The final goal of the enumeration portion of reconnaissance is to identify the services and applications that are operational on the target system. If possible, the attacker would want to know the service type, vendor, and version to facilitate the identification of any vulnerability.
The following are some of the several techniques used to determine active services:
- Identify default ports and services: If the remote system is identified as having a Microsoft operating system with port 80 open (the WWW service), an attacker may assume that a default installation of Microsoft IIS is installed. Additional testing will be used to verify this assumption (nmap).
- Banner grabbing: This is done using tools such as amap, netcat, nmap, and Telnet.
- Review default web pages: Some applications install with default administration, error, or other pages. If attackers access these, they will provide guidance on installed applications that may be vulnerable to attack. In the following screenshot, the attacker can easily identify the version of Apache Tomcat that has been installed on the target system.
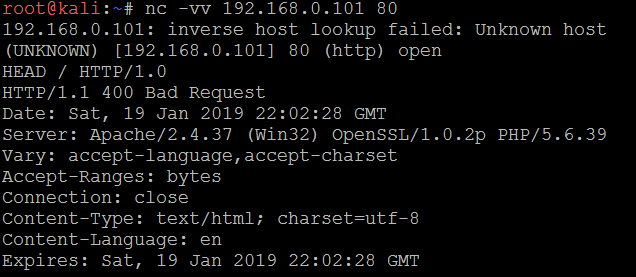
- Review source code: Poorly configured web-based applications may respond to certain HTTP requests such as HEAD or OPTIONS with a response that includes the web server software version, and, possibly, the base operating system or the scripting environment in use. In the following screenshot, netcat is launched from the command line and is used to send raw HEAD packets to a particular website. This request generates an error message (404 not found); however, it also identifies that the server is running Apache 2.4.37 with application server PHP 5.6.39: