Kerberos is a type of Network authentication protocol, which uses a secret key cryptography to communicate between the client and the server. It was developed at MIT to mitigate many security problems like replay attacks and spying. It makes use of tickets to provide authentication for the server-side resources. It followed the idea of avoiding additional logins (single sign on) and storing the passwords at a centralized location.
In a nutshell, the authentication server, the ticket granting server and the host machine act as the leading cast in the process of authentication.
- Authentication Server: A server-side application which aids in the process of authentication by making the use of submitted credentials of a user
- Ticket Granting Server: A logical key distribution center (KDC) which validates the tickets
- Host Machine: A server which accepts the requests and provides the resources
You can see this in the following diagram:
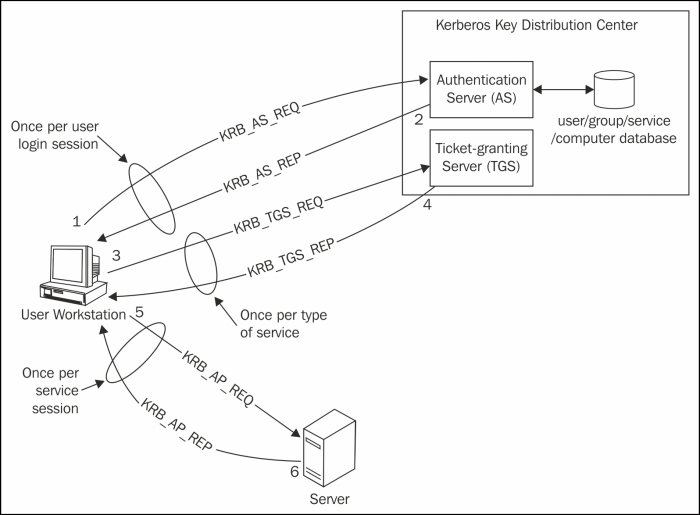
Authentication with Kerberos takes place in the following steps:
- When a person logs into his machine with the credentials, a request will be sent to ticket granting ticket (TGT).
- If the verification of the user turns out to be true, when checked from the user database, a session key and a TGT will be created by the authentication server (AS).
- Thus, the obtained TGT and session key will be sent back to the user in the form of two messages, in which TGT will be encrypted with the ticket granting the server's secret key. The session key will be encrypted with the client secret key and it contains a time stamp, life time, TGS name and TGS session key.
- The user on the other end, after receiving the two messages, uses the client secret key that is, the user's password to decrypt the messages of the session key. The TGT cannot be decrypted without the TGS secret key.
- With the available information of the
sessionkey and the TGT, the user can send a request for accessing the service. The request contains two messages and some information at this point. In the two messages, one is an encrypted message, containing a user ID and timestamp. The other is a decrypted message, containing the HTTP service name and the life time of the ticket. With the above two messages, an authenticator and TGT will be sent to the ticket granting server. - The messages and the information (Authenticator and TGT) will be received by the TGS, and it will check for the credibility of the HTTP service from the KDC database and decrypt both the authenticator and the TGT. Once everything goes fine, the TGS tries to verify some important parts like client ID, time stamp, lifetime of TGT and authenticator. If the verification turns out to be successful, then the TGS generates an encrypted HTTP service ticket, HTTP service name, time stamp, information about the ticket validity and the session key of HTTP service. All of the preceding ones will be encrypted by the HTTP Service session key and will be sent back to the user.
- Now, the user receives the information and decrypts it with the TGS session key that he/she received in the earlier step.
- In the next step, to access the HTTP service, the user sends an encrypted HTTP service ticket and an authenticator which is encrypted with the HTTP service session key to the HTTP service. The HTTP service uses its secret key to decrypt the ticket and takes hold of the HTTP service session key. With the acquired HTTP service session key, it decrypts the authenticator and verifies the client ID time stamp, lifetime of ticket, and so on.
- If the verification turns out to be successful, the HTTP service sends an authenticator message with its ID and time stamp to confirm its identity to the user. The user's machine verifies the authenticator by making use of HTTP service session key and identifies the user as an authenticated one who accesses the HTTP service. From then onwards, the HTTP service can be accessed by the user without any bumps, until the session key expires.
Kerberos is a secure protocol as the passwords from the user can never be sent as plain text. As the process of authentication takes place with the agreement of both the client and the server through encryption and decryption, it turns out to be a rigid one to break to some extent. The other advantage comes from its capability to give server access to the user until the session key expires without reentering the password.
Kerberos does have some disadvantages:
- The server must be continuously available for the verification of the tickets which may result in blocking, if the server goes down.
- User's keys are saved on a central server. A breach of this server may compromise security for the whole infrastructure.
- Kerberos necessitates a heavy infrastructure, which means a simple web server is not sufficient.
- The setup and the administration of Kerberos requires specialized skills.
Requests takes the support of the requests-kerberos library for the purpose of authentication. For this reason, we should first install the requests-kerberos module.
>>> pip install 'requests-kerberos'
Let's have a look at the syntax:
>>> import requests >>> from requests.kerberos import HTTPKerberosAuth >>> requests.get('https://demo.example.com/resource/path', auth=HTTTPKerberosAuth())
In the preceding lines of code, we carried out Kerberos authentication by creating an HTTPKerberosAuth object and setting it to the auth parameter which will be submitted to the server.
