Route mapping was originally used as a diagnostic tool that allows you to view the route that an IP packet follows from one host to the next. Using the Time To Live (TTL) field in an IP packet, each hop from one point to the next elicits an ICMPTIME_EXCEEDED message from the receiving router, decrementing the value in the TTL field by 1. The packets count the number of hops and the route taken.
From an attacker's or penetration tester's perspective, the traceroute data yields the following important data:
- The exact path between the attacker and the target
- Hints pertaining to the network's external topology
- Identification of accessing control devices (firewalls and packet-filtering routers) that may be filtering attack traffic
- If the network is misconfigured, it may be possible to identify internal addressing
In Kali, traceroute is a command-line program that uses ICMP packets to map the route; in Windows, the program is tracert.
If you launch traceroute from Kali, it is likely that you will see most hops filtered (data is shown as * * *). For example, traceroute from the author's present location to demo.cyberhia.com would yield the following:

However, if the same request was run using tracert from the Windows command line, we would see the following:
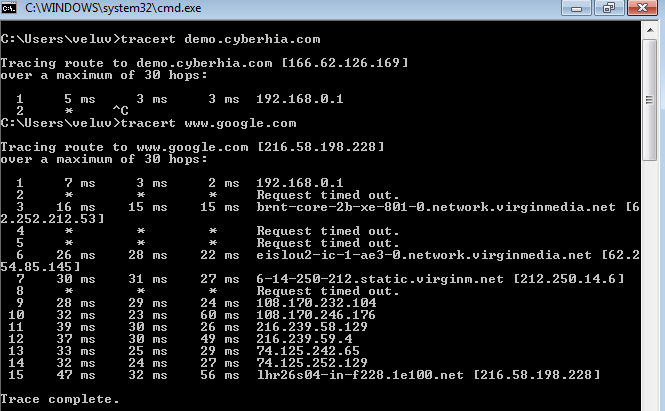
Not only do we get the complete path, but we can also see that www.google.com is resolving to a slightly different IP address, indicating that load balancers are in effect (you can confirm this using Kali's lbd script; however, this activity may be logged by the target site).
The reason for the different path data is that, by default, traceroute uses UDP datagrams while Windows tracert uses ICMP echo request (ICMP type 8). Therefore, when completing traceroute using Kali tools, it is important to use multiple protocols in order to obtain the most complete path and to bypass packet-filtering devices.
Kali provides the following tools for completing route traces:
|
Application |
Description |
|
hping3 |
This is a TCP/IP packet assembler and analyzer. This supports TCP, UDP, ICMP, and raw-IP and uses a ping-like interface. |
|
intrace |
This enables users to enumerate IP hops by exploiting existing TCP connections, both initiated from the local system or network or from local hosts. This makes it very useful for bypassing external filters such as firewalls. intrace is a replacement for the less reliable 0trace program. |
|
trace6 |
This is a traceroute program that uses ICMP6. |
hping3 is one of the most useful tools due to the control it gives over packet type, source packet, and destination packet. For example, Google does not allow ping requests. However, it is possible to ping the server if you send the packet as a TCP SYN request.
In the following example, the tester attempts to ping Google from the command line. The returned data identifies that demo.cyberhia.com is an unknown host; Google is clearly blocking ICMP-based ping commands. However, the next command invokes hping3, instructing it to do the following:
- Send a ping-like command to Google using TCP with the SYN flag set (-S)
- Direct the packet to port 80; legitimate requests of this type are rarely blocked (- p 80)
- Set a count of sending three packets to the target (-c 3)
To execute the previous steps, use the commands shown in the following screenshot:
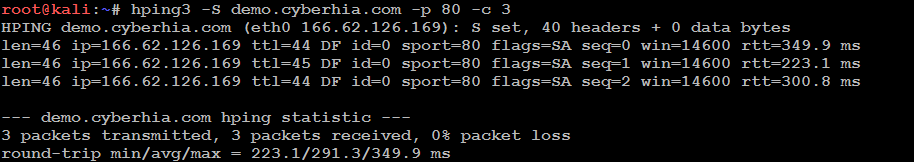
The hping3 command successfully identifies that the target is online and provides some basic routing information.
