WPA enterprise is a technology that's utilized in widespread corporations. It does not use a single WPA-PSK, which most of the users use to connect to the wireless network. To maintain the governance and the flexibility of the domain accounts, corporates utilize the implementation of WPA enterprise.
A typical approach to compromising an enterprise wireless would be first to enumerate the wireless devices and finally attack the connected clients to find out the authentication details. This consists of spoofing a target network and also providing a good signal to the client. Then, the original valid access point later leads into a MiTM attack between the Access Point (AP) and the clients connecting to the AP. To simulate an enterprise WPA attack, attackers must be physically near to the target when they have a range of access points. Attackers can also sniff the traffic using Wireshark to identify the wireless network traffic handshake.
In this section, we will explore two different tools that attackers would typically utilize to perform different types of attack on WPA/WPA2 Enterprise.
Wifite is an automatic wireless attack tool that's preinstalled in Kali Linux, and is written in Python. The latest version of Wifite is V2, which has previously known aircrack-ng bugs.
This tool utilizes the following attacks to extract the password of a wireless access point:
- WPS: The Offline Pixie Dust attack and the Online Brute-Force PIN attack
- WPA: The WPA Handshake Capture and offline crack, and the PMKID Hash Capture and offline crack
- WEP: All of the aforementioned attacks, including chop-chop, fragmentation, and aireplay injection
Now we are all set to start Wifite so that we can perform a WPA four-way handshake capture and then perform an auto password cracking attack. This tool can be directly launched from the Terminal by typing wifite. Attackers should be presented with the interactive mode so that they can select an interface, as shown in the following screenshot:
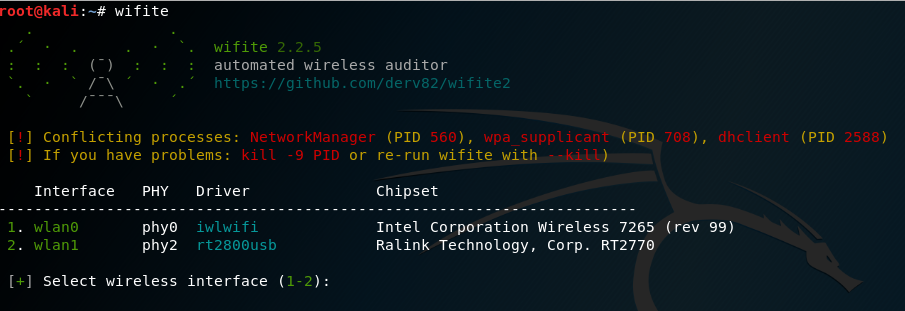
Once the interface has been selected, it should automatically enable the adapter in monitor mode and start to list all the Wi-Fi ESSID, channel, encryption, and power, regardless of whether it is WPS or not, as well as the number of clients connected to a particular ESSID. Once the target ESSID is selected, attackers should press Ctrl + C from the keyboard, which should launch the attack.
By default, four attack types would be launched automatically. These are WPS Pixie Dust, WPS PIN, PMKID, and WPA Handshake. Attackers can choose to ignore the first three attacks if they aren't relevant by pressing Ctrl + C. While the handshake is being captured, attackers can see which clients have been discovered that are connected to the station. Once the handshake has been captured, by default, the copy of the handshake be will stored in the current folder, hs/handshake_ESSID_MAC.cap.
Once the handshake has been successfully captured, it will be analysed using tshark, Pyrit, cowpatty, and aircrack-ng, which will validate the handshake for ESSID and BSSID.
Wifite is programmed to automatically use a wordlist to run with aircrack-ng. The custom wordlist can also be passed directly while launching Wifite by typing wifite -wpa -dict /path/customwordlist. A successful handshake cracking would typically return the password for the wireless access point (router), as shown in the following screenshot:
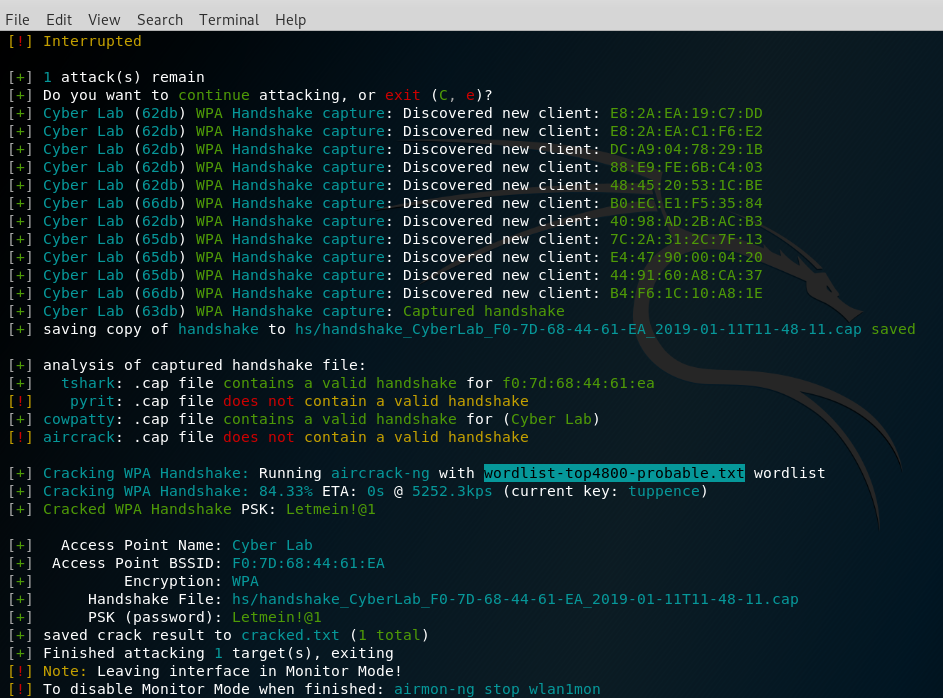
All the passwords will be saved in the cracked.txt file in the current folder from where Wifite was run from. The tool has an anonymous feature that can change MAC to a random address before attacking, and then change it back when attacks are complete.
Now, we will take a deep dive into Fluxion, which is an automatic wireless attack tool that's used to evade wireless and create evil access points, which are written in a mix of Bash and Python.
The latest version of Fluxion can be downloaded by running git clone https://github.com/wi-fi-analyzer/fluxion.git. This tool is based on linset script (https://github.com/vk496/linset) of evil twin attack Bash scripts.
Attackers can utilize this tool to perform the following type of attacks:
- Scans the wireless networks
- Utilizes packet capture to find out the handshake (provided a valid handshake has been done)
- Provides a web interface
- Creates a fake AP within seconds to imitate the original AP
- It is capable of spawning MDK3 (a tool to inject packets into the wireless networks)
- Automatically launches a fake DNS server to capture all the DNS requests and redirects them to the hosted machine
- A fake web page is created as a portal to the key in the password
- Automatic termination of the session once the key is found
Once Fluxion has been cloned, make sure that you run the install.sh, which is in the install folder, to install all the dependencies and libraries that are required for Fluxion to run without any issues. The successful installation of the Fluxion attacker is shown in the following screenshot:
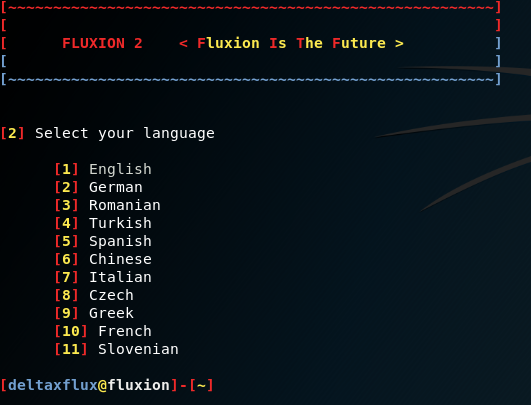
Fluxion allows attackers to select from eleven different languages; once a language has been selected, you will be given an option to select from all of the wireless LAN interfaces that are available on your laptop/PC. Upon selecting an interface, Fluxion provides you with an option to select a specific channel or all channels to scan the networks; it is the attacker's choice to select the channel based on the target Wi-Fi. Once the scanning has been performed and identified the list of the wireless APs, press Ctrl + C to move to the next screen, as shown in the following screenshot:

Once the entire list of wireless APs are available, attackers are now able to proceed with any selected network. For example, from the preceding screenshot, attackers have selected 16 (Cyber Lab) as the target, which is running on encryption WPA2, and have moved on to the next stage of mimicking the Wi-Fi, just like copying their own infrastructure and setting it up without much difference. Fluxion allows us to select two options, as shown in the following screenshot:
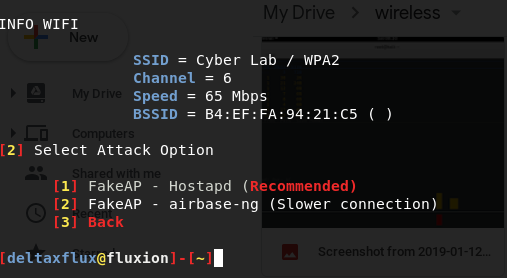
As you can see, these two options are as follows:
- Set up a FakeAP through Hostapd
- Set up a FakeAP using airbase-ng
A FakeAP attack is an easy attack method that's used to host a wireless AP with the same name and reduce signal strength using Websploit, thereby forcing the clients to our AP via the FakeAP. The testers will be presented with the handshake check, along with two options: to select either pyrit or aircrack-ng.
Fluxion is written in such a way that it will automatically utilize MDK3 to deauthenticate all the clients connected to the AP, as shown in the following screenshot:

Simultaneously, Wi-Fi handshake data capture is captured through another window, as shown in the following screenshot:
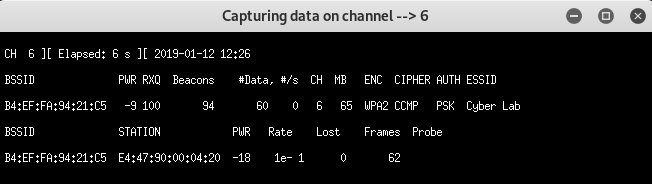
Once the user has re-connected to the Cyber Lab, during re-connection, Fluxion captures the handshake. This enables attackers to move to the next step, which is to check the handshake, as shown in the following screenshot:

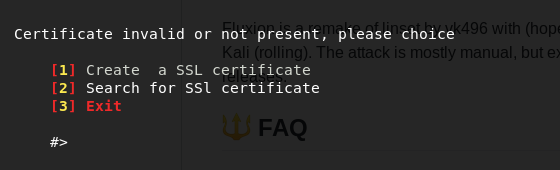
If the handshake resulted in corruption, press 2 go back and launch the same attack. However, it is very rare that attackers aren't able to capture the handshake. If the handshake is valid, then we move on and create our SSL certificate, as shown in the following screenshot. Testers can choose to generate a new SSL certificate or use the existing one:
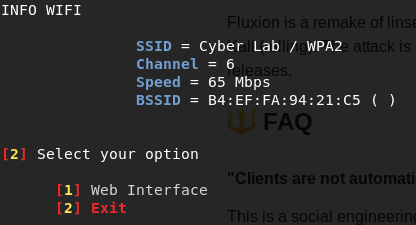
Once the SSL certificate has been generated, we have an web interface option to select, as shown in the following screenshot. Fluxion provides the option for you to select a language for the web interface that will force the victim who gets connected to our hosted AP to log an adaptive portal:
Now that we are up with the evil twin, with our new access point, testers can validate, as shown in the following screenshot:

When attackers perform the FakeAP attack, they are able to see the following screens running in a completely automated manner. Here, a DHCP server, fake DNS server, and a fake website are being hosted on the same system running while running Fluxion in Kali Linux:
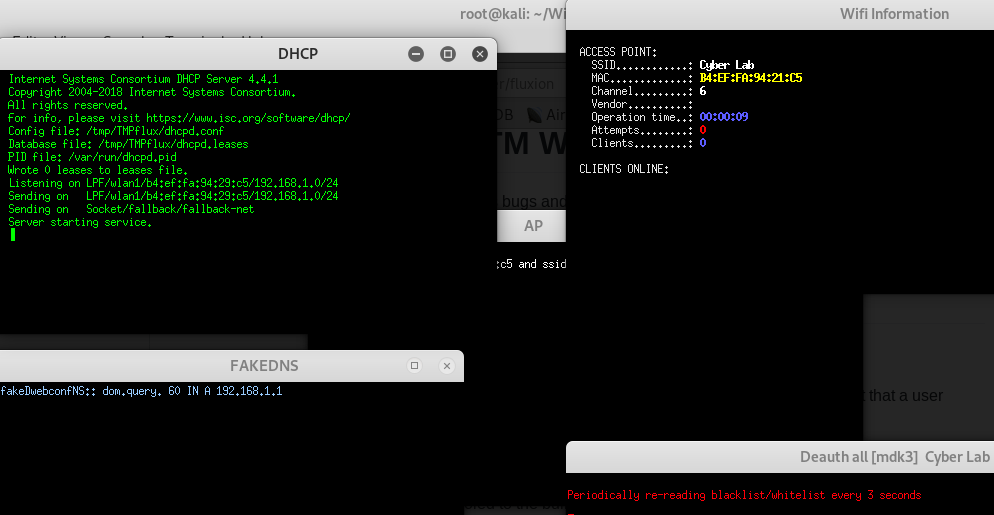
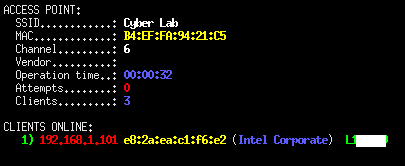
Attackers can confirm whether there are any victims connected to their fake AP in the Wifi Information tab. This will display the connected hostname, along with the fake IP address and original MAC address under the Clients Online section, as shown in the following screenshot:
On the other hand, victims who are connected to the fake AP will be presented with an additional mode to log in so that they can access the internet. For example, the following screenshot depicts the message a victim will receive on Windows:

Once the victim clicks on the additional login information or tries to access any URL, they will redirected to a login page that was set up during our web interface selection, as shown in the following screenshot:
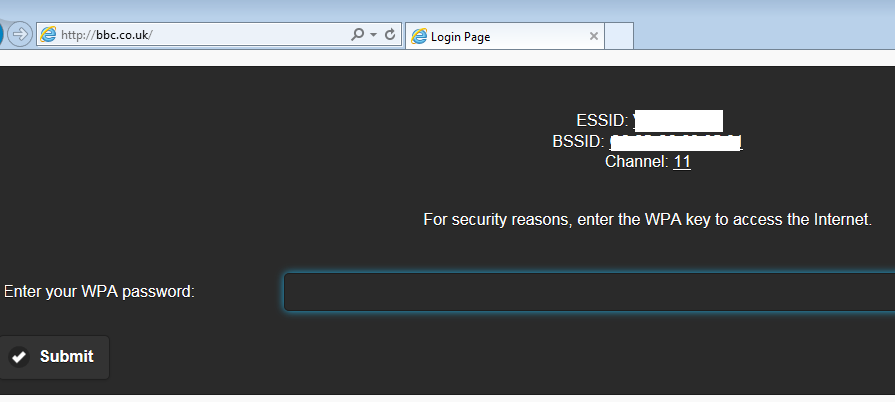
If the victim enters the right WPA password, this will be used to crack the password from the handshake that was captured during the initial stages. A successful password crack will be displayed in the Wifi Information tab, and the handshake and cracked password will be stored in the root folder by default:

