Let us look at some features of the AWS CloudHSM service.
AWS CloudHSM provides FIPS 140-2 level 3 compliant HSM for using and generating your encryption keys. It protects your encryption keys with a single tenant, exclusive access, and dedicated tamper-proof device in your own AWS VPC.
AWS CloudHSM offers a utility pricing model like many other AWS services. You pay only for what you use and there are no upfront costs whatsoever. You are billed for every running hour (or partial hour) for every HSM you provision within a CloudHSM cluster.
AWS CloudHSM is a fully managed service, so you need not worry about scalability, high availability, hardware provisioning, or software patching. These tasks are taken care by of AWS. The AWS also takes automated encrypted backups of your HSM on a daily basis.
AWS monitors health and network availability of HSMs. It does not have access to keys stored inside these HSMs. This access is available only to you and users authorized by you. You are responsible for keys and cryptography operations. This separation of duties and role-based access control is inherent to CloudHSM design, as shown in the following figure:
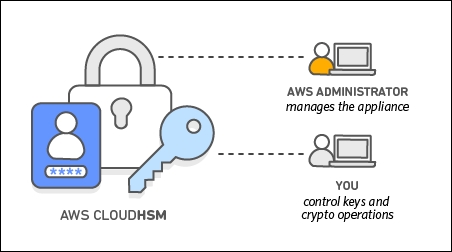
Figure 5: AWS CloudHSM separation of duties
A CloudHSM cluster can store up to 3,500 keys of any type or size. It integrates with AWS CloudTrail so all activities related to CloudHSM are logged and you can get a history of all AWS API calls made to CloudHSM.
With so many features and benefits, AWS CloudHSM has many use cases when it comes to securing your data. Let us look at some of the most popular use cases for this service.
Web servers and web browsers often use SSL or TLS for a secure connection to transfer data over the internet. This connection requires the web server to use a public-private key pair along with a public key certificate in order to establish an HTTPS session with each client. This activity acts as an overhead for the web server in terms of additional computation. CloudHSM can help you offload this overhead by storing the web server's private key in HSM as it is designed for this purpose. This process is often known as SSL acceleration.
A certificate authority is an entity entrusted for issuing digital certificates for a public key infrastructure. These digital certificates are used by an individual or an organization for various scenarios by binding public keys to an identity. You need to protect private keys that are used to sign the certificates used by your certificate authority. CloudHSM can perform these cryptographic operations and store these private keys issued by your certificate authority.
Oracle databases offer a feature called transfer data encryption for encrypting data before storing it on disk. This feature is available in some versions of Oracle. It uses a two-tier key structure for securing encryption keys. Data is encrypted using the table key and this table key is encrypted by using the master key. CloudHSM can be used to store this master encryption key.
