8
Toward New Intelligent Architectures for the Internet of Vehicles
Léo MENDIBOURE1, Mohamed Aymen CHALOUF2 and Francine KRIEF3
1 LaBRI, Bordeaux, France
2 IRISA, Rennes, France
3 ENSEIRB-MATMECA, Bordeaux, France
8.1. Introduction
The reference architecture of Cooperative-Intelligent Transport Systems (C-ITS) (ETSI 2010) was defined by the joint work of various standardization organizations: IEEE, ISO, ETSI, etc. Structured along three main axes (management, control, security), this architecture must enable the deployment of a large-scale vehicular communication system. As proven by Kaiwartya et al. (2016), in the current state it has various limitations: capacity to process a significant data volume, interoperability between various networks, guaranteed quality of service (QoS), guaranteed security and respect of private life, etc. This is why vehicular networks evolved toward a new paradigm: the Internet of Vehicles (IoV).
Relying on the principles of the Internet of Things (IoT), IoV must enable addressing the limitations of Vehicular Ad hoc NETworks, also known as “VANET”. For this purpose, IoV relies on the development of new types of communication: vehicle to pedestrian (V2P), vehicle to object (V2O), etc. This must make possible the improvement of road safety services, the development of global traffic management services as well as the design of new entertainment services (multimedia, advertising, etc.).
The communication architecture that should enable the ascent of the IoV has not yet been normalized. This architecture must meet many criteria: safety and protection of private life, simplified management, optimized dissemination of information, scaling, etc. (Kaiwartya et al. 2016). Various architectures aiming to make possible these various improvements, based on the reference C-ITS architecture, were proposed in the literature. These architectures rely on the integration of various technologies: network function virtualization (NFV), software-defined network (SDN), Blockchain, edge computing (EC), etc.
All these architectures share a common point: the idea of integrating artificial intelligence (AI) techniques in the control plane. Indeed, whatever the chosen approach (NFV, SDN, EC, etc.), knowledge sharing and intelligent decision making are presented as essential points. The use of AI, in addition to other technologies, could bring many improvements to the control plane: dynamic routing, prediction of vehicle movement and congestion control.
However, the set of architectures described in the literature focuses only on the improvement of the control plane. But intelligent decision making could also reinforce security plane and private life protection (intrusion detection, secure routing, etc.) as well as the architecture management plane (load balancing, allocation of virtual resources, etc.). Moreover, as suggested in Mendiboure et al. (2019a), the addition of a fourth plane, the knowledge plane (KP), in the service of all the other planes (management, control and security) could have many advantages.
The objective of this chapter is to describe and compare the work aiming to improve the operation of vehicular networks by AI integration in the control plane. Then we define an architecture enabling this work and offering intelligent services, not only to the control plane, but also to the management and security planes. Using existing work, we present for each of these planes the advantages of using AI techniques and a list of challenges to be addressed is provided.
First of all, section 8.2 presents the context: the principle of the IoV and also its applications. Then section 8.3 presents the various works integrating AI techniques in the vehicular communication architecture. This same section explains the interest of the definition of a new architecture for IoV. As a continuation, section 8.4 describes in detail the proposed architecture, its main components, as well as its advantages. Finally, section 8.5 presents the stakes of the proposed architecture and section 8.6 presents the conclusion and the perspectives concerning the integration of AI techniques in the vehicular communication architecture.
8.2. Internet of Vehicles
This section presents the characteristics of the IoV as well as the applications made possible by this new vehicular architecture.
8.2.1. Positioning
As indicated in Kaiwartya et al. (2016), the development of the IoV has three main objectives:
- – address the limitations of vehicular ad hoc networks, namely:
- - lack of interoperability: the current vehicular architecture does not enable the interconnection of heterogeneous networks (Wi-Fi, cellular, Li-Fi, etc.), thus preventing the deployment of global and reliable intelligent transportation services;
- - absence of Internet connectivity: the current vehicular architecture does not guarantee Internet connectivity to vehicles. Consequently, the development of commercial services (advertising, entertainment, etc.) or of efficient traffic management services is impossible;
- - limited intelligent decision making: due to limited Internet connectivity and reduced computing/storage capacities of vehicles, the processing of significant data volumes is impossible;
- - lack of exchanges: vehicular ad hoc networks being designed to enable vehicle interconnection, the integration of new types of connected objects (cameras, telephones, etc.) is not an option, although it could have many benefits (detection of pedestrians and cyclists, creation of cooperative map, etc.);
- – address the increase in the number of traffic accidents: intelligent transport systems aim first of all to provide and improve road safety. Since the number of traffic accidents and fatalities is constantly increasing (Kaiwartya et al. 2016), the development of road safety services is essential and must rely on an architecture enabling the development of global services;
- – provide new opportunities: integration of new objects in the vehicular networks, interoperability between various networks and guaranteed Internet connectivity could enable the generation of significant data volumes, the provision of new services and consequently attracting new investors: service providers, car manufacturers, etc.
8.2.2. Characteristics

The development of the IoV and the improvement of vehicular communication network performances rely on two important concepts:
- – integration of new types of objects in the vehicular networks through new types of communication, which is referred to as vehicle to everything (V2X):
- - vehicle to pedestrian (V2P);
- - vehicle to object (V2O);
- - vehicle to grid (V2G);
- - vehicle to cloud (V2C);
- – integration of new technologies in the C-ITS architecture (Figure 8.2), each of them making it possible to overcome certain limitations of vehicular ad hoc networks:
- - NFV: provides virtualization of network functions and services leading to cost reduction (standard material), more rapid deployment and simplified scalability (flexibility);
- - SDN: a technique for uncoupling the control plane and the data plane, enabling network programmability and an overall view, and high adaptation to the context (dynamicity);
- - EC: based on the deployment of computing and storage capacities on the edge of the network, extension of cloud capacities, which should limit the latency times (better user experience) and unload the network core (scalability);
- - blockchain: a distributed technology enabling transparent, secure and unfalsifiable information storage and exchange, which facilitates the development of efficient, robust and scalable security solutions;
- - AI: involves techniques that should enable the improvement of the existing architecture, and also newly integrated technologies (EC, NFV, SDN) through decision-aiding and process automation methods.
8.2.3. Main applications
Addressing the limits of vehicular ad hoc networks, integrating new types of objects and enabling Internet connectivity, the IoV facilitates many new applications, which can be classified in various categories (Mendiboure et al. 2019b):
- – transport management: real-time traffic management, parking place reservation, electric vehicle charging points, etc.;
- – road safety: intersection management, cooperative avoidance of collisions, detection of obstacles, etc.;
- – vehicle management: personal assistant, remote maintenance system, etc.;
- – driver assistance: advanced driver assistance systems (ADAS), parking assistance, creation of cooperative maps, etc.;
- – connected health: tiredness detection, user comfort, medical assistance, etc.;
- – new transportation modes: platooning, creation of connected vehicle convoys or car sharing, new modes of transportation aimed at reducing the number of vehicles on the roads and fuel consumption, and therefore pollution.
8.3. IoV architectures proposed in the literature
To overcome the limits of vehicular ad hoc networks and offer new services, many evolutions of C-ITS architecture were proposed in the literature. This section aims to present these various architectures by highlighting an essential point: the integration of AI techniques in these systems. Therefore, the advantages and limits of these architectures are evaluated based on their automation level.

Figure 8.2. Presentation of IoV architectures described in the literature
8.3.1. Integration of AI techniques in a layer of the control plane
The first approach proposed in various papers involves the integration in the vehicular architecture of a new layer, namely an AI layer enabling the recovery, storage, analysis and processing of data from lower layers (Kaiwartya et al. 2016; Aliyu et al. 2017; Borcoci et al. 2017).
Aliyu et al. (2017) (Figure 8.2(2)) define a new architecture composed of four layers and specifically aimed at the development of cloud computing services in a vehicular environment. The AI layer should enable the processing of data from lower layers (perception, coordination) and thus render possible applications requiring the processing of massive volumes of data, notably for real-time traffic management. This layer also aims to improve the operation of cloud services by increasing the computing capacity of the vehicles using cloud (VuC) services and by optimizing the use of the vehicular cloud computing (VCC) resources.
A similar architecture, intended to serve as a basis for the IoV, is proposed by Kaiwartya et al. (2016) (Figure 8.2(6)). Using various AI techniques (expert systems, VCC, massive data analysis), this layer has the same objectives as that presented by Aliyu et al. (2017): processing of massive volumes of data and application operation improvement. Nevertheless, according to the authors, this layer could also enable the commercialization of vehicular networks. Indeed, the definition and development of economic models (Business layer) for service providers could rely on the statistical analysis of application use data provided by the AI layer.
This definition of a five-layer architecture is resumed by Borcoci et al. (2017) (Figure 8.2(3)). Nevertheless, it is extended in two directions: integration of EC capacities and integration of SDN in the architecture. EC capacities may enable the deployment of intelligent services as close as possible to the user, thus improving the user experience quality and limiting the transmission of information. Moreover, the use of SDN may lead to improving the management of these resources: positioning of applications and reservation of resources (bandwidth, storage and computing capacity, etc.).
8.3.2. Integration of AI techniques in several layers of the control plane
However, the interest of AI is not limited to cloud resources management and processing of information for applications.
Contreras-Castillo et al. (2017) (Figure 8.2(4)) define a seven-layer architecture for IoV. Intelligence is integrated here at various levels: the preprocessing layer, communication layer and control layer. At the level of the preprocessing layer, data processing should make it possible to limit the amount of data transmitted and improve relevance, which would consequently reduce network load. At the level of the communication layer, AI must enable an optimal choice of the transmission technology depending on the required QoS. Finally, at the level of the control layer, AI must enable a management of service providers and data exchange, as it was already proposed in previous works (section 8.3.1).
This idea of applying AI techniques at various levels can also be found in Chen et al. (2018) (Figure 8.2(5)). The authors introduce the idea of cognitive Internet of Vehicles (CIoV). According to them, the absence of intelligent decision making would limit the influence of IoV: suboptimal resource management, lack or reliability of the decision process, weak marketing potential, etc. Hence, AI is applied here not only to network management (network traffic management, safety management, resource allocation), but also to a protection of road users: vehicle self repair, driver health monitoring, driver safety control, emotions analysis, etc. AI application is consequently extended to various levels (communication, cognition and control) and also to various domains (human and network).
8.3.3. Definition of a KP associated with the control plane
To allow for interlayer decision making, Jiacheng et al. (2016) (Figure 8.2(1)) propose the addition of a KP. In this SDN-based architecture, the KP must enable the processing of information coming from the lowest layers (data layers) depending on the needs of other layers (application, control). Hence, this plane must be of help in addressing the main challenges related to SDN integration: management of resource mobility and heterogeneity through various functions (packet transmission control, network virtualization, handover management, etc.).
8.3.4. Comparison of architectures and positioning
The work presented in this section aims to improve the vehicular communication architecture through the integration of AI techniques.
The set of works presented aims to enable the improvement in control plane performances (Table 8.1). Some of these works focus on the evolution of only one layer, the applicative layer, through the addition of one AI layer for data preprocessing and analysis serving applications (Kaiwartya et al. 2016; Aliyu et al. 2017; Borcoci et al. 2017). Others propose multilayer approaches intended also to a better transportation of data (interoperability, routing, bandwidth optimization) (Contreras-Castillo et al. 2017; Chen et al. 2018). Only one of these papers (Jiacheng et al. 2016) proposes the addition of a KP that may enable interlayer decision making and centralized and optimized information processing.
Table 8.1. Comparison of various proposed architectures
| Architecture | Contribution | Multilayer | Knowledge plane | ||
| Management | Control | Security | |||
| Aliyu et al. (2017) | Cloud | Yes | No | No | No |
| Kaiwartya et al. (2016) | Cloud | Yes | No | No | No |
| Borcoci et al. (2017) | Cloud | Yes | No | No | No |
| Contreras-Castillo et al.(2017) | Non | Yes | No | Yes | No |
| Chen et al. (2018) | Yes | Yes | No | Yes | No |
| Jiacheng et al. (2016) | No | Yes | No | Yes | Yes |
| Proposal | Yes | Yes | Yes | Yes | Yes |
Some works also propose the use of AI to support the management plane (cloud resources management, resource management on the edge of the network, positioning of applications) (Kaiwartya et al. 2016; Aliyu et al. 2017; Borcoci et al. 2017; Chen et al. 2018). Nevertheless, Jiacheng et al. (2016) do not address this question and focus on the interactions between the SDN control plane and the KP. Moreover, the idea of interlayer decision making and optimization at several levels has until now been proposed only in support of the control plane. Furthermore, none of the previously mentioned works addresses the idea of applying AI to support the security plane and protect private life (intrusions, routing, etc.) irrespective of its reliability.
To address these limitations, the following part of this document defines a new architecture for the IoV and studies the main advantages, as well as the main barriers, in terms of control, management and security and private life.
8.4. Our proposal of intelligent IoV architecture
This section presents the proposed IoV architecture as well as the various plans it includes (control, management, security and private life, and knowledge). Moreover, it analyzes the various AI applications for control, management and security and private life presented in the literature.
8.4.1. Presentation
The proposed intelligent IoV architecture is presented in Figure 8.3. It includes the following four planes:
- – management and orchestration plane (MOP): this plane is in charge with the global management of architecture and resources;
- – security and privacy plane (SPP): this plane offers security and private life protection services to all the other planes: authorizations, access control, profile management, etc.;
- – KP: this plane offers information processing and analysis and decision making services to all the other planes;
- – control and data plane (CDP): this plane is in charge of recovery, transportation and optimal distribution of information.
This architecture is the first to propose a KP for the IoV. The first work on the KP dates from 2003 and aimed to enable networks to make decisions, particularly management decisions, without human intervention (Clark et al. 2003). The management tasks were accomplished by the network itself, each autonomous entity being able to self-configure, self-optimize, self-protect and self-repair (Krief 2010). Due to implementation difficulties, the KP realizations were limited to concept proofs, but given the current advances, mainly in the field of AI, its deployment can be expected today.
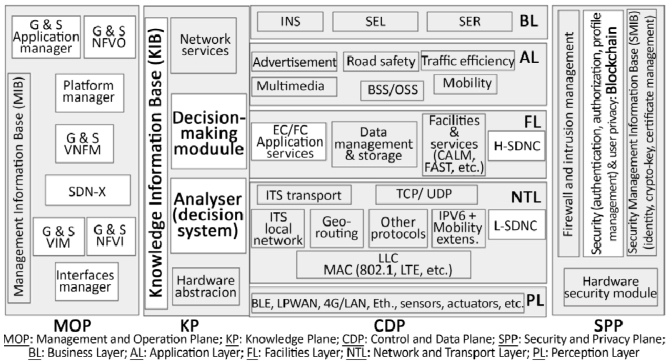
Figure 8.3. Our proposal
8.4.2. A KP for data transportation
Vehicle mobility is very important for data transportation. Indeed, the variation in the number of vehicles with time in a given space involves constant optimization of data transportation to enable high performances: routing, congestion, etc. The application of AI techniques to the control plane of architecture is proposed for various applications, particularly vehicle flow motion prediction, congestion control and dynamic routing.
Vehicle flow motion prediction is a first important point. Indeed, it must enable the improvement of many ITS applications: management of road traffic congestion, reduction of greenhouse gas emissions, reduction of fuel consumption or improvement of services based on localization. Huang et al. (2014) were the first ones to propose a deep learning-based approach for vehicle flow motion prediction. This solution, based on a stacked restricted Boltzmann machines, integrating the idea of multitask learning, aims to improve the performances of methods based on previously used static networks and to prove the interest of a dynamic approach. Nevertheless, the proposed system could be improved. Indeed, traffic prediction is not coupled here with time information. Similarly, Lv et al. (2015) proposed another deep learning-based approach that should enable fine prediction of vehicle motion. Because of unsupervised learning of an auto-encoder model, this approach should also enable nonlinear spatial and temporal correlations by analyzing the data flow. The comparison between this method and other existing approaches (back propagation, ransom walk, support vector machines) proves its efficiency in terms of road traffic prediction. Finally, in Ide et al. (2015), the authors consider both the vehicle flow motion prediction problem and that of Long-Term Evolution (LTE) communications connectivity. Hence, because of the physical data provided by the vehicles and the use of Poisson dependency networks, they build a model enabling them to predict vehicle motion. Owing to information on cellular connectivity measurement, the proposed system also enables, using Poisson regression trees, the distributed prediction of cellular connectivity for each vehicle. Thanks to this, it should be possible to improve the vertical handover process and optimize machine-to-machine communications.
A second important point is congestion control. Indeed, to limit the packet loss and the end-to-end transmission delay and to increase the reliability of vehicular networks, limiting data congestion is essential. Congestion control strategies can rely on various approaches aimed at optimizing various parameters: power management, throughput management, prioritization and scheduling, etc. The idea of intelligent congestion control, to improve these solutions, was proposed in many articles. For example, Taherkhani and Pierre (2016) discuss a solution based on a k-means partitioning that should enable congestion management in intersections using a roadside unit (RSU) to control the congestion level of radio channels. These RSUs recover the data transmitted by the set of vehicles at the intersection level and group them depending on various parameters: size and type of messages, validity, position of the receiver, distance between the vehicle and the road side infrastructure, etc. Consequently, depending on the available resources, communication parameters are assigned to each of these groups: transmission delay, transmission power, congestion window size, etc. Consequently, this enables congestion limitation. Nevertheless, the solution proposed has various limitations, notably the computing capacity and the latency related to this information processing. For the proper operation of cooperative road safety services, the vehicles send short messages to surrounding vehicles (beacons) containing varied information: position, speed, etc. In an area with a significant number of vehicles, the transmission of these regular messages may lead to congestion problems. This is why Toutouh and Alba (2016, 2018) proposed swarm intelligence–based congestion control methods aimed at optimizing the frequency of these messages. Through these methods the use rate of radio communication channels is maintained at a level enabling the proper operation of the network, congestion prevention, while maximizing the number of exchanged messages and, consequently, improving the reliability of the information received by each vehicle. However, as highlighted by these authors, the performances of these two algorithms remain still to be proven within a real environment.
Finally, communication between two vehicles requires a calculation of the path taking into account the characteristics of various links (life duration, bandwidth, delay, etc.). Many approaches based on AI techniques were proposed for making an optimal calculation. For example, Zhang et al. (2018a) proposed a solution based on genetic algorithms enabling an optimal routing aimed at ensuring high QoS. These algorithms try to rapidly find an approximate solution to an optimization problem. Using information related to vehicle traffic (speed, direction, etc.), the authors describe a mechanism for the dynamic computation of the optimal communication path between two vehicles. The proposed solution should enable the management of connectivity dynamicity (motion of vehicles, link break) and the optimization of the packet transmission delay. Nevertheless, the proposed process is complex, and the optimization of the time for searching the optimal path should be considered. In Lai et al. (2015), a machine learning-based approach is proposed. The authors consider three main problems of data dissemination: vehicle motion prediction, evaluation of the transmission capacity of the equipment and evaluation of the transmission direction. The study of these various problems is done at the RSU level, which share information concerning the position of vehicles and the capacity of their communication links. An intelligent computation of the optimal path is then done by the system. The authors want this way to prove the relevance of using AI techniques for routing, ensuring a packet loss ratio and a latency below those offered by the existing solutions. Finally, Yao et al. (2018) describe a mechanism that should enable the determination of future positions of the vehicles and finding the optimal path to reach them. For this purpose, the authors propose a system based on a hidden Markov model and on the history of past motions of the vehicles. Indeed, by analyzing the places previously visited by these vehicles and making a time–space correlation, it is possible to determine where the vehicles are heading to and, consequently, what paths they use. Using this approach, it seems possible to improve the packet transmission delay and to reduce losses. However, to verify the performances of the solution proposed by the authors, implementation in the real environment is required.
8.4.3. A KP for IoV architecture management
Vehicular communication architecture must enable optimal resource management: computing, storage and communication. This management must be present at various levels to enable load balancing between various heterogeneous networks, between various operators as well as between various computing servers. This should enable high performances for all the users, offering the possibility to minimize delay and packet loss and to maximize bandwidth. Similarly to data transmission, for an optimization of resource use, an AI approach was proposed in many articles. The existing works can be classified into three large categories corresponding to various contributions: load balancing between various heterogeneous networks, load balancing for intervehicular communications and management of computing and storage resources (EC).
Due to the motion of vehicles, there are areas and, consequently, base stations that may have to deal with a large number of communications, driving a reduction of QoS. This is why intelligent solutions were developed. These solutions enable load balancing and vertical control in vehicular networks. For example, Li et al. (2017) proposed a solution aimed at enabling efficient association of the user with heterogeneous base stations due to reinforcement learning. Indeed, in order to guarantee good QoS, an optimized distribution of vehicles between various base stations is required. Hence, the association is first established depending on the current information of the base stations and their capacities. Then associations are optimized depending on the information collected by these base stations (peak traffic times, motion of vehicles, etc.), making it possible to determine the number of vehicles that should be associated in a given area and, consequently, how to associate them. To prove the benefits of this approach, the authors compared it to currently used methods: maximal signal to noise ratio (max-SINR) and distributed dual decomposition optimization. In the case of heterogeneous networks, load balancing can also be used to guarantee maximal QoS at any moment, as proven in Xu et al. (2014). The authors of this article also propose the use of a reinforcement learning method (fuzzy Q-learning) that should offer significant adaptability to the evolution of traffic conditions. Indeed, it must enable the determination of the optimal network for data transmission depending on four parameters: signal to noise ratio, number of vehicles connected to the concerned network, speed of the vehicle and amount of data to be transmitted. The authors prove the relevance of this service for multimedia applications. Because of the proposed load balancing technique, throughput is improved and low latency is ensured. Finally, in an attempt to limit the deployment of base stations and to best use the available resources, Zheng et al. (2016) defined a system expected to help optimize the packet transmission delay in a virtual environment (SDN). This system, relying on Markov chains and Bellman equations, is composed of two main parts. The first is a macroscopic management of virtual resources allocation (MaVRA) based on the analysis of global and timeextended parameters, especially traffic density. As for the second part, it involves a microscopic management of virtual resources allocation (MiVRA) depending on rapidly evolving parameters, notably the state of the queues of network equipment and the state of communication channels. Through a simulation, the authors of this article prove the gains in terms of delay of the proposed approach.
Certain applications, notably those related to road safety, have strong latency constraints and rely mainly on intervehicular communications. However, to maintain high QoS, it is important to use the set of available resources optimally. This is why Ashraf et al. (2016) introduced a system enabling load balancing between various vehicle-to-vehicle (V2V) paths. For this purpose, the authors define a mechanism introducing the formation of groups of vehicles depending on their movement (position, direction and speed). The formation of these groups enabled the optimization of intergroup exchanges. This optimization also occurs inside these groups because of the formation of pairs of vehicles depending on the stability and QoS of these communication links. Hence, this system enables the best use of the available V2V links. Similarly, Ye et al. (2019) define a decentralized mechanism enabling a vehicle to optimally use the available communication resources. This system, based on reinforcement learning and deep learning, meets the V2V communication constraints, while minimizing the interferences with vehicle-to-infrastructure (V2I) communications.
Finally, in order to offload the core of the network and offer a lower latency, as well as a higher throughput, many works advance the idea of deploying information storage and processing servers at network edge (EC). There are, nevertheless, many problems related to the use of these resources, such as whether these resources should be available at the level of the RSU (base stations) or inside the vehicles. This is why Sun et al. (2018) are interested in the sharing the computing resources between vehicles. Hence, if one vehicle has resources that it does not use at a given moment, these resources could be used by the surrounding vehicles. The problem of the QoS of this type of service however remains, and this is why the authors propose a system that should enable the latency time minimization during the outsourcing of data processing. This approach relies on a task replication algorithm based on game theory (combinatorial multi-armed bandit theory). This system should enable each vehicle intending to outsource computing tasks to know how much time would take to each of the surrounding vehicles to complete this task. Thanks to this, it is possible for these vehicles to select a vehicle offering sufficient QoS for the considered application. The authors also consider the question of task replication, when the density of vehicles is significant, and the performance evaluation of this system. These tasks can also be dealt with at the RSU level. However, to avoid overloading an equipment, interequipment collaboration is essential. This is why Li et al. 2019 introduced reinforcement-based learning to enable load balancing between various roadside servers. This system relies on road traffic analysis and future road traffic prediction to estimate the load level of each server of roadside equipment and, consequently, to optimize task distribution (data processing, storage, etc.), particularly for HD (highdefinition) applications that should improve road traffic conditions.
8.4.4. A KP for securing IoV architecture
In order to guarantee road user safety and prevent the actions of malicious entities, securing vehicular communications is also an essential issue. Indeed, sending erroneous messages, deleting messages or still disturbing communications could strongly deteriorate the performances of IoV system, and even render it dangerous for road safety. Because of the integration of AI techniques, the safety level of the IoV architecture could be improved, particularly through intrusion detection, prevention of routing attacks and protection against denial of service (DoS) attacks.
Intrusion detection should facilitate the identification of abnormal behaviors at various levels: vehicle, roadside equipment, etc. Kang and Kang (2016) propose a system that should enable the detection of intrusions inside the vehicle, using deep learning techniques. In particular, this system should enable the detection of abnormal behaviors inside the controller area network (CAN) data bus of the vehicle. This CAN bus is a system used to establish a communication between the various components of the vehicle. Its security is consequently essential for the operation of the autonomous vehicle. According to the evaluation conducted by the authors, the proposed unsupervised classification method and the definition of characteristic vectors based on the analysis of packets sent through the vehicle should enable efficient detection of real-time attacks. Zeng et al. (2018) aim to propose a system that uses machine learning to locally and globally detect intrusions. Global detection is done by RSUs, which have significant computing capacity and a global view of the network, due to their exchanges. Local detection is done at the vehicle level. Vehicles being organized in cluster, this system aims to identify abnormal behaviors of two types of vehicles: cluster heads (CHs) and vehicles exchanging of other clusters (multipoint relay [MPR]). Data concerning CH context and behavior are sent to RSUs and analyzed using a neural network in order to determine if the behavior of the CH is normal or malicious. Locally, vehicles are in charge of controlling the behavior of vehicles communicating with other clusters (MPR). Their computing capacities being limited, these vehicles compare the number of packets received and transmitted by these MPR vehicles. Hence, the combination of these two systems (local and global) must enable securing vehicular communications and deleting malicious vehicles. Finally Alheeti et al. (2015) compare the performances of various AI techniques for intrusion detection and abnormal behaviors of vehicles (gray holes) in vehicular networks. The first approach is based on a support vector machine (SVM) system and the second on a feedforward neural network (FFNN) system. This comparison proves the high efficiency of neural networks in anomaly detection and the limitation of the number of false negatives. However, the performances of this approach in terms of delays prove to be significantly lower than those of the SVM approach.
The detection and prevention of DoS attacks is another essential point. Indeed, the perturbation of vehicular communication services can hinder the exchanges between vehicles or between vehicles and infrastructure and may jeopardize the road users’ safety. This is why Nyabuga et al. (2016) propose the detection of attacks using particle swarms optimization. Indeed, for the detection of DoS attacks on the V2I and V2V communications, the swarm approach may yield detection probabilities higher than those of the approaches using genetic algorithms, as proven by the authors. Alheeti et al. (2016) propose the first approach based on fuzzy Petri nets for the detection of intrusion and DoS attacks in a vehicular environment. The proposed approach must enable, because of the extraction of various characteristics (number of forwarded packets, number of discarded packets), the identification of external attacks (at the level of other vehicles) and internal attacks (inside the vehicle) with high probability and a limited false alarm rate. Nevertheless, it is still possible to improve the proposed solution (extension to other attacks, evaluation and use of resources). Finally, in Lyamin et al. (2018), the authors focus on the detection of radio jamming–based attacks in platoons. Indeed, the formation and proper operation of these platoons rely essentially on the exchange of information between vehicles and a perturbation of these communications, readily implemented, could pose a real danger. Hence, the authors first compare the existing reference methods based on models or data. Second, they propose a new hybrid method based on the statistical analysis of the network traffic and on data exploration methods. This new intelligent approach should make it possible to reach acceptable performances, even in cases of variable jitter during the emission of information messages. The same article undertakes an interesting discussion related to the application of deep learning to vehicular networks and the current limitations of these approaches, notably the amount of data required for learning.
Finally, during the computing of the communication paths, in order to avoid network disruption, it seems important to take into account the potentially malicious or infected nodes in order to eliminate them from the routing process. Hence, Krundyshev et al. (2018) focus on the malicious nodes transmitting false routing information and indicating that they provide the shortest communication path to the destination node, without this being the case. There are many routing attacks in vehicular networks: DoS, black hole, wormhole, Sybil, etc. The proposed solution should make it possible to prevent these various attacks by analyzing node behavior. For this, it relies on a confidence model and on a swarm intelligence algorithm (intelligent water drops algorithm). Because of a definition of a confidence index for each vehicle, based on the opinion of other vehicles, and because of a rapid transmission of this information, the proposed solution makes it possible to maintain a low transmission delay and high throughput and received packet percentage for various types of attacks (wormholes and black holes). Similarly, Zhang et al. (2018b) try to define an approach leading to high packet delivery rates and low throughputs in attack situations, without generating significant additional communication costs. This method relies on an adaptive routing algorithm AntHocNet, to which a fuzzy logic detection system was applied in order to exclude a decision and routing process, as the nodes may prove to be malicious. To identify the malicious nodes, each vehicle analyzes the behavior of surrounding vehicles depending on various parameters, notably the transmitted (received/sent) packet ratio over a certain period of time. This is why this method makes it possible to improve the performances of AntHocNet algorithm in case of black hole attacks. However, the scalability of this solution and the analysis of its performances for other types of attacks remain to be studied.
8.5. Stakes
The architecture that was proposed here, relying on the definition of a KP that serves all the other planes (control, management, security and private life) is expected to have many benefits: intrusion detection, load balancing, congestion control, vehicle motion prediction, etc. Nevertheless, the implementation of the proposed architecture depends on overcoming many obstacles, notably the security and the protection of private life, the complexity of computing methods, distributed learning and vehicle flow motion.
8.5.1. Security and private life
As indicated in Liang et al. (2019), although intelligent approaches may have many benefits for the security plane (intrusion detection, secure routing, etc.), the integration of AI techniques in vehicular architecture may raise serious security and confidence questions. Indeed, since training these algorithms relies on the analysis of existing data as well as on the integration of erroneous data or data manipulated by a malicious entity, these may modify the expected behavior of the intelligent system. Hence, in an environment as sensible as the vehicular environment, the study of reliability and robustness of these AI techniques seems essential. Moreover, the development of these approaches requires sharing user and processing power outsourced on the edge of the network or in the cloud. The development of solutions ensuring protection of user private life (anonymity, processing as close as possible, etc.) is also an essential question.
8.5.2. Swarm learning
Swarm learning techniques operate based on the collection of information by each node of the network and by information exchange between these nodes. Indeed, cooperation is essential so that each node has a global or partially global view. But in a vehicular environment, information transmission serving this intelligence may require significant communication resources that may not be available. Indeed, swarm learning approaches intended for vehicular communications such as Toutouh and Alba (2016, 2018) or Nyabuga et al. (2016) do not take into account the limitations related to vehicular environment. Moreover, applying these methods to vehicular environment requires considering the idea of cooperation systems that take into account the physical constraints of equipment and the environment constraints (delays, communication channels, bandwidth, transmission power, etc.).
8.5.3. Complexity of computing methods
The question of computing complexity is also an important problem. Indeed, the solutions based on deep learning developed outside the vehicular environment require significant computing and storage capacities for algorithm learning and training. This is expected to yield results at increasingly higher performances. However, the vehicles have limited computing and storage capacities and these solutions cannot be deployed in this context. This is why Zeng et al. (2018) propose an intrusion detection solution adapted to the capacities of vehicles. Taking into account these capacities and the development of less computing power consuming solutions are essential. Indeed, since vehicular communications require low latency, many decisions and computations will be expected to be made by the vehicles, without external support. Therefore, adaptation to these resources requires the design of low complexity computing methods, which guarantee high performance levels.
8.5.4. Vehicle flow motion
Although Huang et al. (2014), Ide et al. (2015) and Lv et al. (2015) introduce various solutions for the prediction of the vehicle flow motion, none of them has for the time being been tested in a real environment. Moreover, many improvements may be considered in order to increase performances (Huang et al. 2014). The prediction of vehicle flow motion is the common basis of these works, whether it is a matter of securing, controlling or managing the communications. Moreover, the development of a reliable, normalized solution, offering optimal performances, notably in terms of latency, is an essential point for the whole vehicular architecture. Moreover, the analysis of driver and vehicle user behavior may enable the development of even higher accuracy solutions. Consequently, it is an open domain for which the evaluation of proposals in a real environment is crucial.
8.6. Conclusion
The reference architecture of cooperative intelligent transportation systems has various limitations in its current state: capacity to process a significant amount of data, interoperability, guarantees of QoS, etc. This is why vehicular networks evolved toward a new paradigm: the IoV. IoV is expected to address the limitations of vehicular networks and to develop new services: driver assistance, road safety, health, etc.
The evolution of vehicular architecture and the ascent of the IoV rely on the integration of new technologies in the vehicular architecture. AI is part of these technologies. Indeed, it could offer many advantages, particularly through intelligent decision making and the automation of many services. This is why many publications have already proposed definitions of vehicular communication architectures integrating AI techniques. Nevertheless, these architectures focus essentially on an evolution of the control plane of the vehicular communication architecture and not on an evolution of other planes, namely the management and security planes, for which the integration of AI techniques could also bring many benefits.
This is why this chapter proposes the addition of a fourth plane, namely the KP, in support of all the other planes. This plane is also expected to enable multilevel decision making, a more efficient information processing and an improvement of many services. Section 8.4 of this chapter presents this KP, as well as the benefits for each plane: management (load balancing, management of distributed resources, etc.), control (motion, congestion control, dynamic routing) and security (intrusion detection, DoS, secure routing). The integration of AI in the vehicular architecture requires, nevertheless, the consideration of various points, notably the security and protection of private life, the complexity of computing methods, swarm learning and the prediction of vehicle motion.
8.7. References
Alheeti, K.M.A., Gruebler, A., and McDonald-Maier, K.D. (2015). On the detection of grey hole and rushing attacks in self-driving vehicular networks. 7th Computer Science and Electronic Engineering Conference (CEEC). 24–25 September 2015, Colchester, United Kingdom, 231–236.
Alheeti, K.M.A., Gruebler, A., McDonald-Maier, K.D., and Fernando, A. (2016). Prediction of DoS attacks in external communication for self-driving vehicles using a fuzzy petri net model. IEEE International Conference on Consumer Electronics (ICCE). 9-11 January 2016. Las Vegas, USA, 502–503.
Aliyu, A., Abdullah, A.H., Kaiwartya, O., Cao, Y., Usman, M.J., Kumar, S., Lobiyal, D.K., and Raw, R.S. (2017). Cloud computing in VANETs: Architecture, taxonomy, and challenges. Institution of Electronics and Telecommunication Engineers (IETE) Technical Review, 35(5), 523–547.
Ashraf, M.I., Bennis, M., Perfecto, C., and Saad, W. (2016). Dynamic proximity-aware resource allocation in vehicle-to-vehicle (V2V) communications. IEEE Globecom Workshops, 1–6.
Borcoci, E., Obreja, S., and Vochin, M. (2017). Internet of vehicles functional architectures: comparative critical study. The Ninth International Conference on Advances in Future Internet (AFIN). 10-14 September 2017. Rome, Italy, 10–14.
Chen, M., Tian, Y., Fortino, G., Zhang, J., and Humar, I. (2018). Cognitive Internet of vehicles. Computer Communications, 120, 58–70.
Clark, D.D., Partridge, C, Ramming, C., and Wroclawski, J.T. (2003). A Knowledge plane for Internet. Proceedings of the 2003 Conference on Applications, Technologies, Architectures, and Protocols for Computer Communications. ACM publisher. 25–29 August 2003, Karlsruhe, Germany, 3–10.
Contreras-Castillo, J., Zeadally, S., AND Guerrero Ibáñez, J.A. (2017). A seven-layered model architecture for Internet of Vehicles. Journal of Information and Telecommunication, 1(1), 4–22.
ETSI (2010). Intelligent Transport Systems (ITS), communications architecture. Document, European Telecommunications Standard Institute, Sophia Antipolis.
Huang, W., Song, G., Hong, H., and Xie, K. (2014). Deep architecture for traffic flow prediction: Deep belief networks with multitask learning. IEEE Transactions on Intelligent Transportation Systems, 15(5), 2191–2201.
Ide, C., Hadiji, F., Habel, L., Molina, A., Zaksek, T., Schreckenberg, M., Kersting, K., and Wietfeld, C. (2015). LTE connectivity and vehicular traffic prediction based on machine learning approaches. IEEE 82nd Vehicular Technology Conference (VTC2015-Fall). 6–9 September 2015, Boston, USA, 1–5.
Jiacheng, C.H.E.N., Haibo, Z.H.O.U., Ning, Z., Peng, Y., Lin, G., and Xuemin, S. (2016). Software defined Internet of vehicles: Architecture, challenges and solutions. Journal of Communications And Information Networks, 1(1), 14–26.
Kaiwartya, O., Abdullah, A.H., Cao, Y., Altameem, A., Prasad, M., Lin, C.T., and Liu, X. (2016). Internet of vehicles: Motivation, layered architecture, network model, challenges, and future aspects. IEEE Access, 4, 5356–5373.
Kang, M.J. and Kang, J.W. (2016). Intrusion detection system using deep neural network for in-vehicle network security. PLOS ONE, 11(6), 1–17.
Krief, F. (ed.) (2010). Communicating Embedded Networks: Network Applications. ISTE Ltd, London, and Wiley, New York.
Krundyshev, V., Kalinin, M., and Zegzhda, P. (2018). Artificial swarm algorithm for VANET protection against routing attacks. IEEE Industrial Cyber-Physical Systems (ICPS). 15–18 May 2018. St. Petersburg, Russia, 795–800.
Lai, W.K., Lin, M.T., and Yang, Y.H. (2015). A machine learning system for routing decision-making in urban vehicular ad hoc networks. International Journal of Distributed Sensor Networks, 11(3), 374391.
Li, J., Luo, G., Cheng, N., Yuan, Q., Wu, Z., Gao, S., and Liu, Z. (2019). An end-to-end load balancer based on deep learning for vehicular network traffic control. IEEE Internet of Things Journal, 6(1), 953–966.
Li, Z., Wang, C., and Jiang, C.J. (2017). User association for load balancing in vehicular networks: An online reinforcement learning approach. IEEE Transactions on Intelligent Transportation Systems, 18(8), 2217–2228.
Liang, L., Ye, H., and Li, G.Y. (2019). Toward intelligent vehicular networks: A machine learning framework. IEEE Internet of Things Journal, 6(1), 124–135.
Lv, Y., Duan, Y., Kang, W., Li, Z., and Wang, F.Y. (2015). Traffic flow prediction with big data: A deep learning approach. IEEE Transactions on Intelligent Transportation Systems, 16(2), 865–873.
Lyamin, N., Kleyko, D., Delooz, Q., and Vinel, A. (2018). AI-based malicious network traffic detection in VANETs. IEEE Network, 32(6), 15–21.
Macedo, D.F., Dos Santos, A.L., Nogueira, J.M.S., and Pujolle, G. (2008). A knowledge plane for autonomic context-aware wireless mobile ad hoc networks. IFIP/IEEE International Conference on Management of Multimedia Networks and Services (MMNS). 22–26 September 2008. Samos Island, Greece, 1–13.
Mendiboure, L., Chalouf, M.A., and Krief, F. (2019a). Towards a 5G vehicular architecture. Communication Technologies for Vehicles – Proceedings of the 14th International Workshop. Nets4Workshops, Colmar.
Mendiboure, L., Chalouf, M.A., and Krief, F. (2019b). Edge computing based application in vehicular environments: Comparative study and main issues. Journal of Computer Science and Technology, 34(4), 869–886.
Movahedi, Z., Ayari, M., Langar, R., and Pujolle, G. (2012). A survey of autonomic network architectures and evaluation criteria. IEEE Communications Surveys & Tutorials, 14(2), 464–490.
Nyabuga, S.M., Cheruiyot, W., and Kimwele, M. (2016). Using particle swarm optimization (PSO) algorithm to protect vehicular ad hoc networks (VANETS) from denial of service (DoS) attack. International Journal of Advanced Research in Computer Engineering & Technology (IJARCET), 5(3), 628–631.
Sun, Y., Song, J., Zhou, S., Guo, X., and Niu, Z. (2018). Task replication for vehicular edge computing: A combinatorial multi-armed bandit based approach. 2018 IEEE Global Communications Conference (GLOBECOM). 9–13 December 2018. Abu Dhabi, United Arab Emirates, 1–7.
Taherkhani, N. and Pierre, S. (2016). Centralized and localized data congestion control strategy for vehicular ad hoc networks using a machine learning clustering algorithm. IEEE Transactions on Intelligent Transportation Systems, 17(11), 3275–3285.
Toutouh, J. and Alba, E. (2016). Distributed fair rate congestion control for vehicular networks. The 13th International Symposium on Distributed Computing and Artificial Intelligence (DCAI). 1–3 June 2016. Seville, Spain, 433–442.
Toutouh, J. and Alba, E. (2018). A swarm algorithm for collaborative traffic in vehicular networks. Vehicular Communications, 12, 127–137.
Xu, Y., Li, L., Soong, B.H., and Li, C. (2014). Fuzzy Q-learning based vertical handoff control for vehicular heterogeneous wireless network. 2014 IEEE International Conference on Communications (ICC). 10–14 June 2014, Australia.
Yao, L., Wang, J., Wang, X., Chen, A., and Wang, Y. (2018). V2X routing in a VANET based on the hidden Markov model. IEEE Transactions on Intelligent Transportation Systems, 19(3), 889–899.
Ye, H., Liang, L., Li, G.Y., Kim, J., Lu, L., and Wu, M. (2018). Machine learning for vehicular networks: Recent advances and application examples. IEEE Vehicular Technology Magazine, 13(2), 94–101.
Ye, H., Li, Y.G., and Juang, B.H.F. (2019). Deep reinforcement learning for resource allocation in V2V communications. IEEE Transactions on Vehicular Technology. 68(4), 3163–3173.
Zeng, Y., Qiu, M., Ming, Z., and Liu, M. (2018). Senior2Local: A machine learning based intrusion detection method for VANETs. International Conference on Smart Computing and Communication. 10–12 December. Tokyo, Japan, 417–426.
Zhang, G., Wu, M., Duan, W., and Huang, X. (2018a). Genetic algorithm based QoS perception routing protocol for VANETs. Wireless Communications and Mobile Computing. 3897857, 1–10.
Zhang, H., Bochem, A., Sun, X., and Hogrefe, D. (2018b). A security aware fuzzy enhanced reliable ant colony optimization routing in vehicular ad hoc networks. 2018 IEEE Intelligent Vehicles Symposium (IV). 26-30 June 2018. Changshu, China, 1071–1078.
Zheng, Q., Zheng, K., Zhang, H., and Leung, V.C. (2016). Delay-optimal virtualized radio resource scheduling in software-defined vehicular networks via stochastic learning. IEEE Transactions on Vehicular Technology, 65(10), 7857–7867.
