In this chapter, you will learn about system hacking, which includes being able to recognize various types of password attacks, use password cracking tools, and detect password cracking countermeasures. System hacking involves using rootkits and additional tools that cover the tracks of attackers, which will also be discussed in this chapter.
Identify different types of password attacks.
Use a password cracking tool.
Identify various password-cracking countermeasures.
Identify different ways to hide files.
Recognize how to detect a rootkit.
Identify tools that can be used to cover attacker tracks.
Password Attacks: Passive Online Attacks
After completing the enumeration and scanning phases, an attacker then looks to discover user accounts or hosts with weak security configurations. System hacking includes cracking passwords, using keyloggers, and employing spyware. Installing rootkits and using steganography also falls into the category of system hacking.
- Passive: With a passive password cracking attack, an attacker sniffs network traffic to find out if any password information is revealed.
Wire sniffing only functions in a common collision domain, with the attacker running a sniffer on one of the LAN’s systems.
Man-in-the-middle and replay attacks sniff both sides of a connection at the same time. This is common in telnet and wireless technologies and is hard to implement owing to TCP sequence numbers and speed. Replay attacks acquire packets with a sniffer, extract the information, and then place the packets back on the server.
Active: Password guessing is one of the more effective active online attack techniques. Information that was gathered through reconnaissance and enumeration may now be useful. An example of an active online attack includes password guessing. Password guessing occurs when an attacker builds large dictionaries that include words from foreign languages, proper names, and commonly used passwords. In this instance, attackers scan user profiles to look for clues.
- Offline: Passwords should never be stored in plain text. A hashing algorithm is usually used. A number of offline attacks, detailed below, are available.
Pre-computed hashes verify logon usernames and passwords against a system-wide list. The file containing the list must always be encrypted, because if the file has the encrypted password in readable format, the hash function can be identified by the attacker.
A syllable attack is a mix of brute force and dictionary attacks that utilizes each possible combination of words in the dictionary.
A rule-based attack takes place if the attacker has some password details (i.e., that the password contains a two-digit number).
In a network distributed attack, the attack makes use of the network’s unused processing power to decrypt passwords. Machines running DNA clients can access the DNA manager that is installed in a central location.
A rainbow attack takes place when the password hash table (known as the rainbow table) is produced and saved in memory. The rainbow table can be used to retrieve a plaintext password from a ciphertext.
Nontechnical: Password attacks do not necessarily mean that technology is being used. Sometimes a password attack can be the result of some keen observation or a manipulation of others. Examples of nontechnical attacks include shoulder surfing, keyboard surfing, and social engineering.
Password Attack Example
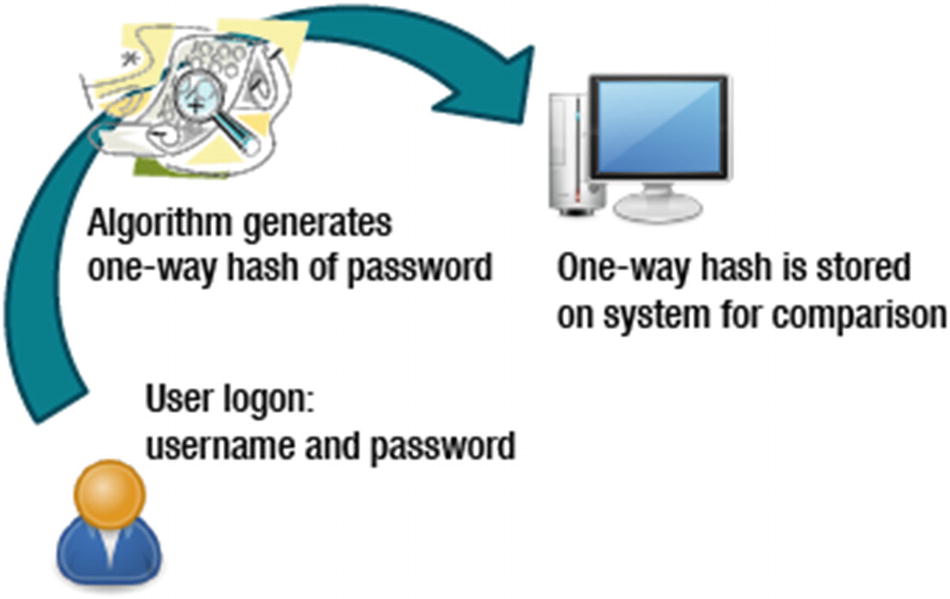
A password attack
Null Sessions
Null sessions can be established by connecting to a share without supplying a username or password. A null session allows the unauthenticated host to collect data such as password policies, usernames on local machines, and account lockout policies.
Shared resources can be listed by using the command Net View \TargetComputerName. Port 139 or 445 must be open for a null session to be successful.
Trusted domains for resources enumeration
Computers outside the domain for user authentication and enumeration
The SYSTEM account for authenticating and listing resources
NetBIOS null sessions allow read and write access with Windows NT/2000 and read access with XP and 2003. Prevention measures include firewalls, disabling Netbios over TCP/IP, adding RestrictAnonymous=1 to HKLMSYSTEMCurrentControlSetControlLSA. Utilities such as Desktop Sentry allow you to see who is connected to your machine , giving you a user name and IP address.
For more information, read Null Session Vulnerability (http://msdn.microsoft.com/en-us/library/ms913275(v=winembedded.5).aspx)
Authentication
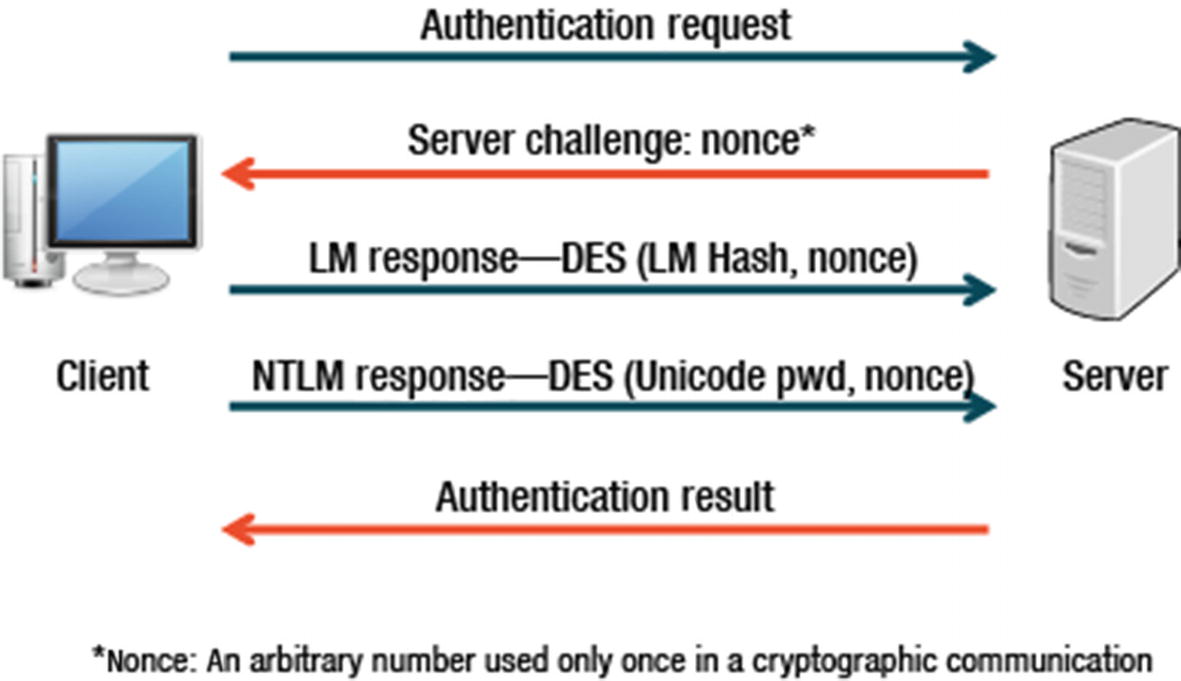
Authentication
- 1.
A network path to the server is established by the client.
- 2.
The server responds with a challenge message that is used to establish the client’s identity.
- 3.
The client responds to the challenge with one or both of two hashed password values (which are stored on the server). If the hash value is grabbed by an attacker, the attacker can authenticate without knowing the password.
Kerberos Operation
Kerberos employs powerful encryption to prove the identity of the client to a server and the server can in turn authenticate itself to the client.
To illustrate how the Kerberos authentication service works, think about your driver’s license. You can present your license to other parties to prove you are who you claim to be. Because other parties trust the state in which the license was issued, they will accept your license as proof of your identity.
The server of Kerberos includes user IDs and hashed passwords for all users who have realm services authorizations.
The Kerberos server also has secret keys exchanged with each server to which it grants access tickets.
The foundation for authentication is the ticket in a Kerberos environment. Tickets are used with the client in a two-stage process. The first ticket is a ticket-granting ticket (TGT) given to the requesting client by the AS. This ticket can then be presented by the client to the Kerberos server with a ticket request to access a particular server. This client-to-server ticket (also known as a service ticket) is used to obtain access to the service in the realm of a server.
As it is possible to encrypt the whole session, this prevents the potentially unsafe transmission of items that can be captured on the network , such as a password.
Tickets are time-stamped and also have a lifetime, so trying to reuse a ticket won’t work. See Figure 4-3.
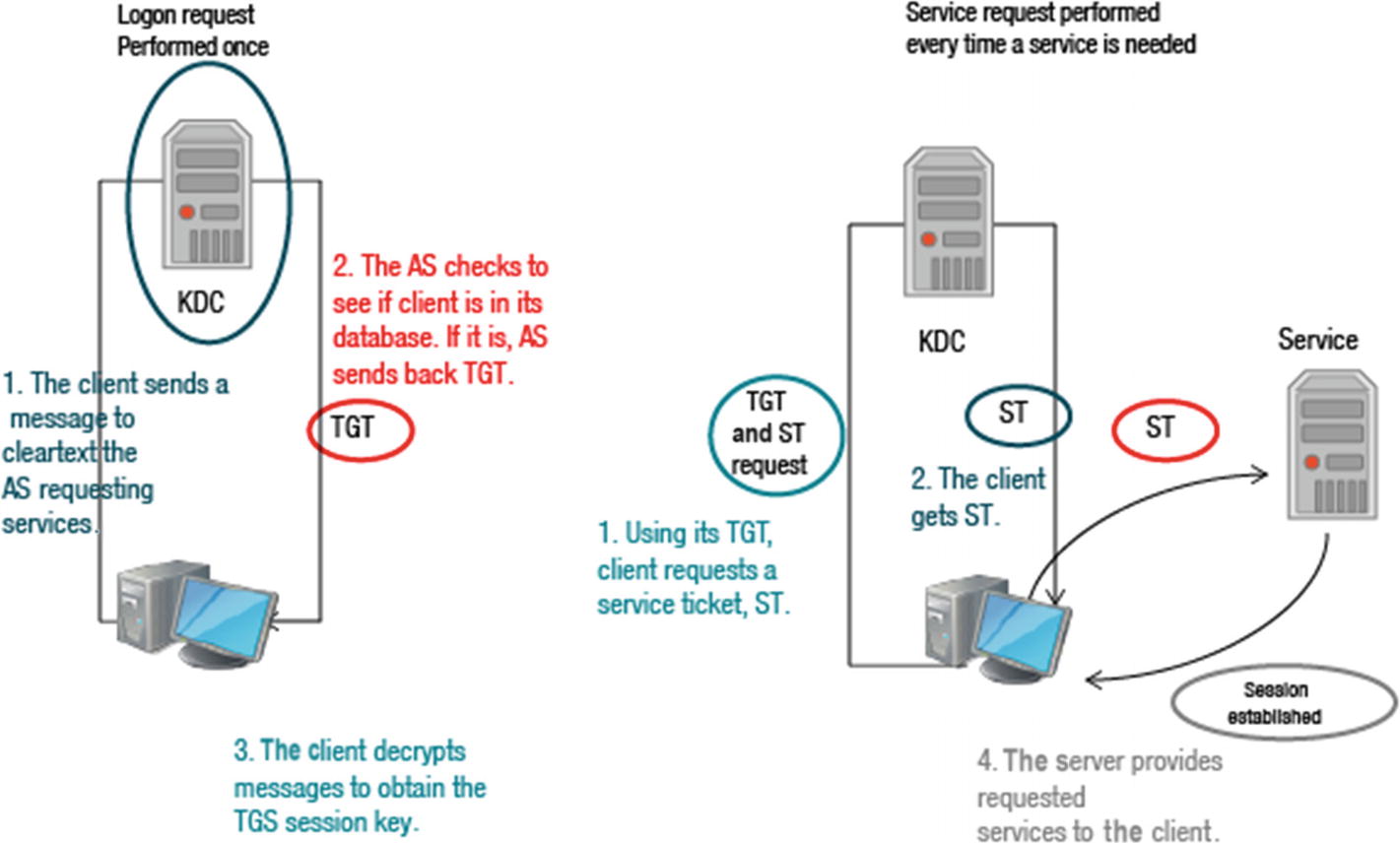
Kerberos operation
Password Cracking Countermeasures
The LAN Manager or LM hash is the default hash for systems running DOS, Windows 3.11, 95, ME, NT, 2000, XP, and Windows 2003.
NT hash is the default hash used for Windows Vista, 7, 8, Server 2008, and Server 2012. Kerberos authentication is not available in earlier versions.
The LM hash is less secure than NT hashes.
- 1.
Implement the NoLMHash Policy using Group Policy.
- 2.
Implement a NoLMHash policy by editing the registry.
- 3.
Locate HKEY_LOCAL_MACHINESYSTEMCurrentControlSetControlLsa, click Add Key, and type NoLMHash.
- 4.
Use a password longer than 15 characters (LM hashes cannot be used with passwords of that size).
Escalating Privileges
SYSTEM account is reserved for the Windows operating system and has unique access to the drive.
Network Service is a predefined local account with less authority than SYSTEM used by the system programs that run on a computer that need access to the network.
Local Services are used by system programs that run on a computer that do not need access to the network.
Password Cracking

Example of a brute force attack
Example of a cryptanalysis attack
Keyloggers
Keyloggers can be either hardware- or software-based. A keylogger captures a user’s keystrokes, records the data in a file, and saves, emails, or transfers the file per the settings configured.
The user is usually unaware of the fact that they are being monitored, and the attack can be a hardware- or software-based approach. Countermeasures include keeping anti-virus software up to date, looking for suspicious processes running, and physically checking the computer hardware.
Hiding Files
Computer files have attributes such as the file’s length, when it was created, accessed, and last modified, and if is hidden, archived, or read-only. The attrib command is used to display or change file attributes.
The Microsoft NTFS file system contains forks known as alternate data streams which are used to store author or title attributes or image thumbnails. APIs and command line tools can be used to create and access forks. Windows Explorer and the DIR command ignore forks.
A fork is a byte stream associated with a file system object, and every file has at least one fork. Forks may contain primary data integral to the file, or just metadata (www.2brightsparks.com/resources/articles/ntfs-alternate-data-stream-ads.html).
Rootkits
Rootkit detection is tricky because the rootkit can undermine the software that would find it. Removal is complicated or virtually impossible if the rootkit is in the kernel. Reinstalling the operating system may be the only way to eradicate the problem.
Rootkits hide the existence of certain processes or programs from being detected by using normal methods (auditing, logging, IDS). They provide an attacker privileged access to a computer and are configured to track traffic, generate log files, and create backdoors such that the attacker has continuous access to the system. An attacker can almost entirely conceal files inside the system by using alternate data streams.
- 1.
Run dir /s /b /ah and dir /s /b /a-h inside the potentially infected OS and save the results.
- 2.
Boot into a clean CD, run dir /s /b /ah and dir /s /b /a-h on the same drive, and save the results.
- 3.
Run a clean version of WinDiff from the CD on the two sets of results.
When a rootkit is detected, there are countermeasures that can be taken. A reactive countermeasure is to back up all critical data, excluding the binaries, and perform a fresh installation from a trusted source. You can also use code checksumming. Another option is to boot in safe mode with minimal device drivers, which makes the rootkit’s hidden files visible.
Steganography
Steganography is the technique of concealing data behind other data. When this is accomplished, bits of unused data in image, sound, text, audio, or video files are replaced by other data. The least-significant-bit insertion method is commonly used to hide data. The least-significant bit of each byte within the image can be overwritten using a binary representation of the hidden data. The steganography tool creates a copy of the palette of an image. The LSB of the 8-bit binary number of each pixel is substituted with one bit from the hidden message, creating a new RGB color in the copied palette, and changing the pixel to the 8-bit binary number of the new RGB color.
Steganalysis is the process of detecting messages hidden using steganography and extracting the data. The steganalytic tools use a detection, extraction, or destruction approach .
Covering Tracks
Attackers clean up after themselves by trying to get rid of the evidence. Rootkits can disable logging entirely and discard all existing logs. Auditpol.exe can disabling auditing, and clearing the event log can be done by DumpEventLog, Event Viewer, ElSave, and WinZapper. Other tools that get rid of an attacker’s tracks are Evidence Eliminator, Traceless, Tracks Eraser Pro, Armor Tools, and Zero Tracks.
Summary
In this chapter, you learned how attackers crack passwords and you learned the countermeasures to prevent this from occurring. You now understand the different ways to hide files and why attackers install rootkits. Lastly, you now know what tools attackers use to cover their tracks.
