Phishing is an email fraud attack carried out against a large number of victims, such as a list of known American internet users. The targets are generally not connected, and the email does not attempt to appeal to any specific individual.
Instead, it contains an item of general interest (for example, "Click here for bargain medication") and a malicious link or attachment. The attacker plays the odds that at least some people will click on the link attachment to initiate the attack.
On the other hand, spear phishing is a highly specific form of phishing attack; by crafting the email message in a particular way, the attacker hopes to attract the attention of a specific audience. For example, if the attacker knows that the sales department uses a particular application to manage its customer relationships, they may spoof an email pretending that it is from the application's vendor with a subject line of Emergency fix for <application> - Click link to download.
- Before launching the attack, ensure that sendmail is installed on Kali (apt-get install sendmail) and change the set_config file from SENDMAIL=OFF to SENDMAIL=ON.
- To launch the attack, select Social Engineering Attacks from the main SET menu, and then select Spear-Phishing Attack Vectors from the submenu. This will launch the start options for the attack, as shown in the following screenshot:

- Select 1 to perform a mass email attack; you will then be presented with a list of attack payloads, as shown in the following screenshot:

- The attacker can select any available payload, according to the attacker's knowledge of available targets gained during the reconnaissance phase. In this example, we will take an example of 7) Adobe Flash Player "Button" Remote Code Execution.
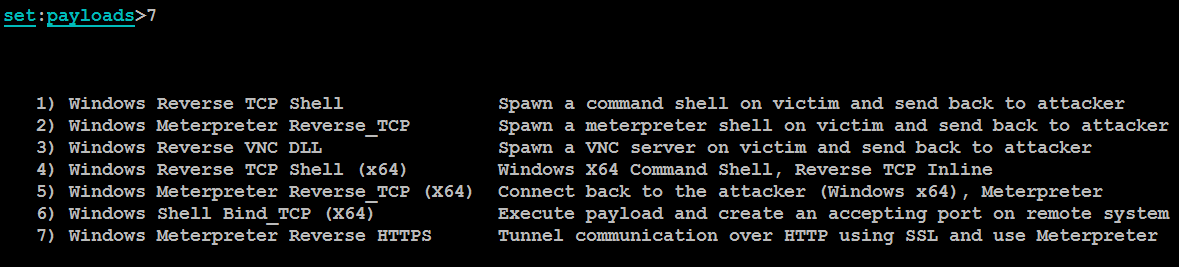
When you select 7, you will be prompted to select the payloads, as shown in the following screenshot. We have utilized Windows Meterpreter reverse shell HTTPS for this example:
Once the payload and exploit is ready from the SET console, attackers will get the confirmation shown in the following screenshot:

- Now, you will be able to rename the file by selecting option 2. Rename the file, I want to be cool.
- Once you rename the file, you will be provided with two options to select, either E-mail Attack Single Email Address or E-mail Attack Mass Mailer:

- Attackers can choose mass mailer or individually target a weaker victim, depending on their own choice. If we use a single email address, SET provides further templates that can be utilized by the attackers, as shown in the following screenshot:

- After you select the phishing template, you will be offered the option of using your own Gmail account to launch the attack (1) or using your own server or open relay (2). If you use a Gmail account, it is likely that the attack will fail; Gmail inspects outgoing emails for malicious files and is very effective at identifying payloads produced by SET and the Metasploit framework. If you have to send a payload using Gmail, use Veil-Evasion to encode it first.
It is recommended that you use the sendmail option to send executable files; it allows you to spoof the source of the email to make it appear as though it originated from a trusted source.
To ensure that an email is effective, the attacker should take care of the following points:
- The content should provide a carrot (the new server will be faster, have improved antivirus) and a stick (changes you will have to make before you can access your email). Most people respond to immediate calls for action, particularly when it affects them.
- In the sample given previously, the attached document is titled template.doc.
- In a real-world scenario, this would be changed to instructions.doc.
- Ensure that your spelling and grammar are correct, and the tone of the message matches the content.
- The title of the individual sending the email should match the content.
- If the target organization is small, you may have to spoof the name of a real individual and send the email to a small group that does not normally interact with that person.
- Include a phone number; it makes the email look more official, and there are various ways to use commercial voice over IP solutions to obtain a short-term phone number with a local area code.
Once the attack email is sent to the target, successful activation (the recipient launches the executable) will create a reverse Meterpreter tunnel to the attacker's system. The attacker will then be able to control the compromised system.
