Traditionally, during Internal network scanning, it is very likely that attackers exploit the internal SMB sessions that are most commonly used. In the case of external exploitation, attackers can engage nmap to perform the enumeration, but this scenario is very rare. The following nmap command will enumerate all of the remote users on the Windows machine. This information normally creates lots of entry points much like brute forcing and password guessing attacks in later stages:
nmap --script smb-enum-users.nse -p445 <host>
Attackers may also utilize the Metasploit module, auxiliary/scanner/smb/smb_enumusers, to perform the activity. The following screenshot shows the successful enumeration of users on a Windows system running Metasploitable3:
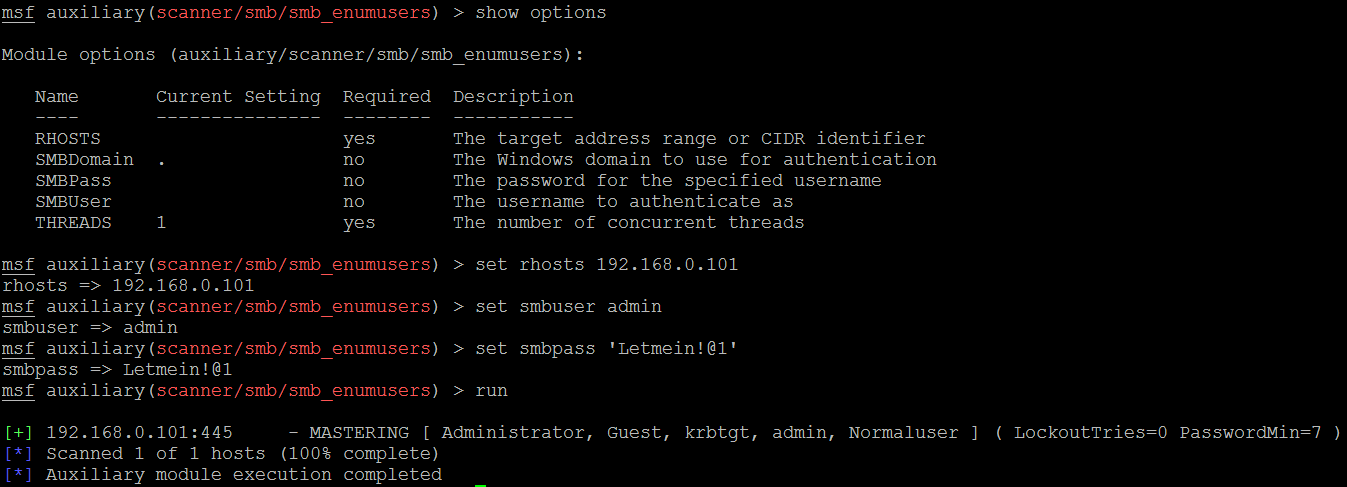
This can be achieved either by having a valid password guess to the system or by brute forcing the SMB logins.
