A number of malicious programs contain features of viruses, worms, Trojans, and rootkits. These malicious programs are written for a number of reasons including pranks, financial gains, or to distribute political messages. In this chapter, you will learn the various ways a Trojan can infect a system, specific countermeasures to be aware of, and how to recognize a virus, including virus detection methods and countermeasures.
- 1.
Explain how a Trojan infects a system.
- 2.
Identify ports used by Trojans and Trojan countermeasures.
- 3.
Identify the symptoms of a virus.
- 4.
Describe how a virus works.
- 5.
Identify virus types, virus detection methods, and virus countermeasures.
Trojan Horses
Trojans are malicious programs that can cause considerable damage to both the hardware and software of a system. Backdoors are ways to access a device without following the usually required security and authentication procedures.
A legitimate communication path on a network or within a computer system that transfers data is referred to an overt channel . A channel that transfers information and violates the security policy is referred to as a covert channel. To create a covert channel, an overt channel can be manipulated. The Trojan is a simple type of a covert channel.
A Trojan horse, or simply a Trojan, is a malware that is apparently a normal, useable program but actually contains a virus. During the Trojan War, the Greeks used a Trojan horse to obtain access to the city of Troy. Likewise, a Trojan horse enters the victim’s computer undetected and has the same level of privileges as the victim. It can falsely implicate a remote system as an attack source.
A Trojan steals sensitive information, stores illegal materials, and is used as an FTP server for pirated software. A Trojan runs in stealth mode and can alter the registry or other auto-starting methods.
A backdoor is a method used to bypass the usual authentication methods on a system. There are numerous ways that a Trojan can infiltrate a system, including instant message applications, Internet relay cache, attachments, physical access, browser and email software bugs, file sharing, fake programs and freeware, and accessing suspicious sites.
Indicators of a Trojan Attack
CD-ROM drawer opens/closes automatically
Computer screen blinks or is inverted
Backgrounds/wallpaper settings change automatically
Color settings change automatically
Anti-virus is automatically disabled
Date and time change
Mouse pointer disappears
Pop-ups suddenly appear
If a system experiences any of the symptoms mentioned, it warrants a closer look as to what exactly is going on with that system.
Ports Used by Trojans
Ports Used by Trojans
Trojan | Protocol | Port |
|---|---|---|
Back Orifice | UDP | 31337 or 31338 |
Deep Throat | UDP | 2140 and 3150 |
NetBus | TCP | 12345 and 12346 |
Whack-a-mole | TCP | 12361 and 12362 |
NetBus 2 | TCP | 20034 |
GirlFriend | TCP | 21544 |
Devil | TCP | 65000 |
Evil | FTP | 23456 |
Sub Seven | TCP | 6711, 671, 6713 |
Portal of Doom | TCP, UDP | 10067, 10167 |
Netstat Command

Netstat results
Types of Trojans
Remote Access Trojans provide full control over the victim system.
Data-Sending Trojans can install a keylogger and can provide access to confidential data.
Destructive Trojans will delete files on the target system. A DoS Attack Trojan allows the attacker to start a distributed denial-of-service attack.
Proxy Trojans turn the target computer into a proxy server, making the computer accessible to the attacker.
FTP Trojans open port 21, allowing the attacker to connect via FTP.
Other Trojans can disable antivirus software, create ICMP tunnels, or permit attackers to bypass firewalls.
ICMP Tunneling
Arbitrary data is injected into an echo packet sent to a remote device via ICMP tunneling . In the same fashion, the remote machine responds by injecting a response into yet another ICMP packet and returning. Using ICMP echo request packets, the client conducts all communication, while the proxy utilizes echo reply packets. This vulnerability exists because the RFC for governing ICMP packets allows for an arbitrary data length for any echo reply or echo message ICMP packets.

ICMP tunneling
Tools Used to Create Trojans
Backdoor tools include Tini, Icmd, NetBus, and Netcat.
Concealment tools include Wrappers, EXE Maker, Pretator, Restorator, and Tetris.
Remote access tools include VNC, RemoteByMail, and Atelier Web Remote Commander.
Shell and tunneling tools include Windows Reverse Shell, Perl-Reverse-Shell, XSS Shell, XSS Tunnel, and Covert Channel Tunneling Tool.
Other tools include SHTTPD Server, Trojan Horse Construction Kits, Rapid Hacker, SARS Trojan Notification, and T2W (Trojan to Worm).
Trojan Countermeasures
- 1.
Do not download files from unknown sites.
- 2.
Do not use the preview panes in programs.
- 3.
Run antivirus, firewall, and intrusion detection software on your desktop.
- 4.
Delete suspicious device drivers.
- 5.
Scan for suspicious open ports, running processes, and registry entries.
- 6.
Run a Trojan scanner.
- 7.
While downloading useful files, do not download other programs; this may result in infections of viruses that can steal your personal data.
Detecting Tools
To detect a Trojan, scan for suspicious open ports. Then scan for suspicious processes that may be running. Scan the registry. Use a tool such as Wireshark to scan for suspicious network activity. Finally, run a Trojan scanner. A few more tools that can be used to detect a Trojan are Netstat, fPort, TCPView, CurrPorts, PrcView, Msconfig, Autoruns, and HijackThis.
Backdoor Countermeasures
The countermeasures listed will help protect a system from having a backdoor created and thereby providing access to an attacker. Care should always be taken when downloading email attachments or installing applications downloaded from the Internet. If the site provides a hash value for a file download, make sure that you verify the value after downloading the file to insure that the file has not been tampered with. You should use an antivirus package that can recognize a Trojan signature and keep your applications updated with the latest security patches.
Countermeasure Tools
Anti-Trojan software includes TrojanHunter, Comodo BOClean, Spyware Doctor, and SPYWAREfighter.
Backdoor tools include Tripwire, System File Verification, MD5sum.exe, and Microsoft Windows Defender.
Process Monitor

Process Monitor summary example
Malware Tool: Poison Ivy
User-friendly malware applications such as the Poison Ivy Remote Access Trojan are often used by cybercriminals to enable them to conduct a lot of post-exploitation activities, such as loading malware, executing programs, deactivating services, disrupting processes, and stealing information.
Poison Ivy is a highly dangerous malware tool because it allows hackers to establish a continuous connection to a victim’s machine via an encrypted connection. Poison Ivy has been used as an attack tool in many high-profile incidents, including an attack on the RSA network in 2011.
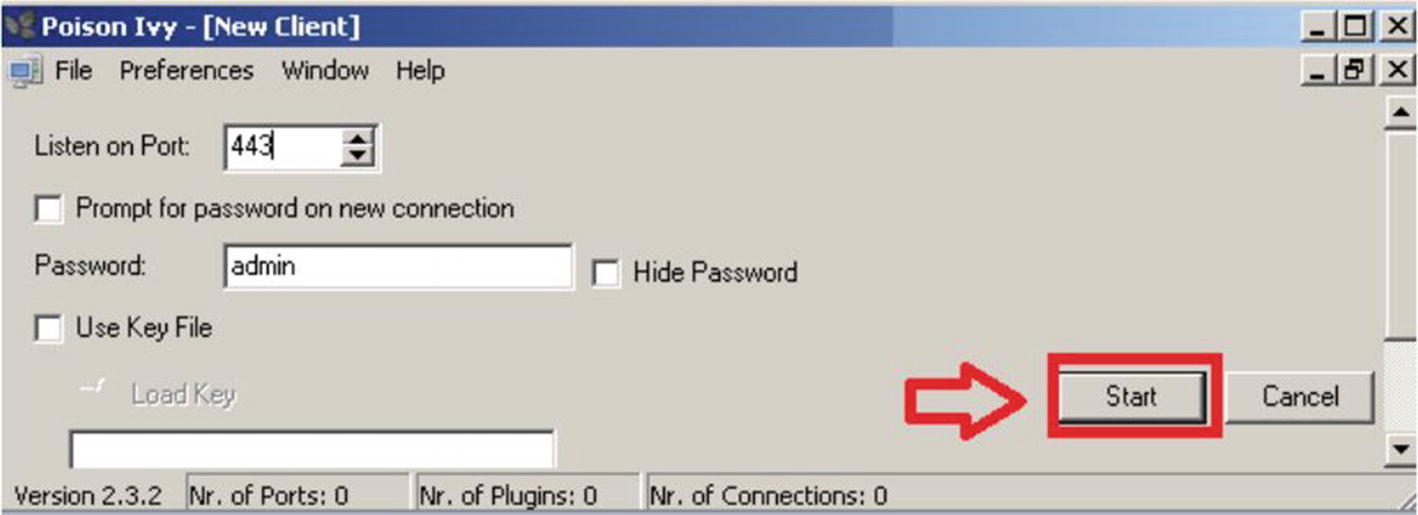
Poison Ivy listening to ports
Viruses and Worms
A virus requires a host, a program or file that enables it to spread from one computer to another. A virus is spread by human action, like opening an attachment or running a program.
A worm is self-replicating. Human action is not required. A worm spreads from computer to computer via the network utilizing a security hole.
Symptoms of a Virus
Recognizing the symptoms of a virus means you can act faster to limit the damage to your system or your network.
- 1.
Programs take longer to load.
- 2.
Hard drive is always full.
- 3.
Unknown files keep appearing.
- 4.
The keyboard or computer emits strange or beeping sounds.
- 5.
The computer monitor displays strange graphics.
- 6.
File names turn strange, often beyond recognition.
- 7.
A program’s size keeps changing.
- 8.
The memory on the system seems to be in use.
Technical damages because resources such as memory, CPU time, and network bandwidth are wasted.
Ethical or legal damages result due to unauthorized data modification, copyright, or ownership problems.
Psychological damages such as trust problems and lack of knowledge round out the mayhem.
Stages of a Virus’ Life
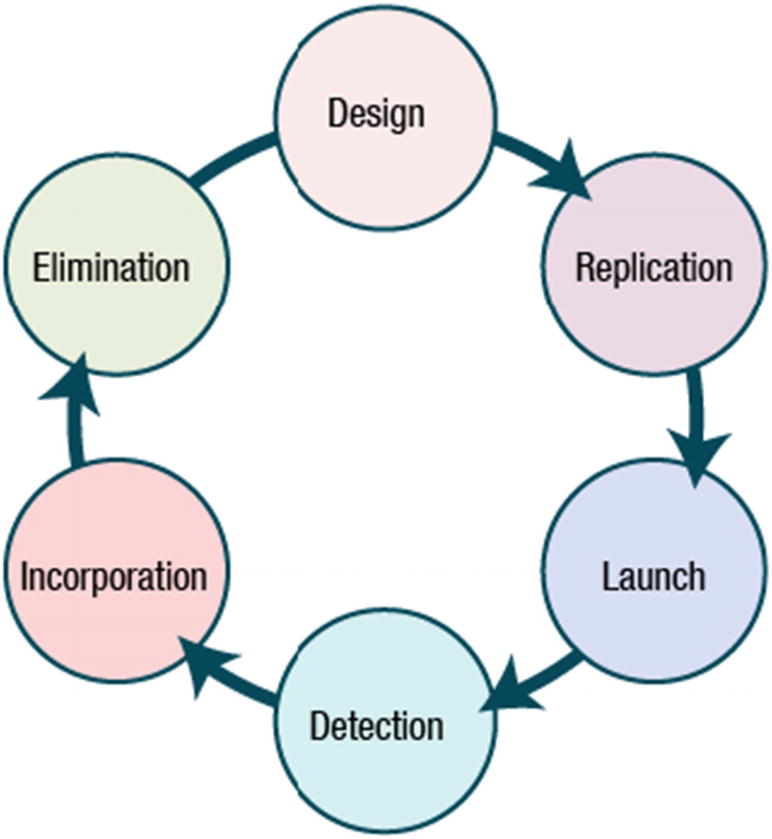
Stages of a virus’ life
Infection Phase
A virus has two phases, really. The first is the infection phase and it is followed by the attack phase. Once a virus is triggered, the sequence of events will continue until the user notices the symptoms and takes the proper steps.

Infection phase
Types of Viruses
Shell virus: In a shell virus, the virus code forms a layer around the target host program’s code, the original code moves to a new location, and the virus assumes its identity.
Add-on virus: An add-on virus appends code to the beginning of the host code so the virus code is executed before host code.
Intrusive virus: An intrusive virus overwrites its code over the host’s program code so the original code does not execute properly.
What Viruses Attack
Another way that viruses can be classified is based on what they infect. A common target is the boot sector, which is an area on the disk that is executed when a computer is started up.
Program viruses infect executable program files or files with .exe, .com, or .sys, for example. Multipartite viruses infect program files which in turn affect the boot sector. Network viruses use the commands and protocols of a computer network to replicate.
Source code viruses are more unusual due to the skill required to write them, and there are many types of source code out there. Macro viruses perform a sequence of actions when an application is run.
How Viruses Infect
Viruses can also be classified according to how they infect the target system. A terminate-and-stay resident virus remains in memory until the system is restarted. A transient virus has a life that depends on its host. When its attached program ends, the virus terminates. A companion virus has the identical file name as the target program file. As soon as the particular program is executed, the virus infects the computer. Polymorphic viruses change their characteristics to evade antivirus programs. Stealth viruses alter and corrupt service call interrupts when they are being run. When a request to perform an operation involves these service calls, the virus interrupts and replaces that call.
Cavity viruses fill the empty spaces of a program and are more difficult virus to write. Tunneling viruses attempt installation beneath the antivirus program by intercepting the interrupt handlers of the operating system and evade detection. Camouflage viruses cover themselves as genuine applications and are easily traced by antivirus programs. There are also bootable CD-ROM viruses that can enter a system by being loaded on a CD-ROM.
Self-Modification Viruses
Antivirus programs scan for patterns or a virus signature, a byte that is part of the virus. If a pattern match is found, the antivirus program flags that file as infected. With self-modification viruses, the code is modified upon each infection. Encryption with a variable key uses encryption keys and each infected file uses a different combination of keys. To manipulate freshly executed files, metamorphic code viruses rewrite themselves whereas polymorphic code viruses infect a file with a copy of a polymorphic code that is encrypted.
The Worst Computer Viruses
- 1.
The ILOVEYOU worm was a VBScript. It spread by using Microsoft e-mail clients. It utilized a file attachment named LOVE-LETTER-FOR-YOU.TXT.vbs that when opened, copied itself to the Windows system directory. The worm modified the registry so that it would run when the system booted.
- 2.
The Melissa virus also spread through accessing the victim’s contacts in Microsoft Outlook. This virus lowered the computer’s security settings. The virus targeted a Word document template. Melissa overwhelmed many servers due to the volume of e-mail that it generated.
- 3.
SQL Slammer exploited the buffer overflow vulnerability in Microsoft SQL Server. Although the worm did not contain a destructive payload, it did produce a massive amount of network traffic.
- 4.
Nimda used five different methods of infection and became the Internet’s most widespread worm, affecting workstations and servers running the Windows operating system. The name “nimda” is actually the reverse spelling of “admin.”
- 5.
Anna Kournikova computer worm used a promise of a picture of the tennis play as an enticement to open the attachment.
File Extensions
Are you familiar with the file types in the list below? .COM .INI .LNK .BIN .ASP .MP3 .CSS .REG .DLL .VBS .BAT .SYS |
Countermeasures
A virus scanner is a must-have. After a new virus is discovered, the signature strings of the virus are identified. Your antivirus software must be updated with the new signatures in order to scan your memory files and system sectors. Although virus scanners can check programs before they are executed and are the easiest way to check new software for known viruses, they are a reactive solution.
Integrity checkers read and record integrated data to develop a signature for those files and system sectors. Some are also capable of analyzing the types of changes that viruses make.
Interception looks at requests to the operating system for actions that cause a threat to a program. If it finds a request, the interceptor pops up and asks for user interaction before continuing.
Handle.exe: Displays information about open handles for any process in the system.
Listdll.exe: Shows the command line parameters and all the associated DLLs that are used.
Fport.exe: Reports all open TCP/IP ports and maps them to an application.
Netstat.exe: Displays network connections and network protocol statistics.
Antivirus Software

Microsoft Security Essentials
Utilizing Malware
Hackers often use malware programs like Dark Comet to maintain a connection to a victim’s machine. The hacker is then able to perform malicious tasks on the victim over that connection.
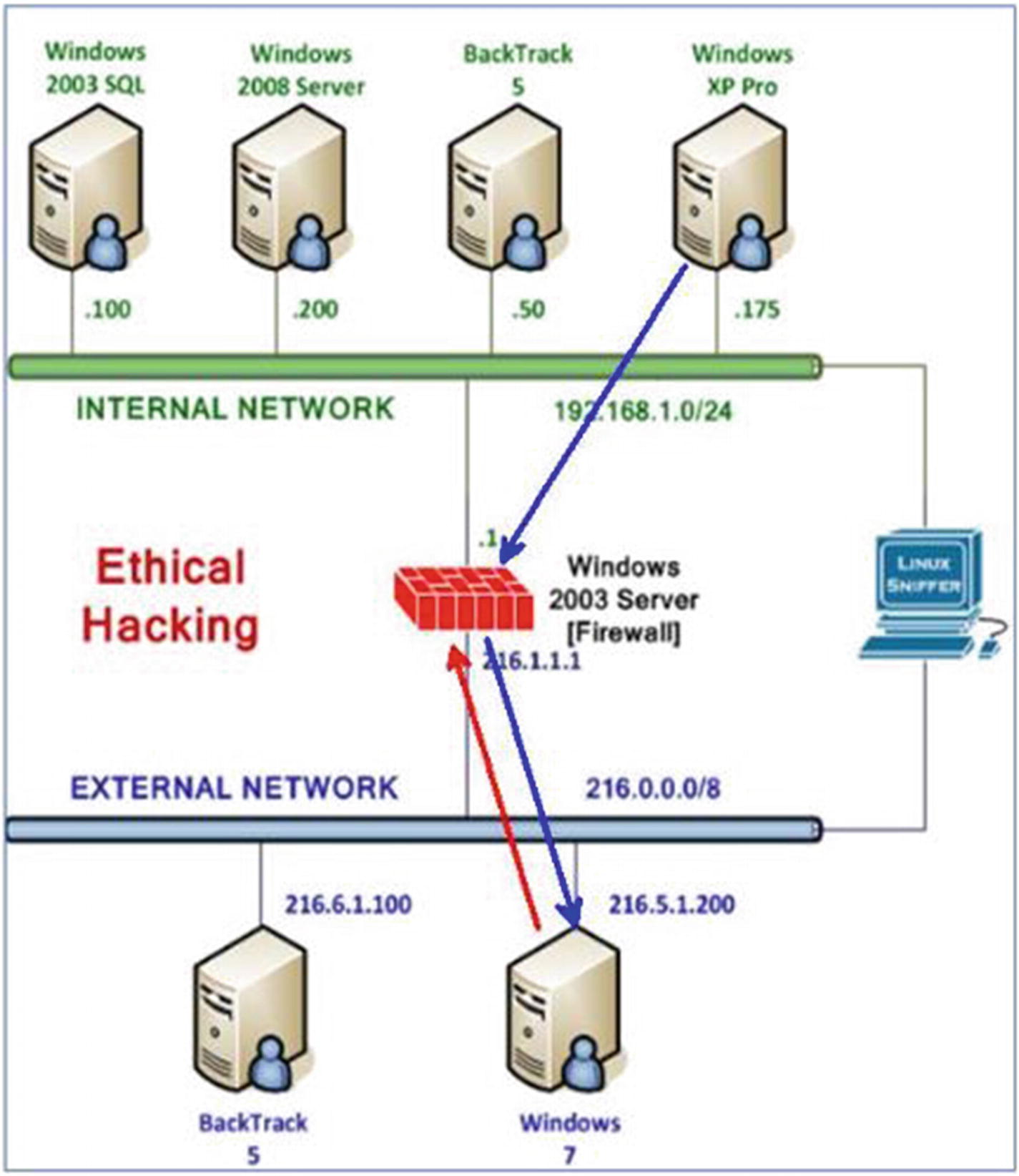
Windows 7 using a public IP address on the WAN
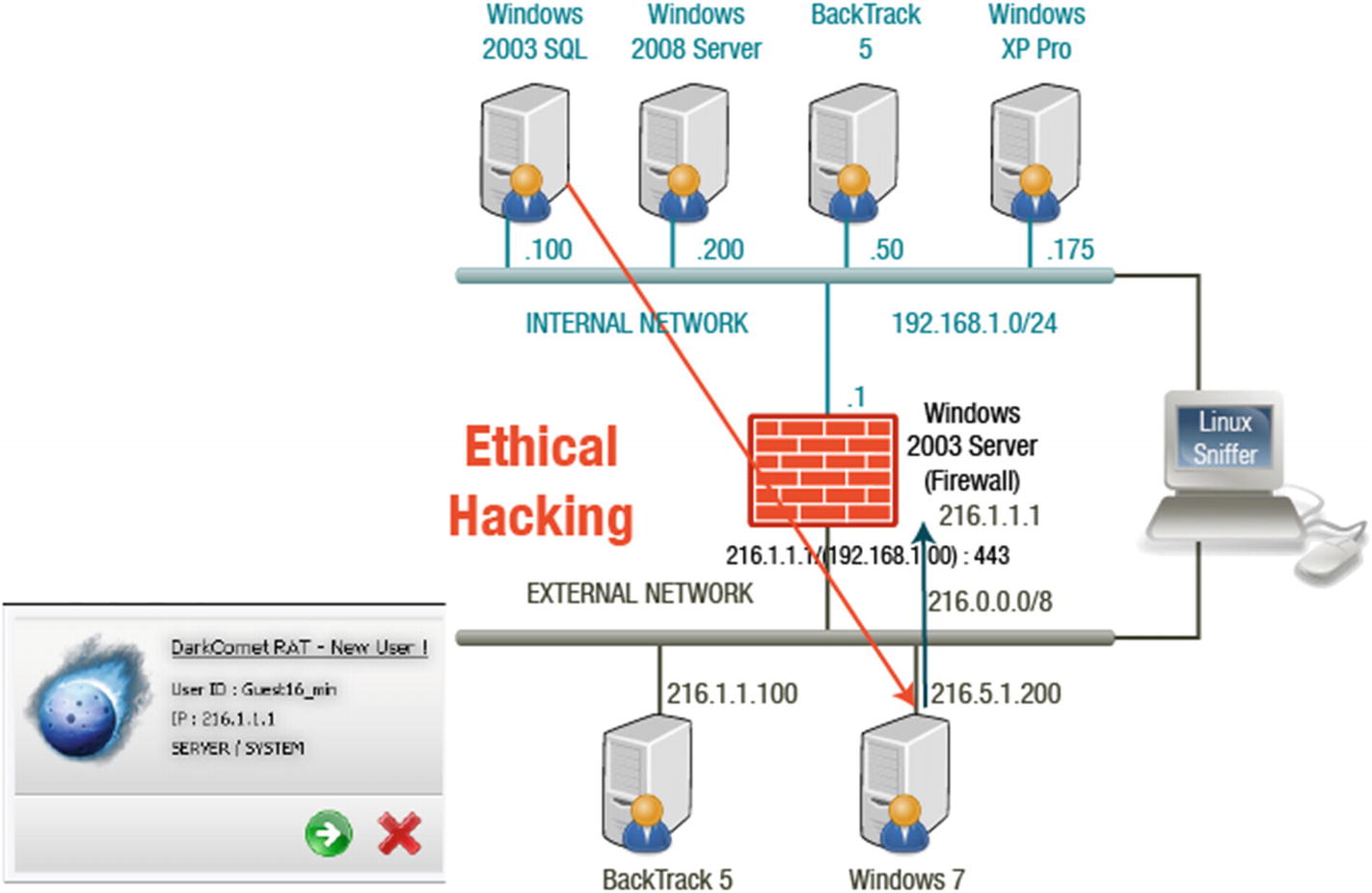
SQL injection and Dark Comet
Exploiting the Connection
Dark Comet connection
Summary
Malicious programs are written to benefit the attacker and are created for a multitude of reasons. These programs contain features of viruses, worms, Trojans, and rootkits. In this chapter, you learned the ways Trojans infect a victim’s system, countermeasures, and the ports used by Trojans. You can now identify symptoms of a virus, virus types, and virus detection methods in countermeasures. Lastly, you understand how a virus works and are familiar with the concepts of backdoors and worms.
