Download the Burp Suite free edition from http://portswigger.net/burp/download.html and then run it. Make sure you use a browser that will not interfere with the assessing of your application testing. Most current browsers will mitigate much of your testing automatically, and most of these protective measures cannot be turned off, to complete unhindered testing. Firefox has these protection capabilities, but they can be turned off for development and security analysis. Additionally, the plugin support that Firefox has allows you to assess applications better. Many an assessor who has just started has not been able to understand why some new Cross-site Scripting (XSS) attack that they just executed was blocked. Often, it is some built-in browser protection in Chrome or Internet Explorer that says it is off, but really, it is not.
Now, from Firefox, turn on the local proxy support by entering 127.0.0.1 and port 8080 in the manual proxy configuration, as shown here:

While assessing web applications, you would want to restrict your scope to only the system you want to test. Make sure that you set this and then filter all other targets to clean up your output and prevent yourself from attacking other hosts by mistake. This can be done by either right clicking on the host in the Site map window or clicking on the Scope tab and adding it manually, as shown in this screenshot:

Now that Burp has been set up, we can start assessing the DVWA site, which has a simple login page that requires a username and a password. When each of these web pages are loaded, you have to either disable the Intercept mode or click on Forward to go to the next page. We are going to need the intercept capabilities in a few minutes, so we are going to leave that enabled. Basically, Burp Suite—as mentioned previously—is a transparent proxy that has all of the specified traffic sent between the website and the browser. This allows you to manipulate data and traffic in real time, which means that you can have the application perform differently than intended.
To start this analysis, we have to see how the login page formats its request as it is sent to the server so that it can be manipulated. So, we provide a bad username and password in the login prompt—the letter a for both—and capture the request in the proxy. The following image shows the raw capture from the erroneous login that was captured by Burp Intruder.
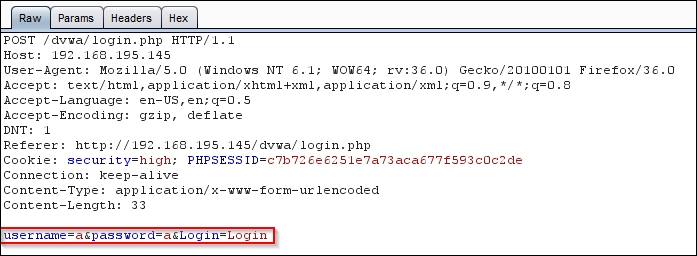
Then, right-click on it, select Send to Intruder, and turn off Intercept in the proxy. This allows us to repeatedly manipulate the request sent to the server to see whether we can get different responses.
Following this pattern, we can configure the attack to run through a list of usernames and passwords, and this may grant us access. The click on the Intruder major tab and the Position minor tab. Select the two positions for the originally supplied username and password and then select Cluster Bomb from the drop-down, as shown in the following screenshot:
Note
There are multiple types of intruder attack, and cluster bomb will be the most commonly used type in your assessments. More details about intruder attacks can be found at https://support.portswigger.net/customer/portal/articles/1783129-configuring-a-burp-intruder-attack.

Then create two lists; payload set 1 is for the usernames, and payload set 2 is for the passwords.

Next, select Always for following redirections, as logins often create website transitions.

Then click on the Intruder menu item and select Start, which will show a new popup. You can identify the viable account by the change in size compared to the other results.

Now you can gain direct access to the web application, which allows you to move through the application.
