Chapter 10. Tools of the Trade
The happy people are those who are producing something; the bored people are those who are consuming much and producing nothing.
—William Ralph Inge
The HaXor that stole Christmas...what a great way to start this tools-of-the-trade chapter.
Every holiday season all over the world, people experience an OOBE, otherwise known as an “out of box experience.” OOBE is an acronym that refers to the excitement and wonderment that many people enjoy when they open the box their new computer comes in. The smell of the new plastic, the tactile sensation of the new keyboard, the sound that a new PC makes when you boot it up for the first time, all the sights and sounds that come with getting your brand new, shiny SuperComp 2000 Mini-tower PC with 1 full gigabit megabytes of super duper speedy RAM and the 78-gigabyte triple IDE hard drive, otherwise known as an Apple G5—or so I have heard.
As you might imagine, this scene plays out in many households throughout the world every time the Christmas season rolls around. The previous year’s PC is relegated to being the de facto “family” computer—the one that never gets its hard drive defragged or patched and consequently takes three days to boot up.
This year’s PC is going to little Johnnie (or Joanne, to be politically correct) because he is a freshman in high school now and is required to turn in top-notch reports for biology and chemistry and whatever other classes require report writing on a computing platform 150 times more powerful than the computers on the Space Shuttle and NORAD combined.
Besides, little Johnnie/Joanne needs something pretty powerful for playing all those online games that are available via the brand spanking new broadband connection you got last month when you were planning ahead for the big box under the tree! And, of course, the computer will be up in their room to make doing their homework less of a chore and more of an individual accomplishment, achieved in their combination bedroom and office. Perhaps they might even have received a laptop; that broadband modem has wireless, so you can use it when you need to work, too.
Take a moment to get a few things crystal clear. First, teenage children do not need a computer that is capable of breaking RC5 encryption in less than two days; we already have several government agencies that are capable of doing just that, and they really do not like the additional competition. Secondly, the words “You’ve got mail” will not be heard through the speakers of the super computer in question when it gets connected to an unsupervised broadband connection that has download speeds rivaling a T1. You can expect to hear the sounds of heavy metal, rap, and whatever other kinds of music they can download via MP3s.
Regardless of whatever story your little high-school sophomore tells you, if they are in any kind of computer science course at school (as more than 80 percent of them are), they are striving for one goal: to be crowned “Uber Haxor” (pronounced oober hacksor) by their little felonious classmates. That’s right, your little baby that used to eat peas and carrots with their toes is but a few mouse-clicks away from being brought up on charges under the U.S.A. Patriot Act, and the shiny new PC you bought for Christmas is the high-tech hotrod that might end up getting them an extended stay at the “grey bar” motel. How many of the attacks, techniques, and tools discussed in this book cost money? Not many, and those that do have cracks available in the Internet.
The combination of intelligence and a burgeoning contempt for authority in any form (teenager) can make a state-of-the-art computing device a dangerous thing if it ends up in the wrong hands. Now, you might be saying to yourself, “my child would never do anything like that. I’ve brought him up to respect authority and have taught them the difference between right and wrong.” All this might be 100 percent correct, but in educating the little tyke, you might have forgotten that the Internet is still as wild and wooly as the west was in the 1800s.
Surfing the Internet is a common occurrence for children who have grown up in the last 10 years, and the morality of the Internet is still in its infancy. At last count (and some people have actually counted), thousands of websites are dedicated to hacking, cracking, and computer crime. Finding information on how to write viruses is easier and more fun than locating a recipe for double fudge brownies.
Broadband Internet access has created a culture of anonymity that has never existed before for children seeking ways to rebel and embarrass their parents for grounding them or taking away the car keys. E-mail, websites, and chat rooms have empowered children to explore the boundaries of society in an instant and exploit the weakness of that very society on a whim when they determine that society has treated them badly.
Even at this point, you might still be convinced of your child’s enduring innocence and good intentions when it comes to behaving responsibly with regard to Internet usage. You might be correct in maintaining your belief; but then again, if you had asked the attacker’s mother who was recently in the news if her son was capable of these kinds of acts, she probably would have denied that her son was capable of executing the attacks, and we know how that story turned out.
This chapter discusses the security tools that attackers use so readers can understand what they are up against. The chapter then examines the tools available to identify weaknesses in your network and the anatomy of a security audit, which is a crucial piece to ensure that your network is secure.
Essentials First: Vulnerability Analysis
This section looks at some of the tools that are freely available to attackers. The fundamental truth this section teaches is that the bad guys have good tools. Previous chapters touched on many of the specific attack tools; however, attackers have a broad toolset with which they can launch multilevel attacks against your network. When an attacker gains a foothold in one aspect of your network, it is then leveraged to exploit another aspect of your network.
Attackers, for example, can, do, and will take advantage of weak authentication and authorization, improper allocations, poor security implementation, shared privileges among users/applications, or even poor employee security habits to gain unauthorized access to critical network resources.
Throughout this book, you have seen that there are many ways to allow even the best security procedures and technologies to be circumvented. To understand how this is done, you must spend some time understanding the exact methods and tools the attackers use. Perhaps it is exciting to see an attacker’s tools; however, if any network resource is your responsibility, you better ensure that you are using these tools to assess your network’s security. It is extremely important that you use these tools on behalf of your network so that vulnerabilities can be detected and found before an attacker uses them against you. You can count on these tools being used in your network—the decision you have to make is who is going to use them first?
Fundamental Attacks
Leading edge security technologies, policies, and procedures can quickly have their effectiveness nullified if those who are responsible for network security do not understand the methodology and tools that will be used against your network. This chapter discusses some of the methodologies and various tools that attackers use, how they operate, and the tools and techniques you can use protect your network resources against these hacker tools.
Even the best security technologies and procedures can be rapidly nullified unless you know the precise methods and tools being employed against you. Therefore, it is crucial to be able to identify the various tools of the hacker trade, how they operate, and what kinds of protections thwart these attacks. This includes a thorough knowledge of the common tools and techniques discussed in the sections that follow.
IP Spoofing/Session Hijacking
This type of attack occurs when an attacker creates a packet with a different IP address to gain entry to a system. This attack exploits trust relationships by allowing the attacker to assume a trusted host’s identity. For this attack to be successful, the attacker must determine the “patterns of trust” for the target host—that is, for example, the range of IP addresses that the host trusts. After the attacker determines the pattern of trust, he can move onto the next step of the attack by either compromising the host or disabling it in some manner. These types of attacks are often used as the first step in the overall attack strategy.
Note
![]()
Because the attacker has spoofed an IP address (that is, made it up so the target trusts it—the address could be a local LAN address, whereas the attacker is not local) the attacker might not see the response from the target. This means that the attacker is blind to their success, and is why this is usually a first step. It is common to blindly exploit a vulnerability in this matter and, after the host is compromised, move to the next step.
IP Spoofing/Session Hijacking Tools
A variety of tools accomplish exploitation through IP spoofing/session hijacking:
• Dsniff—A collection of tools for network auditing and penetration testing specifically known as Dsniff, filesnarf, mailsnarf, msgsnarf, urlsnarf, and webspy passively monitor a network for interesting data (passwords, e-mail, files, and so on). arp spoof, dns spoof, and macof facilitate the interception of network traffic.
• Hunt—A program for intruding into a connection, watching it, and resetting it. Hunt was an outgrowth of similar products like Juggernaut, but it has several features that cannot be found in these products.
• Ettercap—A powerful Apple OS X- and UNIX-based program employing a text-mode GUI, easy enough to be used by “script kiddies.” All operations are automated, and the target computers are chosen from a scrollable list of hosts detected on the LAN. Ettercap can perform four methods of sniffing: IP, MAC, ARP, and public ARP. It also automates a variety of other tools.
Prevention
Of course, preventing these kinds of attacks is as important as understanding them and the tools that are used. Virtual private networks (VPNs) are effective against IP spoofing because a VPN encrypts the original IP addresses as they are transmitted across the network. If either the data or the source address prove to be tampered with, the packet is deleted. This prevents an attacker from penetrating a system without access to the VPN encryption keys.
Packet Sniffers
These tools gather packets being transmitted past the point where the sniffer is connected to on a network. Sniffers generally come either software-based (for PCs/PDAs) or hardware-based (on a dedicated computer). Using sophisticated network sniffers that can decode data from packets across all layers of the OSI model, attackers can steal usernames and passwords and use that information to launch further attacks. In general, attackers can use sniffers by compromising the corporation’s physical security—say, walking into the office and plugging a laptop into the network. With the growing use of wireless networks, someone in the parking lot with a wireless device can access the network. By using sniffers, attackers can obtain valuable information about usernames and passwords across public or private networks—in particular, from applications such as FTP, Telnet, and others that send passwords in the clear. Protocols such as SMTP, IMAP, and POP3 are used for remote access to e-mail applications via simple username and password authentication techniques and are especially susceptible to sniffer attacks. Because users tend to reuse passwords across multiple applications and platforms, attackers can potentially use the acquired information to obtain access to other resources on the network, where their confidentiality could be compromised.
Denial of Service (DoS) Attacks
Also known as Distributed Denial of Service (DDoS), Packetstorming, Tribal Flooding, and the other DDoS attack methods used to overload networks by making so many requests that regular traffic is slowed or completely interrupted have existed for some time—not only in theory, but also in practice. A “regular” denial of service (DoS) attack does not involve breaking into the target; rather, the attacker’s goal is to simply overload the target (router or web server) with so much fake traffic that it cannot cope.
When the target is unable to cope, genuine users are unable to connect and are therefore “denied service.” A distributed denial of service (DDoS) attack generates the false traffic from multiple hosts across the Internet. A DDoS attack uses multiple computers throughout the network that it has previously infected with a DDoS Daemon (program); these computers are then known as zombie computers.
Note
![]()
A DDoS daemon is a specialized computer program that was designed for use in controlling and coordinating a DDoS attack. As of this writing, there are four known programs: Tribal Village (TFN), TFN2K, Trinoo, and Stacheldraht, which is German for “Barbwire.” You can learn more about these programs by visiting the following URLs:
http://staff.washington.edu/dittrich/misc/trinoo.analysis
http://staff.washington.edu/dittrich/misc/tfn.analysis
http://staff.washington.edu/dittrich/misc/stacheldraht.analysis
These zombie computers all work together as a zombie network to send out bogus connection messages, thereby increasing the amount of open connections with which the target must deal. This prevents legitimate users from accessing the services being offered. DoS attacks are easy to implement and can cause significant damage, thereby disrupting a server or network’s operation and effectively disconnecting them from the Internet. A DoS attack can be conducted using various bogus connection techniques. For example, a SYN flooding attack uses fictitious, half-open TCP connection requests that exhaust the resources of the targeted system. DoS attacks exploit weaknesses in the architecture of the system that is under attack; as we just saw, capacity limitations are one example. In some cases, DoS attacks exploit the weaknesses of many common Internet protocols, such as the Internet Control Message Protocol (ICMP). For example, some DoS attacks send large number of ICMP echo (ping) packets to a broadcast address. These packets being sent use a spoofed source IP address of the potential target. The replies coming back to the target can cripple it. These types of attacks are called smurf attacks.
A smurf attack is a type of DoS attack that exploits the use of the Internet Control Message Protocol (ICMP, a.k.a. PING) and the IP’s network and broadcast addresses. A smurf attack’s purpose is to disable a target host or network by consuming all of its resources; aside from this, it causes no permanent damage. Every IP subnet has two special addresses:
• The network address, which is the first address in the subnet
• The network broadcast address, which is the last address in the subnet range
The IP network address serves as the identity address of a given subnet in the IP routing table. The IP broadcast address was devised as a method for sending information to all the hosts in a given subnet. Most IP implementations respond to messages with the network or broadcast address as the source address. This support is known as “directed broadcast.” This feature is also data used for legitimate purposes.
ICMP/Ping Attack
A ping-based attack uses the characteristics of ICMP to the attacker’s benefit. The compromised hosts are directed to attack the designated target via a continuous stream of ping packets. This causes an incredible number of ping requests coming from thousands of compromised hosts to begin impacting the host. This is certainly an unwelcome scenario, but the attacker has also altered the ICMP Packet [ICMP echo request]. Each packet does not contain the compromised host’s source address; instead, each packet’s source address is the target’s address (that is, the source and destination address are the targets). The target system then transmits a response [ICMP echo reply] to each packet, which is destined to itself, thus causing traffic to increase exponentially until the target crashes because of its inability to handle such a high volume of traffic. To take this further, imagine if a broadcast was allowed onto a LAN with the target’s source address. The real caveat implicit in this attack is that the traffic appears completely normal and is typically allowed into any network and through firewalls, and so on. You can see this attack in action with a properly positioned sniffer or probe.
SYN Flood Attack
In TCP/IP, a three-way handshake occurs whenever a client attempts to connect to a service, such as FTP or HTTP. The three-way handshake is defined as follows:
- The client sends a packet with the SYN (synchronization) flag in the TCP header set to the service.
- The service responds with a SYN-ACK (synchronization-acknowledgment).
- The client sends a handshake to the service(a SYN-ACK transaction) and the session is considered established so data begins to flow.
Note
![]()
Richard Stevens (TCP/IP Illustrated, p. 231) explains the format of the SYN packets and is an excellent resource for those wishing to understand the details of TCP/IP.
A SYN flood attack is when the client does not respond to the service’s SYNACK, thereby tying up the service until it times out. In this type of attack, the client never responds because the client’s source address is forged (spoofed). The attacker’s goal is to send SYN packets to the service faster than it takes for the service to timeout waiting for the client’s SYN-ACK response. This causes the service to become so busy acknowledging the SYNs and waiting for the client that it cannot answer requests for service from legitimate users and therefore denies them service.
Preventing DoS Attacks
You might be wondering how can you defend against denial of service (DoS) attacks. This is perhaps one of the most difficult attacks to defend against because many of the attacks come in the form of traffic that would be considered a normal occurrence on your network. Perhaps one of the most common defenses is to rate limit certain types of traffic. For example, you might want to allow ping (IMCP); however, too much of it could be considered a DoS attack, so you would rate limit ICMP. In contrast, you must carefully watch other types of traffic. Perhaps limiting HTTP (web) traffic to your Internet e-commerce site would be a mistake! Again, the depends rule strikes fear into your IT staff when considering how to defend against a DoS attack.
Man-in-the-Middle Attacks
In this form of assault, the attacker places himself in the middle of a communication flow between two hosts: usually, a server and a client. The attacker then intercepts messages transmitted between the two hosts. The attacker can look for a variety of things. Perhaps he wants to see how much money is in your bank account, your password to the fantasy football website, or even block the connection. The interesting part and point of concern here is that if the attacker does not alter anything, you will not know that the packets are being intercepted by an attacker in the middle!
Network sniffers, or Ettercap (http://ettercap.sourceforge.net/), are often used to accomplish this type of attack. You will also find that man-in-the-middle attacks can be used to reconstruct public cryptic keys. This discussion is beyond the scope of this text; however, protecting passwords and keys is always a good idea in case you need another reason for a password policy.
ARP Spoofing
ARP spoofing is one way in which a man-in-the-middle attack can be successful if executed on either a wired or wireless LAN. The process of updating a target computer’s ARP cache with forged entry is referred to as “ARP poisoning.” This technique involves the attacker constructing forged a ARP request and reply packets to change the Layer 2 Ethernet MAC address to one of their choosing. By the attacker sending forged ARP replies, a target computer could be convinced to send frames destined for Host B to instead go to the attacker’s computer first so they can be recorded and read. When done properly, Host A has no idea that this ARP redirection took place, as shown in Figure 10-1.
Figure 10-1. Man in the Middle: ARP Spoofing
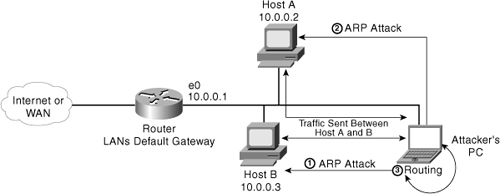
Role of IP Spoofing in Man in The Middle Attacks
IP spoofing plays an important role in man-in-the-middle attacks. In IP spoofing, an attacker compromises or disabled a trusted host. The attacker then sends IP packets with the source address of the disabled trusted host to the target, effectively masquerading as the trusted host to gain access to or disable the target host.
Back Doors
A back door, or trapdoor, is a secret way of gaining access to a program, operating system, BIOS, or network service. You often see these types of back doors in computer games where a certain phrase or key combination provides you unlimited money, power, health, and so on. Back-door entry to resources can be accidentally or intentionally opened by users or by design; consider the following examples:
• Deliberately placed by system developers to allow quick access during development and not turned off before release.
• Placed by employees to facilitate performance of their duties because the ‘proper procedure’ made them think that it made their jobs harder, so there must be a smarter and easier way. Users might not be as technical as your IT staff, and often they find back doors because they do not have a preconceived notion of how something should work.
• Normal part of standard ‘default’ operating system installs that have not been eliminated by “OS hardening,” such as retaining default user logon ID and password combinations. Again, vendors do not want technical support calls, so they make it as easy and open as possible. This means that your IT staff must review and harden every server!
• Placed by disgruntled employees to allow access after termination. In many cases, an employee suspects that the loss of his job is coming. This makes him angry and feel unappreciated, so he wants to ensure that he can strike back as necessary when the time comes.
• Created by the execution of malicious code, such as viruses or a Trojan horse that takes advantage of a vulnerability in an operating system or application.
As discussed previously, these attacks and tools are the most common types of vulnerabilities used by attackers. Understanding them will better allow you to understand the tools and techniques discussed in the following section.
Miscellaneous Attacks
This section provides an overview of some of the more unusual and unique attacks.
Land Attacks
A land attack is an IP spoof-based attack where the source and destination address are the same. This attack crashes some TCP/IP implementations that do not know how to handle the packet. This is a rarity in terms of appearance in the real world, but is a standard signature on ISS, NFR, Dragon, and Cisco Net Ranger and IDS-IOS.
Xmas Tree Attack
In an Xmas tree attack, a TCP packet sent to any known service port sets all the code flags (URG, ACK, PSH, RST, SYN, and FIN). An alternative version of this attack is a TCP packet without any flags set. Both cases are the result of packet craft and do not exist in the “wild.”
Teardrop Attack
The teardrop attack uses fragmented UDP packets. The first fragment is fine, but the second packet overwrites part of the first fragmented packet. This results in a memory error, and the system crashes.
Ping Pong Attack
There are two variations on the ping pong attack:
• A flood of spoofed packets to the echo service (UDP/TCP port 7), which is a simple service that echoes back any data sent to it.
• Sending a spoofed UDP message that appears to be from the chargen service port to the echo (UDP port7) service on another system. The chargen service responds to any packet sent to the service port with a 72-byte random character string. After the spoofed connection is established, the echo port sends traffic to the chargen port and a loop develops.
Both variations consume CPU resources; enough attacks cause the system to becomes CPU-bound and crash.
Ping of Death
Like teardrop, this attack exploits IP’s fragmentation capability. The attack host sends an ICMP with a packet size that exceeds the maximum IP datagram size of 65,535 bytes. The attacked system waits until all the fragments are delivered, and then reassembles the packet; this results in a buffer overflow that crashes the system.
SYN Flood (Half-Open Attack)
Each TCP open (SYN) request requires a server to reserve resources to support the connection. The attack works by flooding a service with SYN requests from spoofed IP addresses (routable or unroutable addresses work). The server then acknowledges the SYN requests and responds with SYN-ACKs. These are never responded to because sources of the SYN requests never made the request. Depending on the system, the connection timer can allow between one to three minutes before reclaiming the allocated resources. The actual expected response to SYN-ACK is a few milliseconds. With a steady stream of SYN requests, the server’s connection queue can be filled with incomplete connections that block out legitimate user requests.
Firewalking
Many people consider firewalls immune to attacks or standard techniques that allow attackers to figure out their rule sets in order to bypass them. That belief was true for a while; however, new techniques are always being developed and, in this context, firewalking is a concept that allows the attacker to send specially crafted packets through a firewall to determine what ports and services are permitted through the firewall. An attacker with this knowledge can make their port scans hidden and thus map your network through your firewall.
Firewalking works because IP packets contain a field that prevents them from being sent around a network forever. This field is known as the Time-To-Live (TTL). When this field reaches zero, the packet is discarded. In firewalking, this field is set to a value that will allow the packet to get beyond the firewall and then be dropped by a host or device after the firewall. What allows this to happen is that the TTL value is one of the first things checked and, if its value is zero, a device sends back a packet acknowledging that it is being dropped without the original packet ever really being processed.
The following section discusses security assessments and penetration tests and the value they bring to securing your network.
Security Assessments and Penetration Testing
Companies with security offerings these days often have a security assessment as their first step in assisting a client in securing their network. A security assessment is an excellent first step for an organization that is concerned with understanding the extent of the security on their network (and its effectiveness). A strongly recommended practice is that individuals outside of your organization perform security assessments on a yearly basis. This provides an objective and honest evaluation of your security, and because vulnerabilities are always being discovered, your network would be evaluated often enough to understand its effectiveness. A variety of available types of security assessments exist:
• Internal vulnerability and penetration assessment
• External vulnerability and penetration assessment
• Physical security assessment
Before arranging a security assessment of any sort, you should learn more about the processes and procedures that the vendor is going to use. Because too many security service companies exist out there to risk your company’s security without some due diligence, you should review the following paragraph:
Understand the plan for the security assessment. If not planned and understood, assessing the actual network vulnerabilities can cause havoc in your network. There must be a legal agreement on the scope of the testing and the extent to which it will go; this protects both parties. Finally, it is important to define the success criteria of an assessment so that both parties understand what is to be accomplished.
The following sections examine the recommended approach that you should take and the benefits to the security of your network for each type of assessment.
Internal Vulnerability and Penetration Assessment
According to a recent study by the FBI, internal users and processes account for over 60 percent of network security threats in today’s enterprises. These threats are a result of improper configuration of network devices, lack of effective security procedures, and outdated and unpatched software. Security consultants should be able to identify these threats to determine your network’s level of risk to intentional or accidental threats.
Today’s organizations find it difficult to stay up-to-date on the numerous new vulnerabilities found each day in operating systems and applications. Security consultants should be aware of the latest vulnerabilities and help you assess the state of your internal network security mechanisms. They should also be able to recommend corrective steps for moving forward with your organization’s security goals.
Assessment Methodology
Internal network security assessments must be performed onsite at your location and focus on internal security risks associated with policies, procedures, and networked hosts and applications. At a minimum, a security consultant should perform the following work:
• Gather customer-provided network information, if applicable.
• Gather and document publicly available network information for your review so you can understand what an attacker would know.
• Perform network mapping techniques to determine the topology and physical design of your network.
• Network application probing and scanning.
• OS fingerprinting and vulnerability detection to expose vulnerable hosts.
• Identification of traffic patterns and flows to compare with expected normal business expectations.
• Detect any potentially weak user authentication systems such as users who never change passwords, or insecure wireless networks.
• Vulnerability analysis using public, private, and custom tools.
• Manually verify all detected vulnerabilities to ensure that false positives are not reported.
• Observe internal security practices and policies throughout your network.
• Analyze findings and report analysis along with specific recommendations for moving forward.
The end result of an internal risk assessment should be a document that contains the assessment methodology, the work performed, and details gathered on every system, including the high-risk systems found vulnerable to attack, and detailed lists of vulnerabilities. The assessment results document provides a clearer picture of your network architecture and security risks. The document should also contain the results of all work performed and conclusions from each test phase regarding the remediation required and the relative priority of these recommendations. Of course, this document must also include recommendations for mitigating detected network security risks in a cost-effective manner.
External Penetration and Vulnerability Assessment
As traditional business systems become more distributed among an organization’s geographically disperse locations, the risk of external attacks increases. These risks are further exaggerated by improper router and firewall configuration and insecure, outdated, or improperly configured web-based applications.
Today’s small and medium-sized businesses find it difficult to stay up-to-date on the numerous new vulnerabilities found each day in operating systems and applications. Granite Systems (www.granitesystems.com) world-class network design consultants are aware of the latest vulnerabilities. They can help you assess the state of your current perimeter defense mechanisms and recommend steps for moving forward with your organization’s security awareness.
Assessment Methodology
External Penetration and Vulnerability Assessments are performed against your network at places where it interacts with the outside world. This could be through connections to the Internet, wireless, phone systems, and other remote access locations. The intent of this type of security assessment is to determine where and how your network is vulnerable to external attacks.
In many cases, an External Assessment and an Internal Security Assessment look at the same types of things. The difference is the point of view and, in this case, it is from the outside trying to look in to see what can be discovered. The following list examines the work that should be done for an External Penetration and Vulnerability Assessment:
• Gather customer-provided network information, if applicable.
• Gather and document publicly available network information for your review so you can understand what an attacker would know.
• Perform stealthy network mapping techniques to determine your network’s topology and physical design and to see if these simulated attacks can be detected.
• Network application probing and scanning.
• Firewalking, war dialing, and war driving, as needed.
• OS fingerprinting and vulnerability detection to expose vulnerable hosts.
• Identification of traffic patterns and flows to compare with expected normal business expectations.
• Detect any potentially weak user authentication systems such as users who never change passwords or unsecure wireless networks.
• Vulnerability analysis using public, private, and custom tools.
• Manually verify all detected vulnerabilities to ensure that false positives are not reported.
• Analyze findings and report analysis along with specific recommendations for moving forward.
The end result of an external penetration and vulnerability assessment is a document that contains the same level and type of information as an internal assessment, except from an external point of view. Although this chapter examines internal and external assessments separately, these assessments are best performed together in the real world. They will then allow a clearer picture of your network’s security, end-to-end.
Physical Security Assessment
This book focuses on the logical security of networks, which is only part of the coverage that this type of assessment provides. Many assets are physical in nature and can be harmed through cruder and perhaps simpler methods than we have discussed. For example, are your IT resources kept in a room with overhead water-based sprinklers? If so, that is not physically secure because microchips and water do not mix. A simple denial of service would be to trigger the fire alarm in your building and let the water do the rest. I hope your tape backups are protected from water damage and that they are current....
Although this is a digital age, today’s IT systems still depend on physical hardware and reside in physical locations. Without the use of proper physical security mechanisms, all other security measures in place can be defeated. As the sensitivity of an organization’s information increases, physical security takes a more important role. What good is it to have the latest firewall, IDS, and VPNs if you leave the door open to your equipment?
Physical security controls can be either deterrent or detective in nature and are designed to limit your organization’s exposure to physical threats. A physical security risk assessment can help your organization design and implement cost-effective physical security measures to deter would-be attackers, monitor suspicious activities, and ultimately protect your valuable corporate resources from tampering, compromise, or destruction.
Assessment Methodology
A Physical Security Assessment must be performed onsite at your location and focus on physical security measures and internal practices of a physical nature that are in place to protect your network resources. A Physical Security Assessment should entail the following:
• Observe external building access points and safeguards in place.
• Observe physical safeguards in place, such as closed-circuit cameras, badge access, and visitor sign-in practices.
• Review physical protection mechanisms for IT resources, but also paper records.
• Determine physical safeguards in place for securing IT equipment, such as restricted access to computing environment, floppy-drive locks, redundant power sources, and protected data communication channels.
• Observe employee habits as it relates to physical security.
• Observe the physical disposal methods of critical data; do you recall dumpster diving?
• Make recommendations for securing your IT resources from physical security breaches.
• Understand the backup procedures and storage of critical data.
• Examine vendor and visitor access policies (if they exist) to determine how unknown individuals are handled.
The end result of a physical risk assessment is a document that contains the methodology followed, the work performed, the results of the work performed, and recommendations for mitigating detecting physical security risks in a cost-effective manner.
Many of these assessments cannot be automated to any great degree, so you must open your network and its resources to a trusted outside organization. When selecting this organization, you should request the following:
• Review of industry standard certifications to ensure that there is at least a measurable level of competence associated with those who are assessing your network.
• Contact several references of the company you are thinking about using and make sure that the references are relevant to the services you need performed.
• Ask for and review sample assessments. This can be difficult to do because assessments usually contain sensitive customer data, but any company that is committed to providing security services should have the ability to show you a sanitized version.
• Set expectations and deliverables clearly in the agreement to proceed/contract and so forth, thereby protecting yourself and the vendor’s employees. Clear communication can solve 99 percent of the world’s problems.
• Ask the security company to walk you through the assessment process before they come out to your location. If they cannot recite the process from memory, chances are they have either not been in business very long, or the person you are speaking with is not a field technician.
Miscellaneous Assessments
Other types of assessments that are related to security in some ways should be mentioned for possible consideration:
• Procedural risk assessment—This assessment allows security professionals to review your security policies and procedures to ensure that they conform to best practices. Chapter 2, “Security Policies and Responses,” discussed policies and procedures of this nature.
• Disaster recovery—Where your organization is based in an area of the world that is susceptible to tornados, hurricanes, earthquakes, lightning strikes, floods, fire, or some combination of these, the need for a plan of recovering your network infrastructure and critical data becomes more important with every passing day. The influence and persuasiveness of IT is ever-increasing.
• Information handling security assessment for banks and medical offices—With new legislation regarding the security of financial and medical records (HIPPA for medical and Gramm-Leach-Bliley Act for financial) coming out each year, professions tasked with maintaining these types of records are being held to increasingly higher data security standards, or face jail time.
Assessment Providers
A simple Google search on security assessments reveals over 400,000 hits, and this number will continue to grow. Some companies, such as the following, are worth mentioning as excellent providers of assessments services:
• Cisco Secure Consulting Services—Provides enterprise customers with comprehensive security analysis of large-scale, distributed client networks externally from the perspective of an outside hacker and internally from the perspective of a disgruntled employee or contractor according to their web-site. You can learn more at http://www.cisco.com/go/securityconsulting.
• INRGI—Provides customized security solutions and assessments for customers of all sizes with a specialization in ensuring that business focus drives the security solution versus the more common occurrence of IT driving business. You can learn more at http://www.inrgi.netindex_security.html.
• Aegis Security—Provides contract security work and web design: http://www.aegis-security.com/.
• Granite Systems—Provides assessments of all types to understand, design, and recommend the proper solution. Granite Systems hold the distinction of the three in that they offer Managed Security and Network Services to further support any organization’s needs. You can learn more at http://www.granitesystems.net.
The following section begins looking at the assessment and vulnerability tools that are available to automate the search for security risks.
Vulnerability Scanners
When hackers want to breach your systems, they typically look for well-known security flaws and bugs to attack and exploit, some of the most common of which have been discussed in earlier chapters of this book. A true attack, which has the end goal of penetrating and controlling the target system, relies on the attacker gathering the most accurate and comprehensive view of an organization’s security. As the attacker evaluates the network, he exploits vulnerabilities to determine precisely how to get control of valuable information assets.
Attacking vulnerabilities used to be a time-intensive procedure that required a lot of knowledge on the part of the attacker. Today, however, automated tools have changed all of that. Almost gone are the days of having to figure out the publicly available exploit codes and maintaining them all in order to be effective.
You might be wondering if I am talking about the role of attackers and commiserating with them about how hard it is to control the data. Or perhaps I am talking about how network administrators are faced with such a daunting task. In fact, I am talking about both, and the point is that this is no longer the biggest concern. Today, attacks have been scripted and published, and companies have formed to automate the detection of attacks and exploit vulnerabilities. This section looks at the most comprehensive of these tools that, included with the individual tools covered elsewhere in this book, should provide you with excellent resources to detect vulnerabilities and begin correcting them.
Features and Benefits of Vulnerability Scanners
Applications that perform security scan and vulnerability assessments do the scanning and calculations in the background. Frankly, the focus here is not in how vulnerabilities are detected, but on what is vulnerable. The value of these scanning tools can be summarized in the following four categories:
• Scan and detection accuracy—Scans and reported vulnerabilities must be accurate with minimal false positives—defined as normal activity or configuration that the system mistakenly reports as malicious. The opposite also holds true then; there can be no false negatives—defined as malicious activity that is not detected.
• Documentation and support—Must be clear, concise, well written, and easy to understand (like this book). This includes reporting documentation and application operation so users can figure out how to make the application work and see the documented findings in the report.
• Reporting—The most important aspect of a vulnerability scanner is when you need to know the next steps after a vulnerability has been detected (that is, what was detected and how to fix it); thus, a report must be customizable, useful and accurate.
• Vulnerability updates—New vulnerabilities are constantly being released and, with today’s technology, every system should have a way to update itself automatically.
The following section looks at three of the most popular vulnerability scanners that are currently on the market.
Nessus
Nessus is to vulnerability detection what Snort is to IDS: an open source solution supported by a community of Internet volunteers. You can learn more about Nessus at http://www.nessus.com.
In Their Own Words
The following section is a direct quote from the Nessus web page on how it describes its product:
The “Nessus” Project aims to provide to the Internet community a free, powerful, up-to-date and easy to use remote security scanner.
A security scanner is software, which will audit remotely a given network and determine whether bad guys (a.k.a. ‘crackers’) may break into it, or misuse it in some way.
Unlike many other security scanners, Nessus does not take anything for granted. That is, it will not consider that a given service is running on a fixed port - that is, if you run your web server on port 1234, Nessus will detect it and test its security. It will not make its security tests regarding the version number of the remote services, but will really attempt to exploit the vulnerability.
Nessus is very fast, reliable and has a modular architecture that allows you to fit it to your needs.
Scan and Detection Accuracy
Scans and reported vulnerabilities must be accurate, with minimal false positives—defined as normal activity or configuration that the system mistakenly reports as malicious. The opposite also then holds true; there can be no false negatives—defined as malicious activity that is not detected.
Nessus has good capabilities to detect vulnerabilities and is accurate in the vulnerabilities it detects and finds. Being an open source project, Nessus is constantly being watched, tested, studied, and improved upon. With so much visibility, this product has become configurable for those with the knowledge to understand its underpinnings. Figure 10-2 shows the Nessus setup screen and its flexibility, strength, and many possible options.
Figure 10-2. Nessus Vulnerability Scanner Setup Screen
Documentation and Support
Documentation must be clear, concise, well written, and easy to understand. This includes reporting documentation and application operation so users can figure out how to make the application work and see the documented findings in the report.
Nessus documentation is excellent, average, and very poor. If you are trying to install Nessus on an Apple laptop or for the first time, some excellent resources can help you get Nessus running with minimal stress.
When you are trying to determine how Nessus functions or what it can do as part of its standard documentation, you are going to have to deal with the fact that what little is written has been done by programmers. Ever try and read a Linux MAN page? If you have, you know what I mean—it is not for beginners.
From a technical support perspective, because Nessus is not a company, there is no formal technical support number, and the website is basic. However, a mailing list has many of the core Nessus programmers, and they can be helpful.
Reporting
The most important aspect of a vulnerability scanner is when you need to know the next steps after a vulnerability has been detected (that is, what was detected and how to fix it); thus a report must be customizable, useful, and accurate.
Nessus creates reports in a variety of formats, the most useful being HTML. These reports are fully hyperlinked with complete analysis of the vulnerabilities detected, their level of risk to your network, and with great, pretty pictures that can visualize the vulnerabilities. On a downside, the reports are UNIX-centric and full of contextual and grammatical errors, not something that you can share without serious editing. The information is accurate, just not as polished as a commercial product.
Vulnerability Updates
New vulnerabilities are constantly being released and, with today’s technology, every system should have a way to update itself automatically.
Nessus is kept up-to-date via scripting that can be automated to ensure that it has the latest signatures. Although Nessus does not run on Windows, it does have a Windows client that allows connections to Nessus servers so scans can be run remotely.
Nessus is a good vulnerability scanner that has exceptional functionality as a result of its open source status. There are some excellent resources available for Nessus. Other related links can be found at the following URLs:
http://www.securityprojects.org/nessuswx/
Nessus is freely available for download and requires no purchase because it is open source software. This means that it is an excellent solution for network administrators that will not cost their organization any money. However, this also means that the old computer sitting in the corner of your neighborhood attacker can be loaded with Linux (free) and Nessus (also free). Then, the vulnerability scanning, which is also free, will commence against your network.
Retina
Retina is eEye’s premiere security scanner that leads their suite of security products. eEye offers several products that focus on securing the Microsoft product line. You can learn more about Retina at http://www.eeye.com.
In Their Own Words
The following section is a direct quote from the eEye corporate web page on how they describe their vulnerability scanner, Retina:
Created by eEye Digital Security, Retina Network Security Scanner is recognized as the #1 rated network vulnerability assessment scanner by Network World magazine. Retina sets the standard in terms of speed, ease of use, reporting, non-intrusiveness and advanced vulnerability detection capabilities.
Retina can scan every machine on your network, including a variety of operating system platforms (e.g. Apple, Windows, UNIX, Linux), networked devices (e.g. switches, firewalls, routers, etc.), databases and third-party or custom applications, all in record time. After scanning, Retina delivers a comprehensive report that details all vulnerabilities and appropriate corrective actions and fixes.
eEye is a recognized digital security research powerhouse. As a result, Retina incorporates the most comprehensive and up-to-date vulnerabilities database -- automatically downloaded at the beginning of every Retina session. In addition to scanning against the most complete database of known vulnerabilities, customers can write their own customized audits. Furthermore, Retina’s unique, artificial intelligence option (CHAM) can be used for extensive testing and detection of previously unknown security issues within your network.
Scan and Detection Accuracy
Scans and reported vulnerabilities must be accurate with minimal false positives—defined as normal activity or configuration that the system mistakenly reports as malicious. The opposite also holds true, then; there can be no false negatives—defined as malicious activity that is not detected.
Retina has an excellent presentation interface for the execution of scans; it is intuitive and comes with a variety of other tools so it can be used for more than just a vulnerability scanner. One of the best features that Retina provides is the easy customization, scheduling, and penetration audit customization. What sets Retina apart is the capability to create scanning policies with different scans for different devices. For example, you can scan Internet servers differently than employee PCs. Figure 10-3 shows an example of targeting a specific device in Retina.
Figure 10-3. Selecting a Target Range in Retina

Documentation and Support
Documentation must be clear, concise, well written, and easy to understand (like this book). This includes reporting documentation and application operation so users can figure out how to make the application work and see the documented findings in the report.
Retina documentation is included in the Windows help file and appears to be complete, answering many of the questions a typical user would have. It does not contain many in-depth how-to’s, but it provides enough examples that their lack is not a hindrance. A web-based form that is submitted to the eEye technical support team only provides support options for users.
Reporting
The most important aspect of a vulnerability scanner is when you need to know the next steps after a vulnerability has been detected (that is, what was detected and how to fix it); thus, a report must be customizable, useful, and accurate. Figure 10-4 shows the summary of vulnerabilities after Retina completes its scan of your network.
Figure 10-4. Vulnerability Summary by Risk Level

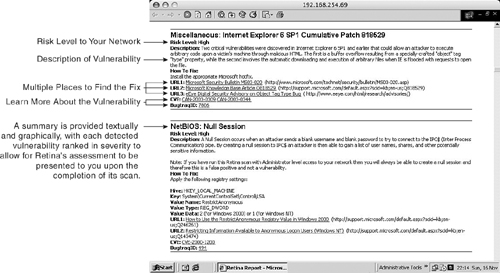
Like Nessus, Retina provides an overview of the detected vulnerability along with links to additional information and corrective actions, such as a Microsoft HotFix. Figure 10-5 shows specific detected vulnerability information, what the risk is and where to find the manufacturers fix.
Figure 10-5. Vulnerabilities Details
Vulnerability Updates
New vulnerabilities are constantly being released and, with today’s technology, every system should have a means of updating itself automatically.
Retina is exceptional is this regard; it can be configured not only to update its list of vulnerabilities, but also the application itself. Curiously, the open source movement has missed the boat on that feature. Retina takes a bit of getting used to, and it is an effective vulnerability scanner.
Penetration Testing Products
Vulnerability identification, detection, and prioritization are all assessment functions. You can only classify a product as penetration testing if it actually exploits a given vulnerability. Vulnerability assessment and penetration testing complement each other. They do very different things, so they must be two separate categories.
This “confusion” is often encountered during the sales process. Penetration testing product picks up where the vulnerability scans leave off.
Vulnerability assessment does an adequate job of providing the tester with a snapshot of the current network configuration. Unfortunately, this snapshot does not address the implication of a successful intrusion to organizational assets. It only relates what the vulnerabilities are; it does not probe deeper to reveal what happens when the vulnerabilities are exploited. The following details the limitations of vulnerability assessments and scanners:
• Provides just partial information assurance
• Only identifies vulnerabilities; does not provide meaningful weighting of vulnerabilities or prioritization of remedies
• Produces a long list of potential weaknesses, often including numerous false positives
• Does not demonstrate what information assets can be compromised
• Cannot simulate real-world attacks
• Does not exploit trust relationships between network components, nor demonstrate the implications of a successful attack
Core security is roaring into the security penetration testing marketplace with its exploit product, Core Impact! Yes, exploit product (they run applications in the product). Core Impact actually does not detect a vulnerability; rather, it exploits a vulnerability and installs an agent on the targeted server. This agent then allows you to escalate attacks and own the target machine. Core Impact product eliminates the annoying and embarrassing occurrence of false positives. Although the following section discusses at length how Core Impact achieves this, you can learn more about Core Impact at http://www.coresecurity.com.
In Their Own Words
The following section is a direct quote from the Core Security web page describing their product:
CORE IMPACT is the first comprehensive penetration testing solution for assessing specific information security threats to an organization. The product is designed to replace expensive, inconsistent manual penetration testing with a professional, state-of-the-art automated penetration testing product. CORE IMPACT goes beyond vulnerability scanners by enabling real-world attacks on IT assets and presenting analysis of information security risks in one comprehensive application.
Scan and Detection Accuracy
Scans and reported vulnerabilities must be accurate, with minimal false positives—defined as normal activity or configuration that the system mistakenly reports as malicious. The opposite also holds true, then; there can be no false negatives—defined as malicious activity that is not detected. Impact, however, does not actually scan for vulnerabilities; in fact, only limited scanning is possible with this product—in scanning mode, simple port scanning and target operating system detection. As you will see, this OS detection is a nice capability because it makes taking advantage of an exploit easier to accomplish! Why, though, are we talking about a product that does not detect my potential vulnerabilities? Impact eliminates false positives and actually allows you to compromise a host and proceed as if you were an attacker, thereby taking the analysis of vulnerability detection to a whole new level.
Documentation
Documentation must be clear, concise, well written, and easy to understand. This includes reporting documentation and application operation so that users can figure out how to make the application work and see the documented findings in the report.
Core Impact provides a variety of excellent reports that log every action of the application during its function, scanning, and compromising of hosts throughout your network. Impact can generate two types of reports:
• Findings report—A report that enumerates all the discovered hosts and their found vulnerabilities
• History report—An exhaustive report of all the activities performed by the auditor using Impact
Normally, these reports are standard type reports that you would expect. What makes them unique, however, is that Impact allows them to be customized and printed according to the level of detail you want to present. For example, the report given to an organization’s executive team should differ greatly from the report presented to the IT staff. Impact allows this level of customization.
Documentation and Support
The most important aspect of a vulnerability scanner is when you need to know the next steps after a vulnerability has been detected (that is, what was detected and how to fix it). Therefore, a report must be customizable, useful, and accurate.
When learning new software or applications, I find that it is important that the product has a good documentation and support. This allows users to learn on their time versus other methods, such as training or scheduled web seminars (which I’m not a big fan of).
Vulnerability Updates
New vulnerabilities are constantly being released, and with today’s technology, every system should have a way of updating itself automatically.
Impact allows for easy updating of the attack modules through a single click of a button. Core Security is committed to making the product grow and evolve so they have an aggressive development schedule. You will not find every possible vulnerability within Core Impact; however, there are also continual updates in this regard. It is a challenge to determine exactly which vulnerabilities become modules and, so far, observations have shown that good choices and options that rather limited; however, they are growing quickly.
Core Impact In Action
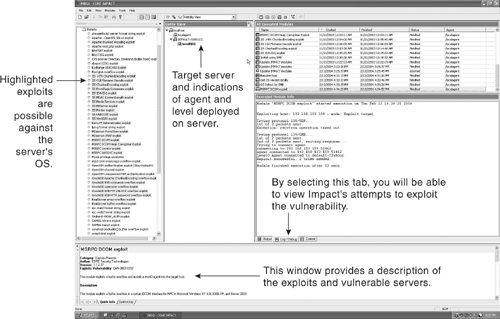
This section discusses how Core Impact actually exploits a vulnerability and installs a special, undetectable piece of software known as an agent on the target machine. This agent allows you to control the targeted server. The level of control depends on the vulnerability the agent has exploited. For example, in the figures that follow, the exploit taken advantage of allows full control of the targeted server. In Figure 10-6, you can see that Core Impact is targeting the MSRPC DCOM vulnerability against a Windows 2000 Professional laptop that runs SP3 with the corresponding agent deployed.
Figure 10-6. Core Impact Agent Deployed
After the agent is deployed on the server, you can determine the level of access you have gained by exploiting this vulnerability. As shown in Figure 10-7, the agent has been successfully deployed. Right-clicking the deployed agent displays a list of possible available options.
Figure 10-7. Agent Options
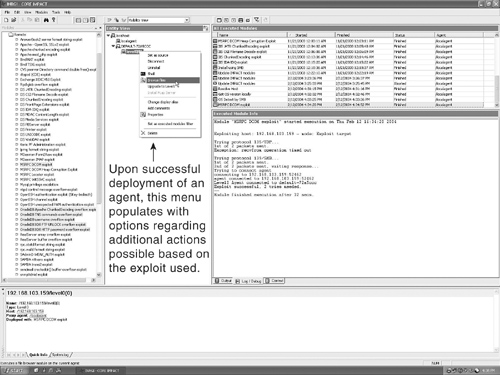
One of the scariest things about the possibilities in this scenario is that this agent allows you to browse all the files on the server on which the agent is installed. As shown in Figure 10-8, the agent can provide you with access to the most sensitive files on the exploited server. Specifically, you can upload, download, and manipulate files at your whim. Agents are not detectable when running on an exploited system; however, they are present and provide you with the capability to truly test whether your systems are vulnerable to exploits that might have been detected by a similar product, such as Nessus or Retina.
Figure 10-8. Browsing Files

The last point to cover is the mini-shell. Figure 10-9 shows the shell screen and the available options. As you can see, uploading, downloading, and executing files is simple once an agent is deployed.
Figure 10-9. Mini-Shell
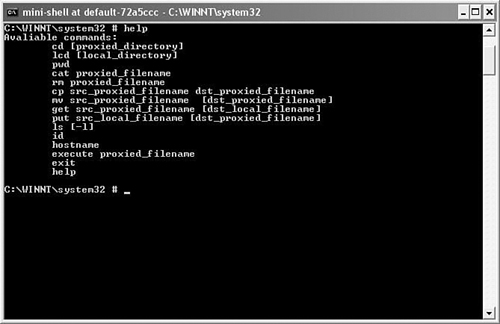
It is also possible to deploy additional agents against other servers when you find the weak link. In the example, it is possible to leverage that access gained against other internal devices. The interesting and disturbing part here is that, if these attacks were in fact detected, they would appear to be coming from the compromised machine!
Chapter Summary
This final chapter covered several additional new vulnerabilities and described how they are used to attack systems. Understanding these common attacks is crucial for understanding what the rest of the chapter is explaining. Security assessments and penetration testing are effective tools that, if used correctly, allow your network to be evaluated by qualified engineers who deploy the proper security analysis tools to find the vulnerabilities. A good security assessment, however, covers more than just the logical vulnerabilities in your network. The remainder of this chapter was dedicated to the various security scanning tools that are available, some of which are free open source solutions.
Chapter Review Questions
1. The freely available tool known as Ettercap can perform what four types of packet sniffing?
2. Define what a DDoS is and how it functions.
3. Identify and explain three reasons that can result in a back door exploit being present on a system.
4. Define the concept of firewalking.
5. Where should an external penetration and vulnerability assessment performed in your network?
6. When considering vulnerability scanners, why are a program’s ability to conduct an accurate scan crucial?
