Open Vulnerability Assessment System (OpenVAS) is an open source vulnerability assessment scanner and also a vulnerability management tool often utilized by attackers to scan a wide range of networks, which includes around 47,000 vulnerabilities in its database; however, this can be considered a slow network vulnerability scanner compared with other commercial tools such as Nessus, Nexpose, and Qualys.
If OpenVAS is not already installed, make sure your Kali is up to date and install the latest OpenVAS by running the apt-get install openvas command. Once done, run the openvas-setup command to set up OpenVAS; to make sure the installation is OK, run the openvas-check-setup command and it will list the top 10 items that are required to run OpenVAS effectively. Once the installation is successful, testers should be able to see the following screenshot:
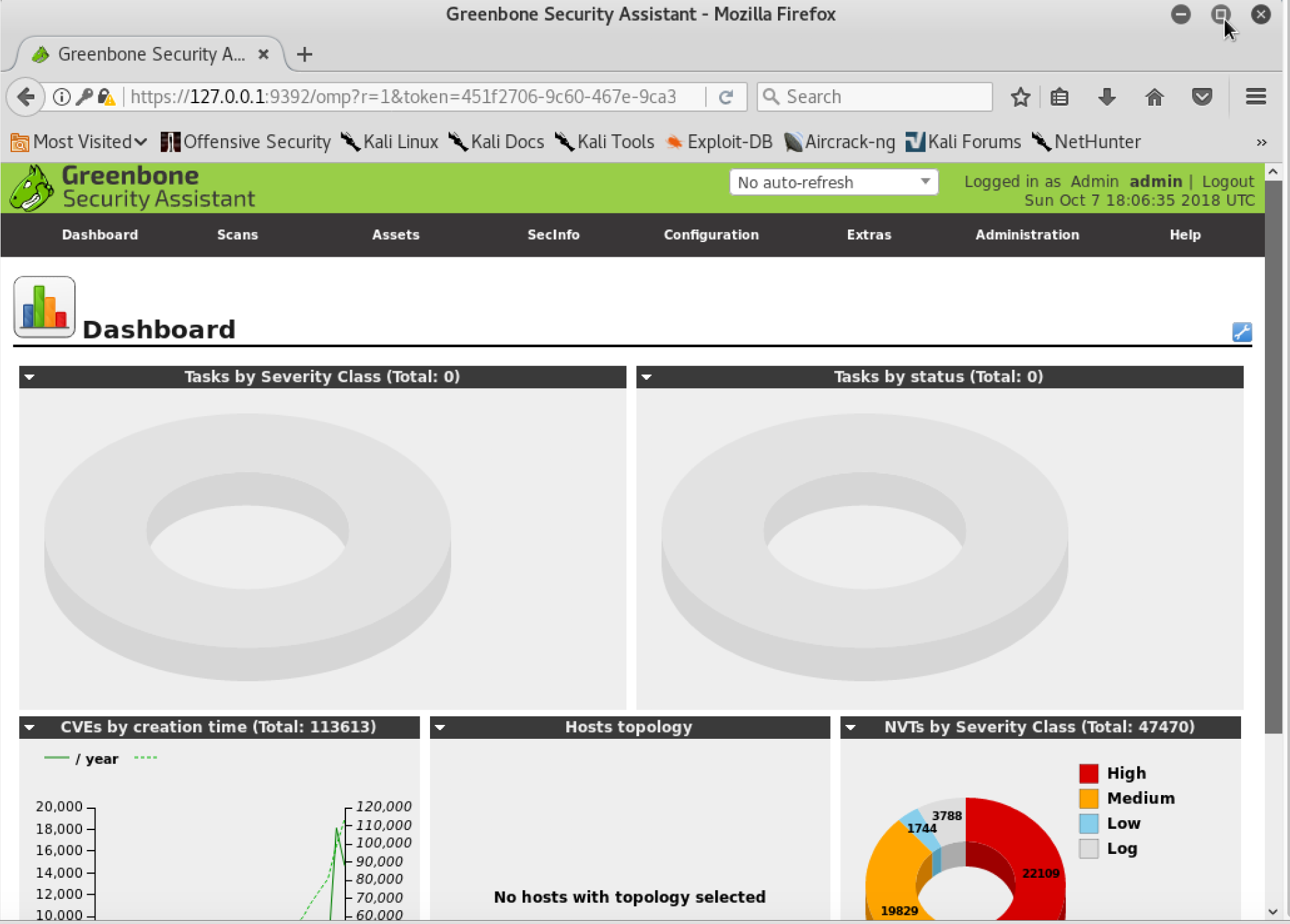
The next task is to create an admin user by running the openvasmd --user=admin --new-password=YourNewPassword1,--new-password=YourNewPassword1 command, and start up the OpenVAS scanner and OpenVAS manager services by running the openvas-start command from the prompt. Depending on bandwidth and computer resources, this could take a while. Once the installation and update is complete, penetration testers should be able to access the OpenVAS server on port 9392 with SSL (https://localhost:9392), as shown in the following screenshot:

The next step is to validate the user credentials by entering the username as admin and password as yournewpassword1, and testers should be able to log in without any issues and see the following screenshot. Attackers are now set to utilize OpenVAS by entering the target information and clicking Start Scan from the scanner portal: