Tabnabbing exploits a user's trust by loading a fake page in one of the open tabs of a browser. By impersonating a page of a site such as Gmail, Facebook, or any other site that posts data (usually usernames and passwords), a tabnabbing attack can collect a victim's credentials. SET invokes the credential harvester attack that we previously described.
To launch this attack, launch SET from a console prompt, and then select 1) Social-Engineering Attacks. In the next menu, select 2) Website Attack Vectors. The tabnabbing attack is launched by selecting 4) Tabnabbing Attack Method.
When the attack is launched, you will be prompted with three options to generate the fake websites that will be used to gather credentials. The attacker can allow SET to import a list of predefined web applications, clone a website (such as Gmail), or import their own website. For this example, we will select 2) Site Cloner.
This will prompt the attacker to enter the IP address that the server will POST to; this is usually the IP address of the attacker's system.
The attacker must then employ social engineering to force the victim to visit the IP address for the post back action (for example, URL shortening). The victim will receive a message that the site is loading (as the attack script loads the cloned site on a different tab in the browser, as shown in the following screenshot):
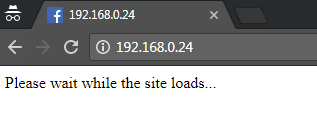
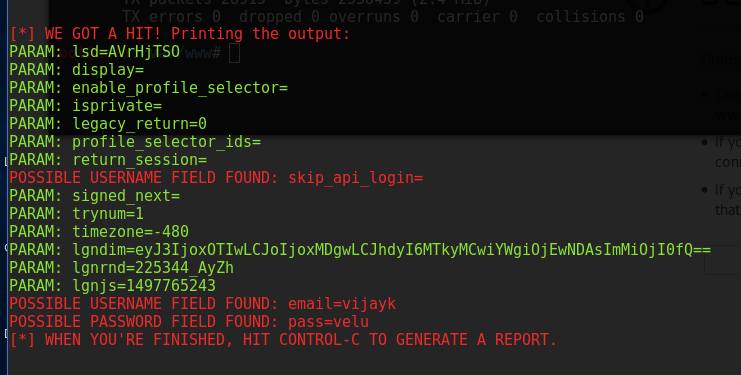
The target will then be presented with the fake page (with the false IP address still visible). If the users enter their usernames and passwords, the data will be posted to the listener on the attacker's system. As you can see in the following screenshot, it has captured the username and the password:
The Hail Mary attack for website attack vectors is multi-attack web method that allows the attacker to implement several different attacks at one time, should they choose to. By default, all attacks are disabled, and the attacker chooses the ones to run against the victim, as shown in the following screenshot:
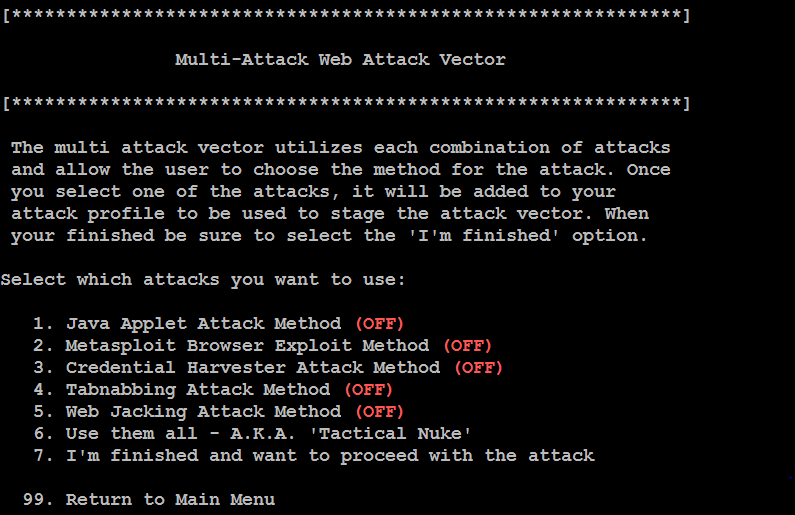
This is an effective option if you are unsure which attacks will be effective against a target organization; select one employee, determine the successful attack(s), and then reuse these against the other employees.
