In AWS, the combination of Users, Groups, and Roles can be used to build a model for role-based access for users and applications using AWS services. As we have already mentioned, a user in AWS represents an entity that needs to be uniquely identified within the AWS environment when interacting with AWS services and components. This entity can be a user, a service, a server, or any other uniquely identifiable initiator of a request to AWS services. We have the ability to create up to 5,000 users in IAM in our AWS account. To manage users, we will sign in to the AWS Management Console with the newly created user and navigate to the Users section of AWS IAM:

Here, we can click on the user and manage the user's properties. On the Summary page, we can see the policies attached to this user:
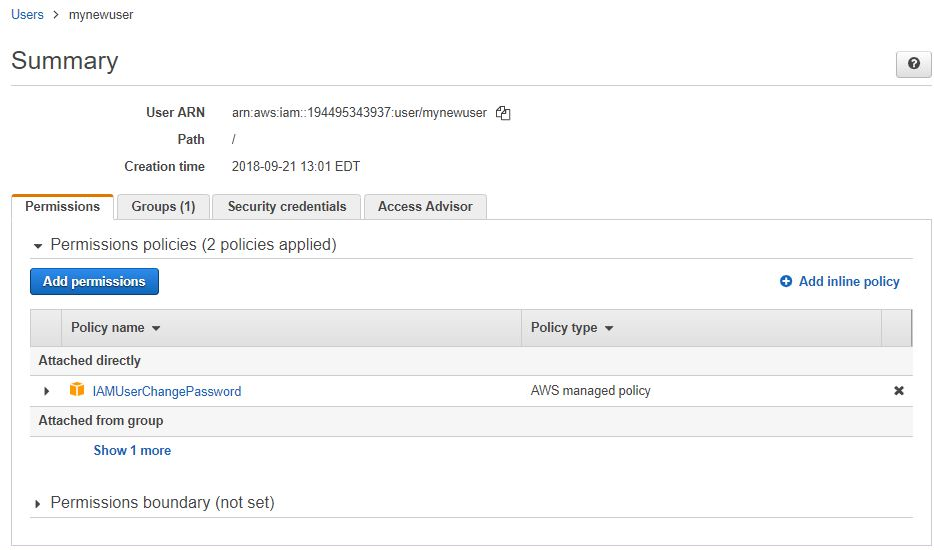
Since we chose to set a global password policy for all users to be able to change their own password, all users will automatically be assigned the default IAMUserChangePassword policy, which defines this permission. All other permissions are set via the group membership, which we can see if we click on Groups. Here, we are able to look at the group membership and add the user to other groups:

By clicking on Security credentials, we can manage the way this user authenticates to AWS, reset the console password, manage the MFA device, and inactivate and create new access key IDs and secret access keys. As we already explained, the credentials are visible to the administrators only upon creation:

Let's go ahead and rotate the user's access key by making the existing key inactive by clicking on Make Inactive, then clicking on Create access key to create a new one. Once we have done this, we can see two access key IDs in our console, one of them inactive and one of them active. A user can have multiple access keys assigned to them and all of those can be arbitrarily deactivated and reactivated if needed:

You are encouraged to explore the Security Credentials tab and perform all of the tasks that can be done in this section:
- Reset the user's management console password
- Add an MFA device to the user
- Manage access keys
- Optionally, you can test out a signing certificate or SSH key for this user if you have one
