Credentials, generally the username and password, give a person access to networks, computing systems, and data. An attacker can use this information indirectly (by logging on to the victim's Gmail account and sending emails to facilitate an attack against the victim's trusted connections), or directly against the user's account.
This attack is particularly relevant given the extensive reuse of credentials; users typically reuse passwords in multiple places.
Particularly prized are the credentials of a person with privileged access, such as a system administrator or a database administrator, which can give an attacker access to multiple accounts and data repositories.
The SET's credential harvesting attack uses a cloned site to collect credentials.
To launch this attack, select Website Attack Vectors from the main menu, then select Credential Harvester Attack Method, and then select Site Cloner. For this example, we will follow the menu selections to clone a website, such as Facebook, as shown in the following screenshot:

Again, the attacker's IP address must be sent to the intended target. When the target clicks on the link or enters the IP address, they will be presented with a cloned page that resembles the regular entry page for Facebook, as shown in the following screenshot, and they will be prompted to enter their usernames and passwords:

Once this is done, the users will be redirected to the regular Facebook site, where they will be logged in to their account.
In the background, their access credentials will be collected and forwarded to the attacker. They will see the following entry in the listener window:
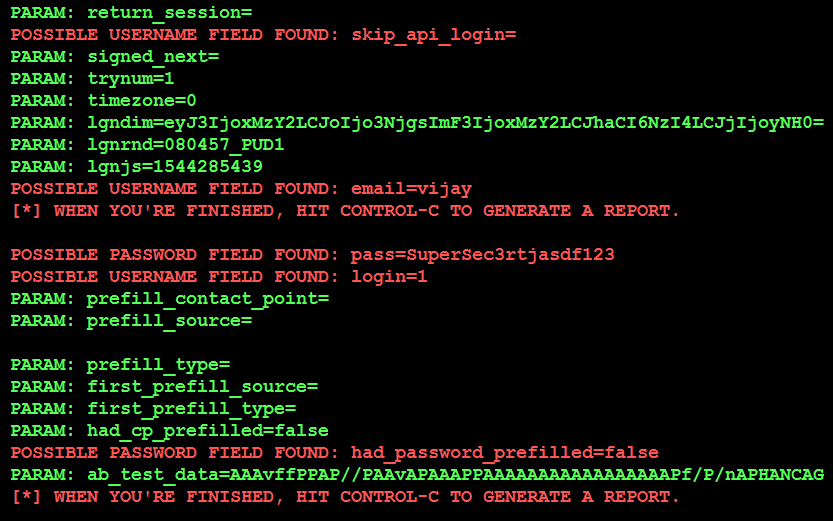
When the attacker has finished collecting credentials, entering Ctrl + C will generate two reports in the /SET/reports directory in XML and HTML formats.
Note that the address in the URL bar is not the valid address for Facebook; most users will recognize that something is wrong if they can see the address. A successful exploit requires the attacker to prepare the victim with a suitable pretext, or story, to make the victim accept the unusual URL. For example, send an email to a targeted group of non-technical managers to announce that a local Facebook site is now being hosted by IT to reduce delays in the email system.
The credential harvesting attack is an excellent tool for assessing the security of a corporate network. To be effective, the organization must first train all the employees on how to recognize and respond to a phishing attack. Approximately two weeks later, send a corporate-wide email that contains some obvious mistakes (incorrect name of the corporate CEO or an address block that contains the wrong address) and a link to a program that harvests credentials. Calculate the percentage of recipients who responded with their credentials, and then tailor the training program to reduce this percentage.
