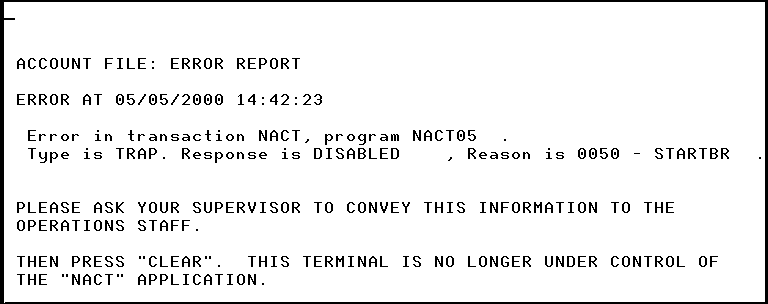
The program sends a screen to the terminal user (see Figure 5-2) with a text description of the problem and a request to report it. The text is based on the CICS command that failed and the particular error that occurred on it. The name of the transaction and the program (and, if applicable, the file) involved are also shown. The command, error type, and program name are passed to the NACT04 program from the program that transferred control to it; other items come from the CICS EXEC Interface Block (EIB). The EIB is a CICS control block associated with a task, containing information accessible to the application program. We’ll look at it in more detail in The EXEC Interface Block (EIB) in Chapter 11.
After writing the screen, the program abends, so that any updates to recoverable resources performed in the half-completed transaction get backed out.
You’ll see the NACT04 program in action in the Execution Diagnostic Facility (EDF) session described in Chapter 16.
As you saw in Figure 4-3, the NACT04 program begins by issuing an EXEC CICS ASSIGN command. This command obtains information from CICS about the environment and the problem. This helps you diagnose a problem and determine whether the NACT04 program was entered using an EXEC CICS ABEND command or whether the application program passed control to it using an EXEC CICS XCTL command or called it using an EXEC CICS LINK command. Alternatively, it could have been called by a COBOL dynamic CALL, although this is not used in the sample application program.
The EXEC CICS ASSIGN Command
The CICS ASSIGN command requests values from outside the application program’s local environment. The syntax is as follows:
EXEC CICS ASSIGN ABCODE(data-area) ABPROGRAM(data-area) ASRAINTRPT(data-area) ASRAKEY(cvda) ASRAPSW(data-area) ASRAREGS(data-area) ASRASPC(cvda) ASRASTG(cvda) FCI(data-area) INVOKINGPROG(data-area) NETNAME(data-area) PROGRAM(data-area) RETURNPROG(data-area) STARTCODE(data-area) TERMCODE(data-area) RESP(data-area) RESP2(data-area) END-EXEC
The options in this command are:
- ABCODE(data-area)
Returns a four-character abend code. (Abend codes are documented in the CICS Messages and Codes manual that is on the CD-ROM). If an abend has not occurred, the variable is set to blanks.
- ABPROGRAM(data-area)
Returns an eight-character name of the failing program for the latest abend. If the abend originally occurred in a DPL server program running in a remote system, ABPROGRAM returns the DPL server program name.
This field is set to binary zeros if it is not possible to determine the failing program at the time of the abend.
- ASRAINTRPT(data-area)
Returns an eight-character program status word (PSW) containing interrupt information at the point when the latest abend with a code of ASRA, ASRB, ASRD, or AICA occurred.
The field contains binary zeros if no ASRA, ASRB, ASRD, or AICA abend occurred during the execution of the issuing transaction, or if the abend originally occurred in a remote DPL server program.
- ASRAKEY(cvda)
Returns the execution key at the time of the last ASRA, ASRB, AICA, or AEYD, abend, if any. CVDA values are:
- CICSEXECKEY
Returned if the task was executing in CICS-key at the time of the last ASRA, ASRB, AICA, or AEYD abend.
- USEREXECKEY
Returned if the task was executing in user-key at the time of the last ASRA, ASRB, AICA, or AEYD abend.
- NONCICS
Returned if the execution key at the time of the last abend was not one of the CICS keys; that is, not key 8 or key 9.
- NOTAPPLIC
Returned if there has not been an ASRA, ASRB, AICA, or AEYD abend.
- ASRAPSW(data-area)
Returns an eight-character program status word (PSW) at the point when the latest abend with a code of ASRA, ASRB, ASRD, or AICA occurred.
The field contains binary zeros if no ASRA, ASRB, ASRD, or AICA abend occurred during the execution of the issuing transaction, or if the abend originally occurred in a remote DPL server program.
- ASRAREGS(data-area)
Returns the contents of general registers 0–15 at the point when the latest ASRA, ASRB, ASRD, or AICA abend occurred.
The contents of the registers are returned in the data area (64 bytes long) in the order 0, 1…, 14, 15.
- ASRASPC(cvda)
Returns the type of space in control at the time of the last ASRA, ASRB, AICA, or AEYD abend, if any. The CVDA values on the ASRASPC option are:
- SUBSPACE
Returned if the task was executing in either its own subspace or the common subspace at the time of the latest ASRA, ASRB, AICA, or AEYD abend.
- BASESPACE
Returned if the task was executing in the base space at the time of the last ASRA, ASRB, AICA, or AEYD abend.
- NOTAPPLIC
Returned if there has not been an ASRA, ASRB, AICA, or AEYD abend.
- ASRASTG(cvda)
Returns the type of storage being addressed at the time of the last ASRA or AEYD abend, if any. The CVDA values are:
- CICS
Returned if the storage being addressed is CICS-key storage. This can be in one of the CICS dynamic storage areas (CDA or ECDA).
- USER
Returned if the storage being addressed is user-key storage in one of the user dynamic storage areas (UDSA or EUDSA).
- READONLY
Returned if the storage being addressed is read-only storage in one of the read-only dynamic storage areas (RDSA or ERDSA) when CICS is running with the PROTECT option on the RENTPGM system initialization parameter.
- NOTAPPLIC
Returned if:
There is no ASRA or AEYD abend found for this task.
The affected storage in an abend is not managed by CICS.
The ASRA abend is not caused by an 0C4 abend.
An ASRB or AICA abend has occurred since the last ASRA or AEYD abend.
- FCI(data-area)
Returns a one-byte facility control indicator. This indicates the type of facility associated with the transaction; for example, X’01’ indicates a terminal or logical unit. A value is always returned.
- INVOKINGPROG(data-area)
Returns the eight-character name of the application program that used the LINK or XCTL command to link or transfer control to the current program. If you issue the ASSIGN INVOKINGPROG command:
In a remote program that was invoked by a distributed program link (DPL) command, CICS returns the name of the program that issued the DPL command.
In an application program at the highest level, CICS returns eight blanks.
In a user-replaceable program, a Bridge Exit program or a program list table program, CICS returns eight blanks.
From a global user exit, task-related exit, or application program linked to from such an exit, CICS returns the name of the most recent invoking program that was not a global user exit (GLUE) or task-related user exit (TRUE).
- NETNAME(data-area)
Returns the eight-character name of the logical unit in the VTAM network. If the task is not initiated from a terminal, INVREQ occurs. If the principal facility is not a local terminal, CICS returns the netname of the remote terminal. If this command was issued by a user transaction that was started by a bridged-to transaction, the value returned is the termid of the Bridge Facility.
- Program(data-area)
Returns an eight-character name of the currently running program.
- RETURNPROG(data-area)
Returns the eight-character name of the program to which control is to be returned when the current program has finished executing. The values returned depend on how the current program was given control, as follows:
If the current program was invoked by a LINK command, including a distributed program link, RETURNPROG returns the same name as INVOKINGPROG.
If the current program was invoked by an XCTL command, RETURNPROG returns the name of the application program in the chain that last issued a LINK command.
If the program that invoked the current program with an XCTL command is at the highest level, CICS returns eight blanks.
If the ASSIGN RETURNPROG command is issued in the program at the top level, CICS returns eight blanks.
If the ASSIGN RETURNPROG command is issued in a user-replaceable module, or a program list table program, CICS returns eight blanks.
If the ASSIGN RETURNPROG is issued in a global user exit, task-related exit, or application program linked to from such an exit, CICS returns the name of the program that control is returned to when all intermediate global user exit and task-related user exit programs have completed.
- STARTCODE(data-area)
Returns a two-byte indicator showing how the transaction issuing the request was started. It can have the following values:
Code
Transaction Start By
D
A distributed program link (DPL) request that did not specify the SYNCONRETURN option. The task cannot issue I/O requests against its principal facility, nor can it issue any syncpoint requests.
DS
A distributed program link (DPL) request, as in code D, that did specify the SYNCONRETURN option. The task cannot issue I/O requests against its principal facility, but can issue syncpoint requests.
QD
Transient data trigger level.
S
START command without data.
SD
START command with data.
SZ
FEPI START command.
TD
Terminal input or permanent transid.
U
User attached task.
- TERMCODE(data-area)
Returns a two-byte code giving the type and model number of the terminal associated with the task. The first byte is a code identifying the terminal type, derived from the terminal resource definition. This is the DEVICE attribute (described in the CICS Resource Definition Guide). The second byte is a single-character model number as specified in the TERMMODEL attribute.
The EXEC CICS ASSIGN command as used in the NACT04 program
First we obtain various information from CICS about the environment and the problem. We use this to determine what actions to take and whether the program was entered using CICS ABEND handling or whether an application program transferred control to it using a CICS XCTL command or called it using a CICS LINK or COBOL Dynamic CALL. The syntax is as follows:
EXEC CICS ASSIGN ABCODE(AA-ABCODE)
ABPROGRAM(AA-ABPROGRAM)
ASRAINTRPT(AA-ASRAINTRPT)
ASRAKEY(AA-ASRAKEY)
ASRAPSW(AA-ASRAPSW)
ASRAREGS(AA-ASRAREGS)
ASRASPC(AA-ASRASPC)
ASRASTG(AA-ASRASTG)
FCI(AA-FCI)
INVOKINGPROG(AA-INVOKINGPROG)
NETNAME(AA-NETNAME)
PROGRAM(AA-PROGRAM)
RETURNPROG(AA-RETURNPROG)
STARTCODE(AA-STARTCODE)
TERMCODE(AA-TERMCODE)
RESP(AA-RESP)
END-EXECThe EXEC CICS INQUIRE PROGRAM Command
Having determined how the error handling program received control (through the LINK or XCTL command), the EXEC CICS INQUIRE PROGRAM is used in two ways: one to confirm that this was the program where the error occurred, and secondly, if it is not, then to browse the other programs to see if it can find the culprit.
The syntax of the EXEC CICS INQUIRE PROGRAM is as follows:
EXEC CICS INQUIRE PROGRAM(name) LOADPOINT(ptr-ref) ENTRYPOINT(ptr-ref) LENGTH(data-area) END-EXEC
Description
The INQUIRE PROGRAM command returns information about a particular program, map set, or partition set installed in your CICS system. All of these resources are load modules and, therefore, CICS uses the same INQUIRE command for all three. To avoid confusion, we use the word module to refer to the object of your inquiry, except in some cases where the option applies only to executable programs.
CICS determines the information you request from both the resource definition and, where applicable, the load module. Information from the module takes precedence over that in the definition if there is a conflict. However, CICS inspects a module only if it is already loaded and is the copy currently available for use. CICS does not do a load for an INQUIRE PROGRAM command, nor attempt to autoinstall a resource for which it has no definition.
- ENTRYPOINT(ptr-ref)
Returns the entry point address of the module, if it is loaded. The top bit of the address is set on if the addressing mode is 31 and off if it is 24. If the module has not been loaded, or is a remote program, or is a Java Virtual Machine (JVM) program, a null pointer (X’FF000000’) is returned.
- LENGTH(data-area)
Returns a full-word binary field giving the length of the module in bytes. A value of 0 is returned if the module has not been loaded in the current CICS session. A value of –1 is returned if it is a remote program, or a JVM program.
- LOADPOINT(ptr-ref)
returns the load address of the module. If it is not currently loaded, or if the program is running under a JVM, a null pointer (X’FF000000’) is returned.
Browsing
You can also browse through the definitions of these three attributes of resources in your system by using the browse options (START, AT, NEXT, and END) on INQUIRE PROGRAM commands. In browse mode, the definitions are returned in alphabetical order, and you can specify a starting point with the AT option if you wish.
This command has introduced an argument value of cvda, which stands for a CICS-value data area. It is implemented in a similarly to DFHRESP, so to test the value returned in the ASRAKEY argument, you would code:
IF AA-ASRAKEY = DFHVALUE(USEREXECKEY)
The EXEC CICS INQUIRE PROGRAM as used in the NACT04 program
NACT04 uses the INQUIRE PROGRAM command as follows:
EXEC CICS INQUIRE PROGRAM(AA-ABPROGRAM)
ENTRYPOINT(WF-ENTRY-POINT) LOADPOINT(WF-LOAD-POINT)
LENGTH(WF-LENGTH)
RESP(WF-RES)
END-EXECAnd for browsing:
EXEC CICS INQUIRE PROGRAM START
RESP(WF-RES)
END-EXEC
PERFORM UNTIL (MA-ABPROGRAM NOT = '*UNKNOWN')
OR (WF-RESP = DFHRESP(END))
EXEC CICS INQUIRE PROGRAM(AA-ABPROGRAM) NEXT
ENTRYPOINT(WF-ENTRY-POINT) LOADPOINT(WF-LOAD-POINT)
LENGTH(WF-LENGTH)
RESP(WF-RES)
END-EXEC
ADD WF-LENGTH TO WF-LOAD-POINT
GIVING WF-END-POINT
IF AA-ASRAPSW-NSI < WF-END-POINT
AND AA-ASRAPSW-NSI > WF-LOAD-POINT
MOVE AA-ABPROGRAM TO MA-ABPROGRAM
END-IF
END-PERFORM
EXEC CICS INQUIRE PROGRAM END
RESP(WF-RES)
END-EXECThe EXEC CICS DUMP TRANSACTION Command
The DUMP TRANSACTION command dumps all, a series, or any single main storage area related to a task, any or all of the CICS resource definitions (DCT, FCT, SIT, or TCT), or all of these together.
Warning
If you issue a DUMP TRANSACTION for a DUMPCODE that is defined in the transaction dump table with SYSDUMP, you also get a system dump.
If there is no entry in the system dump table for the specified DUMPCODE, a temporary entry is made. This entry is lost on the next CICS start. The system dump table is described in the CICS Problem Determination Guide. The syntax for this command is:
EXEC CICS DUMP TRANSACTION DUMPCODE(name)
RESP(data-area)
END-EXECThe option in this command is:
- DUMPCODE(name)
Specifies a name (1–4 characters) that identifies the dump. If the name contains any leading or imbedded blanks, the dump is produced but INVREQ is raised. No entry is added to the system dump table.
If you omit all the options except DUMPCODE, you get the same dump as if you specified TASK, but without the DL/I control blocks.
EXEC CICS DUMP TRANSACTION as used in NACT04
We take a dump but with a code based on the type of error we have encountered. This way we ensure we do not conflict with any CICS dump codes. Note that if these are not wanted, they can be suppressed by operational procedures:
EXEC CICS DUMP TRANSACTION DUMPCODE(DUMP-CODE)
RESP(AA-RESP)
END-EXECThe EXEC CICS SYNCPOINT ROLLBACK Command
The SYNCPOINT ROLLBACK command backs out any updates to protected resources and returns them to a state they were in before this transaction began. The syntax is as follows:
EXEC CICS SYNCPOINT ROLLBACK END-EXEC
ROLLBACK specifies that all changes to recoverable resources made by the task since its last syncpoint are to be backed out. This option can be used to tidy up protected resources in a HANDLE ABEND routine, or to revoke database changes after the application program finds irrecoverable errors in its input data.
Warning
A failure occurring during the backout phase (phase 2) of syncpoint processing does not return an error condition and the transaction is not abnormally terminated. Subsequent units of work in the transaction are allowed to continue normally. See CICS Recovery and Restart Guide for further information.
The EXEC CICS WRITE OPERATOR Command
The WRITE OPERATOR command enables an application to write a message to one or more system consoles and, if necessary, wait for a reply. The command can specify route codes. This is of particular use to application packages that need to issue their own system operator messages.
As a result of a change in the way CICS handles messages sent to the console, text lengths of greater than 113 characters are split into two lines:
EXEC CICS WRITE OPERATOR
TEXT(data-value)
END-EXECTip
If ACTION (or one of the equivalent CVDA values below) is specified, the message is retained until the console operator explicitly deletes it or CICS terminates.
The option for this command is:
The EXEC CICS WRITE OPERATOR command as used in the NACT04 program
By writing these messages out to the sytem operator, we enable automated operations policies to be implemented and this will depend on the way your CICS systems are set up for running transactions. The syntax for this command is:
EXEC CICS WRITE OPERATOR
TEXT(MA-STD-INFO)
END-EXECIn the code there is another WRITE OPERATOR that sends a second message held in data variable MA-XTR-INFO.
Other Commands
In addition to the previous commands, the error handling program also uses a number of other commands including those which enable you to add a date and time stamp in a variety of formats to the messages. They are EXEC CICS ASKTIME and EXEC CICS FORMATTIME. Finally, the command EXEC CICS ISSUE DISCONNECT is used when you need to drop the session of the end user’s terminal. For the details of these commands, look in the CICS Application Programming Reference.
What’s Next…
The last two chapters have given us a clear idea of what is involved in setting up the business logic of a simple CICS application. Most of the remainder of this book looks at the various forms of the presentation logic you can use to access your data.
[2] CEMT is a CICS-supplied transaction that enables administrators to query and alter the state of CICS resources.