Attackers normally start the network debugging using traceroute utility, which attempts to map all of the hosts on a route to a specific destination host or system. Once the target is reached, as the TTL (Time to Live) field will be 0, the target will discard the datagram and generate an ICMP time exceeded packet back to its originator. A regular traceroute will be as follows:
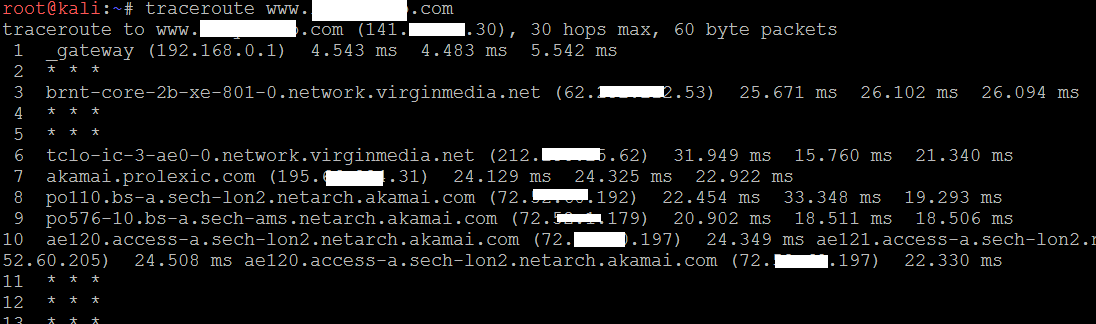
As you see from the preceding example, we cannot go beyond a particular IP, which most probably means that there is a packet filtering device at hop 3. Attackers would dig a little bit deeper to understand what is deployed on that IP.
Deploying the default UDP datagram option, it will increase the port number at every time it sends an UDP datagram. Hence, attackers will start pointing a port number to reach the final target destination.
