Chapter 2. Designing Business Applications
In this chapter:
Chapter 1, looked at the essentials of a business application, and the advantages of using CICS to create and run business applications. It also described how many new types of applications, such as interactive web sites, involve an application server such as CICS. As well as having a long pedigree in supporting traditional business applications, CICS also has all of the characteristics needed to support the new types of applications. In this book we are going to develop a fictitious company called KanDoIT. They have been in business for a number of years and now want to expand their business and benefit from e-business opportunities either through the Web or by using message queuing technology or using clients to link to their CICS servers. Initially they have to set about gathering requirements from users and begin to develop an application that satisfies those needs. Much of the remainder of this book describes the design and the programming of the components of the KanDoIT company’s application.
Before looking at the details of the application, this chapter gives you some more ideas about the facilities that you can exploit in CICS to make writing scalable transactions with integrity easier. It covers the following topics:
The key design elements that you need to consider when developing general business requirements
The CICS facilities that support the key design elements
The process for developing the components of a business application
The Heart of a Business Application
There are three key aspects of a business application design that support the general business requirements outlined in Chapter 1:
These are described in more detail as follows.
Components
An important principle of business application design is to separate program code into components. Although this may sound obvious, this has not always been done and is such an important topic that we are going to spend some time on it.
Components are not the same things as objects, nor are they simply the divide and conquer aspect of implementing a large project. Components are about managing a complex IT environment, keeping it in step with the needs of the business, and about reuse—the ability to use large amounts of an existing application to build a new one. With good component design, you have the ability to enhance a business application rapidly in response to market needs or to exploit a newly-emerging technology with adherence to business rules assured and without loss of auditability.
There are three aspects that fundamentally differentiate the parts of a modern business application:
- Different responsibilities within the overall application
For example, in a bank application, one program might deal with personal accounts, and others with scheduled transactions or cash.
- Different types of responsibility
For example, one program may be dealing with presentation of data to users, another with interest rate calculations or credit to an account which results in the update of databases.
- Different hardware and software platforms
For example, you might have part of an application running in CICS Transaction Server, part running on another server platform, part running on a client workstation, and part running on a web server that presents static HTML and converts business data to dynamic HTML. Some are server components; others are client components.
The advantage of server components is that they are (usually) installed in one place and shared by all users. Therefore they can be maintained easily. The advantage of client components is that users get more predictable response times from the client code. However, because client code is installed in many places, it can be more difficult to maintain unless you employ methods that automatically update client code.
Where you place the function of a business application is determined by finding a balance between achieving good response times and maintainability.
There are also some practical differences; that is, the components may be:
Run in different geographical locations
Run on different types of hardware
Written by different people (in different companies, different groups, or with different skills)
Developed, tested, and deployed at different times
Modified, retested, and redeployed at different times
These differences cannot be ignored. Instead, they must be taken into account when designing and developing an application. In other words, your application should be structured into components.
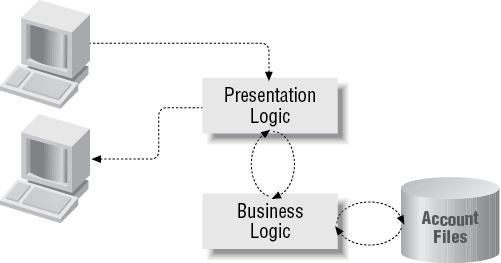
The key components of any business application are business logic components and presentation logic components. The business logic component is responsible for business calculations and updating databases. These components are the hardest to develop, the most critical to the operation of the business, and the most valuable to reuse. Get these right and everything falls into place. The presentation logic components and their component interfaces control the presentation of information to end users. The presentation logic components are represented in this book as the 3270 interface using COBOL, as a web interface using servlets and Java Server Pages (JSP), as a Graphical User Interface (GUI) using Visual Basic, and as a Java program using MQSeries to access data in our CICS application. In Figure 2-1 we show the 3270 frontend. Each of the three other frontends have a similar input screen and account display screen.
Business logic components
The individual functions of a business logic component should be designed to operate in a server environment. Business logic functions typically:
Validate input data
Search the database
Cross-validate input data and database data
Update data (including additions and deletions)
Log activities
Business logic components should do these things in a way that adheres to business rules and ensures their consistent implementation. For example, they should:
Update a journal on a particular database containing sensitive material (such as a payroll) for an audit trail.
Provide the one-and-only approved program that performs complex computations such as interest earned on a deposit account or discount granted on a customer order.
Obey rules imposed by regulatory bodies.
Ensure that consistency cannot be compromised. For example, critical updates that are inextricably linked should be done in the same program.
The criteria for grouping business logic functions into business logic components are pragmatic. Business logic components should:
Encapsulate as much data as possible.
Have an interface that can be tested independently.
Be able to move to another server without affecting other components.
Have a purpose and responsibility that can be discussed in a business context and should not have a purely technical definition such as everything running on a server X.
Presentation logic components
This is the code primarily concerned with the presentation of data to an end user and receipt of data from an end user. It should:
Invoke the general-purpose presentation management code that controls the layout of data on a visual display screen or other output device.
Validate input.
Handle interactions in the correct sequence.
Confirm completeness (that is, that all necessary information has been provided).
Presentation logic may be designed to run on a client. For example, if the user sits at a personal computer, the presentation logic could be a Visual Basic application; if the user uses a web browser, the presentation logic could be a set of Java servlets running on a web server.
Component interfaces
Not all components have interfaces that can be invoked by other components. Those that have invocable variables must:
Publish the interfaces for use when developing client components (which may not be programmed in the same language or run on the same type of machine).
Be tested thoroughly against the interfaces.
Protect the interfaces using security mechanisms.
Make the interfaces available to any executing client, locally or remotely.
A note about traditional CICS applications
Many CICS applications written in the past combined presentation logic and business logic. Such applications are difficult to treat as components. As such, you would have to use the External Presentation Interface (EPI) to do many of the processes that are described in this book. For example, EPI allows a Java program to emulate a CICS 3270 terminal, and start CICS transactions on the server. The program sends and receives data as CICS terminal datastreams. Programming in EPI involves screen-scraping, where you must extract data from a screen-orientated buffer row by row and column by column. It is intended for use by CICS server programs that cannot be modified to be called by the External Call Interface (ECI) due to the tightly coupled presentation and business logic. See Chapter 12, for more information about the ECI.
Transactions
In a business application, a transaction has the same meaning as it does in everyday English—a single event or item of business between two parties. Business application transactions should have the so-called ACID[1] (Atomicity, Consistency, Isolation, and Durability) properties, which are described in more detail later on in this section. However, before explaining what ACID transactions are, consider the problems that can occur with transactions.
Imagine a component that operates on bank accounts. The component has three services that could be invoked by end users, one to add to an account, one to delete from an account, and one to move money between accounts.
The most difficult of these is to move money, because it must do everything necessary to ensure that all the accounts are updated and that the operation only proceeds when appropriate. Consider what would happen if things went wrong—if the server failed or if the database contained errors after some, but not all, of the updates had been done. One customer could have his money withdrawn, without the other customer receiving any money (providing an unintended bonus for the bank!). Or, even worse (for the bank at least!), both customers could receive money, resulting in an unintended loss for the bank.
Also, consider what could happen if two bank employees try to move money from the same account at the same time. If the component is designed to read the database to check whether there are sufficient funds and then update the database with the new balance, one of the updates could be lost.
To prevent problems such as these, we need to create ACID transactions:
- “A” is for Atomicity
To be atomic, a transaction must execute completely or not at all. This means that every file, database, or queue operation within the transaction must execute without error. If any part of the operation fails, then the entire unit of work is terminated, which means that changes to the data are undone. There is no trace of the attempt to execute the transaction. The requirement may exist to log the start of a transaction for audit purposes. If all the operations execute successfully, the transaction can be committed, which means that the changes to the data are made permanent or durable.
- “C” is for Consistency
This means that the transaction taken as a whole does not violate any of the integrity constraints associated with the state of the resources. Obviously, the program itself is the arbiter of consistency in a business sense. In our simple example, moving money should not alter the total amount of money in the accounts.
- “I” is for Isolation
Isolation means that even though transactions execute concurrently, they appear to be serialized. In other words, it appears to each transaction that any other transaction executed either before it or after it, but not simultaneously.
Remember that we are developing a multi-user system accessing a shared database. When some but not all of the updates needed for consistency have been done, the database is inconsistent. When all the updates have been done but the transaction has still not yet committed, the transaction could back out. In either of these cases, allowing other transactions to see or update the records could result in errors in the database.
Isolation means that other transactions can be prevented from seeing or updating the same records. In other words, the data that a transaction accesses cannot affect or be affected by any other part of the system until the transaction is completed. If moving money was not isolated, an inconsistent view of the database would be possible—or worse, concurrent updates could corrupt the database. Complete isolation is logically equivalent to forcing serialization of all transactions against the database, only allowing concurrent transactions that do not affect each other in any way at all.
- “D” is for Durability
This means that after a transaction completes successfully (that is, commits), its changed state survives failures. This normally requires that all the data changes made during the course of a unit of work must be written to some type of physical storage when the transaction is successfully completed.
Trying to implement the ACID properties by unique application code in every business application component would be difficult. It would totally obscure the business logic, making the code difficult to maintain and audit. The problem is that some things are not business issues but technical issues—things the technology should address in order to ensure the code is as easy to write as possible—so as to allow the business logic programmer to focus on the business issues. There is a clear difference between business exceptions, (such as, “the account does not have enough money in it”) and technical exceptions (such as, “the account database has only accepted one of my updates”). Our system software, our middleware, should hide the messy realities of the machinery and present us with services that don’t need us to solve this problem.
Using an application server such as CICS, you can obtain the ACID properties by defining groups of updates that must all be done together. As the transaction proceeds, the updates are done on a provisional basis, and logged. If they all work, you can commit (syncpoint) the changes, that is, make them permanent. But if there are problems you can cancel the changes, that is, back them out. If the system fails—say there is a power outage before you have issued the commit—the system automatically backs out the changes you made. Your program’s responsibility has ended, though the client may need to resubmit the request once power is restored. You can concentrate on ensuring that business exceptions are handled, and you can safely leave the technical exceptions to the system.
Limitations of ACID transactions
Does the above sound too good to be true? You’re right, it is! Here are the potential problems.
- An ACID transaction should be “short,” because it locks shared resources.
Here, “short” is a relative term. In a large system running hundreds of transactions per second, short would be less than a second. It is up to the designer to set a target for the duration of a transaction, but in almost all cases it is undesirable that human think-time be allowed to control the duration of an ACID transaction. This is important because it means the programs should not wait for user input in the middle of a transaction, however appealing it is to ask for user confirmation before committing. Maintaining File Integrity: Using Locking in Chapter 4 shows some of the practical ways to work around this issue.
- ACID transactions should not be “big.”
Here, “big” is also relative. For example, don’t implement a transaction that runs through the entire database correcting telephone numbers due to changes in the national telephone numbering plan. It should not be logically necessary to do this atomically, that is, do one record or row at a time and commit the result before passing it on to the next, because otherwise it would effectively lock out all other users until completed.
- Be aware that under certain conditions a state known as “deadlock” can occur.
This is where two or more transactions are trying to access the same set of resources and each ends up waiting for the others to complete. For example, program A has updated a record with key X and then wishes to update a record with key Y. Program B wishes to do the reverse. Neither can continue because invalid data would result. The system detects this and arbitrarily cancels one of the transactions which, since there is no actual error, should simply retry and start from the beginning.
- Complete isolation may have intolerable throughput implications.
There are cases with adding or deleting records where complete isolation may not be recommended, in situations where, for example, all transactions are serialized. So typically, systems provide the ability to relax the isolation property, allowing improved concurrence while still preventing multiple concurrent updates to the same record.
Error Handling
It is a well known fact that in computing 80% of programming code deals with handling errors and/or exception conditions, that is, with knowing what is supposed to happen, checking that it has, and doing something about it if it has not!
Suppose a device error occurs on a disk—the data will not be available until the disk is replaced and the data restored. But suppose the application that was trying to read the disk failed to check that the operation succeeded and, as a result, wrote incorrect data to another file. Merely restoring the original data will no longer fix the problem, and finding out why the second file contained garbage could be very difficult.
Suppose a software bug in an infrequently used part of a program caused an undetected overwrite of stored data. Not only could subsequent uses of the program fail because some piece of memory is corrupted, but finding out why the problem occurred could be very difficult.
These examples show why handling errors is vitally important. Errors are a fact of life. In developing applications, it is best to remember these two maxims:
“Anything that can happen will happen, usually at the worst possible time.”
“Absolutely anything can happen!”
Errors that disrupt business applications can stop a company doing business until the problem is fixed, so it is vital to detect errors early, clean up after the errors to allow operations to continue, and record diagnostic information so that problems can be fixed quickly.
The need for a methodical approach
In component-based applications, errors mostly occur in the interface between two components. It is therefore important to document and test the interfaces in a methodical way. Also, components are supposed to hide complexity from their users, so we want to notify errors in a simple way from the user’s point of view.
How is that done? First, some definitions:
- Fault
Something going wrong, such as a LAN (Local Area Network) failure, software bug or unexpected data received.
- Error
- Abend (Abnormal ending)
The situation where program execution cannot continue normally, such as a storage violation.
- Error notification
The passing of information that an error has been detected from one component to another component. This can either be by return code or by executing an abort command.
- Signalling component
The component that notifies an error.
- Receiving component
The component to which notification of an error is given.
As for noticing an error, we need to decide if there is a fault causing it. Not all errors are the result of a fault; for example, a module issuing a database read command that returns a “record not found” error may regard the error as acceptable.
If there is a fault, you need to:
Record enough diagnostic information so that computer support staff can quickly determine what the fault is and correct it.
If possible, bypass the error so that no other components are affected by the problem.
If the error cannot be bypassed:
Clean up as much as possible.
Notify other components of the error.
For presentation logic components, provide clear instructions to end users regarding who to inform about the error and what to do to continue working.
In practical terms, the above guidelines translate to the following:
During design:
Always specify that component interfaces must have return codes.
Consider what the end user should do when errors occur.
During development:
You’ll find more information about error handling in Handling Errors in Chapter 4, which looks at error handling in the COBOL business logic component of the sample application.
How CICS Can Help the Application Designer
A business application should incorporate the key design elements of components, transactions, and error handling. This section provides some more background to show how CICS supports the application designer to structure an application so that it meets the business requirements described in Chapter 1, and incorporates the key design elements. CICS provides the following facilities:
An environment for executing presentation logic and business logic components
Calls between components
Efficient control of concurrently running application programs serving many online users
Provision of ACID properties through management of the units of work (see the following section)
Shared error handling
System management
It’s useful at this point to look at CICS transactions, and CICS programs and linking, in more detail. We’ll also consider how CICS deals with critical activities such as error handling and security.
CICS Transactions
In a CICS application, a transaction is the processing initiated by a request, usually from an end user. A transaction starts, executes, and ends. A single business transaction (such as the enrollment of a new customer) may involve several CICS transactions.
Tip
As well as referring to a single event, transaction can also refer to the class of similar events. Thus, we speak of adding Mary Smith to the payroll file with a (single) add transaction, but we also speak of the add transaction, meaning the class of additions to that particular file.
A CICS transaction may contain one or more Units of Work (UOW) where a UOW begins with the first action to alter a protected resource and ends with either an explicit or implicit syncpoint. To summarize, a business transaction involves one or more CICS transactions that, in turn, can involve one or more units of work.
When processing transactions, CICS accumulates performance statistics and monitors the resources used. This provides the information that enables user departments in your organization to be charged accordingly. It also allows you to find out which parts of CICS are being heavily or lightly used. This helps your systems managers to tune the system to improve its performance.
CICS Programs and Linking
A program is the smallest replaceable unit of an application. Programs are compiled, linked or bound, and turned into a single executable file which is then deployed. They can be written in many languages and run in many different environments. A component of a business application typically consists of multiple programs.
CICS provides a variety of ways for programs using CICS to invoke and be invoked by other programs running inside or outside CICS, for example on web servers or end-user workstations. Program calls can be:
- Synchronous
Control is not returned to the calling program until the call is complete.
- Asynchronous
The calling program continues executing while the call is performed. The access method informs the application program after the operation is completed.
Synchronous calling between programs
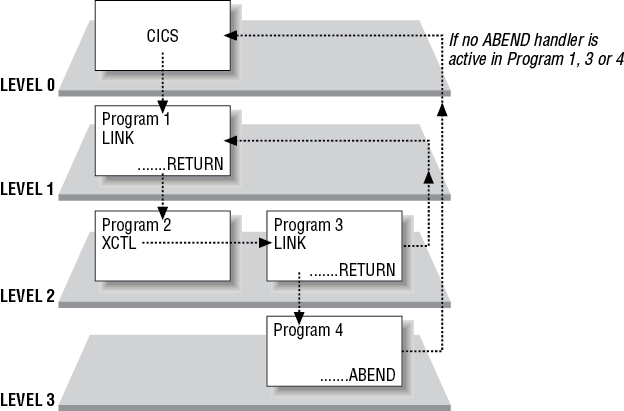
There are two main ways in which one program can invoke another program inside CICS. These are discussed in more detail in Commands for Passing Program Control in Chapter 5. For the time being suffice it to say that the CICS API consists of a number of commands that define resources, make calls to other programs and so on. In this book you will meet a wide range of these commands particularly in Part II and Part V. Two of these commands create links from one program to another. Figure 2-2 shows the linking process and relationship of one program to the next. The commands are:
- EXEC CICS LINK
Allows one program to transfer control to another in a synchronous manner and continue execution after the called program has returned. This also occurs by means of native programming language facilities such as a COBOL CALL statement.The LINK Command in Chapter 5 gives more detail.
- EXEC CICS XCTL
Allows for one program to call another in a synchronous manner but unlike LINK will not receive control back when the called program returns. This has no equivalent high-level language facility. It is particularly useful in error processing when an unexpected error is detected that implies that the program which trapped the error cannot continue. The XCTL Command in Chapter 5 gives more details.
In both cases a COMMAREA (for “communication area”) is used to pass parameters and returned values. For more information about COMMAREAs see Saving Data: Using a Scratchpad Facility in Chapter 5.
The LINK and XCTL commands introduce the idea that different programs involved in the processing for a transaction can be executing at different logical levels. A program invoked directly by CICS is considered to be at the highest logical level of the task (level 1). If it then uses the LINK command to link to another program then the linked-to program is considered to be at a lower logical level (level 2). However, if the program detects an unexpected condition it can use XCTL to call an error handler which will be considered by CICS to be executing at the same logical level as the program issuing the XCTL request. Figure 2-2 illustrates this principle.
Asynchronous calling between programs
One CICS program can invoke another asynchronously passing data in the FROM area defined in the EXEC CICS START command. The program for which START has been issued is executed as logical level 1, independent of the level of program that issued the START. The FROM area can be accessed by executing a RETRIEVE command.
Alternatively you can use MQSeries. This is discussed in Working with MQSeries, later in this chapter.
Calling CICS programs from non-CICS programs
CICS provides a number of ways in which non-CICS programs executing on a variety of hardware and software platforms can call CICS programs. In fact, there are more ways than we are able to describe in this book, but here are a few examples:
A software package known as the CICS Client provides the ECI and EPI facilities:
- ECI (External Call Interface)
Allows the calling program to call a CICS program as though it had been linked to (using the LINK command) by another CICS program. The ECI uses a COMMAREA.
- EPI (External Presentation Interface)
Allows the calling program to call a CICS program as though it had been invoked by a user at a 3270-type device.
The CICS Client is designed to run on end-user workstations and meet the needs of a single user running programs that invoke CICS programs. Our sample application makes use of the CICS Client ECI function call.
For programmers using the ECI or EPI, there are application tools that build some of the program calls automatically. One such tool is VisualAge Interspace. The sample application demonstrates the use of Interspace.
For server applications, a software package known as the CICS Transaction Gateway also supports the ECI and EPI. The CICS Transaction Gateway would be used, for example, by programs running under the control of a web server.
When the calling program is written in Java, there is a pure Java version of the ECI and EPI facilities that access the CICS Transaction Gateway using TCP/IP.
Finally, a CICS program written in Java can be invoked using the Internet Inter-ORB Protocol (IIOP); the sample program uses IIOP.
Defining resources
CICS has a set of resources that are grouped into categories, for example, File Control (FC), Temporary Storage (TS), and so on. These resources can be defined in batch using the DFHCSDUP utility program or online using the Resource Definition Online (RDO) transactions. A historical note: several years ago, many resources were assembled (sic) together into tables; so, for example, File Control resources were aggregated into a File Control Table (FCT).
Working with MQSeries
For asynchronous processing, you can achieve the greatest flexibility by using IBM’s broad range of MQSeries products. Neither the calling program nor the called program needs to know anything at all about where or when the other program executes because MQSeries provides a common set of facilities for sending and receiving messages, takes responsibility for routing messages to the required location, and holds the message until the receiving program wants it. The sample application uses MQSeries to invoke a CICS program.
Error Handling Facilities
Error handling facilities are critical in any application. CICS includes several error handling facilities, including:
ABEND
Return codes in commands
DUMP
TRACE
Sending messages to system consoles where operators can respond to the problems
These are described in more detail in Handling Errors in Chapter 5.
Security
Security is a complex subject that requires careful planning before it is implemented; as such, it is not dealt with thoroughly here. As we have already mentioned, many people, with many different roles, interact with business applications and the security, auditability, and accuracy of the application depends on these roles being kept separate and identifiable. Therefore it is natural that security of business applications should be role-based.
Once each user’s role has been understood, security can be implemented on the following basis:
- Authentication
Where the user’s identities are verified, typically using a user ID and password approach
- Authorization
Where an attempted action by a user is checked to see whether it is permitted
CICS works in co-operation with OS/390 security managers (for example, Resource Access Control Facility (RACF), Access Control Facility (CA-ACF2), or TopSecret) to implement this role-based security, with CICS calling the security manager as required to provide the authentication and authorization checks. CICS can request up to three types of authorization check: transaction security, resource security, and command security.
Transaction security
This is the normal sort of security applied to business applications. All CICS applications, whether started by a user at a terminal or a program connecting to CICS, run under a transaction. Consequently, using transaction security to check the authorization of an authenticated user to initiate the transaction is usually sufficient to protect the resources accessed by the transaction.
Resource security and command security
In some situations, for example where applications require varying levels of access to different users within the same transaction, a more granular approach can be required. In these cases resource security and command security may be applied, as required, to restrict access to specific resources. For example, a transaction that prints any file might use resource-level security to prevent users printing files they are not authorized to see.
Alternatively, command-level security could be used; for example, a transaction that allows the user to select CICS commands to issue could use CICS command security to prevent a user from issuing commands that set the status of a file.
CICS security is applied only to resources owned by CICS. Although a resource security check could be made against a CICS file, this would have no relevance to the underlying security on, for example, its base implementation by a VSAM data set.
CICS resource security and CICS command security are not needed for normal business applications; indeed using them in the wrong situations can give a false sense of security. They do not protect resources from what programmers might do accidentally or deliberately. For example, use of resource security would not prevent the programmer of the payroll update transaction inserting code into the transaction which when executed by others gives the programmer unauthorized pay increases. To guard against this sort of threat, it is necessary to use anonymous peer code reviews.
Other Services for the Application Designer
CICS uses operating system services on behalf of components. However, it doesn’t merely duplicate the services but adds value by providing additional services for running transactions. These services include:
Communication with devices and subsystems.
Recoverable access to shared databases and files, in conjunction with the various database products and data access methods that are available.
Communication with other CICS systems and database systems, both in the same computer and in connected computer systems.
The programming facilities CICS provides are:
- A choice of programming language
You can write your application programs in IBM Assembler, COBOL, PL/I, C, C++, REXX, or Java languages.
- An application programming interface
You need know a little about how CICS works. You request services by issuing CICS commands consistent with the programming language you are using. For example, in COBOL, the EXEC CICS command, or in Java, the JCICS classes.
- An execution diagnostic facility (EDF)
This is used for displaying and changing parameters in command-level application programs, that is, those that use the EXEC CICS command interface interactively.
- A remote edit, compile, and debug capability
This is used in conjunction with the VisualAge compilers for OS/390.
Developing the Components of a Business Application
Having looked at the key elements of a business application, and how CICS addresses these elements, it’s time to consider the process for developing the components of a business application. The stages of the process are:
Design
Programming
Test and debug
Deployment
Design
It’s important to ensure that there is agreement on what each component is required to do. Make sure you document the design of your component thoroughly, and share it with people who are designing other components. Document your component’s interface, if it has one that other components use. Include assumptions about performance and capacity.
If your component has a user interface, test it out on paper first by drawing all of the proposed screens, and asking some of the intended users to check your design by attempting to “use” the screens. Put yourself in the position of the computer, in order to check what happens when it makes a functional request.
Finding problems at the design stage is essential; it is much cheaper and quicker to fix them earlier rather than later.
For each component in our sample application, you will find that there is a chapter describing the design. In these chapters we consider the factors influencing the design of the component, which lead to the decisions made by the component designer.
Programming
Read the design document! The main job of the programmer is to implement the design, as documented. At the same time, the programmer should follow:
Good practice for the language in which the component will be written.
Good practice for the environment in which the component will be running.
Local conventions with regard to file naming, and so on.
For each component in our sample application, we show how to convert the design into a working program.
Test and Debug
Testing is an integral part of any software development, and must be as carefully prepared and implemented as the development of the product itself. There are many different methods for testing and several standards have been developed. It is outside the scope of this book to describe testing standards in detail; however, here are a few useful guidelines:
Test each component in isolation.
Test the application as a whole, that is, from end-to-end. This book covers:
Visual Basic to COBOL
MQSeries to COBOL
Web to Java to COBOL
IBM 3270 green screen using CICS BMS (Basic Mapping Support) to COBOL
Load/Stress the application:
Concurrent users
Running in a system with a high workload
Your testing will inevitably uncover errors in the component’s logic or programming. These then need to be removed, a process known as debugging. Chapter 16, describes some of the debug tools available in CICS, and shows some sample debug screens.
Deployment
Once each component has been designed, programmed, tested, and debugged, it must be deployed correctly. At the same time, the configuration files for the various runtime products must be updated to recognize the components.
Appendix A describes the deployment of our sample application.
What’s Next…
Enough about the background; the next chapter introduces the sample application that will be developed throughout the remainder of the book.
[1] The term “ACID properties of a transaction” was coined by Haerder and Reuter in 1983 and used by Jim Gray and Andreas Reuter. In CICS, ACID properties apply to a “unit of work” (see CICS Transactions).