Chapter 12: Dealing with Incident Response
As you go deeper into the field of cybersecurity, you will begin to see there are many specializations and paths a person can choose to pursue. While many think hacking is everything in cybersecurity, there are many more exciting paths, such as threat hunting, malware researcher, digital forensics, and incident response (IR). This chapter is designed to teach you about the need for and importance of IR within an organization.
Throughout this chapter, you will learn about the importance of and need to implement incident handling processes to prevent a threat from spreading on a network. You will learn about the various teams that are created to assist with incident handling for an organization and even a nation. Furthermore, you will gain the skills to perform both server and network profiling to determine whether a system could potentially be compromised, and lastly, you will learn about various compliance frameworks within the industry.
In this chapter, we will cover the following topics:
- Understanding the incident handling process
- Exploring CSIRT teams and their responsibilities
- Delving into network and server profiling
- Comparing compliance frameworks
Understanding the incident handling process
Cyber-attacks and threats exist all around us and each day threat actors are always looking for new techniques to compromise organizations' networks. As many professionals work both continuously and tirelessly to safeguard their organizations from various cyber-attacks, this is truly a challenging task. Within the field of cybersecurity, there are many roles, such as those that uphold the responsibility of implementing countermeasures to prevent cyber-attacks.
In reality, there are no systems or networks that are 100% protected from cyber-threats as it's only a matter of time before a threat actor will discover a vulnerability within a system and exploit it. While many organizations focus on implementing preventative measures such as security appliances and solutions, they also need to prepare themselves for the event that their security solution fails to stop an attack. As there are many events that occur on a network, such as new connections between host devices, security incidents can occur at any time.
Incident response and handling are essential within an organization. Whether it's a small or large enterprise, IR plays a vital role in responding to a cyber-attack. To get a better understanding of the importance of IR, let's imagine an organization focuses only on implementing a few security solutions, such as a Next-Generation Firewall (NGFW), a Next-Generation Intrusion Prevent System (NGIPS), endpoint protection, and so on without considering the need for IR. Having implemented security solutions is good but it doesn't fully safeguard an organization from all types of cyber-attacks and threats. Imagine one day a cyber-threat was not detected by any of the security appliances and bypassed the threat detection sensors on the network. As a result, a single system was compromised and the threat attempted to spread across the network. Since the company did not have an incident response plan (IRP), procedures, or even professionals, the threat was able to spread like wildfire during a very hot dry season. The impact would be tremendous and may cost the organization a lot of money to restore the systems back to a working state.
The main objective of implementing an incident handling process is to reduce the impact of a cyber-attack, ensure the damages caused are assessed, and implement recovery procedures to ensure affected systems are back to a working state. Additionally, effective IR helps professionals to leverage the information collected from a security incident to better understand the intrusion and its functionality. This data helps the security team to be better prepared and equipped to handle future incidents. To help organizations and professionals in developing and implementing proper incident handling processes and procedures, the National Institute of Standards and Technology (NIST) Special Publication (SP) 800-61 Revision 2 provides the Computer Security Incident Handling Guide, which contains recommendations for incident handling procedures.
Important note
The NIST SP 800-61 Rev. 2 for Computer Security Incident Handling Guide can be found at the following link: https://csrc.nist.gov/publications/detail/sp/800-61/rev-2/final.
Understanding the phases of incident handling
As cybersecurity awareness grows and professionals share their wisdom and insights into the anatomy of various cyber-attacks and threats, organizations are beginning to understand that there might be no prior warning about a cyber-attack on their organization. Leadership teams are seeing the need to implement incident handling policies, plans, and procedures within their organizations to reduce the impact of a cyber-attack on their systems and networks.
As an up-and-coming cybersecurity professional, it's essential you understand each phase of incident handling. According to the NIST SP 800-61 Rev. 2 documentation of the Computer Security Incident Handling Guide, the following are the phases of incident handling in sequential order:
- Preparation
- Detection and analysis
- Containment, eradication, and recovery
- Post-incident activity
The following diagram shows the life cycle of the incident handling process:

Figure 12.1 – Incident handling process
Over the next few sections, you will discover the characteristics and the key elements of each phase. You will also understand how each phase helps both the IR team and security professionals to reduce the impact of cyber-attacks and threats within their organization.
Phase 1 – Preparation
The first phase in incident handling is preparation. During the preparation phase, the organization creates an IR team and ensures each person has the necessary training, tools, and resources to efficiently handle a security incident should one occur. Imagine if the organization does not provide the IR team with the necessary resources and an unexpected security incident occurs. The impact could be very bad if the team is incapable of handling the incident due to a lack of resources, whether those resources are a professional, a tool, or even training. Each resource is essential and plays a vital role within the IR team.
When creating an IRP, the following elements should be considered:
- Mission – What is the mission of the IRP?
- Strategies – What are the strategies to be used in the IRP?
- Goals – What are the goals and how are they going to be achieved?
- Organizational approach – What is the approach the organization is going to use?
- Metrics – What metrics are to be used to measure the IRP is working as expected?
- Roadmap – How is the IRP going to evolve and improve over time?
Additionally, during the preparation phase, the organization works on implementing various security controls to mitigate cyber-attack threats. By implementing and configuring various security appliances and solutions, they will reduce the risk of a cyber-attack. Keep in mind that the IR team is not necessarily responsible for the implementation of security controls. The IR team will analyze the types of controls and how they should be implemented to safeguard the organization's assets.
The following are some recommended resources for the IR team:
- Contact information for each team member and other important persons within the organization
- On-call information for other relevant teams and persons within the organization
- Incident reporting mechanisms such as telephone numbers, email addresses, and secure messaging systems that a user can use to report a security incident
- Incident tracking systems such as ticketing systems
- Smartphones for IR team members for outside-work-hours support
- Secure storage facilities for storing sensitive devices and securing evidence for investigation
- Encryption software for secure communication between team members within the organization and other external parties such as federal agencies
- A war room for central communication and coordination
- Hardware and software such as digital forensic workstations, laptops, spare workstations, blank removable media, printers, packet sniffer/protocol analyzers, digital forensic software, evidence gathering accessories, and training on all the hardware and software.
Phase 2 – Detection and analysis
This phase focuses on ensuring all cyber-attacks and threats are detected and analyzed by the IR team. While there are many events that occur on systems and networks, there could be a potential cyber-attack, which is a security incident that requires an investigation.
A precursor is a sign that a cyber-attack is about to occur on a system or network. An indicator is the actual alerts that are generated as an attack is happening. Therefore, as a security professional, it's important to know where you can find both precursor and indicator sources of information.
The following are common sources of precursor and indicator information:
- Security Information and Event Management (SIEM)
- Anti-virus and anti-spam software
- File integrity checking applications/software
- Logs from various sources (operating systems, devices, and applications)
- People who report a security incident
Once a security incident has occurred, it should be properly documented and recorded in the incident reporting system. The following are key pieces of data to be recorded for a security incident:
- The current status of the incident
- A summary of the security incident
- Any indicators that are related to the incident
- The actions taken by the IR team
- The chain of custody if evidence was acquired
- The impact of the assessment that is related to the incident
- Any contact information about other teams or persons who may be involved
- A list of all the evidence that was gathered during the investigation
- Any comments from the IR team
- The next steps to be taken to respond to the incident
Once an incident has occurred, the IR team needs to contain it quickly before it affects other systems and networks within the organization.
Phase 3 – Containment, eradication, and recovery
Within the containment phase, the IR team works on containing the threat from spreading and compromising other systems within the organization. The main goal of this phase is to stop the spread of the threat. Imagine if the IR team didn't actually start their response from the point the when threat was detected; a lot of damage could be done to the organization. Hence, it is vital to stop a threat as quickly as possible.
The following are some key elements of creating a containment strategy:
- Understanding the potential damage to the affected asset
- The need for the preservation of evidence
- The service availability within the organization
- The effectiveness of the strategy
- The time required to implement the strategy
- The resources needed to implement the strategy
- The time or duration of the solution
Eradication is simply the process of removing the threat from any compromised systems and the network. Additionally, during this stage, IR teams ensure the threat no longer exists on any system or network within the entire organization. Once the threat is completely removed from the organization, the IR team starts the recovery process.
Sometimes during the eradication stage, the IR team will notice not all the threats are contained and/or removed from the organization. At this point, the IR team will need to go back to the previous phase of the incident handling process, which is Phase 2 – Detection and analysis, to detect any other threats and analyze them to determine their behavior. For example, if the threat is malware, the compromised system should be immediately isolated (containment) and the malware should be placed in a sandbox or a detonation chamber to understand what the malware is trying to do. This will help the IR team to determine the network connections and port numbers that the malware is using and other functionality of the malware itself.
In the recovery process, the IR team performs data recovery and the restoration of systems back to a working and operational state. This phase may also include restoring data from clean backups, replacing compromised systems, and the re-installation of the Operating System (OS) and applications.
Phase 4 – Post-incident activity
Security professionals use this phase as an opportunity to learn from the experience of a cyber-attack. The lessons learned will help improve the response and actions taken by the security team when future security events occur, such as improving security controls and device configurations, implementing new threat mitigation techniques, and improving the overall IR strategy to reduce the time taken to detect and respond to an incident.
A lessons learned meeting is recommended according to the NIST SP 800-61 Rev. 2 document and the following are some important questions that should be discussed during the meeting:
- What exactly happened during the security incident?
- What time did the security incident occur?
- What were the steps taken by the IR team to ensure the recovery of systems?
- What could be done differently by both the IR team and management the next time an incident occurs?
- What corrective actions can be implemented to prevent similar security incidents in the future?
- What additional tools and resources are needed to detect and prevent future security incidents?
These are just some of the many questions that should be asked during the post-incident meeting. Additionally, the data collected before, during, and after the incident should be securely stored in the event the threat actor is caught and prosecuted.
Having completed this section, you have gained knowledge and understanding of IR and have seen the importance of implementing strategies to reduce the impact of cyber-attacks and threats within an organization. In the next section, you will learn about the various security teams and their responsibilities in preventing cyber-attacks.
Exploring CSIRT teams and their responsibilities
While security professionals are always fighting the battle against threat actors, there are some cyber-attacks and threats that bypass threat detection sensors and security controls on a network. When such security incidents occur, it's important the security engineer or professional reacts quickly to isolate the threat before it can spread and infect other systems within the organization. Many organizations create a special team of security professionals known as a Computer Security IR Team (CSIRT), which is usually internal to the organization.
A CSIRT is responsible for IR within the entire organization, as well as implementing security controls and countermeasures to prevent future cyber-attacks. They are also responsible for the continuous security testing of the organization's security posture, such as performing vulnerability scanning and assessments, and penetration testing to discover any hidden security weaknesses. Furthermore, the CSIRT is responsible for the continuous monitoring of cyber-attacks and threats to the company's systems and network, while ensuring end users are also protected by regularly conducting cybersecurity awareness training. With all these objectives, a CSIRT is able to proactively prevent cyber-attacks before they happen and learn from data collected from past security incidents.
Important note
A CSIRT is primarily responsible for receiving, reviewing, and responding to security incidents.
The following are the various types of CSIRT teams and their responsibilities:
- Internal CSIRT: This type of CSIRT is created within an organization to monitor and secure the organization's assets from cyber-attacks and threats. This team is also responsible for incident handling and managing the overall security of the company and its assets.
- National CSIRT: This team is created by a nation's government and is designed to provide incident handling services and solutions for a nation.
- Coordination centers: Around the world, there are many cybersecurity coordination centers that analyze threats, respond to major security incidents, and coordinate the exchange of vulnerability disclosures to other CSIRTs, hardware and software vendors, and security researchers within the industry.
- Analysis centers: These are specialized centers that gather data on cyber-attacks and threats from various sources. The data is used to observe the trends of cyber-attacks. These trends are used to predict the future of the next generation of cyber-attacks and threats. Such data on observing trends can help organizations to be better prepared and reduce both the time taken to detect a security incident and its impact.
- Vendor teams: Many software and hardware vendors have a dedicated security team that is responsible for discovering, remediating, and disclosing any security vulnerabilities within their software and hardware products. This team is known as a Product Security IR Team (PSIRT).
- Managed Security Service Providers (MSSPs): While some organizations create an internal CSIRT to manage their cybersecurity operations and incident handling, others choose to outsource these services to a trusted vendor. These vendors are known as MSSPs, who provide security services and incident handling to other organizations as a paid service.
- CERT: The Computer Emergency and Response Team (CERT) is a national team that is responsible for disclosing security vulnerability details and information to their nation's population, providing both security awareness and best practices. However, keep in mind the CERT is not directly responsible for responding to security incidents as that's the role of a CSIRT.
Important note
To view a list of all the national CERTs, you can visit this URL: https://www.first.org/members/teams/.
Having completed this section, you are now able to describe various security response teams and their characteristics. In the next section, you will learn how to perform network and server profiling.
Delving into network and server profiling
An essential skill within the fields of both networking and cybersecurity is the ability to profile both network traffic and host systems on an organization's network. Security professionals are always monitoring the network for any indications of an intrusion. Having the ability to observe and recognize suspicious traffic patterns between a source and destination can help reduce the Mean Time to Detect (MTTD). The MTTD simply defines the average time it takes a security professional or a Security Operation Center (SOC) to detect a security incident.
Security professionals are continuously improving their processes, procedures, and overall workflow to catch these cyber-attacks as quickly as possible. Once an intrusion has been detected, the team needs to respond very quickly to contain the threat before it can affect other systems on the network. Another important metric SOCs continuously work on improving is the Mean Time to Respond (MTTR). The MTTR simply defines the time taken for a security team or professional to resolve a security incident on a network. By reducing both the MTTD and the MTTR, a SOC can use these metrics to indicate improvements in incident handling procedures and processes.
Even profiling servers on a network can help security professionals to determine whether there are any unauthorized services running on the system that may indicate an intrusion on the system. It's vital a baseline is created for both network traffic and server performance. Creating a baseline of normal traffic on a network helps security professionals to determine whether the network is performing normally or there a possible cyber-attack in progress. Additionally, the same can be done for servers within an organization. System administrators and security professionals can use the baseline to determine whether a system is operating normally or infected with malware.
Network profiling
Network profiling allows security professionals to create a baseline of normal network traffic that occurs on a normal business day within an organization. The baseline is then used to compare any future events on the network that may seem abnormal. Imagine an organization's network is usually busy between typical work hours such as Monday – Friday between the hours of 8:00 a.m. and 4:00 p.m. During these times, hundreds of devices and users are exchanging messages and using the network to its full potential. At the end of the workday, after all the employees leave, the network traffic and activities are typically low until the next workday starts. What if one day at 5:00 p.m., when no employee is on the network and the business is closed, there is a high volume of network traffic between the internal corporate network and a remote server on the network?
Security professionals can use their baseline to compare with the traffic flow to indicate whether there is abnormal behavior on the network. Imagine an organization does not have a baseline for its network. If a network-based intrusion occurred one day, the network professionals may not even notice a possible intrusion was happening while not having a real-time traffic flow to compare to a baseline that contains normal traffic within the organization.
Using a tool such as NetFlow or Wireshark allows both networking and security professionals to gather transactional data about a network and devices. It allows security professionals to create a baseline of network traffic, determine the most-used network protocols within an organization, and study network statistics. Imagine there's a malware-infected host on the network and it's sending a lot of messages to a remote server on the network. With tools such as NetFlow and Wireshark implemented, security professionals can actively monitor network statistics and will be able to quickly identify when there is a suspicious amount of messages leaving a particular host on the corporate network with an unknown destination server on the internet. Furthermore, network profiling also allows security professionals to identify internal network attacks. Imagine a disgruntled employee decides one day to research various hacking techniques and attempts to compromise all the organization's internal servers.
The following are key elements that are used by security professionals in network profiling:
- Total throughput: This element simply defines the total amount of data that is being exchanged between a source and destination host devices over a period of time. As a security professional, if you notice there is high traffic between one of your internal servers and a remote device on the internet, this is a possible indication of a cyber-attack in progress. The organization's security team is required to perform an investigation into the flow of traffic between the source and destination to determine whether it's a real intrusion or not.
- Session duration: Session duration is a measurement of time from the point a source host establishes a connection to a destination device and the termination of the connection. Typically, a source device will establish a session to a destination and terminate the connection when the transaction is completed. However, malware-infected systems sometimes establish a session with a typically longer duration with their Command and Control (C2) servers on the internet. Systems with unusual-length sessions between themselves and a remote system should be flagged as suspicious network activity.
The following screenshot shows the connections between a Windows machine and remote devices:

Figure 12.2 – Active connections on a Windows system
As shown in the preceding screenshot, the netstat –ano command on the Windows system allows a security professional to see all the active connections between the local system and any remote devices. You are able to see the protocol (Proto), the source IP address and port number (Local Address), the destination IP address and port number (Foreign Address), the state of the connection, and the associated process ID (PID).
- Ports used: Network service ports are opened on servers that are expecting an incoming connection from a client, while a client device opens a service port to send data to a server. Security professionals may notice there are unusual Transmission Control Protocol (TCP) and User Datagram Protocol (UDP) processes that are attempting to establish sessions to remote systems.
The following screenshot shows a TCP Synchronization (SYN) port scan on a target device:
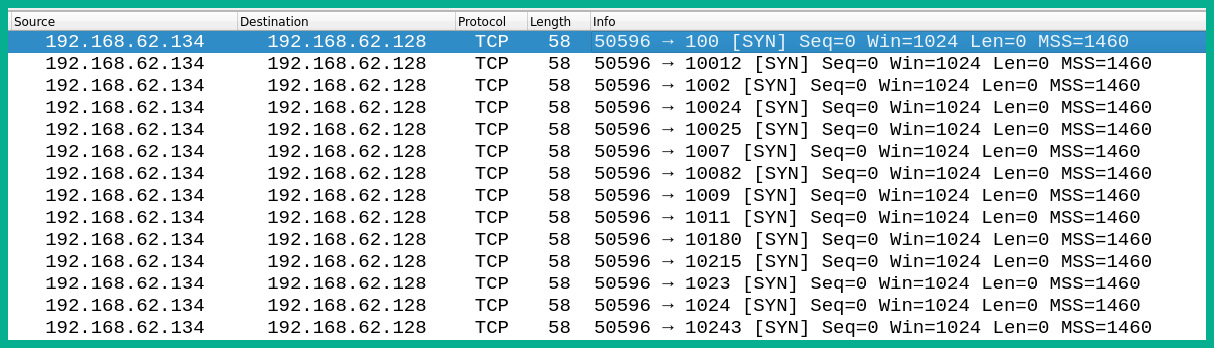
Figure 12.3 – TCP SYN scan
The following screenshot is a TCP SYN port scan captured by Wireshark. As shown, the attacker machine (192.168.62.134) is performing a TCP SYN port scan on a target machine (192.168.62.128) for the purpose of detecting any open TCP ports on the target system. From a security perspective, seeing this traffic flow on the network indicates there is a threat actor performing an unauthorized scan on the network.
- Critical asset address space: This element simply determines the IP address spaces and subnets that contain critical assets that belong to the organization. It's important to monitor both inbound and outbound traffic between these critical asset address spaces and other networks.
As professionals, we always need to ensure there is a balance in monitoring all assets within the organization. While monitoring network traffic, you'll be able to see any intrusions as they happen in real time. However, we cannot forget about our critical servers that are used to provide various services to the organization and store a lot of data. Next, we'll take a dive into learning about server profiling.
Server profiling
The concept of server profiling allows a security professional to create a baseline of a server that is considered to be in its normal operating state. The baseline is used to measure any future events of the server, which can determine whether the server is operating normally or abnormally. To put it simply, systems that are infected with malware will show behaviors such as attempting to establish network connections with remote servers on the internet, attempting to spread malware on the network, and so on. These activities will generally cause the server to behave abnormally and a security baseline can be used to measure the performance and help provide an indication of compromise on the server.
Before establishing a baseline for any server within the organization, you first need to understand the purpose and function of a server. A server can be created and implemented for many purposes, such as file storage, application hosting, directory services, print services, and so on. Not all servers have the same function and purpose on a network, therefore a file server baseline will be different from a directory services server baseline. To better understand how to begin with server profiling, there are various elements that a security professional needs to take into consideration.
The following are the various key elements that are used in server profiling:
- Listening ports: Each server is created for a unique purpose and function on a network. Therefore, each server will be running various services. Each uniquely running service on a server will open a TCP or UDP port to listen for incoming connections from clients on the network. For example, a web server will have port 80 and/or 443 open. If a server has port 80 and/or 443 open but does not have a web service, this may be an indication of suspicious activity on the host.
The following screenshot shows an Nmap scan on a target server (192.168.62.128):
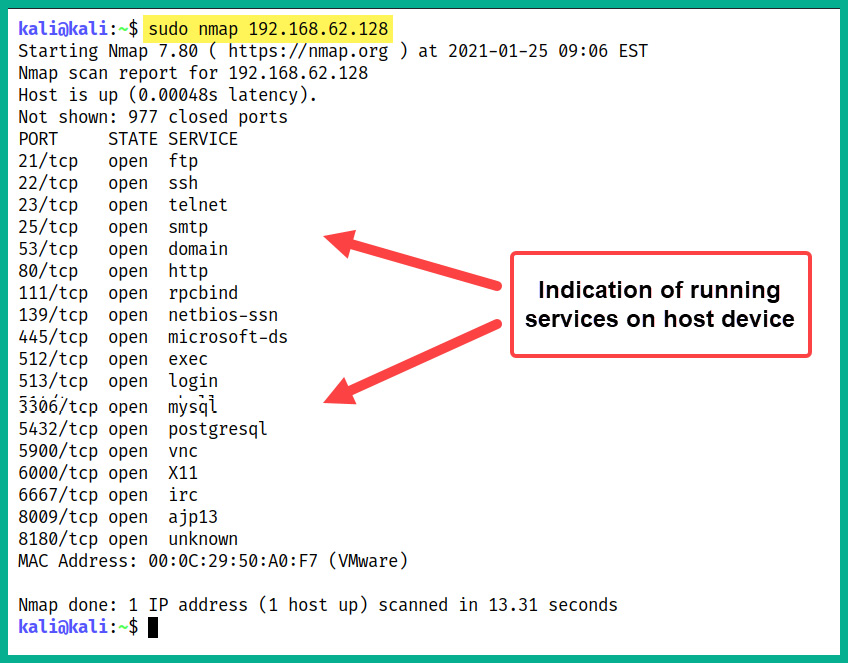
Figure 12.4 – Nmap port scan
As shown in the preceding snippet, a port scan was performed on a target server (192.168.62.128) to determine whether the device has any open ports and running services. The results indicate there are many open ports and each port is associated with a unique service on the device. Imagine this system is on your network; seeing all those open ports on a server would definitely raise a red flag. A server should only be running authorized services based on its purpose and function on the network, and should not have any unused network ports open.
Important note
Nmap (short for Network Mapper) is one of the more popular network scanners in the industry. However, do not scan systems or networks if you do not have legal permission to do so. It is illegal to perform unauthorized scans on systems and networks that you do not own. To learn more about Nmap, please visit https://nmap.org/.
- Logged-in users/service accounts: Knowing which users are authorized to log in to a server makes it easier to create and implement security controls and restrictions. There are also service accounts on servers that are used by the operating system to perform system-related tasks and operations. All user accounts should always be closely monitored as threat actors will attempt to create user accounts for themselves on a compromised system. Additionally, threat actors will attempt to escalate their privileges on a system to ensure their user account has administrative or root-level access.
- Running processes: While a server is configured with one or more roles to provide a service to the network, there may be unauthorized and malicious processes that are also running. Security professionals need to always monitor the running processes on servers and determine what caused the event and whether it's a security incident. To put it simply, threat actors will usually compromise a system and install a backdoor as a service on the victim's system.
- Running tasks: These are tasks that are usually running in the background on a server and are commonly overlooked by IT professionals. However, threat actors and malware can create malicious tasks that are running in the background as a technique to reduce the risk of detection by a security professional or threat detection application. It's important to also monitor all running tasks on a server.
- Applications: Security professionals should monitor the type and purpose of any installed application on a server. Threat actors will also attempt to transfer their applications and install them on compromised systems. Ensuring the security team is always aware of the applications on the servers can help determine whether an unauthorized application is present.
Having completed this section, you have learned about the need for both server and network profiling, which help security professionals to determine what is considered to be normal and abnormal within their organization. In the next section, you will learn about various compliance frameworks and how they are used to improve the security posture within various industries.
Comparing compliance frameworks
While many organizations work toward implementing a Defense in Depth (DiD) approach to secure their systems and networks, there are various industries in which companies are required by law to be compliant with information security standards. Information security standards are designed to reduce the risk of a potential cyber-attack by threat actors on an organization's assets. These standards are created and designed by industry-recognized organizations that focus on data privacy and protection.
While organizations are required to be compliant based on their operating industry, it is definitely worth mentioning that compliance does not necessarily prevent a cyber-attack and does not fully secure a network. Being compliant simply means the organization has met the minimum requirements to satisfy an attemptable level of security within their networks and systems.
As we know, the internet is continuously growing as more organizations connect their corporate networks to it. Today, the internet is the largest network for sharing resources and learning new things, and even organizations are expanding their customer support beyond geographic borders. Even healthcare providers use the internet to share research with other like-minded professionals and interconnect branches together.
Long ago, we needed to make purchases using cash for goods and services. With the advancement of technologies and the internet, organizations such as banks and other financial institutions are leveraging the internet to offer their services to customers beyond just having physical cash. Payment card services such as credit cards and debit cards allow a person to walk around without a wallet filled with a lot of cash, having a simple payment card instead, which is linked to the person's bank account. The way we make in-store purchases has even evolved from using payment cards; now you can link a bank account or a credit card to services such as Google Pay and Apple Pay, allowing a person to use their smartphone to perform payment transactions at the checkout counter in a store.
However, while all these technologies are super awesome and provide convenience for both consumers and retailers, threat actors are always looking for ways to compromise these systems and networks to steal data. Hence, there is the need for various regulatory and compliance standards to ensure various organizations' systems and networks meet at least a minimum level of security to protect data.
Many of us would use a credit card to make daily payments and purchases, but have you ever considered whether the systems and networks transmitting and storing your credit card information are secure? When you visit a healthcare provider and your data is stored on their systems, do you know whether their networks and systems are secure? Ensuring your organization is compliant based on the operating industry, such as healthcare or finance, is vital.
PCI DSS
The Payment Card Industry Data Security Standard (PCI DSS) is a data protection and privacy standard that is created and maintained by the Payment Card Industry Security Standards Council (https://www.pcisecuritystandards.org/). Any organization that provides services and handles the processing of transactions using a payment card is required to be PCI DSS compliant as it will build trust with customers, ensure the company abides by the nation's local laws, and even ensure their systems and networks meet the minimum level of security that is needed to protect payment card data throughout the entire transaction performed by the customer.
The PCI DSS standard is designed to provide the following control objectives:
- Build and maintain a secure network and systems.
- Protect cardholder data.
- Maintain a vulnerability management program.
- Implement strong access control measures.
- Regularly monitor and test networks.
- Maintain an information security policy.
The PCI DSS standard defines how the following data is handled by a system:
- Primary Account Number (PAN)
- Payment cardholder name
- Payment card expiration date
- Service code
- Full track data (magnetic-strip data or equivalent on a chip)
- Card Verification Code (CVC)
- Card Verification Value (CVV)
- Card Security Code (CSC)
- Card Identification Code (CID)
- PINs/PIN blocks
Important note
To learn more about the specific details of the PCI DSS standard, the official document can be found on the PCI Security Standards Council website at https://www.pcisecuritystandards.org/document_library.
HIPAA
The Health Insurance Portability and Accountability Act (HIPAA) was created to provide data protection and privacy within the healthcare industry. With many healthcare providers around the world, there are many systems and networks both transmitting and storing the Protected Health Information (PHI) of patients. While many healthcare providers use computer systems and networks in their day-to-day operations, it's equally important that patients' medical records are treated with care and are kept private and secure from unauthorized users.
The following are examples of PHI medical data as it relates to a patient:
- Patient's name
- Patient's address
- Patient's date of birth
- Telephone number
- Email address
- Social Security Number (SSN)
- Driver license information
- Medical record numbers
- Account numbers
- Health plan beneficiary numbers
- Names of relatives
- IP address numbers
- Biometric information
- Full-face photographic images
Important note
To learn more about HIPAA, you can visit the U.S. Department of Health and Human Services website at https://www.hhs.gov/hipaa/index.html.
SOX
The Sarbanes–Oxley Act (SOX) is a law that was created by the United States Congress and is designed to protect the investors who mistakenly invest in fraudulent financial institutions. Whether these financial institutions are public companies or accounting firms, the law outlines how those companies should control and disclose any financial information. Additionally, SOX helps organizations to ensure there are good practices and integrity in how they conduct both financial practices and reporting.
Important note
To learn more about SOX, you can visit the United States Congress website at https://www.congress.gov/bill/107th-congress/house-bill/3763.
Having completed this section, you have learned about the need for compliance frameworks and their purpose in ensuring data privacy within various industries.
Summary
During the course of this chapter, you learned about the importance of having a proper IR strategy within an organization and have discovered the key elements within each phase of IR. You gained knowledge and understanding of various security teams, such as the different CSIRTs, and their responsibility in helping organizations in the fight against threat actors and their cyber-attacks. Furthermore, you saw the importance of both network and server profiling as they help security professionals to determine whether there is any suspicious activity. Lastly, we covered the fundamentals of various compliance frameworks within the industry, such as PCI DSS, HIPAA, and SOX.
I hope this chapter has been informative for you and is helpful in your journey toward learning the foundations of cybersecurity operations and gaining your Cisco Certified CyberOps Associate certification. In the next chapter, you will learn about various models and frameworks that are used during incident handling within an organization.
Questions
The following is a short list of review questions to help reinforce your learning and help you identify areas that require some improvement. The answers to the questions can be found in the Assessments section at the end of this book:
- Which of the following standards outlines the recommendations for computer security incident handling?
A. NIST SP 800-62
B. NIST SP 800-61
C. NIST SP 800-53
D. NIST SP 800-51
- Which phase of incident handling is responsible for removing a threat?
A. Detection and analysis
B. Post-incident activity
C. Containment, eradication, and recovery
D. Preparation
- Which security team is responsible for disclosing security vulnerability details and information to their nation's population, providing both security awareness and best practices?
A. CERT
B. PSIRT
C. MSSP
D. National CSIRT
- Which tool can a security professional use to profile network traffic?
A. RSPAN
B. SPAN
C. Nmap
D. NetFlow
- Which of the following is a requirement for healthcare providers to protect patients' records?
A. PHI
B. HIPAA
C. SOX
D. PII
