Dangers with IIS Attacks
IIS and Web servers are immediately exposed to a dangerous environment, simply because of the roles the servers are expected to fulfill. IIS is intended to serve Web-based content to both internal and external users who rely on Web services to interact with your organization. In cases where IIS is serving Web content to Internet-based users, it is immediately exposed to significantly more threats than if it were simply providing content on internal networks. Access to IIS servers via the Internet allows anyone navigating the Internet to connect to the servers and perform various activities; this not only includes legitimate users but also malicious attackers.
alt1 Tip
Administrators who have taken a close look at their organizations' IIS logs will be able to agree that both legitimate and malicious activities can be witnessed almost on a daily basis. In addition to viewing IIS logs, administrators should also consider tracking malicious activity by viewing firewall, IDS, and IPS logs on a regular basis.
So, what are some of the dangers of hosting Web content and making the content publicly available? Well, it really depends on the scope of the application, type of content being served, and the sensitivity of the content. Depending on the type of content presented, the impact from an attack against IIS can be significant or just a nuisance. The following examples provide insight into some different situations where attacks against IIS can have various levels of impact on your organization.
One popular attack scenario often chosen by attackers and “hacktivists” is Web site defacement. Web site defacements usually involve finding a flaw in the implementation of a Web application or Web server and leveraging the flaw to change Web site content to spread a targeted message. Some examples of previous defacements can be viewed by visiting the zone-h.[I] Web site and browsing through the archives. Zone-h archives and tracks information about the defacements so the public can view the results of a successful defacement even after the Web site has been restored back to its original state. After viewing several of the recent defacements, you will probably notice some attacks are simply annoying and equivalent to graffiti; however, other examples will display a message crafted by the attacker to make a statement with the goal of promoting his or her political or other agenda.
alt1 Note
A hacktivist-launched attack is usually the work of an individual or a group trying to convey a message and influence people and organizations by using hacking techniques to spread their message. Many of the hacktivist activities of past years have spread messages against nuclear war, power, and political repression and recently have questioned the validity behind research data about global warming.J
Although a defacement attack may appear to be annoying, it can really cause a lot of damages to your organization's reputation if executed properly. In cases where online shopping sites are compromised, it may significantly impact the business that is generated from your site as online customers may lose confidence in how well your organization is focused on securing private customer information.
DoS attacks against IIS can also significantly impact customer confidence and cause prolonged service degradation or outages for legitimate users and customers. Several vulnerabilities exist that may affect IIS Web and FTP server components, allowing attackers to cause DoS conditions.
Attacks do not have to deny service or deface Web sites to be effective. In certain situations, an attacker may decide to compromise an IIS server with the sole purpose of gaining a foothold within the network and then conducting further attacks against internal resources. Once inside your network, an attacker may be able to launch additional attacks from the compromised systems and attempt to gain access to other targets within the Demilitarized Zone (DMZ) or other network segments. We will discuss this type of attack and defenses against it in the section “Defenses against IIS attacks” of this chapter.
Scenario 1: Dangerous HTTP Methods
One of the concerns when dealing with Web servers is learning how the server is configured and what types of interaction are allowed for unauthenticated visitors to applications running on the Web server. Some of these interactions come in the form of HTTP methods as defined in RFC 1945[K] – – HTTP/1.0 and RFC 2616[L] – – HTTP/1.1. HTTP has many methods that can allow various types of interaction between Web clients and Web servers. A brief review of some of the different methods available per the RFCs is provided in Table 6.2.
Table 6.2. IIS versions and platforms
| HTTP methods | |
|---|---|
| GET | The GET method is used when making requests for resources on a Web server. This is the type of request sent to a Web server when you click on a hyperlink to visit a Web site. It will return the header information and the body of the document requested |
| POST | The POST method is often usedwhen users fill out forms and send data to a server. A common example of using POST is when users log into Web servers by providing credentials and clicking a submit button |
| OPTIONS | The OPTIONS method requests information from the server about what methods may be available for a requested resource |
| PUT | The PUT method allows a user agent to place a new content or update an existing content to a specified location. The PUT method can overwrite or create new resources on the server if enabled |
| DELETE | The DELETE method will remove the content specified within the request if the method is enabled on the server |
| HEAD | The HEAD method is almost identical to the GET method; the key difference is the response will only include the metadata for a requested resource |
| TRACE | The TRACE method is often used for diagnostics, testing, and debugging |
Now that you have an understanding or refresher of the basics of HTTP methods, let's explore our first scenario. In this scenario, our attacker “Mike” is working on some projects for work and decides it's time to take a short break. During the day, Mike is a programmer for a company that creates complex network scanning tools but at heart, he just likes to break into networks for fun. He hopes to someday be one of the cool “penetration testers” he always hears about.
During his breaks, Mike likes to explore the Internet and enjoys finding flaws in Web site and server deployments. While he is on his break, he decides to fire up his MacBook Pro[M] and starts looking for targets of opportunity to continue with some research he has been doing on Web server security. At a loss for ideas about whom to experiment on, he decides to poke around the “Brandon's Discount Coding Books” Web site from where he had recently purchased his latest C++ programming book. After a few minutes of reviewing the structure of the Web site, he decides to run a few tools against the Web site and notices that one of the tools indicated the HTTP PUT method is enabled on the Web server. Mike knows this is something that can be very dangerous and that attackers can sometimes use the HTTP PUT method to upload files to the Web server.
In just a matter of minutes, Mike recalls reading that it is possible to upload files with the capability of executing commands on the underlying server. Since the Web server is using Active Server Pages[N] (ASP) for delivering content, he can use his knowledge of HTTP PUT and some specially crafted ASP pages to interact with the server. After a few more minutes of searching on the Internet, Mike finds an ASP page he can upload to interact with the server. Mike then transfers the file named cmd.asp to the server using the HTTP PUT method. Mike then opens up his Web browser and connects to the Web site and the ASP page he had just uploaded a few minutes earlier.
The ASP page uploaded is capable of interacting with the server's local cmd.exe application found on Windows operating systems. The page will allow Mike to interact not only with the Web site but also with the underlying operating system. Mike decides to attempt adding a new user to the operating system by using the net user command. If the Web server is running under the context of a privileged user allowed to create new accounts on the system, then the account should be created. Figure 6.1 illustrates Mike entering the command in the text box of the ASP page he had uploaded earlier to create a new user.
FIGURE 6.1. Add User from Web
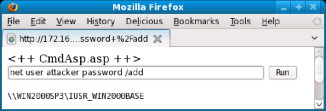
After Mike has run the command, he decides to see if the command actually worked and uses the net user command again to list all of the accounts currently configured on the system. The output from the net user command can be viewed once again on the ASP page that Mike had uploaded earlier by referring to Figure 6.2. As you can see, it appears that Mike has the appropriate permissions to interact with the system.
FIGURE 6.2. List Users
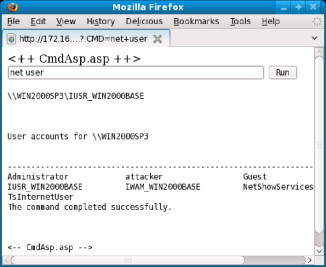
Next, Mike decides that he wants to learn a little bit more about the internal network connected to the Web server and uses the route print command to display a list of configured routes and other important network configuration information. The output for this command is seen in Figure 6.3.
FIGURE 6.3. Print Routes
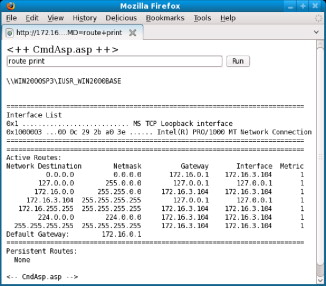
“Where to now?” you ask. Well, the sky is the limit depending on the type of access you currently have and the other protocols or interfaces available on the target system. It is fairly obvious that this attack can have a real negative impact on the security of the Brandon's Discount Coding Books online retail Web site. With the right conditions in place, this entire attack took under 5 minutes to perform. Is your Web server configured correctly?
Scenario 2: FTP Anonymous Access
FTP is a service that has been around for a very long time and many papers have been published on how to properly secure the service. It is used by many organizations as a convenient way of transferring large amounts of data from one location to another. A few examples of data usually transferred include Web content, store application updates, store backups from remote systems, and transaction logs. Many times administrators do a fairly good job at locking down FTP servers to only allow access to authorized users; however, penetration testers still find misconfigured FTP servers on a regular basis.
In this scenario, the attacker “James” is looking for a place to store the latest release of his favorite Massive Multiplayer Online Role-Playing Game (MMORPG), “World of Hackercraft.” This game has been very popular in the MMORPG gaming community for many years and being a true fan, it would be a shame for James not to share the newest release with his closest friends. Since many of his friends are located in various countries around the world, he decides it would be best to upload a copy of the software to a FTP server so they can access it anytime they wish.
Harnessing his knowledge of FTP and the power of the Internet, James first begins to scan blocks of IP addresses in an attempt to identify FTP servers capable of storing the game files. Specifically, James is attempting to identify FTP servers allowing anonymous access with write permissions to the FTP server. Fortunately for James, this does not take long as he was able to find a Voice over IP (VoIP) server with FTP and anonymous writable access enabled. Figure 6.4 illustrates the use of Metasploit to locate FTP servers with anonymous access enabled.
FIGURE 6.4. Metasploit FTP Scan

Once the server is located, he uploads a copy of the game to a directory that he had created on the FTP server. Figure 6.5 illustrates the attacker connecting to the FTP server, creating a directory, and uploading the game for his friends to later download. The software is now ready to be downloaded, so James sends an e-mail to his friends with the IP address of the server and the name of the directory in which the software is stored. James' friends are now able to connect to the FTP server and to the directory to which the software was uploaded and they begin to download the software for later use. James looks forward to meeting his friends in the game and fires up his game client to start exploring the strange new worlds found in the latest release.
FIGURE 6.5. FTP Upload

How is this attack possible? In this scenario, the attacker simply identified a common misconfiguration in the IIS FTP server and used it to his advantage. Anonymous access for FTP is dangerous enough by itself purely because many times sensitive data is left on the server and anyone who finds the server may be able to read the data. Increase the severity of the vulnerability by allowing write access to the server and it will not be long before someone takes advantage of it. As a matter of fact, now that James' friends know the IP address of the writable FTP server they may start uploading more games, cracked software, and other files whenever they like. Implementing proper authentication and authorization in addition to logging can help mitigate this type of risk. In addition, implementing Disk Quotas[O] for FTP is also a good idea and can help prevent abuse of the disk space available should an attacker gain access to a legitimate FTP user accounts.
Ohttp://learn.iis.net/page.aspx/307/using-fsrm-folder-quotas-with-ftp/
Scenario 3: Directory Browsing
When a Web server is hosting Web content, it has several ways that it can handle the data stored in its directories. In many cases, if a default page named as index.html or other is available then the server will render the page displaying something for the user accessing the Web site to look at. If the server is configured correctly, it will display an error indicating directory browsing is not allowed or enabled if a default page is not available. However, if the server is configured to allow directory browsing it will display the contents of directory with hyperlinks that can be clicked, allowing navigation through the directory structure of the Web site.
For many years, Apache Web Server[P] has enabled directory browsing for the /icons/ and /icons/small/ directories by default. Although the directory only contains icons, this can be problematic in cases where administrators may inadvertently add sensitive data to the directory that would expose it to anyone who may visit the site. Although this chapter focuses on IIS and IIS attacks, this Apache example was too good to pass up. An example of directory browsing can be viewed on the Apache Web site located at http://httpd.apache.org/icons/.
In this scenario, the attackers, “Chris” and “JR” are learning about how directory browsing can allow attackers to gain access to sensitive information on IIS Web servers deployed with directory browsing enabled. The information that can be viewed may not be intended for unauthenticated or unauthorized individuals and may provide information that can be used in future attacks. To experiment with learning about what type of information may be visible from directory browsing, Chris and JR decided to browse the Internet and see if they can identify sites having directory browsing enabled. After clicking through random Web sites for approximately 30 minutes, Chris and JR come to the conclusion that there must be a better way to search for misconfigured sites and do a little research.
Chris quickly learns that by using search terms including words that are commonly found on directory browsing pages, he can find many sites with directory browsing enabled. One example is using search terms such as “/scripts” and “to parent directory.” Upon reviewing the results of their search query, Chris and JR quickly realize they are on to something big. After clicking on one of the search results, they are now able to view the directory listed in Figure 6.6.
FIGURE 6.6. Directory Browsing

This directory contains a few files that are immediately appealing to JR as he knows that files with a .sql extension usually means it is an SQL script used to set up, maintain, or modify data stored on an SQL server. JR decides to download the config.sql file and view the contents to determine if any sensitive information is contained within it.
It appears Chris and JR hit the jackpot! Within the config.sql file, there are multiple SQL statements used to configure a database from scratch, and multiple user accounts and initial passwords are found in SQL statements used to populate the initial users database table. Now Chris and JR can use this information to attempt to authenticate to the Web application itself and possibly gain access to administrative functions that are used to configure the Web site. If database ports are available, the attackers may also be able to directly connect to the database and run SQL queries to mine data directly from the database.
This scenario provided you with a quick overview of why and how directory browsing attacks can allow attackers to gain access to your sensitive information. Ensuring that Web servers are not configured to allow directory browsing can help prevent attack such as these form becoming a reality.
alt2 Epic Fail
It is 2:00 a.m. and a penetration tester is working on a penetration test for a client. The tester discovers directory browsing is enabled on an IIS 5.0 Web server used to provide access to business partners and is also used to store internal records that have been scanned for archiving. After discovering that the Web server has directory browsing enabled, the penetration tester decides to use the DirBusterQ tool from the Open Web Application Security ProjectR (OWASP) to identify possible hidden directories.
Qwww.owasp.org/index.php/Category:OWASP_DirBuster_Project
Rwww.owasp.org/index.php/Main_Page
After running the tool, the penetration tester has identified a directory named “checks” as part of the results. The penetration tester investigates further to find that the directory has browsing enabled and it contains scanned copies of accounts receivable checks for the last 3 years. The analyst quickly contacts the client and informs him of the situation.
Unfortunately, this is a true story and you may imagine the surprise of the client when they realized their customer's sensitive data has been exposed in such a manner that anyone can access it. Sadly enough, no records are stored for dealing with configuration management and it is near impossible to determine how long the data has been exposed.
Future of IIS Attacks
IIS has proven to be a reliable platform for hosting Web content and providing services for over a decade. During this period, it has also been the target of attackers and a host to plenty of vulnerabilities. Even as we contribute to the content of this book, more vulnerabilities and exploits have been publicly disclosed, adding to issues previously discovered.
IIS and Web servers allow users to interact with the services and applications provided as a means of facilitating business. For these services to be available to the users seeking access to the information, Web servers must be deployed. Web services must be enabled to serve content to those who legitimately need access to them. Unfortunately, this also means attackers may also have access to the same content and be motivated to leverage vulnerabilities that are identified to gain access to data or resources hosted by the Web server.
In future releases of new versions of IIS and associated components, vulnerability researchers will continue to identify flaws and refine current attacks against IIS. It is likely that there are unpublished vulnerabilities being used against IIS servers today, which will not be discovered or published to the general public for years to come allowing attackers prolonged access to your organizations resources. Ensuring administrators and security professionals stay vigilant and informed of relevant threats will be an important part of protecting your organizations assets.
