Penetration testers can utilize fragroute and wafw00f to identify whether there are any detection or prevention mechanisms put in place such as Intrusion Detection System (IDS) or an Intrusion Prevention system (IPS) or a Web application Firewall (WAF).
fragroute is a default tool in Kali Linux that can perform fragmentation of packets. The network packets will allow attackers to intercept, modify, and rewrite the egress traffic for a specific target. This tool comes in very handy on a highly secured remote environment.
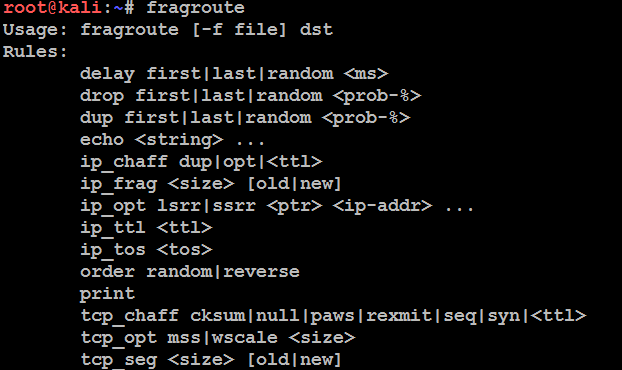
The following screenshot provides the list of options that are available in fragroute to determine any network IDs in place:
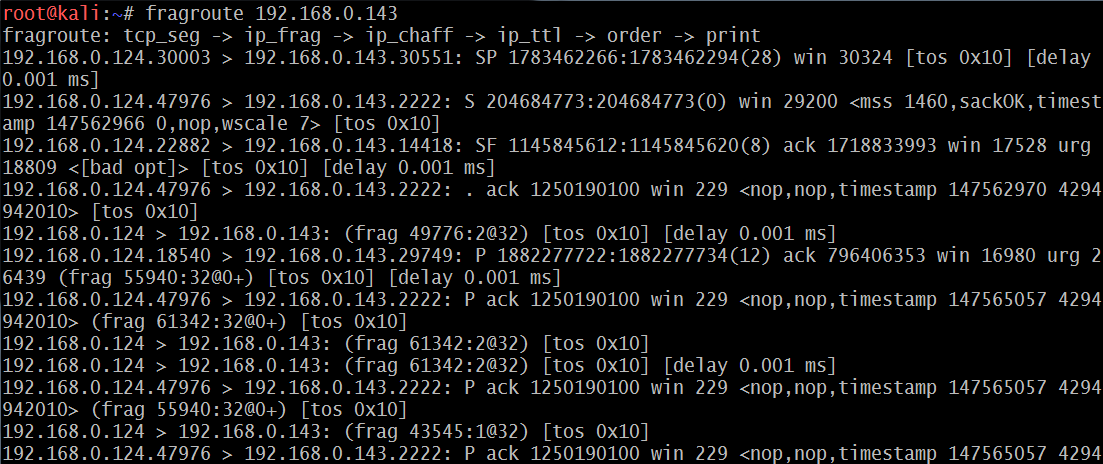
Attackers can also write their own custom configuration to perform fragmentation attacks to delay, duplicate, drop, fragment, overlap, reorder, source-route, and segment. A sample custom configuration would look like the following screenshot:

fragroute on target is as simple as running fragroute target.com and if there are any connections happening to the target.com address, then the attackers will be able to see the traffic that is being sent to the target.com. Note that only when you have a route to the target will you be able to fragment the route. The following screenshot shows that the IP segments are fragmented as per the custom configuration file:
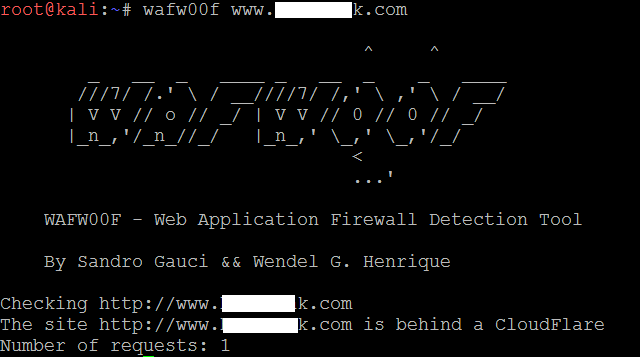
Another tool that attackers utilize during the active reconnaissance is wafw00f; this tool is preinstalled in the latest version of Kali Linux. It is used to identify and fingerprint the Web Application Firewall (WAF) products. It also provides a list of well-known WAFs. It can be listed down by adding the -l switch to the command (for example, wafw00f -l)
The following screenshot provides the exact WAF running behind a web application: