In this recipe, I'm going to show you how to write a certificate enumerator, which does nothing more than pull application certificates as hexadecimal digests and dump them on your screen. The reason I've included this is because, firstly, it demonstrates how you interface with the package manager and pull some information the other modules in this section don't. Secondly, it may be useful to get your hands on an application signature when you're looking for all apps that have been signed with the same public key, which is useful because often developers and malware authors will use the same key for most of their applications. It will also allow you to identify apps that may share resources and autonomously grant each other permissions; how this happens will be discussed in detail in the next section.
- Open up your favorite text editor and enter the following code:
from drozer.modules import Module, common from drozer import android import M2Crypto import subprocess from OpenSSL import crypto class Info(Module,common.Filters,common.PackageManager): name = "Print the Signer certificate for an application" description = "this module allows you to print the signer x509 certificate for a given applicaiton" examples = "run ex.cert.info -p com.android.browser" author = "Keith Makan" date = "11-11-2013" license = "GNU GPL" path = ["ex","cert"] def add_arguments(self, parse): parse.add_argument("-p","--package",default=None,help="The Package Name") def execute(self,arguments): pm = self.packageManager() if arguments.package == None: for info in pm.getPackages(common.PackageManager.GET_SIGNATURES): self.stdout.write("[*] certificate info for {%s} " % (info.packageName)) self.__print_certs(info) elif arguments.package != None: self.stdout.write("[*] certificate info for {%s} " % (arguments.package)) info = pm.getPackageInfo(arguments.package,common.PackageManager.GET_SIGNATURES) self.__print_certs(info) else: self.stdout.write("[!] cannot process arguments : '%s' " % (repr(arguments))) def __print_certs(self,info): sigs = info.signatures[0].toCharsString() sigs = sigs + ' ' temp_cert = open("/tmp/cert.crt","w") end = 2 #converting to DER file for start in range(0,len(sigs)-2,2): temp_cert.write(chr(int(sigs[start:end],16))) end +=2 temp_cert.flush() temp_pem = open("/tmp/cert.pem","w") temp_pem.flush() temp_pem.close() certtext = subprocess.check_output(["openssl","x509","-inform","DER","-in","/tmp/cert.crt","-outform","PEM","-out","/tmp/cert.pem","-text"]) temp_pem = open("/tmp/cert.pem","r") pem_cert_string = temp_pem.read() temp_pem.close() x509cert = crypto.load_certificate(crypto.FILETYPE_PEM,pem_cert_string) m2crypto_crt = M2Crypto.X509.load_cert_string(pem_cert_string,1) self.stdout.write("[*] Version : %s " % (x509cert.get_version())) self.stdout.write("[*] Issuer : %s " % (self._print_x509Name(x509cert.get_issuer()))) self.stdout.write("[*] Subject : %s " % (self._print_x509Name(x509cert.get_subject()))) self.stdout.write("[*] Algorithm : %s " % (x509cert.get_signature_algorithm())) self.stdout.write("[*] NotBefore : %s " % (x509cert.get_notBefore())) self.stdout.write("[*] NotAfter : %s " % (x509cert.get_notAfter())) self.stdout.write("[*] Key Length : %s " % (x509cert.get_pubkey().bits())) self.stdout.write("[*] Public Key : %s " % (self._print_key(m2crypto_crt))) self.stdout.write(" ") #self.stdout.write(" %s " % (certtext)) def _print_x509Name(self,xname): return ''.join(["%s=%s " % (i[0],i[1]) for i in xname.get_components()]) def _print_key(self,m2cert): return m2cert.get_pubkey().get_rsa().as_pem() - Save it to your module repo; if you don't have one, simply create a file somewhere on your machine where you'll save all your modules. You can install the module by executing the following command from your drozer console:
dz> module install [path to your module code]And when this is all done, you can run the module using the following command:
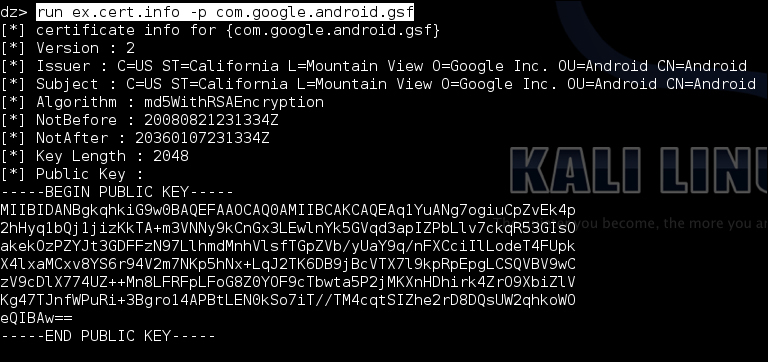
run external.cert.info –p com.google.android.gsfYou should see something like the following screenshot on your screen: