In order to avoid all the information between the users' browsers and the Odoo server, that is to be sent in clear over the network, it is necessary to use the HTTPS protocol that encrypts the exchanges. Odoo cannot do this natively, and it is necessary to configure a reverse proxy that will handle the encryption and decryption on behalf of the Odoo server. This recipe shows how to use nginx (http://nginx.net) for this.
You should know the public name of the server and configure your DNS accordingly. In this recipe, we will use odoo.example.com as the name of your server.
If you want your Odoo instance to be visible by all browsers, you will need to get an SSL certificate signed by a recognized Certification Authority (CA). Using a self-signed certificate can also be made to work, but modern browsers tend to refuse these.
To generate an SSL key, you can use the following process:
- Install
openssl:$ sudo apt-get install openssl - Generate the key for your server:
$ mkdir ~/sslkey $ openssl genrsa -out ~/sslkey/server.key 2048
- Generate a signing request:
$ openssl req -new -key ~/sslkey/server.key -out ~/sslkey/server.csr - The preceding command will ask you a series of questions about your company and your Odoo server's URL. Don't get these wrong or your certificate will be unusable.
- You will be able to send the file,
~/sslkey/server.csr, to a Certification Authority (CA) of your choice. The CA will send you back a file calledserver.crt, which we will use in the recipe.
In order to access your instance using HTTPS via nginx, you need to follow these steps:
- As root, install
nginx:# apt-get install nginx - As root, create a configuration file in
/etc/nginx/sites-available/odoo-80:server { listen [::]:80 ipv6only=off; server_name odoo.example.com; access_log /var/log/nginx/odoo80.access.log combined; error_log /var/log/nginx/odoo80.error.log; location / { rewrite ^/(.*) https://odoo.example.com:443/$1 permanent; } }
- Create a configuration file in
/etc/nginx/sites-available/odoo-443:server { listen [::]:443 ipv6only=off; server_name odoo.example.com; ssl on; ssl_certificate /etc/nginx/ssl/server.crt; ssl_certificate_key /etc/nginx/ssl/server.key; access_log /var/log/nginx/odoo443.access.log combined; error_log /var/log/nginx/odoo443.error.log; client_max_body_size 128M; gzip on; proxy_read_timeout 600s; index index.html index.htm index.php; add_header Strict-Transport-Security "max-age=31536000"; proxy_set_header Host $http_host; proxy_set_header X-Real-IP $remote_addr; proxy_set_header X-Forward-For $proxy_add_x_forwarded_for; proxy_set_header X-Forwarded-Proto https; proxy_set_header X-Forwarded-Host $http_host; location / { proxy_pass http://localhost:8069; proxy_read_timeout 6h; proxy_connect_timeout 5s; proxy_redirect http://$http_host/ https://$host:$server_port/; add_header X-Static no; proxy_buffer_size 64k; proxy_buffering off; proxy_buffers 4 64k; proxy_busy_buffers_size 64k; proxy_intercept_errors on; } location /longpolling/ { proxy_pass http://localhost:8072; } location ~ /[a-zA-Z0-9_-]*/static/ { proxy_pass http://localhost:8069; proxy_cache_valid 200 60m; proxy_buffering on; expires 864000; } }
- As root, link the configuration file in
/etc/nginx/sites-enabled/:# ln -s /etc/nginx/sites-available/odoo80 /etc/nginx/sites-enabled/odoo80 # ln -s /etc/nginx/sites-available/odoo443 /etc/nginx/sites-enabled/odoo443
- As root, remove
/etc/nginx/sites-enabled/default:# rm /etc/nginx/sites-enabled/default - As root, copy the ssl certificate and server key to the appropriate directories
# mkdir -p /etc/nginx/ssl # chown www-data /etc/nginx/ssl # mv server.key server.crt /etc/nginx/ssl # chmod 710 /etc/nginx/ssl # chown root:www-data /etc/nginx/ssl/* # chmod 640 /etc/nginx/ssl/*
- As Odoo, edit the production configuration file of the instance to enable
proxy_mode:proxy_mode = True - As root, restart your
odooinstance andnginx:# service odoo restart # service ng inx restart
We are using nginx as a reverse HTTP proxy. Incoming HTTP and HTTPS connections are handled by nginx, which delegates the processing of the requests to the Odoo server. The Odoo server is configured to only listen on the local loopback interface (127.0.0.1) on port 8069 for normal requests (xmlrpc_port) and port 8072 for the long polling requests (longpolling_port). You may need to adapt the port numbers to your configuration.
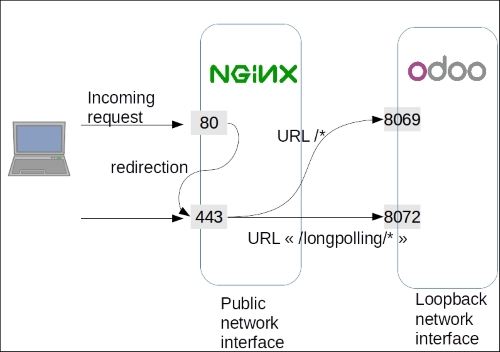
The recipe sets up two files. The first one is the configuration for incoming connections on port 80 using the HTTP protocol. We don't want these because they are in clear text, meaning that the passwords can be sniffed. Therefore, we set up nginx to redirect the URLs permanently to port 443 using the encrypted HTTPS protocol.
The second file is a bit more complex and configures the way nginx should handle connections using the HTTPS protocol:
- The first configuration block configures the SSL protocol, the encryption key, and certificate, as well as the log file's location.
- The second block sets some headers on the requests to handle the proper reverse proxying over HTTPS.
- The
location /block defines the default processing of incoming requests; they will be proxied to the Odoo server listening on port8069. - The
location /longpollingblock handles queries made on URLs starting with/longpolling, which are then forwarded to Odoo on port8072. These connections are used by the bus addon module to send notifications to the web client. - The
location ~ /[a-zA-Z0-9_-]*/static/block uses a regular expression to match the URLs of the static files of Odoo modules. These files are rarely updated, and so we ask nginx to cache them in order to lighten the load on the Odoo server.
This recipe focuses on the nginx configuration. You may be more familiar with other tools such as the Apache web server and mod_proxy. In this case, you can of course use these to achieve a similar setup.
- For more information about the various nginx configuration options, see http://nginx.org/en/docs/.
- For a tutorial on the configuration of Apache2 as a reverse proxy and the use of a personal certification authority, take a look at http://antiun.github.io/odoo-reverse-proxy-howto/.
