The drozer Agent is all set up and you've managed to fire up the drozer console; you can start firing off some drozer modules and really engage with your device's security.
The following recipe details the basic usage of the drozer framework to perform novel tasks such as enumerating the installed packages and filtering them based on package name.
Once you've got your drozer framework up and running, you may want to start scratching and messing around on your Android device. One useful thing you may want to do is list all the packages installed on your device. You can do this by firing off the following command from your drozer console:
dz> run app.package.list
You should see something similar to the following start appearing on your screen:
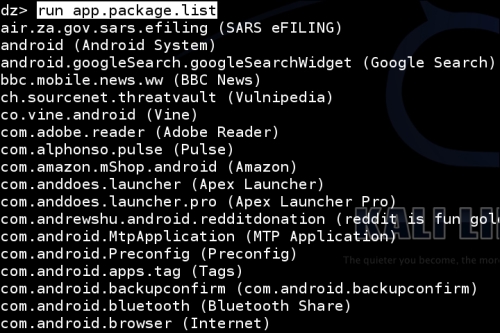
Let's take a look at the drozer source code to find out exactly how it interfaces with the package manager API to get all this useful information. I'm going to be explaining the code behind most of the modules so you get to see how drozer works, and build you up to writing a drozer module of your own later in this chapter! After all, that's what frameworks are about—building your own mods and add-ons.
Beware non-Python users/developers! You may need a little Python background to be able to read this source code; although, seeing that Python is pretty semantic even if you've never written Python code, you should be able to follow pretty easily. An added benefit of drozer's design is that they've basically mirrored the Android Java API to make module development easy to pick up for Android developers. So, in summary, you don't need to run out and get a book on Python just yet. If you've written Android apps before, this will be very easy to follow. Anyway, enough talk—let's see some code!
Note
The following code is available at https://github.com/mwrlabs/drozer/blob/master/src/drozer/modules/app/package.py (lines 99-121).
def add_arguments(self, parser):
parser.add_argument("-a", "--package", default=None, help="the identifier of the package to inspect")
parser.add_argument("-d", "--defines-permission", default=None, help="filter by the permissions a package defines")
parser.add_argument("-f", "--filter", default=None, help="keyword filter conditions")
parser.add_argument("-g", "--gid", default=None, help="filter packages by GID")
parser.add_argument("-p", "--permission", default=None, help="permission filter conditions")
parser.add_argument("-u", "--uid", default=None, help="filter packages by UID")
def execute(self, arguments):
if arguments.package == None:
for package in self.packageManager().getPackages(common.PackageManager.GET_PERMISSIONS | common.PackageManager.GET_CONFIGURATIONS | common.PackageManager.GET_GIDS | common.PackageManager.GET_SHARED_LIBRARY_FILES):
self.__get_package(arguments, package)
else:
package = self.packageManager().getPackageInfo(arguments.package, common.PackageManager.GET_PERMISSIONS | common.PackageManager.GET_CONFIGURATIONS | common.PackageManager.GET_GIDS |
common.PackageManager.GET_SHARED_LIBRARY_FILES)
self.__get_package(arguments, package)
def get_completion_suggestions(self, action, text, **kwargs):
if action.dest == "permission":
return android.permissions
def __get_package(self, arguments, package):
application = package.applicationInfoThe execute() method is called whenever you fire off the app.activity.info module from your console. It's essentially the entry point to the real hard work the module does.
We see the call to the package manager, self.packageManager().getPackages(…); this returns a list of package objects along with each package's permissions, configurations, GID, and shared libraries. The script calls self.__get_package() on each package object to print it out to the drozer console. The same is done for cases where a specific package is supplied via the command-line arguments.
If you'd like to get your own copy of this code, you can grab it from the official drozer GitHub repository, which is very easy to find if you Google hard enough. But to make your lives easier, I've dropped a URL to the code repository in the See also section of this recipe.
The dz> run app.package.list command is a wrapper to the Android package manager; because of this, one of the cool things you can do is filter through applications based on their name, as follows:
dz> run app.package.list –f [application name]
Here, [application name] is the name of the application or package you want to check for. Here's an example:
dz> run app.package.list –f facebook
Another enumeration-type module in drozer you can use to extract information is app.package.info, which will fetch the following information about a package:
- Permissions
- Configuration
- Group IDs
- Shared libraries
You can use this module by firing off the following command from your drozer console:
dz> run app.package.info --help
When used this way, it will extract all the related information about all the packages on your Android device.
Naturally, you might want to narrow down this information to a particular package:
dz> run app.package.info –-package [package name]
You could also use the shorthand for the switch, as follows:
dz> run app.package.info –a [package name]
Here's an example:
dz> run app.package.info –a com.android.browser
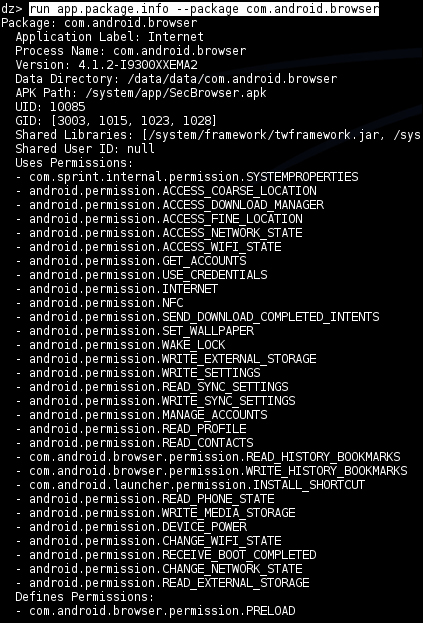
A quick explanation of the output shown in the previous screenshot is as follows:
- Application Label: The displayed name of the application
- Process Name: The name of the process that this application runs in
- Version: The version of the application installed
- Data Directory: The full path to the directory that will be used to store the user data and application specifically associated to this application
- APK Path: The path to the actual Android application package file on the device
- UID: The user ID associated to the application; everything it does on the Android system will be done using the access rights associated to this user ID, unless it gets other applications and processes to do things on its behalf
- GID: The system group IDs associated to this application's user ID; usually, these are associated to an application based on a number of special permissions that are granted to the application
- Shared Libraries: The full path to the shared libraries used by this application
- Shared User ID: The shared user ID this application is allowed to use
- Uses Permissions: A list of the permissions granted to this application
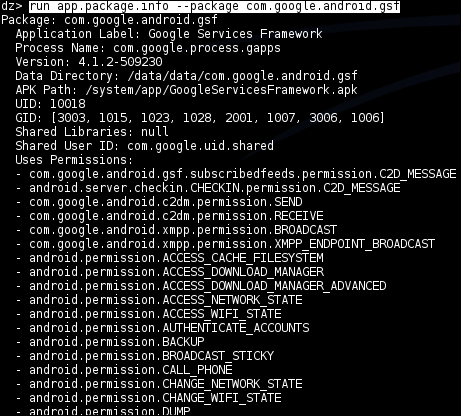
Another example, in case you have a Nexus device, would be to run this against the Google Services Framework as follows:
dz> run app.package.info –a com.google.android.gsf
The previous command should produce the output as shown in the following screenshot:
Another cool thing you can do with the app.package.info module is find packages based on permissions. You can do that by executing the following command:
dz> run app.package.info –p [permission label]
An example would be the following:
dz> run app.package.info –p android.permission.INTERNET
Why is this so cool? Well, you may want to know all the applications with a set of dangerous permissions. I mean, do you know how many of your applications have the INTERNET permission or any other dangerous permission? No? Exactly!
- The drozer GitHub repository at https://github.com/mwrlabs/drozer
- The
package.pydrozer module at https://github.com/mwrlabs/drozer/blob/master/src/drozer/modules/app/package.py
