SNMP stands for Simple Network Management Protocol; traditionally, this is used for collecting information about configuration of network devices such as printers, hubs, switches, routers on internet protocol, and servers. Attackers can potentially take advantage of SNMP that runs on UDP port 161 (by default) when it is poorly configured or left out with default configuration having a default community string. SNMP has been developed from 1987: version 1 had plain text passwords in transit, version 2c had improved performance, but still plain text passwords, and now the latest v3 encrypts all of the traffic with message integrity.
There are two types of community strings utilized in all versions of SNMP:
- Public: Community string is used for read-only access
- Private: Community string is used for both read and write access
The first step that attackers would look for is any identified network device on the internet and find if a public community string is enabled so that they can pull out all of the information specific to the network and draw a topology around it to create more focused attacks. These issues arise since most of the time IP-based Access Control Listing (ACL) is often not implemented or not used.
Kali Linux provides multiple tools to perform the SNMP enumeration; attackers can utilize SNMP walk to understand the complete information SNMP steps as shown in the following screenshot:
snmpwalk -c public ipaddress

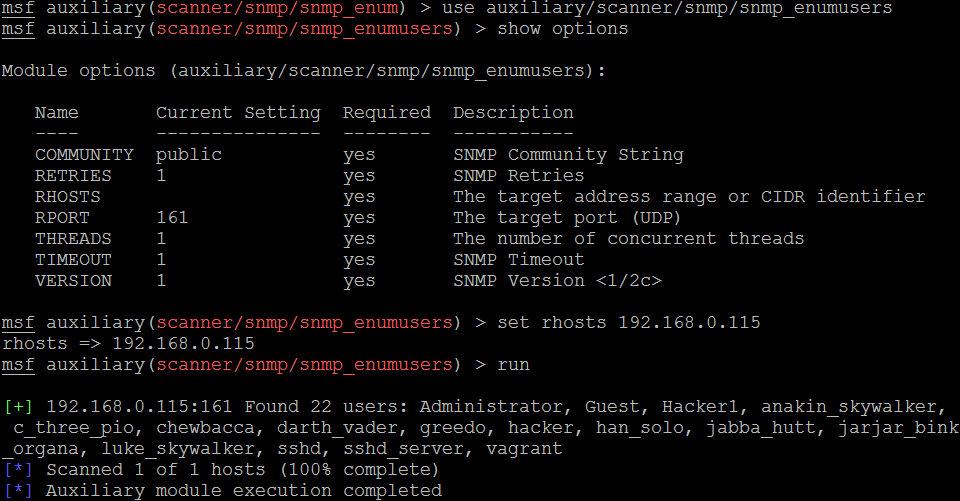
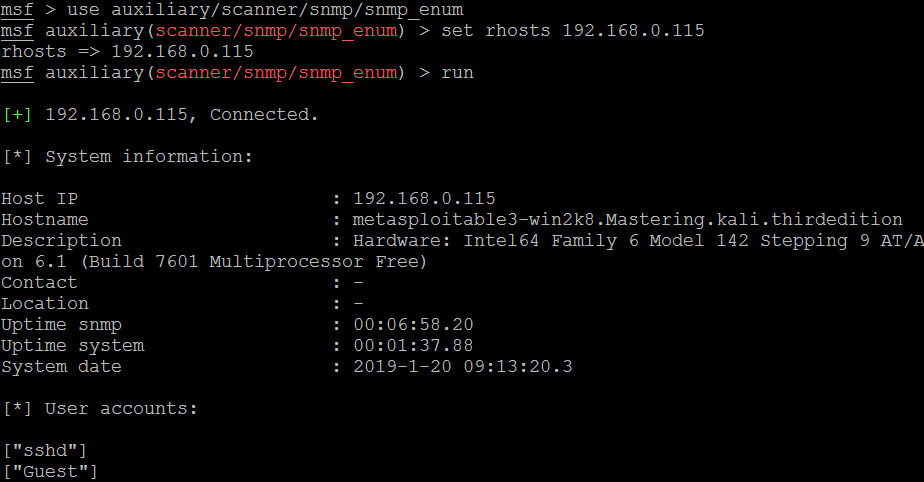
Attackers can also utilize Metasploit to perform SNMP enumeration, by using the /auxiliary/scanner/snmp/snmpenum module as shown in the following screenshot. Some systems have SNMP installed purely ignored by the system administrators:
Attackers will be able to extract all of the user accounts by using account enumeration modules within Metasploit, as shown in the following screenshot: