Chapter 6: Information Security for a Changing World
The world is changing quickly and some of the changes are inherently more secure, while others are less secure. Most changes are benign from a security perspective but require a different approach and render previous technologies and techniques obsolete. While we cannot abandon timeless information security best practices, failure to meet the challenges of a changing world can also result in catastrophe.
At a time where the security talent gap is reaching crisis levels, the changing technology landscape demands more from people who are already stretched thin. Understanding the modern threat landscape is a key element in building an effective security program and reducing the strain on overburdened teams. Trying to apply antiquated technologies and approaches to the modern world creates unnecessary work and stress for cybersecurity practitioners.
Meeting the challenges of today and tomorrow in a thoughtful way will help build resilient systems and processes that can adapt to the changing environment. This chapter will discuss the unique challenges of the modern world using techniques that are timeless and independent of the underlying technology. We will begin by talking about the security triumvirates that provide different perspectives for how a person can evaluate the efficacy of an information security program. Then, we will discuss each of the three disciplines that make up the modern information security landscape. Those three disciplines are securing the workloads that store, process, and transmit sensitive information, securing the endpoints that people use to access them, and managing the identities, access, and behavior of entities that have been granted access to those systems. The disciplines are defined by ambiguous terms in this section intentionally. In the future, just as terminals were replaced by desktops and eventually laptops, computers may increasingly give way to tablets and smartphones or other devices that have yet to be invented. Regardless, there will be an endpoint, or a point of interaction where the intentions of a human being are digitized for the first time. Similarly, just as mainframes gave way to data centers and are currently moving to cloud services, those cloud-hosted workloads may move to a distributed edge and ultimately to an architecture yet to be invented. Regardless, there will always be workloads that store, process, and transmit information.
The key to understanding information security holistically is to look at the objectives and challenges from a high level, rather than focusing on tactics, techniques, and technologies. Tactics, techniques, and technologies change, but the fundamentals rarely do. In fact, it could be argued that the fundamentals are actually thousands of years old. How is that possible? Much of information security is analogous to the military, which has a rich history. To help understand information security at a high level, let's explore frames of reference that may be helpful.
In this chapter, we will cover the following topics:
- Frames of reference
- Challenges with the traditional information security model
- Protecting information
- Securing networks and workloads
- Securing identities and granting access
- Securing endpoints
Frames of reference
Information security is a large problem. It is difficult to understand it holistically without using a frame of reference. Those who try to tackle information security without a frame of reference often retreat to silos and individual disciplines. As a result, many people understand endpoint security, network security, vulnerability management, cloud security, or information protection, but far fewer people understand information security holistically.
The good news is that information security is not that complex when you focus less on technology and focus more on actors and objectives. When you do, you will see parallels between information security and military operations.
Military connection
The connection between information security and military operations makes sense when you think about it and can be useful. In some cases, attacks are, in fact, military operations. In those cases, you could envision the attackers and defenders as cyber armies with similar roles as in a traditional conflict. One is trying to capture an objective and one is trying to defend it, with both sides deploying weapons and tactics to prevent their adversary from accomplishing their objective.
Even in cases where the adversary is a criminal, the operations themselves are not dissimilar from counterinsurgency or counter-terrorism operations. Like counter-insurgency operations, stopping criminals is difficult because they will steal credentials and blend in with the legitimate user population. Countermeasures must be designed so they can prevent the insurgents from accomplishing their objectives while impacting the legitimate user population as little as possible.
I served the United States Army and was deployed to Iraq in 2004 and 2005. Since beginning my information security career, I have been struck by similarities between defending information in an organization and defending the local Iraqi population from insurgents and eventually sectarian violence. The challenges are similar, and the solutions are akin to each other. This is important because while information security is relatively new, and novel techniques and technologies are being created every day, the principles of military operations are well established. This means we can learn lessons from military history and military thinkers that we can apply to modern information security challenges. Additionally, books such as Robert Greene's The 33 Strategies of War and Sun Tzu's The Art of War are useful for both understanding the strategies employed by attackers and developing defensive strategies for your program. There are countless other military strategy books that are as useful as, or more useful than, any information security book when designing an information security program, if you can apply your imagination and see the parallels.
The next way to look at information security from a holistic perspective is the common security triumvirates that I will introduce in the next section. There are more, but in the spirit of the triumvirates, I chose three.
Security triumvirates
The rule of three is a timeless rule used in writing and spoken word that says characters or ideas are more satisfying or memorable when they are presented in groups of three. A triumvirate is a concept that comes from ancient Rome where three people would share power equally. It was rarely equal, but when you think of a triumvirate conceptually, you can imagine three equally powerful concepts that work together.
Many information security concepts are presented in groups of three. I am not certain if these concepts are intentionally presented in sets of three due to the rule of three, or if the rule of three makes concepts presented in groups of three more memorable. Regardless, there are triumvirates that help provide a lens through which to view information security. The first we will examine is perhaps the most widely used: people, process, and technology.
People, process, and technology
People, process, and technology is a fascinating example of a triumvirate because it has all the challenges that real triumvirates had in ancient Rome. In a conceptual triumvirate, each of the three would have equal power. This is rarely the case in the real world, and people, process, and technology is no different. While the three should be equally important and command equal attention from information security architects, that is not what happens. By far, more time, effort, and resources are spent on technology than people and process. An overreliance on technology causes many of the problems we see in information security. Few technologies can protect against modern threats without the people and processes necessary to maximize the value of the technology.
The people aspect of cybersecurity gets the second most attention and resources in most information security programs. Most security leaders know that they need people to make their programs successful. However, due to the global cybersecurity talent shortage and the pace of technology change, it is more difficult than ever for organizations to hire, train, and retain the people they need to optimize their programs. Service providers, including Managed Security Service Providers (MSSPs), help fill the void, and many organizations are outsourcing security expertise out of necessity rather than desire.
The portion of the triumvirate that is often overlooked is the process section. Process is critically important, but it is often an afterthought. Most people would prefer a multiple-choice test over an essay test if given the choice. Technology selection is a multiple-choice test. A person can look at the market and choose the technology they think is best suited to solve their problem. People selection is similar. In good times, you post a job opening and you get a list of applicants. Once the initial screening process is complete, you essentially have a list of qualified candidates to choose from. Process creation is an essay exam. You must build processes to solve complex and multifaceted problems with few guidelines. It requires creativity and critical thinking. Many organizations do not focus on process because doing so is difficult.
Looking at security through the lens of people, process, and technology is useful when evaluating a program to compare how well the programs are built in each area. The next triumvirate looks at security through a different lens. Instead of defining the elements necessary to be successful in information security, confidentiality, integrity, and availability is a triumvirate designed to define information security through the lens of what the program is designed to accomplish.
Confidentiality, integrity, and availability
Confidentiality, integrity, and availability focuses on the three primary objectives of a security program and all three revolve around information. Otherwise known as the CIA triad, it speaks about the confidentiality, integrity, and availability of information. Every information security technology or program is designed to protect against threats to one or more of the three.
Confidentiality deals with ensuring that only authorized people can view sensitive information. Information protection solutions are designed to protect against attacks on the confidentiality of information. The most common way confidentiality is breached is when information is stolen or when unauthorized parties gain access to systems.
Integrity ensures that information is not modified by unauthorized parties. The Solarwinds attack is an example of what can happen when integrity is compromised. Solarwinds customers thought they were updating legitimate software, but the integrity of the software had been compromised by a threat actor.
Example Case: Solarwinds
Solarwinds is an IT software company that provides monitoring tools for many organizations around the world. Solarwinds customers saw what appeared to be a routine update from Solarwinds for one of their popular products. However, the update was not routine, and it was not created by Solarwinds. It is believed the Russian intelligence agency compromised Solarwinds' network and planted malicious software in the update that allowed them to compromise any Solarwinds customer who updated their software. As customers applied the update, which they believed came from Solarwinds, the attackers gained access to systems.
This attack was very sophisticated and highly intelligent. Rather than trying to compromise very well defended networks by using vulnerabilities, they chose to compromise a softer target that had access to their target networks as well as many other networks around the world. This is similar to the idea that caused the target breach through the compromise of an Heating, Ventilation, and Air Conditioning (HVAC) vendor, but at an exponentially larger scale, since Solarwinds was a vendor to thousands of organizations, including national governments.
This attack is devastating for information security professionals. It is difficult for a company to have a deep understanding of the security practices of all their software providers. Also, if people don't trust updates, they will update more slowly as they verify that no malicious software is contained in the update. That means they will be vulnerable for longer, and the time between discovering a vulnerability and patching that vulnerability will lengthen. This gives attackers of all kinds a larger window of opportunity. The Solarwinds attack shows that attacks against integrity are uncommon but can have devastating consequences that reach around the globe and change the way we think about best practices, such as patching systems (Temple-Raston, 2021).
Other integrity attacks include modifying information in a system for some kind of gain. An easy-to-understand, although highly unlikely, example is if I were to break into systems belonging to a financial institution and modify the balances in my accounts or credit cards. Ensuring the information that is in the systems is accurate and has not been tampered with is the goal of the integrity portion of the triad.
Availability deals with ensuring information or systems can perform their intended function. The classic attack on availability is the Denial of Service (DoS) attack. A DoS attack is when an attacker floods a legitimate service with so many requests that it cannot process legitimate requests. This type of attack is often used to take down websites and often uses bot networks in what is known as a Distributed Denial of Service (DDoS) attack. Ransomware attacks are also attacks on availability. The attacker denies legitimate access to files until a ransom is paid.
You could evaluate an information security program holistically by classifying technologies and countermeasures based on whether they were designed to protect the confidentiality, integrity, or availability of information or systems. The next triumvirate we will explore is people, data, and threats.
People, data, and threats
People, data, and threats is a new triumvirate that is gaining traction as a lens through which we can view information security. This triumvirate deals with the indicators that can help an organization identify anomalous activity.
The people element of cybersecurity deals with human behavior analysis. This portion is important because it helps identify insider threats, which have been a blind spot for organizations for many years. In the modern world, people work from anywhere and the information they access is not often located in a corporate-owned data center. As a result, the need to identify imposters and insider threats is magnified. Human behavior analysis helps you to understand the patterns of the people that access information and systems. Behavior analysis is not focused only on insider threats, though. Behavior analysis is an effective way to spot imposters using compromised accounts and may be used to highlight users who need additional training before they accidentally expose data or systems.
Data deals with the need to distinguish between the movements of sensitive information and commodity information and to apply selective controls based on the sensitivity of the information. Not all information is of equal value or equal risk to an organization. Some types of information are necessary to perform the intended business function but represent residual risk. Examples could be health-related information for a hospital. The hospital could not provide the necessary services without the health-related information, but the information itself is not likely to be monetized by the hospital. Other types of information allow an organization to profit from its exclusivity. For example, an innovative business practice or trade secret offers an opportunity for increased revenue and profitability. If others had access to this information, it could result in diminished financial performance. In both cases, protecting that information is critical.
Threats deals with internal and external actor groups and understanding the ways they are likely to attack and the information they will likely target. Threat data alone is rarely meaningful. However, understanding specific threats that are likely to target a specific organization or type of data can help you design effective countermeasures and build effective monitoring systems.
Now that we have established some lenses that can be used to evaluate information security programs, we will explore some of the challenges associated with traditional security models in the modern world.
Challenges with the traditional information security model
Traditional security models often are techno-centric and do not use the security triumvirates discussed previously. Instead, they focus on the technology used and therefore are vulnerable to change. With the current pace of change in the technology landscape, the shelf life of a techno-centric model is shorter than at any previous time in history. It is said that technological change is a flywheel, and we are likely to see a perpetually accelerating pace of change. As a result, techno-centric models don't work.
For decades, there has been a pendulum of trends in information technology swinging between centralized and decentralized infrastructures. Mainframes with terminals were a centralized architecture. All the computing power was in the mainframe, and the terminal was used only to access the mainframe. With the advent of personal computers and laptops, processing power was increasingly decentralized. The cloud computing revolution was a shift back toward a centralized infrastructure. Current conversations about edge computing are conversations about shifting back to a decentralized infrastructure. This pendulum continues to swing faster. Any frame of reference that is specific to an information technology strategy will continue to have a limited shelf life.
However, any of the security triumvirates can be applied in either a centralized or decentralized IT architecture. Effective security programs must be flexible and resilient by building their foundation on timeless principles rather than tactics and technologies. To underscore the fallibility of a security program built on current technology, we will next talk about the pace of technological change.
The Pace of Change
Famous futurist Ray Kurzweil predicted in 2001 that change is exponential and as a result, we will not experience 100 years of change in the next century, but rather 20,000 years of progress at the 2001 rate. It is difficult to comprehend how much change that would be, but most people who study technological change would agree it has never been linear in human history. Technological advancement has been accelerating throughout history. Here are some examples highlighting the pace of change in the new millennium.
The first smartphone with a touch screen and mass-market appeal (iPhone) was released in 2007. Now, the smartphone is the center of most people's worlds. It is difficult to imagine life without them. In some cases, governments have identified smartphone access as a human right, ensuring even the poorest of their citizens have access to them.
In the 1990s, the most popular storage devices were 1.44 MB floppy disks. The average base-level smartphone now has over 177,000 times the storage capacity. People rarely use physical devices to store information, though. Cloud services offer virtually unlimited storage for most people. In the case of social networks, people can use that storage for free, although they must trade access to their personal information to use the service.
In 2005, Google Maps was launched. Before Google Maps, people had to either know where they were going, or print out turn-by-turn directions. Now, most people use their phones to navigate to most destinations.
In the year 2000, the average household with high-speed internet was running at 56k speed. In most metropolitan areas, gigabit internet is widely available. The modern household download speeds are over 17,000 times faster than they were in the year 2000.
The Apple iPod was invented in 2001. While it was not the first portable MP3 player, it was the one that became popular enough to change the way most people purchased and stored music. Before 2001, people would carry large books of CDs in their cars, and people working out who wanted to listen to music had to carry a portable CD player that was prone to skipping. If someone wanted to change the album they were listening to, they would have to remove one CD and insert another. People paid for music on a per-album basis and subscription services for both music and movies did not exist. Now, most people have access to millions of entertainment choices through a monthly fee using services such as Netflix and Apple Music.
The pace of change around us makes it easy to lose perspective. All indications are that the pace of change is increasing and will continue to increase exponentially. Therefore, being flexible and adaptable to change is a key trait if a person wishes to be successful in any endeavor (Hammond, 2020).
Next, we will discuss a discipline that is critical to an information security program, but difficult to execute effectively: protecting information.
Protecting information
I have dedicated most of my adult life to protecting information. I believe that the exclusivity of information is the bedrock of the Western way of life. Without the ability to protect and profit from ideas, you cannot have individual freedom and entrepreneurship. Without the ability to protect a person's identity and creditworthiness, you cannot have an efficient consumer economy. Many organizations run information security programs that focus on everything except protecting information. Many security teams are so focused on systems, vulnerabilities, and threats that they forget the general premise of what they are trying to accomplish. All the people, processes, and technologies that make up an information security program should be focused on protecting the confidentiality, integrity, and availability of information.
A core part of building an effective information security program is to value the information you are protecting. There is an expression I first heard from my long-time CEO Steven Drew that says, You shouldn't spend a dollar to protect a nickel. That sounds obvious, but many organizations deploy expensive security controls without ever assigning value to the information they are trying to protect. If that is the case, how do they know if they are making good investments? I am not naïve, I know it is difficult to create a return-on-investment calculation for security investments, but it is possible. I will give one example of an approach, but there are many possible ways to value information.
I like to use a valuation technique for cost-benefit analysis similar to how an insurance company would gauge risk and risk mitigation for natural disasters or fires. Essentially, the exercise is designed to predict potentially damaging events related to a threat of a data breach in this example. It is important to identify the cost of a single event. In many cases, this would be the cost of a specific record being lost. In this example, there is third-party research, such as the Ponemon Cost of a Data Breach study, that can help value a record. In other cases, such as intellectual property cases, it is more difficult to determine an absolute value, but it is possible to estimate. Then, the exercise would ask participants to estimate how many records would be lost if nothing were to be done. It is generally expressed in the number of records lost per year. Sometimes, the number could be less than one if the event were to occur less than once per year. Then, the cost per record can be multiplied by the frequency to calculate an annual risk exposure in financial terms. The equation could be expressed like the following:
Annual Risk = Financial Risk of a Single Event x The Number of Times it Would Occur (Annually)
Then, the organization can run the same calculation, assuming the proposed countermeasure is being put in place. The difference between the two calculations is the benefit side of the cost-benefit analysis. Is this an exact science? No, but it is better than making no effort to scrutinize security investments.
What would happen if this level of scrutiny was applied to information security investments? I think there would be more of a focus on information protection programs and less of a focus on programs and technologies that are more exciting, but less financially consequential. Protecting information would have the highest return on investment for most organizations.
Now that we've discussed why it is important to protect information, let's talk about why protecting information is difficult.
Challenges of information protection
Information protection is difficult. There is no technology you can buy and deploy that will automatically protect your information. Data Loss Prevention is a great example. One of my early mentors in the space told me that this is not a technology tool, it is a business tool that is facilitated by technology. That statement has proved itself accurate through my years of experience. Technology deployment is easy. It is more difficult to align with business unit leaders to define how information should be used in an acceptable manner and tune the technology to find any deviations from those acceptable business processes.
Modern information protection tools are more powerful than early Data Loss Prevention technologies, and the need to coordinate with business units to define normal and acceptable behavior is more necessary than ever before. With increasing visibility into the behaviors that lead up to an information exfiltration event comes the need to have a deeper understanding of normal behavior for a business unit or role. Understanding these behavior patterns and making a qualitative analysis in near real time is an interesting opportunity for automation in information protection as well. However, effective automation in this space requires capturing and analyzing behavior patterns. Even if that technology existed, it would still be critical to define acceptable behavior by working with business units to understand what should be happening.
It is difficult to protect information. It is much easier to deploy technology such as an antivirus or Intrusion Detection Systems (IDS) because there is little process design and discovery necessary. However, even though it is difficult to protect information, it is a critical capability for organizations to build.
Protecting information is a critical capability
We live in the information age. Information drives the economic engine of most organizations. There are countless articles naming data as the world's most valuable commodity, calling it the new oil. Yet, most organizations outside of Silicon Valley have little insight into the value of the data they hold.
In most organizations, the only way data or information is assigned a value is based on the cost of a data breach. While it is important to understand risk exposure, it is more important to understand the value of information holistically. What types of information are necessary to generate revenue or operate your business? Of those information types, which are only valuable if they are kept private? Of those information types, how much revenue do they contribute to? These are key questions to answer to properly value information.
It is no surprise that organizations that have not valued their information struggle to protect it. If you don't know what to protect, why you should protect it, or what the consequences are if you don't, it is difficult to set objectives for an information security program. Many organizations that do not have the ability to value their information rely upon regulations to tell them what to protect. It is good to comply with regulations designed to protect information. In my view, those regulations serve a necessary purpose in society and the economy. However, those regulations are designed to protect information the loss of which could harm the public or the economy through financial fraud or identity theft. Those regulations are not designed to help an organization protect information that they use to generate revenue or maintain a competitive advantage. Like many other aspects of business, developing and maintaining a competitive advantage using information is the sole responsibility of the organization.
For more than a decade, I have been helping organizations define the information that's important to them and build a strategy to protect it. More than 90% of the organizations I have worked with have intellectual property of some type that can be tied directly to revenue-producing operations. Intellectual property is not just patents, trademarks, and copyrights. Business processes, customer lists, and trade secrets are also intellectual property. While patents, copyrights, and trademarks have legal protections that preclude others from using them against their owner, other types of intellectual property do not, and those types of intellectual property need to be protected more.
To protect data appropriately, you must understand how it flows through the environment during the normal course of business. The best way to do that is to map data flows in the context of an information life cycle.
Mapping data flows
One of the most important ways to protect information is to understand how it should flow through your environment. There are different ways to visualize the information life cycle. The following diagram is an easy way to think about it:
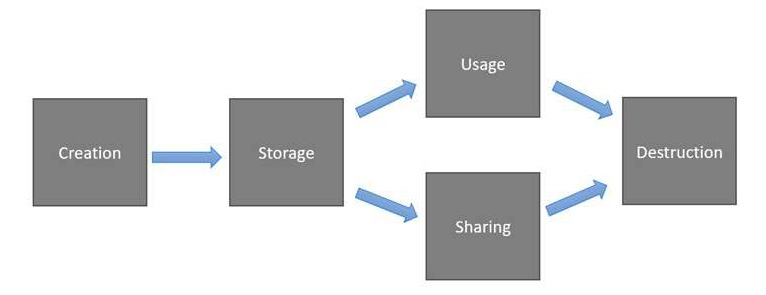
Figure 6.1 – Simple information life cycle
The idea behind mapping data flows is to map how data should move throughout an environment. This distinction is important because an organization that only maps data flows and does not monitor them is naïve. I have never seen an organization that can map its data flows so well that when monitoring is put in place there are no deviations from defined authorized behavior. Monitoring and enforcement are key; however, data flow mapping allows an organization to define its information protection rules and communicate with employees handling sensitive information effectively. Communicating processes and procedures with end users is a foundational element of an effective security program.
Next, we will spend some time defining each stage in the cycle, beginning with creation.
Information creation
Creation refers to the origination of the information in an electronic system owned or operated by the organization. All information an organization controls entered its environment at some point. That point can change based on the information type. For example, intellectual property may be created in a literal sense. It did not exist yesterday, but a member of our organization created it today. Other types of information, such as health data, may be provided by a customer using a form. Financial data, such as credit card data, may be captured at a point-of-sale system. In any case, information and its associated duty of care have a starting point.
Understanding these starting points is critical because as soon as that information enters the environment, there is an implied duty to protect it. However, you cannot protect what you don't know exists. Controlling how information enters the environment becomes very important. Every company that collects sensitive information from customers or partners should have a well-defined process for information collection, and controls to ensure information cannot leak into the environment through other channels. Common examples are customers sending personal information through email or ticketing systems designed to solve problems containing sensitive information. In the case of intellectual property, organizations must define who might create intellectual property and what the process will be if they do. For example, I may not be able to define the next product an automotive engineer creates, but I can probably surmise who will create it, what the file type will be, and where it will be stored. If I cannot define that process, it will be difficult to understand what intellectual property exists and therefore protect it. Protecting intellectual property is difficult, but it is not impossible. The reason most organizations struggle is they cannot define the property or the process of how it is created. This is another example of why security cannot operate in a silo.
Next, we will discuss the next logical step, which is information storage.
Information storage
Once information is created, it must be stored somewhere. This is obvious. However, the method and location of information storage are critical. Physical information was easy to control. Copy machines notwithstanding, data could be moved, but did not often propagate. Digital information is very different. It is often copied as it is moved, and it is not uncommon for hundreds of copies of a single piece of information to exist.
Many organizations can define a location where sensitive information is stored. Most cannot define all locations where sensitive information is stored. This makes powerful technologies such as File Activity Mentoring (FAM) less effective. In the past, monitoring the storage of information was very difficult. Essentially, an organization would have to scan all its storage repositories to generate a report of where sensitive information was located. Those scans could take weeks or months. By the time the scan was completed, the results were outdated, and even the best organizations were constantly chasing the problem. It was very difficult to get ahead. These challenges put tremendous pressure on the data destruction discipline we will discuss later and directly led to over-retention, which indirectly led to regulations such as the GDPR.
Modern technologies such as Cloud Access Security Brokers (CASBs) using Advanced Programming Interface (API) capabilities and some Cloud Security Posture Management (CSPM) solutions allow an organization to monitor the storage and movement of sensitive information in cloud repositories in near real time. There was a time where people were reticent to move information to cloud services because many of the security controls they relied upon were not available. At this point, there are many powerful security tools in the cloud that are not available on-premises. It is important to understand, however, that information in cloud services carries different responsibilities and risks, which we will cover in the Securing cloud workloads section of this chapter.
The determination of how and where information should be stored, whether it should be encrypted at rest, and who should be able to access it should be an intentional decision made by the organization.
A great example is a company I was working with that color coded data repositories based on the most sensitive information they could contain, and then built its access models based on that information. A red data repository contained information that had access restrictions based on government regulations, meaning some employees were legally not allowed to access that information. An orange data repository contained sensitive information but could be accessed by any employee with a need to know in accordance with least privilege. Green data repositories did not contain sensitive information. The company then would scan all orange repositories to ensure there was no red information, and scan green repositories to ensure there was no orange or red information. This approach is ideal in my opinion because it covers several best practices and includes recurring enforcement.
After information storage, there is a natural dovetail. The information will be used internally or shared with a third party. However, for the information to be valuable, someone needs to use it in some way. Therefore, we will start with defining the authorized use of information.
Information use
Understanding the use of information is critical. Many organizations focus solely on who should be able to access information, and once a person is granted access, there are few restrictions placed on what that person can do with that information. The problem is that malicious insiders and compromised accounts can then steal that information with impunity. It is important to monitor how sensitive information is used. However, doing so well requires the discipline to define which data is important and how it should be used.
There are roles and regions where monitoring all employee behavior is acceptable. In most jurisdictions, it is either required by law or expected by custom that such intrusive monitoring is only applied with just cause. It is preferable to define what is authorized with respect to how information should be used in the course of normal business and to alert on deviations from that behavior. Doing so requires the security team to map the use of information with the business unit. If you don't know what normal behavior is, how can you identify abnormal behavior? There are few cases of information theft where the behavior did not cross the threshold of obviously abnormal, but the question is whether the organization had the necessary controls in place to identify that abnormal behavior.
Next, we will talk about information sharing.
Information sharing
Information sharing is often necessary to maximize the value of information. However, when information is shared, the organization often loses visibility of the information and control over how it is subsequently used and shared. For types of information where that visibility and control are necessary, there are tools that allow an organization to retain those rights. However, deploying them can be time-consuming, costly, and onerous. Therefore, it is important to apply those controls only when necessary.
For some types of information, contractual agreements that govern how the information can be used are deemed sufficient. It is important to understand the information, the risks, and the legal protections in place to define the authorized methods of sharing the information. It is then critical to ensure the monitoring and enforcement capabilities are in place to restrict other methods of sharing. In the modern world, sharing has become very easy. There are many methods a user can employ to share information.
Like water and electricity, most users will take the path of least resistance. An effective information security program focuses on making it easy for users to share information properly, and to make it difficult for users to share it improperly. It is often infeasible to make it impossible to improperly share information. For example, in all but the most restrictive environments, there is little to prevent an employee from taking a picture of a computer screen with a phone and texting the picture to someone else. However, it is easier to put the file on a cloud service and invite a collaborator, unless you make it difficult to do so. The best way to guide behavior is to apply resistance to things you don't want to happen and eliminate barriers to productivity using authorized methods. Users will learn where the resistance is and naturally avoid it in most cases. Shaping behavior in this way can reduce risk considerably.
Finally, we will talk about information destruction.
Information destruction
Information destruction deals with the inevitable point in time when information has outlived its usefulness. For many years, there were no regulations that mandated that information should be destroyed. At the same time, storage became cheaper with every passing year. There were regulations that mandated that information should be stored for a minimum amount of time. The response was that most organizations didn't delete anything. The result is that for most organizations, retaining information with no business value is the largest pool of residual risk in their environment. The following example case demonstrates this problem well.
Example Case: Sony Pictures Entertainment
In 2014, Sony Pictures Entertainment's systems were breached by a group calling itself the Guardians of Peace. The group, widely believed to be backed by the government of North Korea, stole large volumes of information from Sony servers. Most of the information was used to try to embarrass Sony Pictures Entertainment. Emails were released that detailed conversations between executives making disparaging remarks about each other, and important people who worked with Sony Pictures Entertainment, such as high-profile actors and directors. The motivation for embarrassing Sony Pictures Entertainment indicates it is unlikely a criminal organization was behind the attack. Most of this information had no business value. The question is, why would they have it? The Sony Pictures Entertainment case highlighted the residual risk carried by most organizations because they over-retain information that has no value. This case highlights the need for an effective data destruction policy.
While the information released was embarrassing, the business disruption was catastrophic. Sony Pictures Entertainment lost all faith in their electronic systems and took most of them offline. Teams resorted to communicating with each other using written notes and whiteboards. For weeks, the organization was crippled and forced to operate its business in the modern world without access to modern technology. The attack was devastating and highlighted the importance of an effective business continuity plan (VanDerWerff, 2015).
Most of the damaging information from the Sony Pictures Entertainment data breach had no business value, but still presented a risk to the organization. The GDPR mandates that personal information that has no business value and no legal retention requirement must be destroyed. This is important because it means that organizations must have a data destruction and certification process in place. Also, it requires that organizations understand information storage and information flows so they can be sure all the copies of the information are destroyed. This sounds easy. In practice, it is very difficult and requires a change in the way organizations think about information and risk.
Once every stage of the life cycle has been defined, you will understand how data should be used in an authorized manner. Now, you can build an information protection program that looks for anything outside those allowed practices. In some cases, the practice may be necessary but was not defined up front. This is fine as programs tend to mature. However, starting with a defined authorized behavior is the most effective way to build an information protection program. I should emphasize that defining authorized behavior and detecting everything else is the most effective way to build any security control. The number of bad things that could happen is infinite. The only thing that is possible is to define what should happen and then to put in controls that detect deviations from those authorized processes.
Successfully establishing a program that understands authorized interactions with information requires input from departments outside information security and ongoing cross-functional collaboration.
Cross-functional collaboration
Cross-functional collaboration, where people from multiple business functions work together to achieve a common goal, is a feature of the most successful information security programs, but it is rare. Few organizations are sufficiently committed to information security to dedicate resources from business units to advance the security program. Few information security programs have the discipline and maturity to make good use of cross-functional collaborators, even if the will exists. However, since cross-functional collaboration improves the security program significantly, it is a worthwhile pursuit to build it into the program, at least up front while objectives are being defined.
Information protection specifically is largely dependent on this collaboration. I was told by one of my early mentors that information protection is not a technology solution, it is a business solution facilitated by technology. Rules governing the creation, use, storage, sharing, and destruction of information are business rules. We simply use technology to enforce them. When framing the problem that way, it is natural to ask for business unit involvement.
If you are responsible for an information protection program, one of your first steps should be to get buy-in from leadership and start building your cross-functional collaboration workflows. These cross-functional collaboration teams will be critical in identifying information, the proper sharing of information, and other items related to keeping information safe in your organization. Now that we understand how and why we should protect information, we will turn our attention to securing networks and workloads.
Securing networks and workloads – past, present, and future
Securing networks and workloads is a heading that is intentionally vague. The methods we use to transport information and who owns them have changed significantly since the early 2000s. Then, people's access to high-speed internet was mostly provided by their employer, who owned the infrastructure, the path to the internet, and the internet circuit itself. Most people either physically came into an office or used a Virtual Private Network (VPN) to access the network remotely. In either case, the organization owned the path to the internet and could put controls in place to monitor its use for a variety of reasons. In the modern world, most people have multiple methods of high-speed access to the internet. Home internet download speeds are often higher than the speeds at work. Most people in developed countries have high-speed internet access on their mobile phones. Many workers never come into their office, and VPN connections are used only for access to specific resources. Organizations have lost control over the path their teams take to the internet.
Workloads have changed as well. In the early 2000s, the term "workload" did not exist because there was no need for it. Workloads were run primarily on physical servers. The first virtual server technology was brought to market in 1999, but virtual servers behaved like physical servers from a security standpoint. Servers were deployed in environments owned by the organization. Many owned and operated large data centers full of servers. Others used colocation facilities, but most organizations had complete control over how systems were built and how information was stored, processed, and transmitted. According to a recent report, 85% of organizations had most of their workloads in the cloud in 2020 (AllCloud, 2020). This means most workloads are no longer owned by the organization; they are renting computing power on demand from others. While this makes sense from a business perspective, it introduces new challenges to security teams.
Next, we will explore how to secure networks.
Securing networks
Securing networks is increasingly challenging when the organization no longer has ownership of the route to the internet and, often, the device being used to connect or the workload the user is connecting to. Further, modern protocols such as Transport Layer Security (TLS) 1.3 make it more difficult to intercept and inspect traffic in transit. TLS is a protocol that ensures traffic is encrypted. If you were to browse to an internet site that starts with the prefix https, you would be using TLS to access that site. Most modern sites use TLS. The change to TLS 1.3 made it difficult for traditional approaches to network security to operate. Traditionally, organizations would use a proxy server. Any user who wanted to access the internet would go through the proxy server, which would read the traffic and the destination and decide whether to allow the transaction to happen. The problem is that this is identical to a Man-in-the-Middle (MitM) attack. TLS 1.3 makes MitM attacks more difficult, which in turn, makes it more difficult to execute an effective proxy strategy for network security.
In response, many organizations are turning toward cloud-based Secure Web Gateway (SWG) solutions. However, when users are accessing the internet through their own networks and on their own devices, it is very difficult to force them to use an SWG. Therefore, modern SWG controls are a partial solution. It is part of a company's duty of care to ensure that if they are providing access to the internet, the access is secure. However, gone are the days where a company could rely upon SWGs as a comprehensive control governing internet access and data movement.
Securing cloud workloads
In Chapter 1, Protecting People, Information and Systems – a Growing Problem, we introduced the shared security model for cloud computing environments. We are going to revisit that model as we focus on solutions to secure cloud environments. Cloud computing is a centralized IT model. History tells us we will move back to a decentralized model in the future. The most discussed decentralized IT model for the future is edge computing. When you hear edge computing, think of a transition back to a decentralized model. However, the dominant IT model currently is the centralized model broadly referred to as cloud computing. Cloud computing is different than previous centralized models in that the actual server infrastructure and data centers are owned by third parties. This idea of outsourcing workloads is new in the history of computing. However, when discussing edge computing, while decentralized, it is likely that it will be offered as a service, meaning the idea of outsourcing workloads does not appear to be a passing phenomenon. Why is this important? Because it means that shared security models are also here to stay. A shared security model means there are two or more entities responsible for the security of a workload. Misunderstandings of who is responsible for what, especially on the customer side, are the root cause of most data breaches involving cloud environments.
Therefore, understanding the following model is critical for securing cloud workloads. Having and understanding a similar model any time you are consuming anything as a service is similarly important:
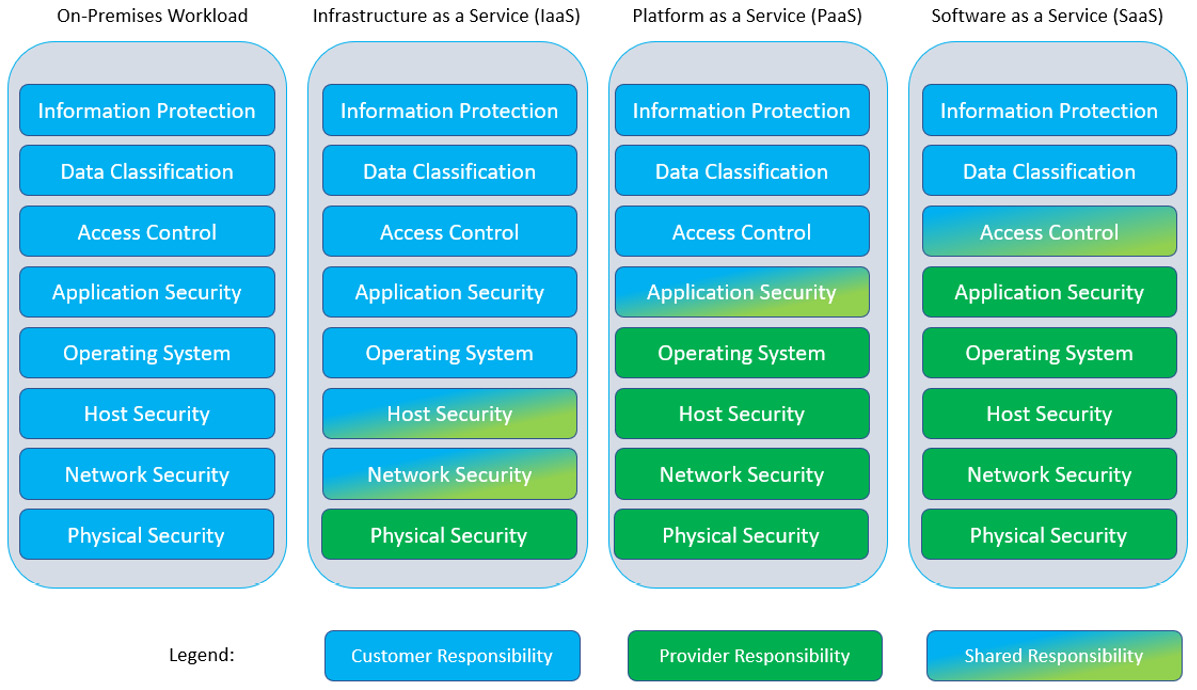
Figure 6.2 – Shared security model for various cloud computing environments
As you can see, depending on which type of cloud computing you are consuming, there are different responsibilities for you and your service provider. Software as a Service (SaaS) is the most widely used and understood model. In this model, the cloud provider provides the underlying infrastructure, compute power, and application to you as the consumer, and you simply use it. If you have ever used Salesforce, Box, OneDrive, Exchange Online, or Gmail, you are using SaaS. Since the provider is in control of most of the stack, they have most of the responsibilities. However, even when consuming SaaS, you are responsible for protecting your information, classifying it if necessary, and controlling who has access to the environment and what permissions they have. In fact, in any model, you cannot outsource responsibility for these disciplines. The reason is that each of them requires some knowledge of your business and what is allowed. There is no way for the provider to know who should have access to a specific document, for example. Cloud Access Security Brokers (CASB) were built specifically to solve the SaaS challenge of providing capabilities to control these three things across many SaaS applications that exist.
Infrastructure as a Service (IaaS) is almost completely the opposite of SaaS. IaaS simply provides computing power on demand. You as the consumer decide what operating system to deploy, what applications to install, and what the intended purpose of the workload is. If you have ever worked with Amazon Web Services (AWS), Google Cloud Platform (GCP), or Microsoft Azure, you are probably consuming IaaS. I say "probably" because all three offer services that are not IaaS, which we will discuss in the next paragraph. In IaaS environments, the provider is responsible for the physical security of their data centers, and they share responsibility with the consumer for securing the networks and the hosts themselves. Everything else is the consumer's responsibility. Broadly, Cloud Workload Protection (CWP) solutions are designed to help customers meet the security needs of an IaaS environment.
Platform as a Service (PaaS) offerings are in between SaaS and IaaS, which leads to confusion. Also, many popular PaaS platforms are offered by companies better known for their SaaS or IaaS offering, adding to the confusion. For example, Salesforce is a popular SaaS application. The underlying Force.com platform, which all Salesforce customers have access to, is a PaaS offering. AWS is IaaS. However, services on the platform, such as Beanstalk, are PaaS offerings. It gets very muddy. Solutions such as Cloud Security Posture Management (CSPM) are designed to help customers meet their PaaS responsibilities. However, it is difficult for customers because most are using PaaS, but most think their PaaS platforms are actually IaaS or SaaS.
The best way to secure cloud workloads is to create an inventory of every cloud service consumed in the environment, classify it as SaaS, PaaS, or IaaS, and define strategies and tools to secure each environment. Most organizations do not have this kind of cloud computing register, but they should. Most breaches involving cloud computing are the customer's fault, and most of those breaches stem from a misunderstanding of the shared security model. The tools are also purpose-built. For example, a CASB solution can help you discover what cloud services are in use, and even have connections to services such as AWS, which is IaaS, but the controls are built for the responsibilities you have in an SaaS environment. Therefore, using a CASB to secure AWS leaves major gaps in your responsibilities in the shared security model.
Next, we will discuss how we can secure identities and grant them access.
Securing identities and granting access
Securing identities and granting access are critical functions for a security program. It is always your responsibility to grant access to systems and information to identities and to build controls to ensure the people requesting access through a login are who they say they are. We discussed Multifactor Authentication (MFA) in Chapter 4, Protecting People, Information, and Systems with Timeless Best Practices, so we will not discuss it in depth during this chapter. However, we will briefly discuss the importance of verifying identities.
Verifying identities
It is important for every organization to have the ability to identify who is requesting access and to verify they are who they say they are. In a world where most people access resources remotely, and many resources are accessible from anywhere because they are cloud based, it is more important than ever to verify identities. Also, with the prevalence of password theft, MFA is a critical capability. Before a user is granted access to a system, we must have the capability to identify that user and be sure the user is not an imposter.
Next, we need to grant access to the information or workloads they must access.
Granting access
Once we can identify the people who are requesting access, we need to grant that access. In Chapter 4, Protecting People, Information, and Systems with Timeless Best Practices, we discussed the concepts of least privilege and need to know. Granting access is where those disciplines come into practice. There are two underlying causes of over-permissive accounts in most environments, fear of business disruption and credential accumulation.
Fear of business disruption is the idea that it is better to give a person more access than they need rather than less. The theory is if I am denied access to a resource, the security team has harmed business productivity and I need to request access before I can accomplish my job function. While understandable, this practice leads to an unacceptable level of risk in my opinion. We should grant access to the resources we know a user will need to perform their intended function. Too often, we grant permissions to all the resources a person might need. Then, if that account is compromised, the attacker has access to more resources than they should, and the damage of the breach is magnified. While it may be a minor annoyance to the end user to have to request access to a resource when they are using it for the first time, the risk posed by over-permissive accounts is much greater.
Example Case: Tesla
Tesla is one of the most innovative companies in the world, led by an outspoken innovator named Elon Musk. Elon has been vocal about instances where he believed employees were stealing from Tesla, which has provided a window into insider intellectual property theft that was rare prior to Tesla's disclosures. Intellectual property theft by insiders is not rare. However, most companies don't have the controls to identify it, and when they do, they rarely disclose the events publicly. The disclosures by Tesla provide security professionals a better ability to understand insider threats.
One such disclosure was made at the end of 2020. In December 2020, Tesla hired an engineer named Alex Khatilov. During the two weeks he spent as an employee of Tesla, Khatilov is accused of stealing more than 6,000 files that help Tesla automate its operations. It was said that these files had nothing to do with his job, but he had access to them and copied them to a SaaS service that he could access from his personal computer, and therefore exfiltrate. During the investigation, thousands of files were found, and it is difficult to determine if or how Mr. Khatilov used them.
There is a key lesson learned from this incident. If the files truly had nothing to do with Khatilov's job, why did he have access to them? If the proper controls were in place, Tesla could have stopped the files from being uploaded to Dropbox. It is clear that some of the controls were in place because the activity was detected. In general, Tesla does a great job of protecting its intellectual property and identifying when it is being stolen. It is important to remember that those who disclose many incidents compared to their peers, such as Tesla, are not inherently lax in their security controls. In most cases, the opposite is true. The most insecure organizations think they don't have a problem and don't have the capabilities to prove otherwise.
Tesla is a great example of monetizing intellectual property. Tesla accounts for about 2% of the United States automobile market, but has a total market capitalization, roughly translated to value, that's bigger than all other United States car manufacturers combined. Some of that can be attributed to Elon Musk's leadership, but much of it can be attributed to innovation and intellectual property (Houcheime, 2021).
Next, we will discuss permissions accumulation.
Permissions accumulation
During my time at InteliSecure, a cyber-security services company that I was with for over 10 years, I served in a variety of roles, and I was the poster child for potential credential accumulation. As I moved from operations to sales, to marketing, and eventually to the C suite, I needed access to different resources. I no longer needed access to other resources. In most organizations, I would be granted access to the new resources I needed, but my access to resources I no longer needed would not be removed. As a result, over time, I accumulated permissions that made my account over-permissive and made me a major risk to the organization. It is important to focus on what a user no longer needs when they change functions as well as the new permissions they need in their role.
It is more difficult than ever to verify identities and grant access properly. Next, we will discuss how human behavior analysis can help with both.
Human behavior
In most cases, I think the applications and effectiveness of machine learning and artificial intelligence capabilities are overstated. Behavior analytics is a notable exception. Behavior analytics is a capability that uses machine learning to analyze human behavior patterns. This application is perfect for machine learning. Machines are very good at recognizing patterns from large datasets, and that is exactly what behavior analytics is designed to do. There are many effective applications for behavior analytics, and it is one of the most promising new technologies in my opinion. It has a special role to play in both verifying identities and granting access. First, let's explore how behavior analytics can help us verify identities.
It is easy to impersonate a user by stealing their password. It is difficult, but possible to defeat MFA methods. It is nearly impossible to be successful in an attack without deviating from a user's normal behavior patterns. Once an attacker is in an environment, they will behave very differently from an authorized user because their objective is different from an employee trying to do their job. As a result, using behavior analytics to trigger a password reset or step-up authentication makes an attacker's objective more difficult to accomplish. Implementing this capability would frustrate and deter all but the most sophisticated and motivated attackers. It would also highlight insider threats because most become malicious, and when they do, they change their pattern of behavior. Next, we will discuss how we can use behavior analytics to combat over-permissive accounts.
Over-permissive accounts are a major problem because most organizations do not know what resources a user actually needs to perform their job function. With behavior analytics, we can analyze how a user leverages the permissions they have been granted. You could even set a policy that says all permissions that have not been used in the last 90 days will automatically be removed and the user must request them again if access is needed. This will immediately solve the over-permissive account problem. In some organizations, a shorter time frame may be appropriate.
Example Case: US Navy Warship Data
The story of a husband and wife trying to sell United States Navy submarine propulsion secrets is entertaining because of the methods they used to try to smuggle the information to people they thought were foreign agents. However, the case itself is sobering. In 2021, the Naval Criminal Investigations Service (NCIS) arrested a 42-year-old engineer and his wife for stealing Navy secrets and attempting to sell them to a foreign government.
As part of his job, the engineer had access to some extremely sensitive secrets about how the US Navy built propulsion systems for its nuclear submarines. The engineer stole documents related to these secrets and sent a sample pack of the stolen information to at least one foreign government. In a poorly translated email, he made it clear that he had secrets and he was willing to share them in exchange for payment.
The engineer was sent a $10,000 good faith payment and an arrangement was made for a meeting. When the meeting took place, the engineer and his wife agreed to hide an SD card containing the documents in a peanut butter sandwich and drop it at a mutually agreed upon location. The information was encrypted, and the agreement was made to provide the decryption key in exchange for an additional $20,000 payment.
Aside from the entertaining nature of the smuggling method, and the curiously low price demanded for such sensitive information, there are some lessons to be learned from this case as it relates to behavior analytics. This engineer was not stealing information and selling it to foreign governments his entire career. Based on the amounts offered for information that would take billions of dollars of research to re-create, he was not an expert in espionage. At some point, he went from an engineer doing his job to a malicious insider seeking to profit from the theft of sensitive information he had access to. Behavior analytics capabilities help detect those changes. While it has not been disclosed, there is a good chance this type of technology helped the NCIS identify this activity and intercede before the engineer was successful in making contact with an adversarial government (Osborne, 2021).
Behavior analytics is becoming an increasingly attainable capability for most organizations. Historically, the capability has been cost-prohibitive, but now technology has advanced to the point where most organizations could deploy these capabilities in a cost-effective manner.
Next, we will discuss securing endpoints.
Securing endpoints
Securing endpoints is another intentionally vague term because endpoints have changed. In the early 2000s, the only smartphone in wide use was the Blackberry, and that technology used a server that was controlled by the organization. Now, most employees have a smartphone that the organizations do not control or have visibility into. In most cases, that smartphone is at least as powerful as a laptop. An endpoint refers to any device that digitizes a user's intentions. This could be a desktop, laptop, tablet, mobile phone, video game controller, smart refrigerator, voice-activated personal assistant, and so on. As you can see from the brief list I was able to come up with off the top of my head, there are an exploding number of endpoints. Securing them has become exceedingly difficult. Further, most organizations do not own most of the endpoints in a user's life. This presents a major problem for security.
Traditional endpoint approaches are no longer a comprehensive control. There is no way for an organization to secure every endpoint a person will use to access their workloads or information. However, it is part of the organization's duty of care to secure the endpoints they issue to users, often using an Endpoint Protection Platform (EPP). Organizations can also exert control over cloud workloads to stipulate the security posture of any endpoint being used to access that environment. This type of control helps organizations secure the endpoint, which is a critical security capability. However, when organizations think about endpoint security, they must think beyond software controls and think creatively about what the rules should be with respect to endpoint security and what leverage points they may use to enforce those controls.
Summary
In this chapter, we have discussed frames of reference that you can use as a lens through which to view security that will help design controls regardless of how the world around you changes. You have learned about the core security disciplines of protecting information, securing networks and workloads, securing identities, granting access, and securing endpoints. You now have the tools necessary to create a security program to meet the challenges of the modern world and a prism through which to view the future as change inevitably comes. In the next chapter, we will turn our attention toward specific problems facing the modern enterprise, along with solutions to help meet those challenges.
Check your understanding
- Choose a security triumvirate and explain it in your own words.
- What are some of the challenges with the traditional information security model?
- What is the information life cycle? What are its stages?
- What is a workload?
- What are the three major categories of cloud services?
- How can human behavior analysis help secure identities and ensure only the proper access is granted?
- What is an endpoint? Can you name at least five different types of endpoint?
Further reading
- AllCloud. (2020). 2020 Cloud Infrastructure Report.
- Hammond, A. (2020, January 2). The 20 Biggest Advances in Tech Over the Last 20 Years. Retrieved from FEE: https://fee.org/articles/the-20-biggest-advances-in-tech-over-the-last-20-years/
- Houcheime, W. (2021, February 3). Tesla Experiences Internal Breach, Leaking Valuable Company Data. Retrieved from Security Boulevard: https://securityboulevard.com/2021/02/tesla-experiences-internal-breach-leaking-valuable-company-data/
- Northrop Grumman. (2013, April 8). Developing a Framework To Improve Critical Infrastructure Cybersecurity. Retrieved from NIST: https://www.nist.gov/system/files/documents/2017/06/02/040813_northrop_grumman_response_part2.pdf
- Osborne, C. (2021, October 11). FBI arrests engineer for selling nuclear warship data hidden in peanut butter sandwich. Retrieved from ZDNet: https://www.zdnet.com/article/fbi-arrests-engineer-for-flogging-nuclear-warship-data-hidden-in-peanut-butter-sandwich/
- Temple-Raston, D. (2021, April 16). A 'Worst Nightmare' Cyberattack: The Untold Story Of The SolarWinds Hack. Retrieved from NPR: https://www.npr.org/2021/04/16/985439655/a-worst-nightmare-cyberattack-the-untold-story-of-the-solarwinds-hack
- VanDerWerff, E. a. (2015, June 3). The 2014 Sony hacks, explained. Retrieved from Vox: https://www.vox.com/2015/1/20/18089084/sony-hack-north-korea
