CHAPTER 2: COBIT, ISO/IEC 20000 AND ITIL
While most will recognize and have in-depth knowledge of one or two of these service management philosophies, we thought it necessary to level-set not only the core structural information, but to also describe the improvement models that are integral to each framework.
Overview of COBIT5
COBIT (Control Objectives for Information and Related Technology) is a business framework for the governance and management of enterprise IT. With aspects in security, quality and compliance, its focus is not necessarily on how to execute a process, but rather what should be done to ensure proper control of that process. Therefore, you won’t technically implement COBIT from the bottom up, but use it as a tool to help you control processes from the top down as a part of a larger governance initiative.
Starting out as a tool designed for IT auditors to assist in the control of IT, it has grown into a model to assist with compliance requirements as well. It helps enterprises understand IT systems, and guides decisions around the level of security, risk and control that is necessary to protect assets through the leverage of an IT governance model.
By using stakeholder needs as the starting point for governance and management activities, COBIT offers a holistic and integrated view of enterprise governance and management of IT that uses consistent and common language. This framework has many rich capabilities, notably the introduction of GEIT (Governance of Enterprise IT) principles, increased focus on enablers, new and modified processes, the separation of governance and management, revised and expanded goals and metrics, and a new process capability model to name just a few.
There are several documents and tools to choose from in the overall COBIT product family. These can be found at www.isaca.org/cobit and include:
- COBIT 5, A Business Framework for the Governance and Management of Enterprise IT4
- COBIT 5 Enabler Guides
- COBIT 5 Enabling Processes
- COBIT 5 Enabling Information
- Other Enabler Guides to be developed
- COBIT 5 Professional Guides
- COBIT 5 Implementation
- COBIT 5 for Information Security
- COBIT 5 for Assurance
- COBIT 5 for Risk
- Other professional guides to be developed.
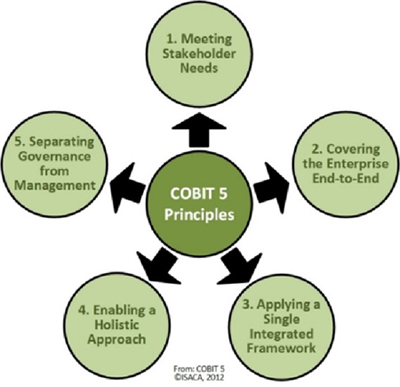
The building blocks of the COBIT framework are leveraged through the use of five principles and seven enablers (see Figure 1).
- Principles
- Meeting Stakeholder Needs
- Covering the Enterprise End-to-End
- Applying a Single Integrated Framework
- Enabling a Holistic Approach
- Separating Governance from Management.
Note that the Principle “Enabling a Holistic Approach” gives rise to the Enablers.
- Enablers (see Figure 2)
- Principles, Policies and Frameworks
- Processes
- Organizational Structures
- Culture, Ethics and Behaviour
- Information
- Services, Infrastructure and Applications
- People, Skills and Competencies.

At the core of any framework are processes. COBIT5 has 37 processes in five domains.
- Evaluate, Direct, Monitor (EDM) – includes processes that address stakeholder governance objectives, specifically value delivery and risk and resource optimization. Additional process activities stress the evaluation of strategic options, hence providing direction to IT. The process supporting the EDM domain include:
- EDM 1: Ensure Governance Framework Setting and Maintenance
- EDM 2: Ensure Benefits Delivery
- EDM 3: Ensure Risk Optimization
- EDM 4: Ensure Resource Optimization
- EDM 5: Ensure Stakeholder Transparency.
- Align, Plan & Organize (APO) – directs solution delivery (BAI) as well as service delivery and support (DSS). Specific activities focus on strategy and tactics and how IT can impact the achievement of business objectives. These processes define the management system for IT and include:
- APO 1: Manage the IT Framework
- APO 2: Manage Strategy
- APO 3: Manage Enterprise Architecture
- APO 4: Manage Innovation
- APO 5: Manage Portfolio
- APO 6: Manage Budget and Costs
- APO 7: Manage Human Resources
- APO 8: Manage Relationships
- APO 9: Manage Service Agreements
- APO 10: Manage Suppliers
- APO 11: Manage Quality
- APO 12: Manage Risk
- APO 13: Manage Security.
- Build, Acquire & Implement (BAI) – this domain provides the solutions based on the previously defined strategies and ensures the solution will support and enhance the business process. Change is also managed in this domain – again keeping the solution aligned with business objectives. The following 10 processes support the BAI objectives:
- BAI 1: Manage Programs and Projects
- BAI 2: Manage Requirements Definition
- BAI 3: Manage Solutions Identification and Build
- BAI 4: Manage Availability and Capacity
- BAI 5: Manage Organizational change Enablement
- BAI 6: Manage Changes
- BAI 7: Manage Change Acceptance and Transitioning
- BAI 8: Manage Knowledge
- BAI 9: Manage Assets
- BAI 10: Manage Configuration.
- Deliver, Service & Support (DSS) – receives the solutions and deploys the necessary functionality for the user community. The focus of DSS is on the delivery and support services including security, continuity, support services, and management of data and the environment. The processes include:
- DSS 1: Manage Operations
- DSS 2: Manage Service Requests and Incidents
- DSS 3: Manage Problems
- DSS 4: Manage Continuity
- DSS 5: Manage Security Services
- DSS 6: Manage Business Process Controls.
- Monitor, Evaluate & Assess (MEA) – monitors processes to ensure compliance as well as achievement of the necessary quality levels. Key areas within this domain include performance management, regulatory compliance, governance and internal control monitoring. Processes supporting these activities include:
- MEA 1: Monitor, Evaluate, and Assess Performance and Conformance
- MEA 2: Monitor, Evaluate, and Assess the System of Internal Control
- MEA 3: Monitor, Evaluate, and Assess Compliance with External Requirements.
These five domains support the separation of governance and management by aligning EDM with governance processes and BAI, DSS, and MEA with a typical Plan-Build-Run-Monitor approach. See Figure 3.
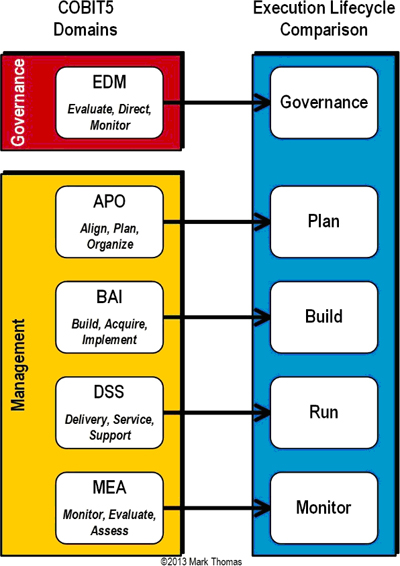
Figure 3: COBIT5 Domains to Lifecycle Activities
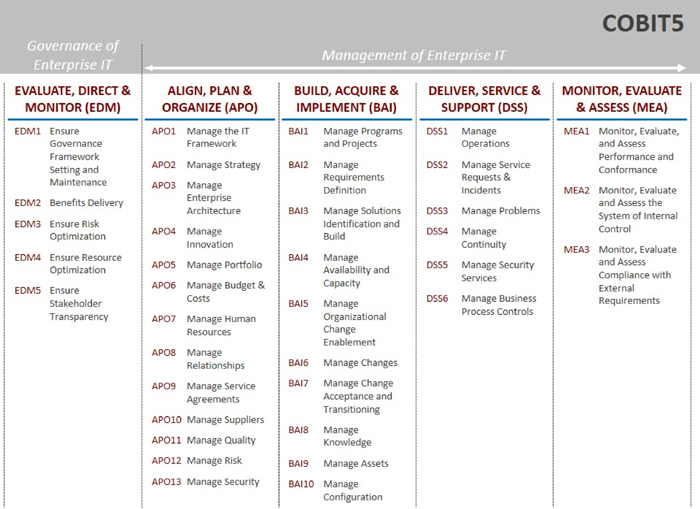
Table 1: COBIT5 Domains and Processes
ISO/IEC 20000-1:2011
The ISO/IEC 20000 family of documents define the international Standard for IT service management with a goal of establishing a common reference for IT service delivery. There are several parts to the Standard, which revolve around the auditable Part 1 (26 pages) and includes:
- Part 1: Service management system requirements
- Part 2: Guidance on the application of service management systems
- Part 3: Guidance on scope definition and applicability of ISO/IEC 20000-1
- Part 4: Process reference model [Technical Report]5
- Part 5: Exemplar implementation plan for ISO/IEC 20000-1 [Technical Report]
- Part 6: Requirements for bodies providing audit and certification of service management systems3
- Part 8: Guidance on implementation of service management systems for smaller organizations3 [Technical Report]
- Part 9: Guidance on the application of ISO/IEC 20000-1 to the cloud6 [Technical Report]
- Part 10:Concepts and terminology [Technical Report]
- Part 11: Guidance on the relationship between ISO/IEC 20000-1:2011 and related service management frameworks [Technical Report]7.
Simply, Part 1 defines the internationally accepted requirements for the Service Management System (SMS) which include the “…design, transition, delivery and improvement of services that fulfil service requirements and provide value for both the customer and service provider.”8
Developed originally as a UK national Standard (BS 15000), the early “edition” was a method allowing consistent measurement indicating compliance to ITIL ‘best practices,’ thus allowing organizations to declare themselves compliant. The international community quickly saw the benefit of BS 15000 and moved it through the process to create the international Standard, ISO/IEC 20000-1:2005. ISO/IEC 20000 continually improves following and driving ITIL improvements. Incorrectly known as the “ITIL Standard,” ISO/IEC 20000 is a service management product in its own right. It demands an integrated process approach based in the PDCA methodology across all aspects of the SMS and services. Combining the SMS with the PDCA drives value-driven service delivery, customer satisfaction and monitored, reviewed and improved services based on objectives and agreed measurements.
The unique aspect of ISO/IEC 20000-1 is the definition of a service management system. A service provider must “…plan, establish, implement, operate, monitor, review, maintain and improve an SMS” throughout the span of service activities (e.g. design, transition, delivery and improvement). Specifically, the SMS includes very clear requirements for management responsibility, governance of processes operated by other parties, document and resource management, and the explicit activities of establishing and improving the SMS following the PDCA methodologies.
The SMS provides the management foundation for the well-known service management processes divided into four main groupings:
- Service Delivery (Service Level Management, Service Reporting, Service Continuity and Availability Management, Budgeting/Accounting, Capacity Management, Information Security Management)
- Relationship (Business Relationship Management, Supplier Management)
- Resolution (Incident and Service Request Management, Problem Management)
- Control (Configuration Management, Change Management, Release and Deployment Management).
Lastly, there is an overall set of requirements for the design and transition of new or changed services. This set of requirements nicely defines the flow of activities beginning with planning for the new or changed service (e.g. requirements gathering, resource management, communication, testing, dependencies, service acceptance criteria, etc.) and progressing through the design, development and transitioning of the new or changed service. Retiring an obsolete service falls under this section as well.
Part 1 is brilliant in its brevity – the requirements are concise and clear. What is not provided by Part 1 is the “how to do.” Part 2 and the other Parts provide further clarification and great insight to the requirements as well as specific examples to fulfil the requirements but, again, the “how to do” is still not prescribed. It is clearly up to the organization and their unique working environment to define how to meet the requirements and then document them. ISO/IEC 20000 family of documents is, in our opinion, the place to start any information gathering for an “adopt and adapt” initiative. Then utilize the other Service Management frameworks and standards as a body of knowledge to complete the “how.”
Table 2 lists the processes and the corresponding section numbering from the source document. These numbers are important to the mapping information found the Appendix.
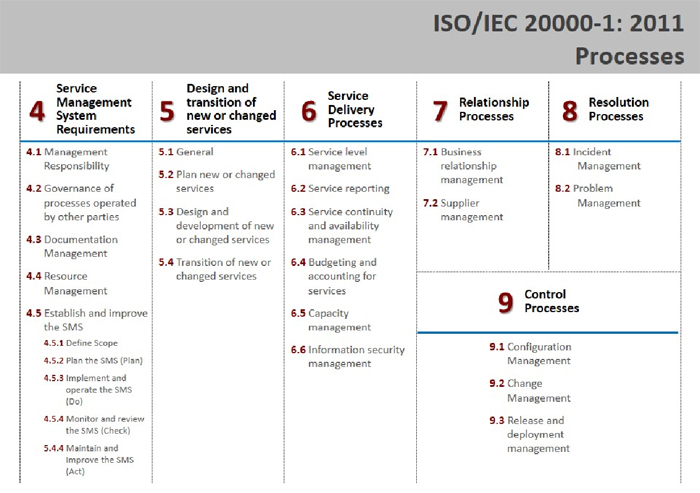
Table 2: ISO/IEC 20000 Processes
Overview of ITIL
The Information Technology Infrastructure Library (ITIL) describes a framework of best practices for the provision of quality services. ITIL is only one of part of a suite of publications that describe IT service management. The activities, processes, functions and capabilities documented in ITIL provide guidance that should be analysed by an organization to define an ‘adopt and adapt’ program of activities to improve service delivery based on their individual needs, culture, organizational structure, and so on. The use of public frameworks and standards benefit the organization as the “wheel isn’t reinvented” and the organization can create their own efficiencies from what has already been learned.

ITIL® Service Lifecycle Publications, 2011 Edition
So where do these ‘best practices’ originate? ITIL is based on various sources (e.g. standards, industry practices, academic research, training and education and internal experience) though the work of a variety practitioners (e.g. employees, customers, suppliers, advisers and technologies). Business requirements (e.g. legal, regulatory, customers, corporate mission, etc.) create knowledge that is fit for business purposes and has defined objectives, a specific context and measurable purpose.
As a ‘public domain’ set of best practices, the information held within ITIL is more likely to be used and improved via use and as such, offers an advantage over proprietary knowledge and processes. Thus, a great deal of the success of ITIL has been due to the fact that the information has been readily and easily available and the vocabulary used in the books has found general acceptance. Additionally, ITIL is vendor-neutral, non-prescriptive and represents best practices from industry leaders of best-in-class service providers. Adopting ITIL enables organizations to:
- Deliver value to customers through services
- Integrate service strategy with business strategy and customer need
- Measure, monitor and optimize IT services
- Manage risk
- Manage knowledge
- Manage capabilities and resources
- Adopt a standard approach to Service Management
- Change organizational culture to support achievement of sustained success
- Improve interaction and relationships with customers
- Optimize and reduce cost.
ITIL is based on the concept of a five-stage service lifecycle. A brief description of each stage is below:
- Service Strategy (SS) – strategy is the source of value creation as it is grounded in the understanding of organizational objectives and customer needs. Concepts such as provider types, market spaces, service assets, and the service portfolio are critical to this lifecycle stage. Processes supporting SS include:
- Strategy Management for IT Services (StM)
- Service Portfolio Management (SPM)
- Financial Management for IT Services (FM)
- Demand Management (DM)
- Business Relationship Management (BRM)
- Service Design (SD) – the stage that turns the service strategy into plans that will deliver business objectives. Key concepts of design and development, management systems, technology and architecture, process design and designing measurement systems are central to the activities within SD. Processes supporting these activities include:
- Design Coordination (DC)
- Service Catalogue Management (SCatM)
- Service Level Management (SLM)
- Availability Management (AM)
- Capacity Management (CapM)
- IT Service Continuity Management (ITSCM)
- Information Security Management (ISM)
- Supplier Management (SuppM)
- Service Transition (ST) – focuses on the processes necessary to deliver new or changed services (or removing a service) with the fundamental purpose of controlling risk. ST ensures the value identified in SS is effectively transitioned to operation. Processes that support the ST activities include:
- Transition Planning and Support (TPS)
- Change Management (ChM)
- Service Asset and Configuration Management (SACM)
- Release and Deployment Management (RDM)
- Service Validation and Testing (SVT)
- Change Evaluation (ChE)
- Knowledge Management (KM)
- Service Operation (SO) – includes the “visible” activities of the service provider – the agreed, designed and transitioned services are now available (visible). The activities and processes of SO all focus on the concept of value delivery not only to the customer and user, but also the service provider. Both proactive and reactive activities dominate this stage, again with the purpose of meeting the current and future needs of the business and service provider alike. Processes and functions (in italics) that support the SO activities include:
- Event Management (EM)
- Incident Management (IM)
- Request Fulfilment (RF)
- Problem Management (PM)
- Access Management (AccM)
- Service Desk
- Technical Management (TM)
- IT Operations Management (ITOpsM)
- Application Management (AppM)
- Continual Service Improvement (CSI) – focuses on the activities that support improvement initiatives within strategy, design, transition and operational activities. Using principles and practices from quality management, CSI links improvement activities to the ongoing needs of the business. Grounded in Deming’s Plan-Do-Check-Act (PDCA) methodology, CSI concentrates on elements of service measurement, reporting and assessments.
- 7-Step Improvement Process (7S)
More information around ITIL and its educational schema can be found at www.itil-officialsite.com.
Table 3 lists the processes and the corresponding section numbering from the source documents. These numbers are important to the mapping information found the Appendix.
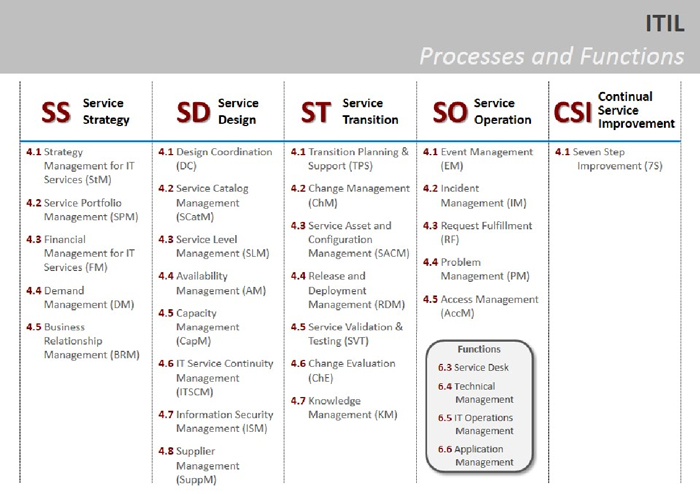
Table 3: ITIL Lifecycle Processes and Functions
Improvement Models
IT Governance Implementation Model
Within COBIT 5 Implementation, the “Implementation Life Cycle” is the core concept and is key to the COBIT5 framework. This reference guide provides a good practice approach to continual improvement that can be used to implement the various components of a governance framework. As with all improvement lifecycles, it can be tailored to meet specific enterprise needs.
It is well-known that any improvement initiative should be driven by the business need of creating value, and to ensure that this value is realized, adoption of efforts should be viewed from several different perspectives. Additionally, efforts should have the right mix of sponsorship, proper scope, well-understood objectives, and should fit the overall appetite for change that the enterprise can absorb.
The implementation lifecycle, illustrated in Figure 5, provides a methodology for organizations to leverage clearly defined (iterative) steps to adopt the COBIT framework. The three interrelated components and their associated steps are shown in the following table.
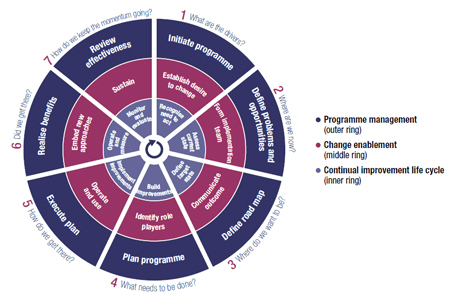
Figure 5: The Implementation Lifecycle
COBIT5 Implementation Guide, ISACA
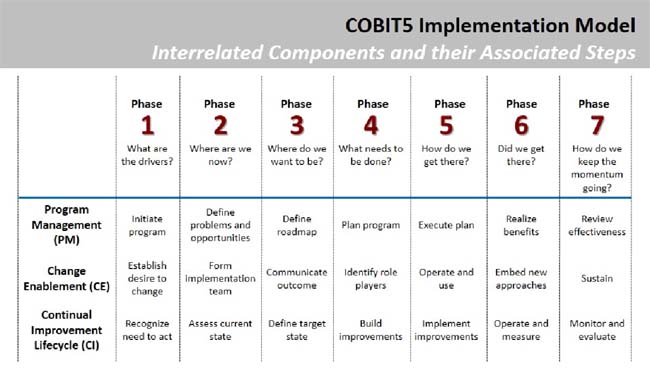
Table 4: Interrelated Components and their Associated Steps
This approach clearly indicates that all three components need to be addressed and that they are interrelated – any major improvement effort (like the deployment of a new or changed service or process) requires the control that good program management will bring as well as some changes within the organization, specifically, understand and addressing the organizational change tolerance as well as developing and enhancing the cultural environment for continual improvement. There are seven phases; each defining a main activity within that component. The seven phases are:
- Phase 1: What are the drivers? Identifies the need for improvement by capturing and addressing change drivers and trigger events (pain points) and subsequently, creates a desire to change from an executive level, documented in a business case.
- Phase 2: Where are we now? The focus of this phase is defining current capability by defining enterprise and IT-related goals via the Goals Cascade. These elements will guide a process capability assessment, with the end result answering “where we are now” based on the pre-defined desired state.
- Phase 3: Where do we want to be? Improvement targets are set based on the process capability assessment. These results will define the gap between the as-is and the to-be state which identify improvement opportunities.
- Phase 4: What needs to be done? Improvement solutions are documented noting that some may be very quick wins and others may have much longer implementation timelines. Define the projects based on priority of the projects overall contribution to overall business objectives.
- Phase 5: How do we get there? Deploy the practical solution meeting the various objectives defined in the previous steps. Ensure good measures are defined, deployed and monitored to ensure continued alignment with business objectives as well as continued engagement of top management and other stakeholders.
- Phase 6: Did we get there? Continue monitoring and ensure no recidivism in order to achieve the expected benefits.
- Phase 7: How do we keep the momentum going? Review the program success, any new governance or management requirements and reinforce the need for continual improvement.
PDCA
Many process-based management systems (i.e. ISO9001, ISO/IEC 20000, ISO/IEC 27001, etc.) are underpinned by the Deming Cycle (Plan-Do-Check-Act - PDCA). The power of this methodology is in its absolute simplicity – four easy to understand steps that drive continual review and assessment of a process or activity. Briefly, PDCA can be condensed as such:
- Plan – objectives, policies, plans are defined for a process, service, system.
- Do – implement the process, service, system.
- Check – monitor and measure the activities and outcomes against the objectives, policies and requirements; report on the results.
- Act – based on the assessed results, take actions to improve the performance.

PDCA is meant to be iterative with each cycle moving the process closer and closer to the defined “ultimate” goal. What is interesting is that the success of PDCA is based on the capture of knowledge from previous iterations. This increase of knowledge within each iteration allows one to refine the ultimate goal, which may very well be an initial “best guess,” to something that is more appropriate and focused on true business need. This methodology allows for movement where the sometimes overwhelming “ready, aim, aim, aim, aim, aim….” actions of getting it “perfect” the first time and never accomplishing anything are now replaced with a “ready, aim, fire, aim, fire” action. Between each “aim, fire” sequence, the lessons learned are applied to the next. This is more “forgiving” than having a specific, “set in stone” goal that on paper, is fantastic but when operationalized, very unrealistic. Now, learning and improvement are a constant rather than a side-effect of, possibly, a very expensive and limited value exercise.
PDCA underpins the activities and processes of the Service Management System (SMS) as described in ISO/IEC 20000-1. Also, it is quite easy to see where the ITIL Service Lifecycle holds the PDCA elements:
- Plan – Service Strategy and Service Design
- Do – Service Transition
- Check – Service Operation
- Act – Continual Service Improvement.
CSI Approach
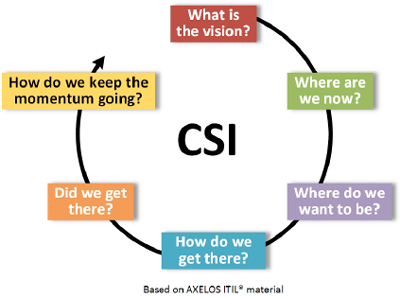
One improvement method found within the 2011 ITIL literature is the CSI Approach (formally CSI Model or CSI Plan). This approach can be summarized in six steps (see Figure 7):
- What is the vision? – understand the high-level business objectives, the organizational culture and environment (is it ready to or can it embrace the changes?), ensure the alignment of business and IT strategies, specifically linking the improvement to the benefit and support of the organizational directions.
- Where are you now? – complete a baseline maturity assessment against a known standard or benchmark (ISO/IEC 20000-1, COBIT, SWOT analysis, etc.) where people (skills and competencies; values and beliefs), process, products (technology and tools) and partners (suppliers and partners) are fully analysed.
- Where do you want to be? – agree and prioritize the improvements that represent the steps necessary to achieve the vision thus setting specific goals and objectives (SMART) across the enterprise within a manageable timeframe.
- How do we get there? – implement a detailed plan based on the improvements previously defined to improve service and process quality.
- Did we get there? – define a series of measurements and metrics to measure progress to the agreed milestones, but also ensure compliance to the new process or service activities.
- How do we keep the momentum going? – using measures and metrics, organizational change techniques and good management to ensure changes become embedded in the organization and there is no opportunity or tolerance for recidivism and then start the cycle again – review vision and objectives, identify new improvements, etc.
Deming’s PDCA can easily be seen in this model with the first three steps fulfilling “Plan” and then the remaining steps match up directly with the final three Deming components.
This approach is valid in any and every aspect of the business. Frankly, we have followed this model on our consulting engagements – it’s clear and simple and it demands a focus on the business need, thus providing value for the customer and service provider. Apply this model not only to in-place services and functions but also to the ones that are only in the planning or ‘pre-planning’ stages. Following this specific model can prevent design flaws, provide focus for strategic activities, and improve transition measures and on-going operational activities because the focus is on the end goal – achievement of business outcome. The question “how does the proposed improvement allow for the achievement of organizational goals?” is now definitively answered.
ITIL® Service Lifecycle Publications, 2011 Edition
Summary
We think it is fairly clear that these three improvement models have a bit of overlap. The main point here is that as a service manager you adopt and adapt a model – be it the Implementation Lifecycle, Deming or the CSI Approach, or one of the many other models available. Or better yet, create something that works for you and your clients, always remembering the many elements to consider to ensure a robust improvement.

4Free to members and non-members of ISACA. All other volumes are available for purchase for non-members.
5Under review – currently in preliminary status
6 Under development
7On hold status pending ISO/ITTF decision on publication
8 ISO/IEC 20000-1:2011, Information Technology – Service Management – Part 1: Service management system requirements
