NAC works on a basic form of the 802.1X IEEE standard. The majority of corporations implement NAC to protect network nodes such as switches, routers, firewalls, servers, and, more importantly, endpoints. A decent NAC implies the controls that are put in place to prevent the intrusion by policies and also define who can access what. In this section, we will take a deep dive into different types of NAC that attackers or penetration testers encounter during an RTE or penetration test.
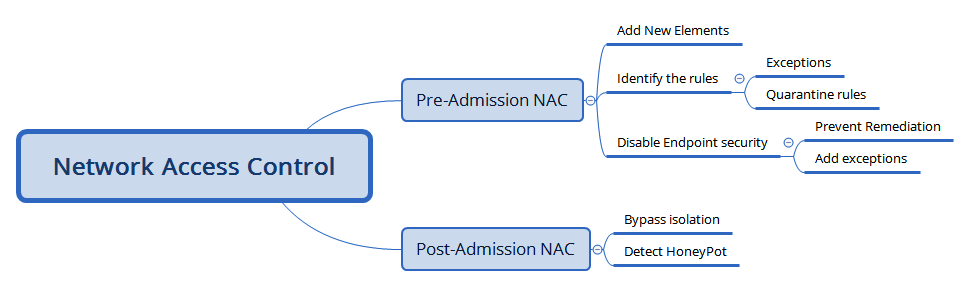
There are no specific common criteria or standardization for NAC; it depends on the vendor and the way it is implemented. For example, Cisco provides Cisco Network Admission Control and Microsoft provides Microsoft Network Access Protection. The primary purpose of NAC is to control the devices/elements, which can be connected and then made sure they are tested for compliance. NAC protections can be subdivided into two different categories:
- Pre-admission NAC
- Post-admission NAC
The following screenshot provides a mind map activities that can be performed by an attacker during an internal penetration test or post exploitation phase as per the kill chain methodology: