Chapter 7. SharePoint – Multi-tier Attacks
Information in this Chapter
As we near the end of our journey through this book, we address some of the security concerns associated with multi-tier attacks and how they can be leveraged to access and seize data stored in Microsoft SharePoint Services and in Microsoft Office SharePoint Server (MOSS). Although this is the last chapter in this book, its placement does not imply that SharePoint is any less important to consider when developing an effective strategy to protect your network. SharePoint Servers store a wealth of information for organizations and are among one of the easiest to deploy the applications that Microsoft provides today. With great power and convenience comes many responsibilities for ensuring data is protected from unauthorized access.
How Multi-tier Attacks Work
Multi-tier attacks are not so different than many other things in life we deal with on a daily basis. Many people who approach problems in a structured, methodical manner find accomplishing goals is easier when taking on a series of smaller tasks to reach an end result. These smaller steps can provide some clarity and simplify the methods we can use to get from where we are to the place we want to be. Each step along the way is just another step closer to meeting the goal.
To further explain how multi-tier attacks may relate to everyday life, we explore some tactics that may be used by sales professionals to gain access to decision makers within an organization. Imagine yourself as a sales person who works in an organization that sells computers to large enterprises. Your sole source of income relies on the fact that you know how to identify sales opportunities and convince decision makers that your product is the best in the market at a very affordable price.
Large organizations are made up of several tiers of management that have different levels of decision making capabilities. Some of these levels of management include (ordered by highest level of authority to lowest level of authority) C-level executives, executive vice presidents, vice presidents, senior management, managers, and supervisors. Typically, decisions with little impact to the organization can be made by lower levels of management and important decisions may be reserved for higher levels of authority in the management structure.
As a sales person, it is prudent to ensure you are making your sales pitch to the people with the abilities of making the decisions to buy your product. You would most likely not want to spend a lot of time winning over a supervisor's approval if they do not have the authority to approve a large purchase of your computers. In some organizations, however, you cannot walk right into a vice president's office and make your sales pitch without trying to bypass the executive secretary or receptionist. This is where we enter our multi-tiered approach to make sure you get in front of the person who can make decisions.
Identifying people within the organization who may be at a lower level in the management chain may be fruitful if you can leverage relationships with those people in order to eventually meet a decision maker at the appropriate level with the appropriate authority to act. No one ever said sales was an easy or quick process, so meeting a supervisor or a manager in order to use them as a stepping stone toward meeting a vice president or an executive vice president may be a necessity.
Ultimately, we can use our access to other people within the organization to ensure that you eventually meet the people who can make the decisions to purchase your product. Something to remember, however, is that even though you have taken different approaches, there is no guarantee of success. Such is the life of a sales person and an attacker who may be using similar techniques to gain access to your SharePoint Server.
In the case of a multi-tiered attack against a SharePoint Server, we first identify the components that make up the SharePoint solution and break them down into possible avenues of attack, just as we did with our management structure example. These components act as different tiers within our overall solution and when combined together allow us to interact with SharePoint. Some of the tiers we think of right from the start include the operating system, Web Server, database, and finally the application we are attacking. Figure 7.1 provides a visual reference to the concept of how multiple tiers may contribute to the makeup of an overall solution.
FIGURE 7.1. Multi-tiered Attacks
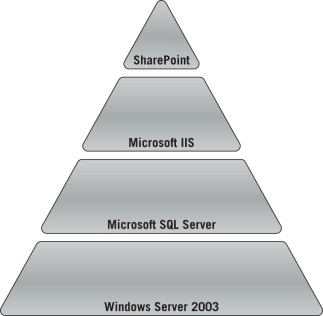
Each of the tiers within this layered approach to the multi-tiered attack scenario provides an attacker with countless possibilities to consider for attacks, which may provide access to the SharePoint application. In many cases, compromising one layer of the tier will allow attackers to punch forward into other layers and provide the opportunity to leverage more attacks.
As an example, recall one of the attack scenarios in Chapter 3 of this book, “SQL Server – Stored Procedure Attacks,” where the attacker was able to leverage access to a Structured Query Language (SQL) Server sysadmin level account. The attacker was able to use extended stored procedures to create a user account on the local operating system and then add the new user account to the local administrators group. This attack allowed the attacker to compromise the integrity of the operating system even though the attack originated from within the SQL Server application.
alt1 Note
Although we are using the example of tiers and high-level components such as the operating system, Web server, database, and application, the tiered approach can also include leveraging protocol, programming logic, and a variety of other types of flaws. This is dependent on the goals of the attacker and the tiers can extend much further or be far more granular than the three tiers we describe here.
Leveraging new attack avenues compounds the possibility of success the attacker may have with meeting his goals. This, of course, is an excellent reason why it is important to be aware of all applications, patch levels, and overall security of the network environment. Segregation of applications running on critical systems is also something to consider when deploying multi-tier applications, this concept will be covered later in this chapter in the “Defenses against Multi-tier Attacks” section.
Attackers may look for vulnerabilities in the operating system tier to exploit and take control of the entire operating system and all applications that reside on it. For instance, an attacker may identify a missing security patch for the Windows Server 2003 operating system that would allow the attacker to exploit it and gain administrator- or system-level access. This would allow our attacker to perform any tasks the privileged accounts could perform, including stealing your data.
The attacker may also take advantage of a vulnerability identified in Internet Information Services (IIS)[A] or the SQL Server[B] database residing on the server to gain access to the operating system or the data stored in the SharePoint database. Attacks can also be leveraged against antivirus solutions or almost any type of software with vulnerabilities an attacker can identify on a target system.
Bwww.microsoft.com/sqlserver/2008/en/us/default.aspx
Multi-tier Attack Anatomy
It is common for attackers to look for alternate avenues of attack if the primary target is configured securely. The old saying “There is more than one way to skin a cat” also applies to attacking computer networks and services. If an attacker cannot gain unauthorized access to a SharePoint Server by direct attacks, the attacker may consider leveraging flaws in other applications if it will help him gain the access he needs.
The discussions about attacking a SharePoint Server for the purpose of obtaining data will revolve around leveraging the infrastructure that supports SharePoint Server and not attacking SharePoint directly. This is primarily to illustrate that although applications may be well secured and locked down from a security perspective, the supporting infrastructure may not be.
