There is no substitute for the human mind. In this section, we will focus more on how a web application looks from the perspective of an attacker. The following diagram shows a mind map of a web application hack:
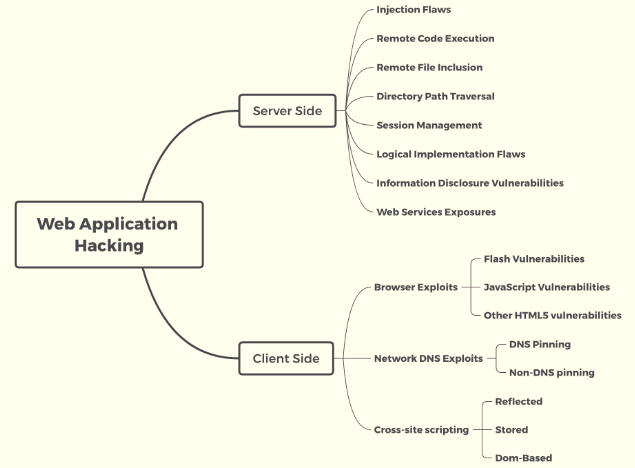
The mind map is split into two categories: attackers can attack either server-side vulnerabilities or client-side vulnerabilities. These vulnerabilities normally occur for one of the following reasons:
- Use of old or unpatched technology
- Poor security configuration for the latest technology
- Coding without security in mind
- The human factor: a lack of skilled staff
On the server side, attackers would typically perform the following list of attacks:
- Web application firewall evasion
- Injection attacks
- Remote code execution
- Remote file inclusion/local file inclusion
- Directory path traversal
- Exploiting session management
- Exploiting the logic of the system or application
- Identifying any relevant information that can help them to perform more dedicated attacks
Client-side attacks are focused on exploiting the vulnerabilities that exist on the client side, rather that the server side. These could include browsers, applications (thick/thin clients), or network, as follows:
- Flash vulnerabilities: Flash Player has 1,068 known vulnerabilities (see https://www.cvedetails.com/vulnerability-list/vendor_id-53/product_id-6761/Adobe-Flash-Player.html) as of December 8 2018.
- JavaScript and Java vulnerabilities.
- DNS pinning/rebinding vulnerabilities: DNS rebinding is a DNS-based attack on the code embedded in web pages. Normally, requests from code embedded in web pages (JavaScript, Java, and Flash) are bound to the website they originate from (a same-origin policy). A DNS rebinding attack can be used to improve the ability of JavaScript-based malware to penetrate private networks and subvert the browser's same-origin policy.
- Non-DNS pinning vulnerabilities.
- Client script injection vulnerabilities/cross-site scripting: reflected, persistent (stored), and DOM-based.
With these vulnerabilities in mind, attackers are equipped with a full list of exploitation kits and are ready to start reconnaissance.
