The first step in conducting a wireless attack is to conduct reconnaissance—this identifies the exact target access point and highlights the other wireless networks that could impact testing.
If you are using a USB-connected wireless card to connect to a Kali virtual machine, make sure that the USB connection has been disconnected from the host operating system and that it is attached to the virtual machine by clicking on the USB connection icon, which is indicated by an arrow in the following screenshot:

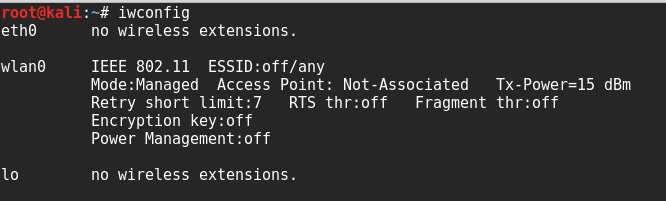
Next, determine which wireless interfaces are available by running iwconfig from the command line, as shown in the following screenshot:
For certain attacks, you may wish to increase the power output of the adapter. This is especially useful if you are collocated with a legitimate wireless access point, and you want the targets to connect to a false access point under your control rather than the legitimate access point. These false, or rogue, access points allow an attacker to intercept data and to view or alter it as needed to support an attack. Attackers will frequently copy or clone a legitimate wireless site and then increase its transmission power compared to the legitimate site as a means of attracting victims. To increase power, the following command is used:
kali@linux:~# iwconfig wlan0 txpower 30
Many attacks will be conducted using aircrack-ng and its related tools. To start, we need to be able to intercept or monitor wireless transmissions; therefore, we need to set the Kali communication interface with wireless capabilities to monitor mode using the airmon-ng command:
kali@linux:~# airmon-ng start wlan0
The execution of the previous command is shown in the following screenshot:
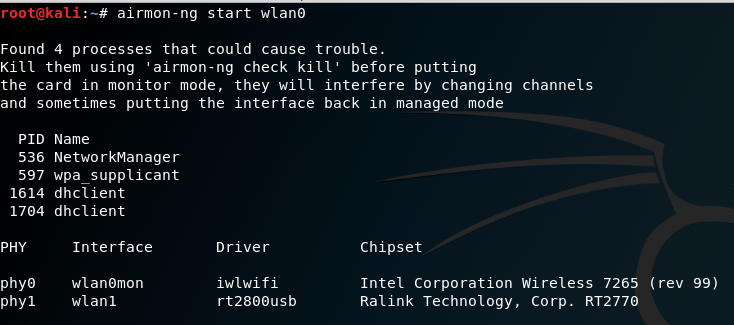
Note that the description that is returned indicates that there are some processes that could cause trouble. The most effective way to deal with these processes is to use a comprehensive kill command, as follows:
root@kali:~# airmon-ng check kill
To view the local wireless environment, use the following command:
root@kali:~# airodump-ng wlan0mon
The previous command lists all the identified networks that can be found within the range of the wireless adapter at that particular point of time. It provides the Basic Service Set Identifier (BSSID) of the wireless nodes on the network, as identified by the MAC addresses, an indication of the relative output power, information on data packets that have been sent, bandwidth information including the channel used and data, information on the encryption used, and the Extended Service Set Identifier (ESSID) that provides the name of the wireless network. This information is shown in the following screenshot; non-essential ESSIDs have been blurred out:
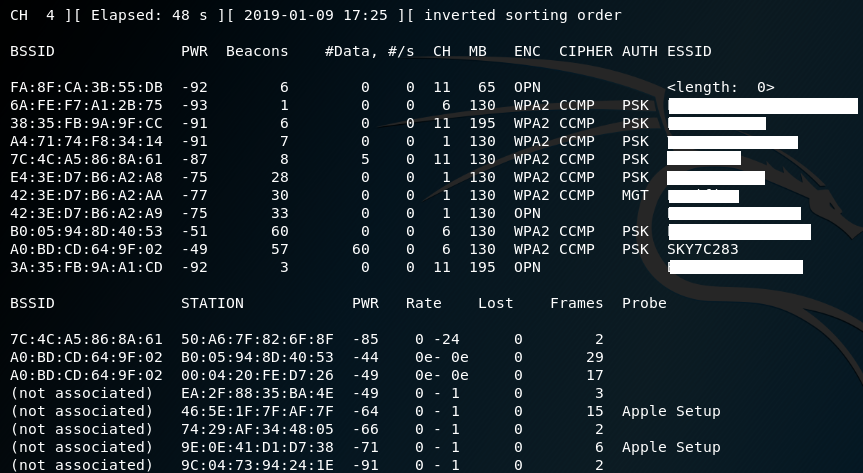
The airodump command cycles through the available wireless channels and identifies the following:
- The BSSID, which is the unique MAC address that identifies a wireless access point or router.
- The PWR, or power, of each network. Although airodump-ng incorrectly shows the power as being negative, this is a reporting artifact. To obtain the proper positive values, access a Terminal and run airdriver-ng unload 36, and then run airdriver-ng load 35.
- CH shows the channel that is being used to broadcast.
- ENC shows the encryption in use—it is OPN, or open, for no encryption being used, or WEP or WPA/WPA2 if encryption is being used. CIPHER and AUTH provide additional encryption information.
- The ESSID is the common name of the wireless network, and is made up of the access points that share the same SSID or name.
In the lower section of the Terminal window, you will see the stations attempting to connect, or that are connected to the wireless network.
Before we can interact with any of these (potential) target networks, we have to confirm that our wireless adapter is capable of packet injection. To do this, run the following command from a Terminal shell prompt:
root@kali:~# aireplay-ng -9 wlan0mon
The execution of the previous command is shown in the following screenshot:
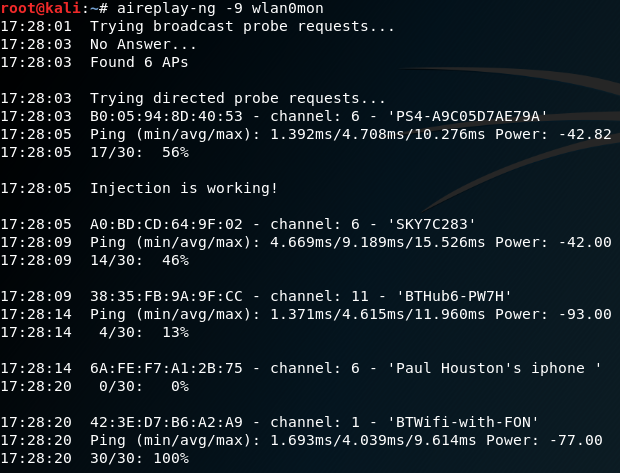
Here, -9 indicates an injection test.
