OAuth is an open standard authorization protocol, which allows client applications a secure delegated access to the user accounts on third party services such as Google, Twitter, GitHub and so on. In this topic, we are going to introduce the two versions:- OAuth 1.0 and OAuth 2.0.
OAuth authentication protocol came up with an idea of mitigating the usage of passwords, replacing them with secure handshakes with API calls between the applications. This was developed by a small group of web developers who are inspired by OpenID.
Here are the Key terms used in the process of OAuth authentication.
- Consumer: The HTTP Client who can make authenticated requests
- Service Provider: The HTTP Server, which deals with the requests of OAuth
- User: A person who has the control over the protected resources on the HTTP Server
- Consumer Key and Secret: Identifiers which have the capability to authenticate and authorize a request
- Request Token and Secret: Credentials used to gain authorization from the user
- Access Token and Secret: Credentials to get access to the protected resources of the user
You can see this in the following diagram:
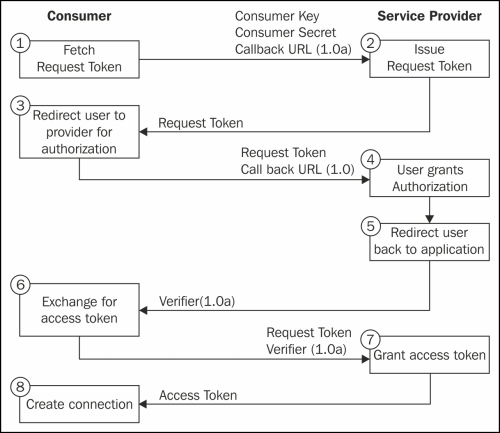
Initially, the client application asks the service provider to grant a request token. A user can be identified as an approved user by taking the credibility of the request token. It also helps in acquiring the access token with which the client application can access the service provider's resources.
In the second step, the service provider receives the request and issues request token, which will be sent back to the client application. Later, the user gets redirected to the service provider's authorization page along with the request token received before as an argument.
In the next step, the user grants permission to use the consumer application. Now, the service provider returns the user back to the client application, where the application accepts an authorized request token and gives back an access token. Using the access token, the user will gain an access to the application.
The requests_oauthlib is a an optional library for oauth which is not included in the Requests module. For this reason, we should install requests_oauthlib separately.
Let us take a look at the syntax:
>>> import requests >>> from requests_oauthlib import OAuth1 >>> auth = OAuth1('<consumer key>', '<consumer secret>', ... '<user oauth token>', '<user oauth token secret>') >>> requests.get('https://demo.example.com/resource/path', auth=auth)
OAuth 2.0 is next in line to OAuth 1.0 which has been developed to overcome the drawbacks of its predecessor. In modern days, OAuth 2.0 has been used vividly in almost all leading web services. Due to its ease of use with more security, it has attracted many people. The beauty of OAuth 2.0 comes from its simplicity and its capability to provide specific authorization methods for different types of application like web, mobile and desktop.
Basically, there are four workflows available while using OAuth 2.0, which are also called grant types. They are:
- Authorization code grant: This is basically used in web applications for the ease of authorization and secure resource delegation.
- Implicit grant: This flow is used to provide OAuth authorization in Mobile Applications.
- Resource owner password credentials grant: This type of grant is used for applications using trusted clients.
- Client credentials grant: This type of grant is used in machine to machine authentication. An in-depth explanation about grant types is out of the scope of this book.
OAuth 2.0 came up with capabilities which could overcome the concerns of OAuth 1.0. The process of using signatures to verify the credibility of API requests has been replaced by the use of SSL in OAuth 2.0. It came up with the idea of supporting different types of flow for different environments ranging from web to mobile applications. Also, the concept of refresh tokens has been introduced to increase the security.
Let us take a look at the usage:
>>> from requests_oauthlib import OAuth2Session >>> client = OAuth2Session('<client id>', token='token') >>> resp = client.get('https://demo.example.com/resource/path')
